The origins of Sysdig, Falco, and Wireshark might be traced again to 1 elementary want: making sense of complicated, real-time community site visitors for higher safety and operational insights. Lengthy earlier than containers and cloud safety grew to become urgent considerations, Gerald Combs and Loris Degioanni, creators of Wireshark, had been fixing a distinct however associated drawback: the best way to seize and analyze packets to know what was occurring throughout networks. Wireshark emerged as a important software, offering unprecedented visibility into community habits and setting the usual for packet evaluation.
The shift towards cloud-native environments introduced new challenges, and conventional packet seize alone had been now not sufficient. Applied sciences like BPF, libpcap, tcpdump, and Snort laid the groundwork, however as workloads moved to containers and distributed methods, deeper runtime visibility and safety monitoring grew to become important. This evolution led to the creation of open-source Sysdig and Falco, which had been designed to deliver the identical stage of runtime perception to the world of containers and cloud safety that Wireshark had delivered to community site visitors. Nevertheless, many engineers and analysts nonetheless wanted an open supply software that would allow them to investigate and troubleshoot cloud system calls and logs with the extent of granularity that Wireshark afforded them on networks.
Stratoshark guarantees simply this: extending the rules of packet seize to watch and safe fashionable, distributed environments and push the boundaries of real-time cloud system evaluation with a workflow that Wireshark customers will discover acquainted.
Understanding the inspiration of packet seize
At its core, Wireshark depends on libpcap, a flexible library that manages reside packet seize, filtering, and file dealing with. Libpcap grew to become a basis for numerous instruments, offering a generic interface that might be prolonged to suit varied wants. Snort, for example, constructed a robust rule engine for community intrusion detection immediately on high of libpcap, leveraging its packet seize capabilities to detect and forestall suspicious community exercise.
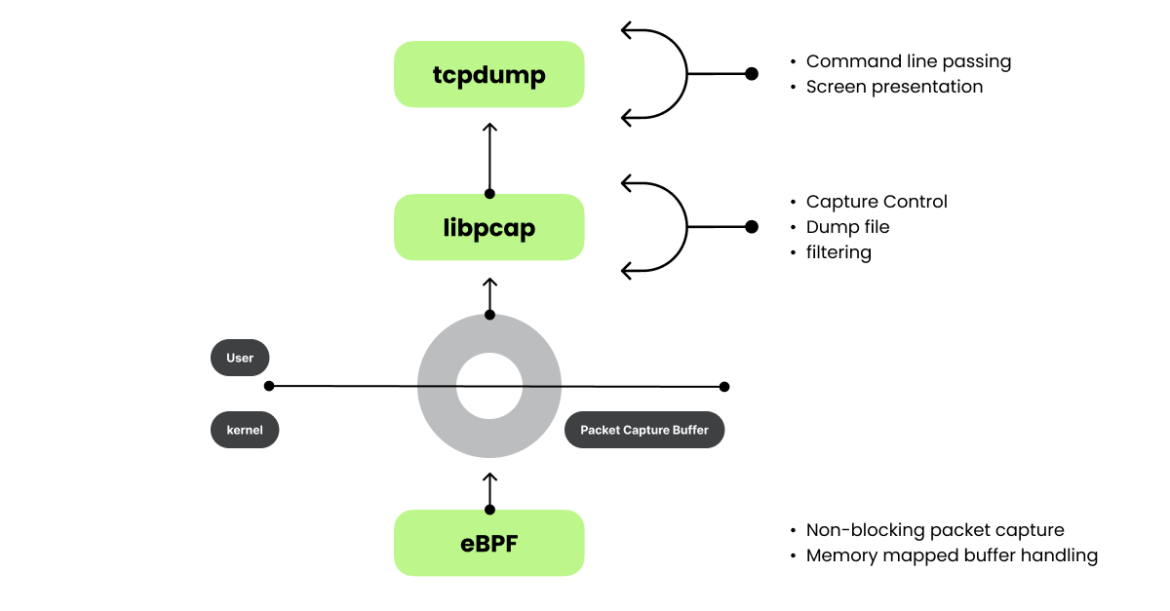
Drawing from the libpcap mannequin, Falco emerged as a runtime safety software that displays Linux, containers, and Kubernetes environments. As an alternative of packets, Falco focuses on system calls to detect anomalies, making use of rules just like these utilized in community monitoring. On the coronary heart of Falco’s structure are two important libraries: libscap and libsinsp. These libraries mirror the function of libpcap within the packet world however for system calls and system state seize. Libscap handles low-level seize duties, managing reside knowledge assortment and recording, whereas libsinsp abstracts system data, providing higher-level insights and filtering capabilities. Collectively, they supply detection analysts with deep, real-time visibility into system exercise and allow sooner detection, investigation, and response to safety threats and efficiency points.
