A Chinese language risk actor is as soon as once more exploiting Ivanti distant entry units at giant.
In the event you had a nickel for each high-profile vulnerability affecting Ivanti home equipment final yr, you’d have numerous nickels. There was the vital authentication bypass in its Digital Visitors Supervisor (vTM), the SQL injection bug in its Endpoint Supervisor, a trio affecting its Cloud Providers Equipment (CSA), vital points with its Standalone Sentry and Neurons for IT Service Administration (ITSM), plus dozens extra.
It began final January, when two critical vulnerabilities have been found in Ivanti’s Join Safe (ICS) and Coverage Safe gateways. By the point of disclosure, the vulnerabilities have been already being exploited by the Chinese language-nexus risk actor UNC5337, believed to be an entity of UNC5221.
Now, one yr and one secure-by-design pledge later, UNC5337 has returned to hang-out Ivanti once more. The group has been exploiting a new vital vulnerability in ICS, which additionally impacts Coverage Safe and Neurons for Zero Belief Entry (ZTA) gateways. Ivanti has additional warned of a second, barely much less extreme bug that hasn’t been noticed in exploits but.
“Just because we’re seeing these often doesn’t necessarily mean that they’re easy to pull off — it’s a highly sophisticated group that is doing this,” Arctic Wolf CISO Adam Marrè factors out, in protection of the downtrodden IT vendor. “Engineering is not easy, and secure engineering is even more difficult. So even though you may be following the principles of secure-by-design, that doesn’t mean that someone isn’t going to be able to come along and either with new technologies, or new techniques, and enough time and resources, hack in.”
2 Extra Safety Bugs in Ivanti Units
As but unexploited (so far as researchers can inform) is CVE-2025-0283, a buffer overflow alternative in ICS variations previous to 22.7R2.5, Coverage Safe earlier than 22.7R1.2, and Neurons for ZTA gateways earlier than 22.7R2.3. The “high” severity 7.0 out of 10-rated concern within the Frequent Vulnerability Scoring System (CVSS) might allow an attacker to escalate their privileges on a focused system, however requires them to be authenticated first.
CVE-2025-0282 — rated a “critical” 9.0 in CVSS — doesn’t include that very same caveat, permitting for code execution as root with no authentication required. Ivanti disclosed few particulars concerning the precise explanation for the difficulty, however researchers from watchTowr have been in a position to efficiently reverse engineer an exploit after evaluating ICS’s patched and unpatched variations.
In response to Mandiant, UNC5337 started exploiting CVE-2025-0282 in mid-December, deploying the identical “Spawn” household of malware it has utilized in exploits of earlier ICS bugs. These instruments embody:
-
The SpawnAnt installer, which drops its malware colleagues and persists via system upgrades
-
SpawnMole, which facilitates back-and-forth communications with attacker infrastructure
-
SpawnSnail, a passive safe shell (SSH) backdoor
-
SpawnSloth, which tampers with logs to hide proof of malicious exercise
“The threat actor’s malware families demonstrate significant knowledge of the Ivanti Connect Secure appliance,” says Mandiant senior guide Matt Lin. Actually, in addition to UNC5337 and its spawn, researchers additionally noticed two extra unrelated however equally bespoke malware deployed to contaminated units. One — DryHook, a Python script — is designed to steal person credentials off focused units.
The opposite, PhaseJam, is a bash shell script that permits distant and arbitrary command execution. Most inventive, although, is its means to keep up persistence via sleight of hand. If an administrator makes an attempt to improve their system — a course of that might unseat PhaseJam — the malware will as a substitute present them a faux progress bar that simulates every of the 13 steps one would possibly anticipate in a reliable replace. In the meantime, within the background, it prevents the reliable replace from operating, thereby making certain that it lives one other day.
DryHook and PhaseJam may need been the work of UNC5337, Mandiant famous, or one other risk actor altogether.
Time to Replace
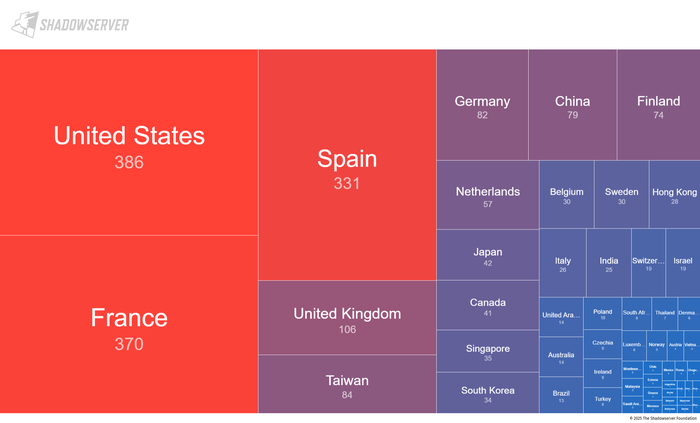
Knowledge from The ShadowServer Basis means that north of two,000 ICS cases may very well be susceptible on the time of writing, with the best focus within the US, France, and Spain.
Supply: The Shadowserver Basis
Ivanti and the Cybersecurity and Infrastructure Safety Company (CISA) have revealed directions for mitigating CVE-2025-0282, emphasizing that community defenders ought to run Ivanti’s built-in Integrity Checker Software (ICT) to hunt out infections, and implement patches instantly.
“We have released a patch addressing vulnerabilities related to Ivanti Connect Secure,” an Ivanti spokesperson tells Darkish Studying. “There has been limited exploitation of one of the vulnerabilities and we are actively working with affected customers. Ivanti’s ICT has been effective in identifying compromise related to this vulnerability. Threat actor exploitation was identified by the ICT on the same day it occurred, enabling Ivanti to respond promptly and rapidly develop a fix. We strongly advise customers to closely monitor their internal and external ICT as part of a robust and layered approach to cybersecurity to ensure the integrity and security of the entire network infrastructure.”
It might be value noting that in contrast to ICS, Coverage Safe and ZTA gateways will not be receiving their patches till Jan. 21. In its safety advisory, Ivanti said that ZTA gateways “cannot be exploited when in production,” and that Coverage Safe is designed to not be Web-facing, decreasing the chance of exploitation by way of CVE-2025-0282 or comparable vulnerabilities.
“It’s important that administrators here are doing the right things,” Marrè says, noting, “That may result in some downtime, which can be disruptive for organizations, which can lead to them putting it off, or not fixing it as thoroughly and as well as they should.”
Lin provides, “We’ve observed organizations that have historically acted promptly in response to these threats did not experience the same negative impacts when compared to organizations that failed to do the same.” He additionally acknowledges, “All the swirl that takes place in the background once one of these patches is announced.
“Safety groups throughout orgs must scramble to not simply patch, but additionally perceive whether or not they’re susceptible, and if that’s the case, do they solely must patch, or have they already been breached? And if they’ve been breached, that begins one other incident response, which creates large workflows throughout firms world wide. It’s vital to not lose sight of the toil and exhaustion that defenders undergo when assessing these situations and never be hyper vital of their preliminary response instances.”