SUMMARY
- Infoblox found widespread area spoofing in spam campaigns whereas investigating ‘Muddling Meerkat.’
- Collaboration with the cybersecurity neighborhood linked Muddling Meerkat’s DNS actions to spam distribution.
- Researchers recognized a number of spam campaigns via abuse studies and area evaluation.
- Strategies included phishing with QR codes, impersonating manufacturers, extortion, and mysterious monetary spam.
- The findings present area spoofing stays extremely efficient, bypassing present safety measures.
In its newest report, cybersecurity agency Infoblox has revealed how scammers use area spoofing in spam campaigns, a discovery made via a collaboration between the cybersecurity and networking neighborhood on analysis about the Chinese language Nice Firewall.
This analysis challenge was initially geared toward understanding the actions of a menace actor often known as a Muddling Meerkat. Muddling Meerkat is understood for conducting unusual DNS operations involving faux Chinese language Nice Firewall responses. The researchers couldn’t decide the final word goal of Muddling Meerkat’s actions, however they did study so much about how area spoofing is utilized in malspam.
The analysis crew, initially perplexed by Muddling Meerkat’s actions, sought exterior views by sharing their findings with the broader safety neighborhood. One key commentary pointed in direction of a possible connection between Muddling Meerkat’s operations and spam distribution.
A number of organizations reported receiving abuse notifications for domains they owned, typically inner domains with restricted exterior publicity. These notifications indicated large-scale spam campaigns originating from Chinese language IP addresses, concentrating on main e-mail suppliers. This commentary resonated with the crew’s personal findings, as they’d beforehand noticed Muddling Meerkat producing faux mail server (MX) data emanating from Chinese language IP house.
A major breakthrough occurred when the researchers found that they owned a number of of the “target” domains recognized within the Muddling Meerkat analysis. By analysing abuse studies associated to their very own domains, leveraging their authoritative DNS server logs, and inspecting their inner spam assortment, the researchers gained unprecedented insights into the techniques employed by spammers.
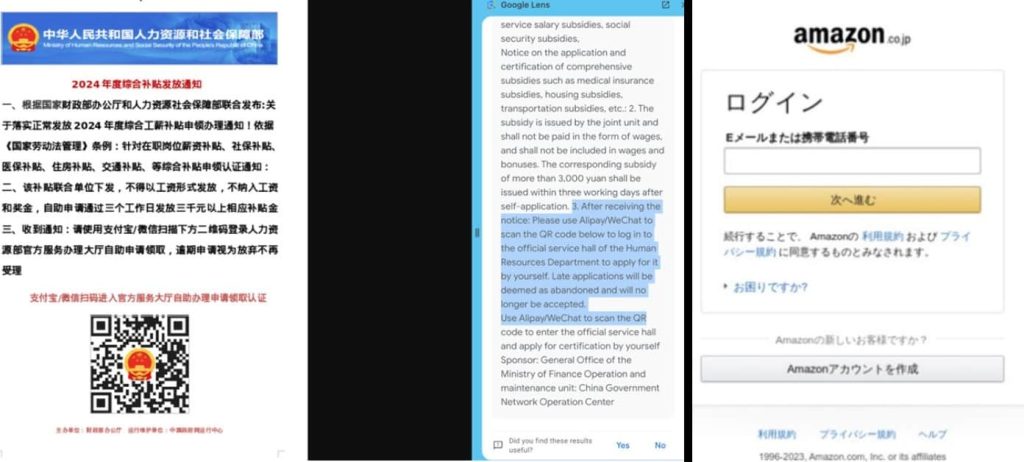
The investigation yielded a treasure trove of details about trendy malspam strategies. A number of distinct campaigns had been recognized, every using refined area spoofing techniques to deceive recipients. These embrace QR Code Phishing, concentrating on Chinese language residents with emails containing QR codes, which redirect victims to phishing web sites. Japanese Phishing campaigns impersonate respected manufacturers like Amazon and main Japanese banks and lure customers to faux login pages.
Extortion campaigns demand ransom funds in cryptocurrency to forestall publicity. Mysterious Monetary Campaigns, originating from China, ship seemingly innocuous spreadsheet attachments purporting to be from a Chinese language freight firm. The aim of those campaigns stays unclear, as they lack clear malicious content material or motive, Infoblox researchers famous of their technical weblog shared with Hackread.com.
However, the analysis reveals a disturbing actuality: area spoofing stays a extremely efficient and prevalent tactic for spammers. Regardless of the existence of varied safety mechanisms designed to detect and forestall spoofing, these campaigns proceed to evade detection and efficiently attain their targets.
Infoblox’s analysis got here simply days after one other area abuse-related report was revealed by WatchTowr, which uncovered greater than 4,000 lively hacker backdoors in expired domains and deserted infrastructure worldwide. This exhibits the continuing problem of combating refined spam strategies and the necessity for steady implementation of cybersecurity measures.
RELATED TOPICS
- Hackers Use Pretend Domains in Trump Buying and selling Card Rip-off
- 99% of UAE’s .ae Domains Uncovered to Phishing and Spoofing
- “Sitting Ducks” DNS Assault Lets Hackers Straightforward Area Takeover
- Scammers Exploit Pretend Domains in Dubai Police Phishing Scams
- DeFi Hack Alert: Squarespace Domains Susceptible to DNS Hijacking