Understanding the present state of system name seize
Open supply Sysdig was the primary undertaking to hyperlink these libraries right into a user-facing software, very similar to tcpdump gives an interface for libpcap. Sysdig mixed libscap and libsinsp to supply deep visibility into system habits, permitting customers to hint exercise throughout containers and hosts with ease. Though Falco and Sysdig share elements, Falco doesn’t immediately rely upon OSS Sysdig; as a substitute, it leverages sysdig-probe, libscap, and libsinsp via clear, modular interfaces. This separation displays a deliberate design option to preserve the core seize libraries versatile, fostering the event of a number of instruments from a standard base.
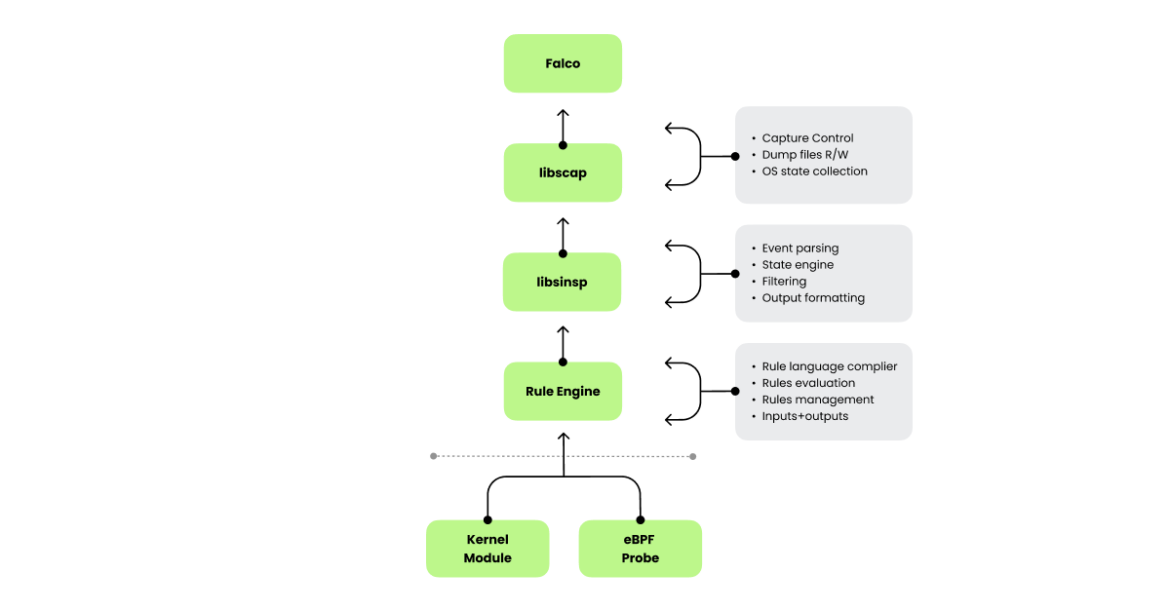
The parallels between Snort and Falco prolong past their reliance on seize libraries. Simply as Snort employs libpcap to investigate packet knowledge, Falco makes use of libscap and libsinsp to investigate system calls. Falco’s rule engine, impressed by Snort’s design, applies pattern-matching rules to runtime knowledge, specializing in cloud workloads and container environments quite than conventional community packets.
