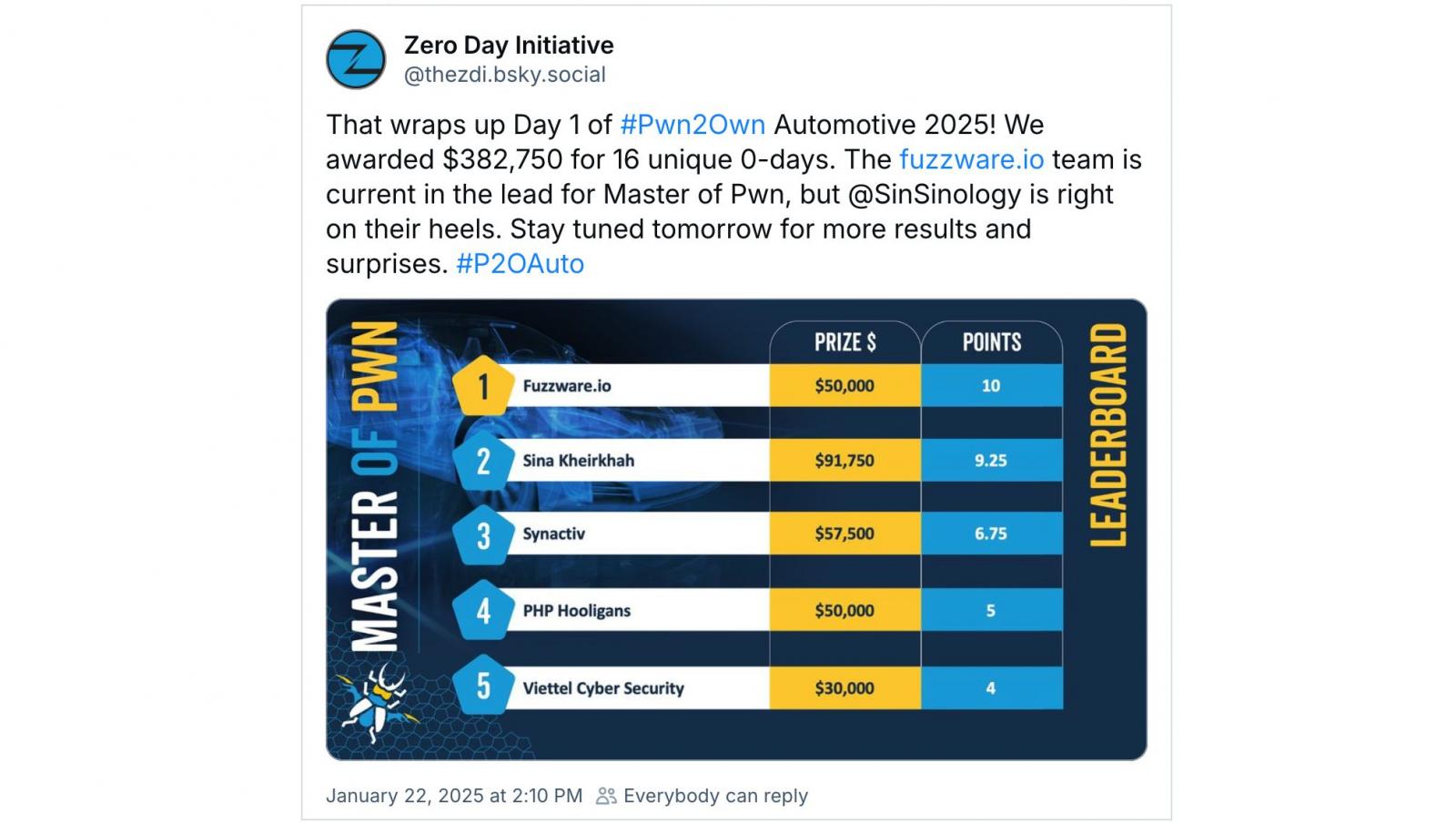
On the primary day of Pwn2Own Automotive 2025, safety researchers exploited 16 distinctive zero-days and picked up $382,750 in money awards.
Fuzzware.io is main the competitors after hacking the Autel MaxiCharger and Phoenix Contact CHARX SEC-3150 electrical automobile chargers utilizing a stack-based buffer overflow and an origin validation error bug. This earned them $50,000 and 10 Grasp of Pwn factors.
Sina Kheirkhah of Summoning Workforce additionally earned $91,750 and 9.25 Grasp of Pwn factors after hacking the Ubiquiti and Phoenix Contact CHARX SEC-3150 EV chargers utilizing a hard-coded cryptographic key bug and a combo of three zero-days (one in all them beforehand identified).
Synacktiv Workforce is in third place on the leaderboard and took dwelling $57,500 after efficiently demoing a bug within the OCPP protocol to hack the ChargePoint House Flex (Mannequin CPH50) utilizing sign manipulation by means of the connector,
Safety researchers from PHP Hooligans additionally efficiently hacked a totally patched Autel charger utilizing a heap-based buffer overflow and earned $50,000, whereas the Viettel Cyber Security staff collected $20,000 after acquiring code execution on the Kenwood In-Car Infotainment (IVI) utilizing an OS command injection zero-day.
After the zero-day vulnerabilities are exploited and reported throughout Pwn2Own, distributors have 90 days to develop and launch safety patches earlier than TrendMicro’s Zero Day Initiative publicly discloses them.
The Pwn2Own Automotive 2025 hacking competitors, which focuses on automotive applied sciences, takes place in Tokyo from January 22 to January 24 throughout the Automotive World auto convention.
All through the competition, safety researchers can goal electrical automobile (EV) chargers, in-vehicle infotainment (IVI) techniques, and automotive working techniques (i.e., Automotive Grade Linux, Android Automotive OS, and BlackBerry QNX).
Whereas Tesla additionally supplied a Mannequin 3/Y (Ryzen-based) equal benchtop unit, contestants have solely registered makes an attempt in opposition to the corporate’s wall connector.
The whole schedule for this yr’s automotive hacking contest is out there right here, whereas the schedule for the primary day and the outcomes for every problem might be discovered right here.
Throughout the primary version of Pwn2Own Automotive in January 2024, hackers collected $1,323,750 for hacking Tesla twice and demonstrating 49 zero-day bugs in a number of electrical automotive techniques.
Two months later, throughout Pwn2Own Vancouver 2024, safety researchers earned $1,132,500 after exploiting 29 zero-days (and a few bug collisions). Synacktiv went dwelling with $200,000 and a Tesla Mannequin 3 automotive after hacking the ECU with Car (VEH) CAN BUS Management in beneath 30 seconds.