Safety researchers hacked Tesla’s Wall Connector electrical car charger twice on the second day of the Pwn2Own Automotive 2025 hacking contest.
In addition they exploited 23 extra zero-day vulnerabilities in WOLFBOX, ChargePoint Residence Flex, Autel MaxiCharger, Phoenix Contact CHARX, and EMPORIA EV chargers, in addition to within the Alpine iLX-507, Kenwood DMX958XR, Sony XAV-AX8500 In-Car Infotainment (IVI) techniques.
PHP Hooligans had been the first to crash the Tesla Wall Connector after utilizing a Numeric Vary Comparability With out Minimal Test zero-day bug to take over the gadget. They had been adopted by Synacktiv, who additionally hacked Tesla’s EV charger through the Charging Connector, an method that is by no means been demonstrated publicly earlier than.
At the moment, two bug collisions occurred throughout Tesla Wall Connector hacking makes an attempt: one by staff PCAutomotive and the opposite by the Summoning Crew’s Sina Kheirkhah, who used an exploit chain of two already-known bugs.
Based on the Pwn2Own Tokyo 2025 contest guidelines, all gadgets focused in the course of the competitors should have all safety updates put in and run the newest working system variations.
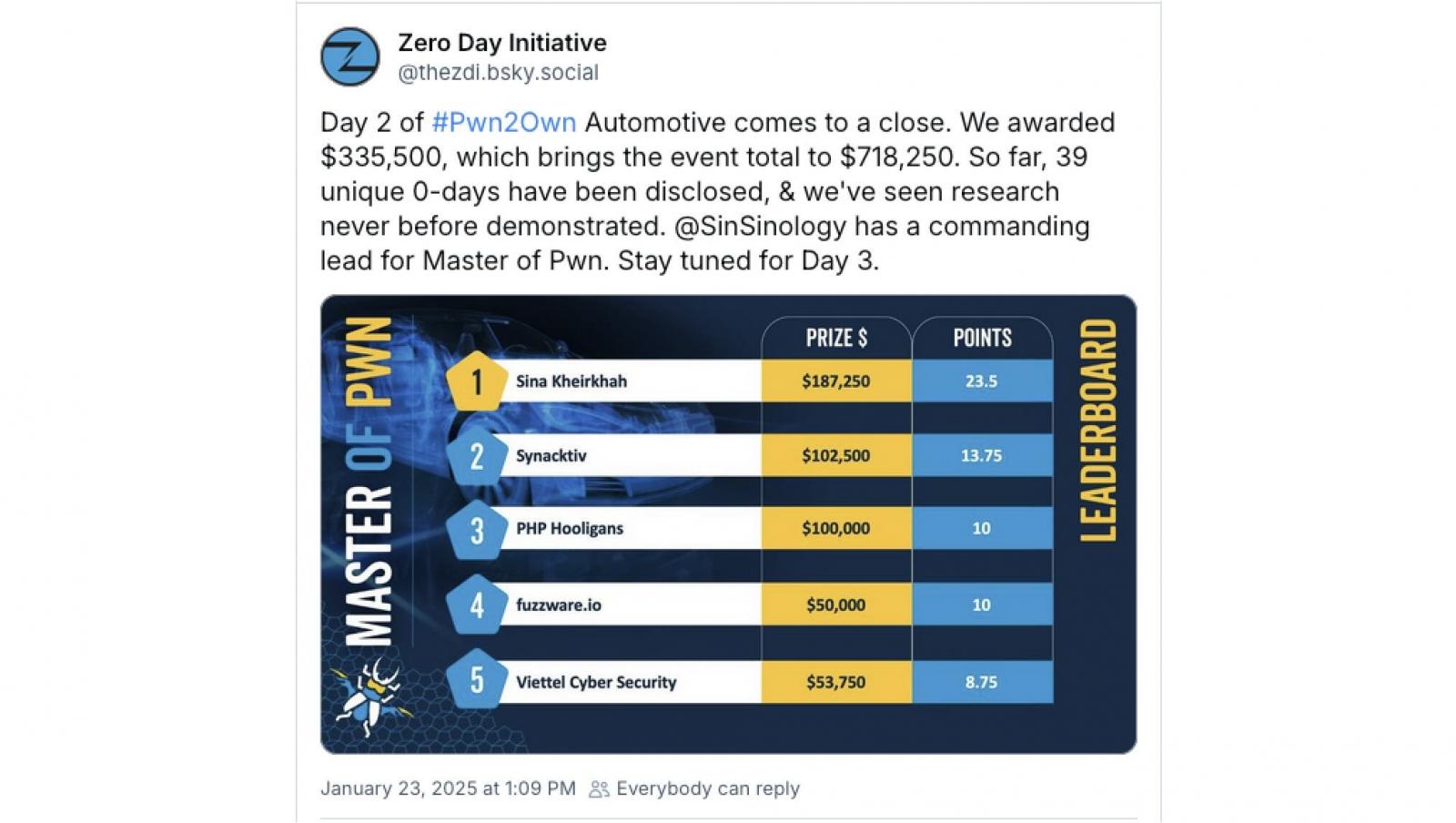
Development Micro’s Zero Day Initiative awarded $335,500 in money rewards in the course of the second day for 23 zero-day vulnerabilities. Sina Kheirkhah is presently within the lead for Grasp of Pwn.
On the primary day of Pwn2Own Automotive, safety researchers exploited 16 distinctive zero-day vulnerabilities and picked up $382,750 in money awards. After the competitors ends, distributors may have 90 days to develop and launch safety fixes earlier than ZDI publicly discloses the zero-day bugs.
The Pwn2Own Automotive 2025 hacking contest will give attention to automotive applied sciences from January 22 to January 24 in the course of the Automotive World convention in Tokyo, Japan.
Hackers will goal automotive working techniques (i.e., Automotive Grade Linux, Android Automotive OS, and BlackBerry QNX), electrical car (EV) chargers, and in-vehicle infotainment (IVI) techniques.
Despite the fact that Tesla additionally offered a Mannequin 3/Y (Ryzen-based) equal benchtop unit, no safety researcher had registered an try in opposition to the corporate’s wall connector earlier than the competitors’s schedule was revealed. The schedule for the second day and the outcomes for every problem can be discovered right here.
One yr in the past, throughout the primary version of Pwn2Own Automotive in Tokyo, safety researchers had been awarded $1,323,750 for hacking a Tesla twice and exploiting 49 zero-day bugs in a number of electrical automotive techniques.