| 1998 | 2013 | 2013 | 2015 | 2016 | 2025 |
| Wireshark | Docker | Sysdig | Kubernetes | Falco | Stratoshark |
Wireshark was developed throughout an period when conventional on-premises networks had been the norm, and packet sniffing on bodily networks was customary observe. AWS cloud providers didn’t emerge till 2006. When Docker popularized containerization, Sysdig rapidly adopted to offer system visibility. Equally, as Kubernetes gained traction, Falco was launched to boost container safety. Now, with widespread cloud adoption, community engineers are keen to use their packet evaluation experience — honed via Wireshark — to the world of Linux containers and cloud environments. This want for seamless packet inspection in fashionable infrastructures led to the creation of Stratoshark.
Stratoshark bridges the hole between community packet evaluation and fashionable cloud-native safety. The software depends on libscap and libsinsp, sourced from the falcosecurity/libs repository, alongside plugins from falcosecurity/plugins. In doing so, Stratoshark extends the evolutionary arc that started with Wireshark. By integrating acquainted packet inspection methods with up to date runtime monitoring, Stratoshark represents the following step in unifying conventional community safety with the calls for of cloud-native environments.
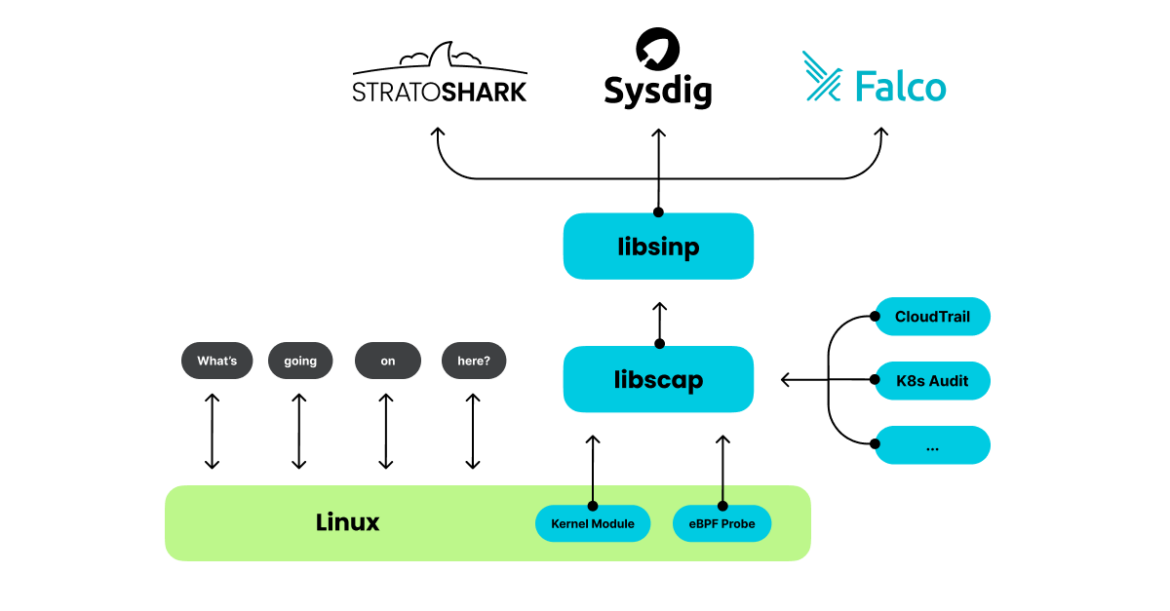
Monitoring Cloud Audit Logs in Stratoshark
falcodump is an extcap software that enables customers to seize log messages from cloud suppliers. The extcap interface is a flexible plugin interface that enables exterior binaries to behave as seize interfaces immediately in Wireshark. Within the case of Stratoshark, every plugin is listed as a separate interface. For instance, the AWS CloudTrail plugin could be listed as “cloudtrail.” All situations of Stratoshark come packed by default with the Falco CloudTrail plugin, which may pull AWS CloudTrail logs from an S3 bucket or SQS/SNS.
Whereas Stratoshark might be put in on Home windows and MacOS, native system name captures aren’t but supported on these platforms. This will solely be executed on Linux methods, just like Falco, which you must construct from scratch with the suitable Falco libs and plugins. If you’re enthusiastic about putting in on different methods, you will get the early growth packages for Home windows and OSX.
1. Amassing an SCAP file
The best option to acquire a Syscall CAPture (SCAP) file is through Sysdig OSS. The Sysdig OSS Github repository gives a single-line command to put in Sysdig OSS on nearly any Linux distribution, or you possibly can run Sysdig as a Docker container:
curl -s https://s3.amazonaws.com/obtain.draios.com/steady/install-sysdig | sudo bashCode language: Perl (perl)You may run the beneath 5-second timeout command to get a 5s seize out of your Linux atmosphere right into a file known as generic-capture.scap:
timeout 5 sysdig -w generic-capture.scapCode language: Perl (perl)2. Studying the SCAP in Stratoshark
If you’re not enthusiastic about capturing your individual .scap file proper now, you possibly can obtain one of many examples supplied beneath:
- 502 Error seize for troubleshooting HAProxy 502 – Obtain
- 404 Error seize of a 404 error from a leaky file – Obtain
- curl-wsdl-win64.scap seize of curl exercise – Obtain
- Lively Malware seize from Kubernetes – Obtain
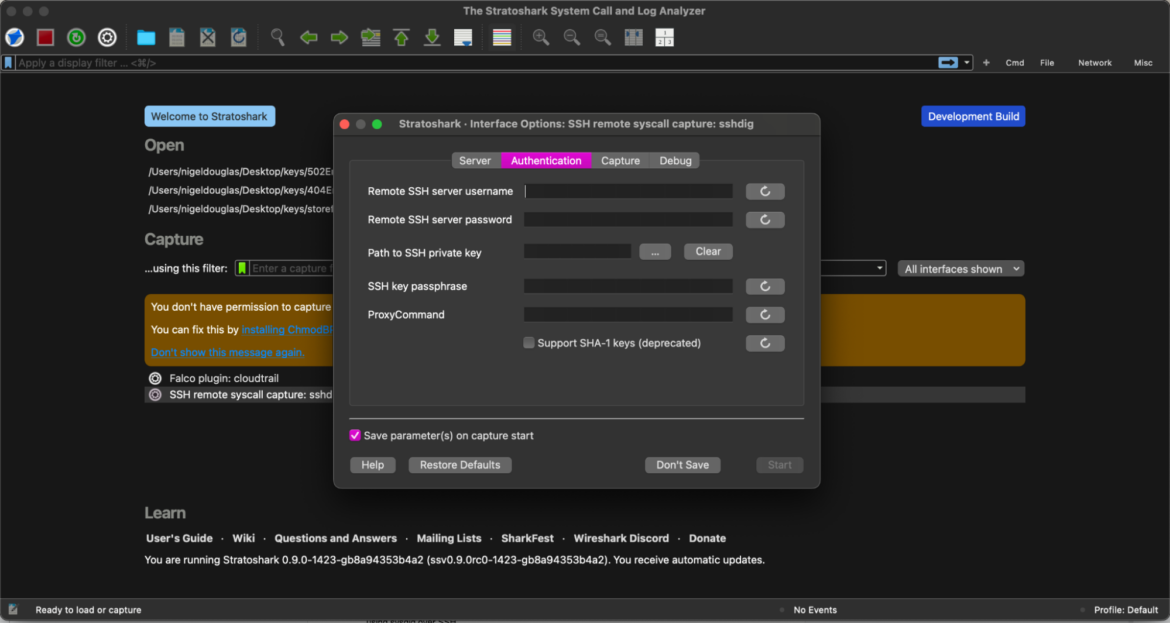
While you open the Stratoshark person interface (on Mac), you’ll discover the flexibility to both open an current SCAP seize file from Sysdig OSS or connect with AWS utilizing the Falco Cloudtrail Plugin. The ultimate choice is to hook up with an SSH distant syscall server through sshdig.
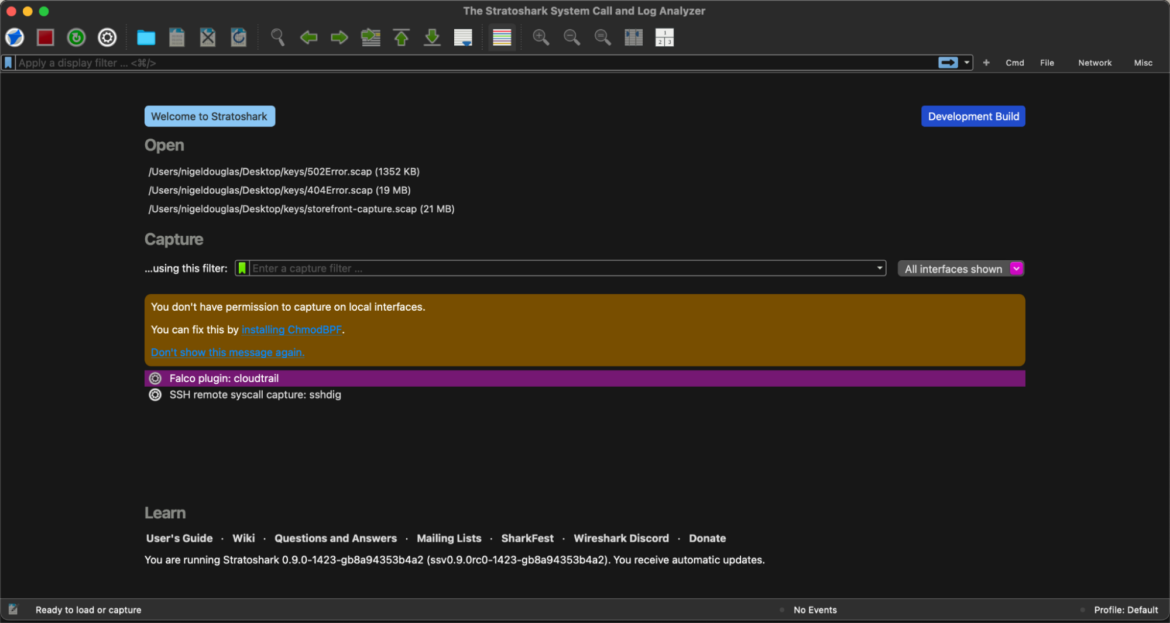
As of the model Stratoshark 0.9.0rc0-974 and later packages supplied right here, Stratoshark features a new seize supply named “sshdig.” It enables you to seize syscalls from a distant host utilizing Sysdig over SSH. You’ll must know the SSH server tackle, username, and password credentials to attach.
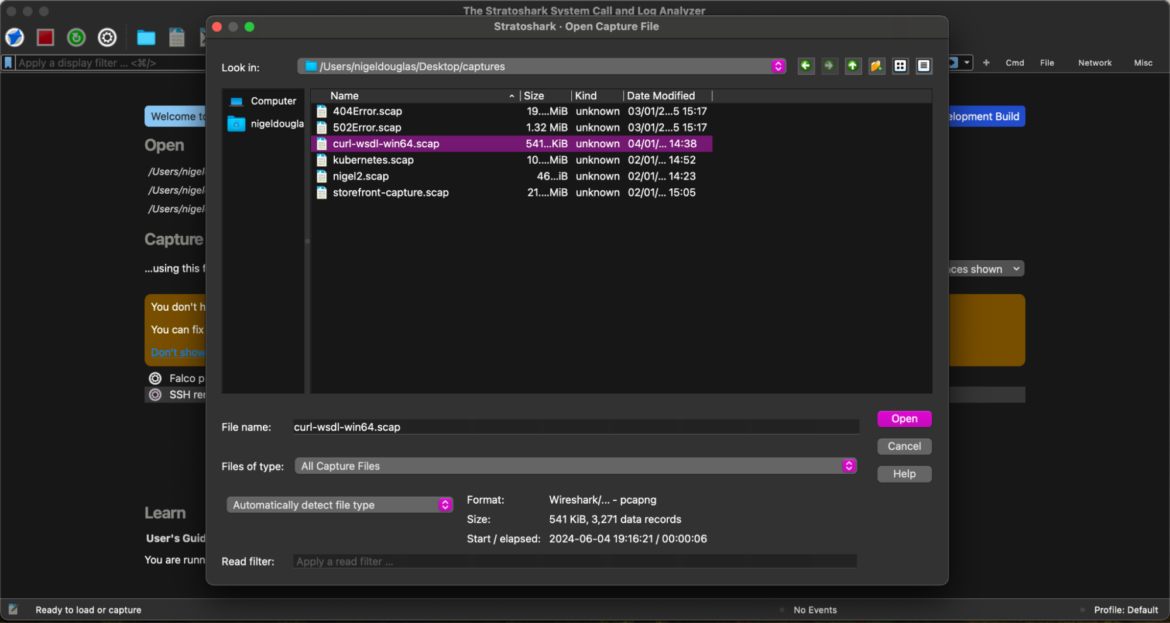
For this tutorial, we’ll use Stratoshark with the curl-wsdl-win64.scap seize file supplied by the Wireshark crew on Discord. Click on on the blue folder icon within the higher toolbar and open the .scap seize – just like the way you’d open a PCAP file in Wireshark.
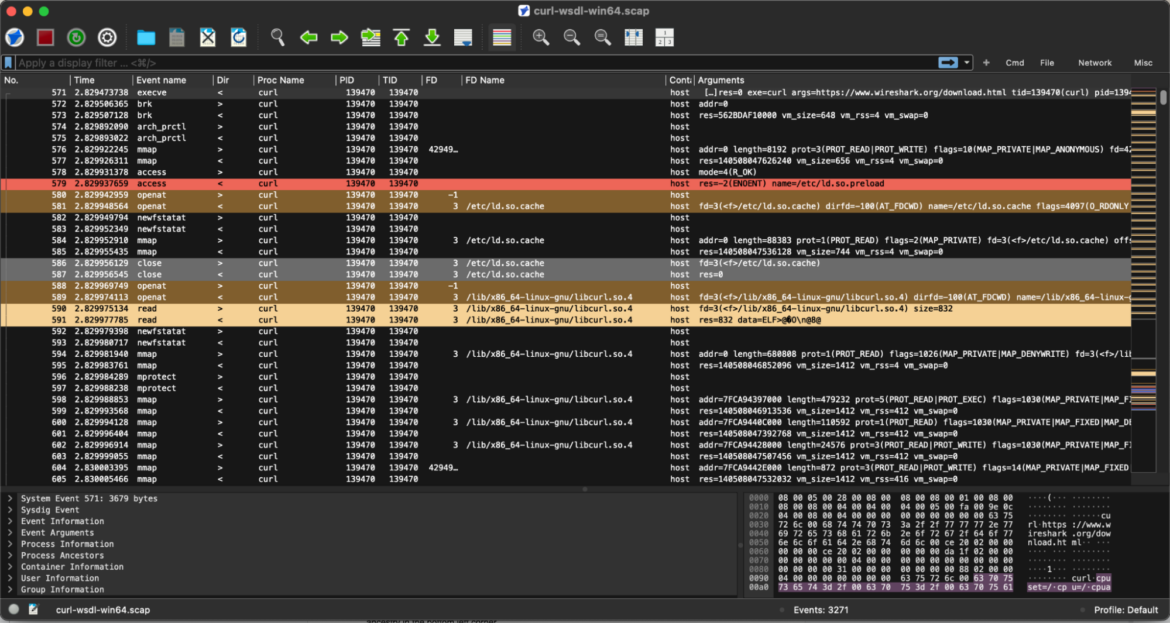
While you open the file, you’ll discover the interface intently mirrors the acquainted person expertise of Wireshark. Nevertheless, not like conventional packet inspection, further fields within the backside left nook present insights into occasions, customers, and course of ancestry, providing a extra complete system exercise view.
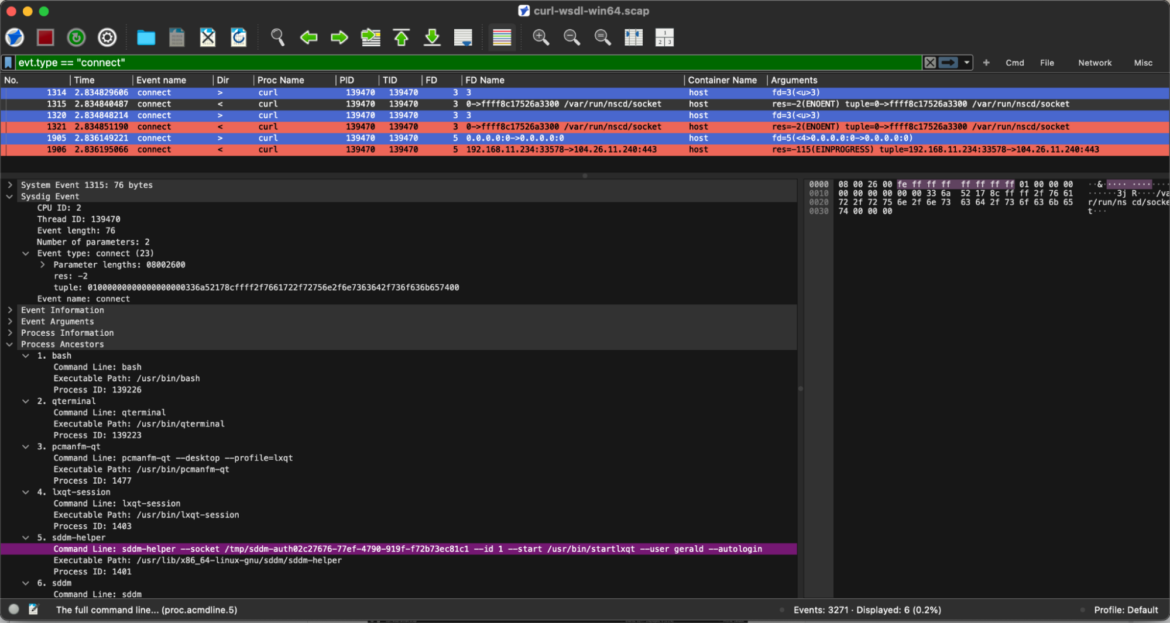
To establish all outbound connection requests initiated by curl, we are able to effortlessly apply the next occasion filter search:
evt.sort == "connect"Code language: Perl (perl)By inspecting the method ancestry, we are able to hint the precise command-line argument that initiated the outbound community connection. This not solely highlights the particular cURL request accountable but in addition reveals the total context surrounding the occasion — from mother or father processes to related threads — providing a clearer image of how and why the connection was made. This stage of visibility is essential for troubleshooting, auditing, and enhancing total community safety.
From a troubleshooting standpoint, it’s necessary to acknowledge that system calls can generally fail for authentic causes. Nevertheless, figuring out and understanding the foundation trigger of those failures is important, particularly when coping with key elements or protocols, such because the Falco Bridge on this state of affairs. Gaining visibility into why these failures happen permits operations and safety groups to conduct deeper investigations, mitigating potential system instability or efficiency points earlier than they escalate.
To streamline this course of, the next Stratoshark filtered search highlights all related exercise in pink, drawing instant consideration to areas that will require nearer inspection. This makes it simpler to pinpoint irregularities and tackle them proactively.
(evt.failed == True) && !(evt.res == "EAGAIN") && !(evt.res == "EALREADY")Code language: Perl (perl)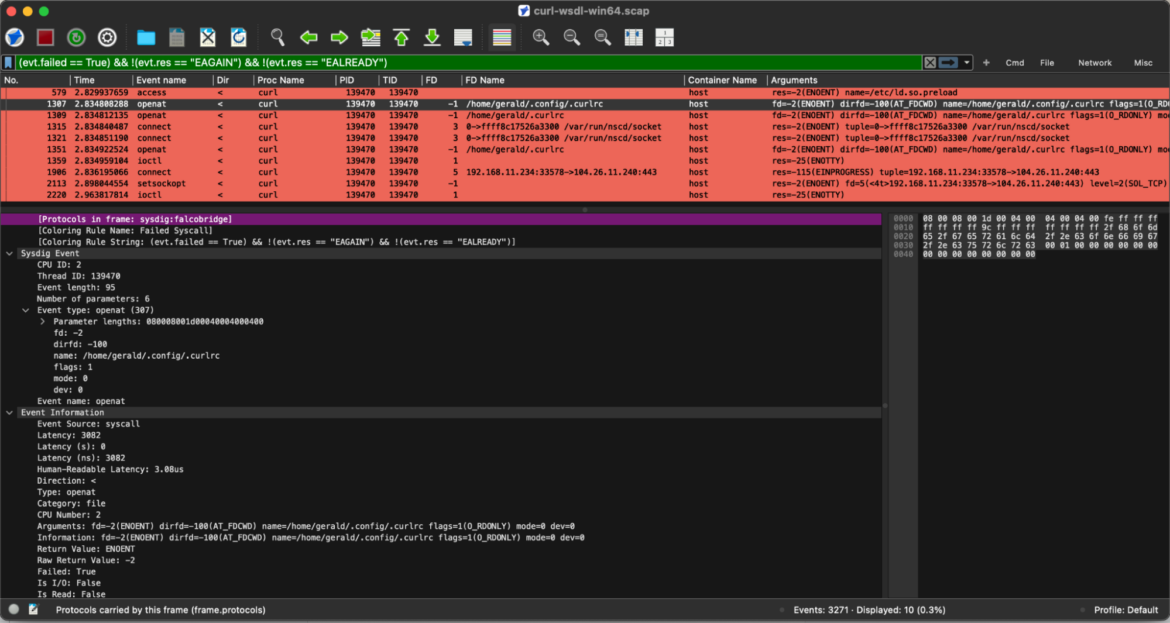
Conclusion
Stratoshark represents the following evolution in packet evaluation and the newest milestone in Sysdig’s ongoing open supply journey. Stratoshark guarantees to bridge the hole between conventional community monitoring experience, the dynamic nature of system name displays in containers, and sporadic audit exercise in cloud environments. Born from the open-source ingenuity behind Wireshark, Sysdig, and Falco, Stratoshark empowers engineers to increase their experience into fashionable infrastructure.
Whether or not you’re simply getting began or desirous to dive deeper, there’s no higher time to discover what Stratoshark has to supply. To be taught extra concerning the open-source tasks driving this innovation, go to Sysdig’s contributions web page. For a better have a look at Stratoshark in motion, don’t miss Gerald Combs’ keynote from Sharkfest Europe — it’s an important look ahead to anybody keen about the way forward for packet evaluation.