Common hashish model STIIIZY disclosed an information breach this week after hackers breached its point-of-sale (POS) vendor to steal buyer data, together with authorities IDs and buy data.
STIIIZY is a a California-based hashish model identified for its pod-based vaporizers and a wide range of hashish merchandise, together with flower, edibles, THC concentrates, and extracts.
In an information breach notification revealed earlier this week, STIIIZY says it first suffered an information breach on November 20 when notified by its POS vendor.
“On November 20, 2024, we were notified by a vendor of point-of-sale processing services for some of our retail locations that accounts with their organization had been compromised by an organized cybercrime group,” reads the information breach notification revealed to STIIIZY’s web site.
“An investigation conducted by the vendor revealed that personal information relating to certain STIIIZY customers processed by the vendor was acquired by the threat actors on or around October 10, 2024 – November 10, 2024.”
As a part of the breach, the risk actors stole a variety of delicate buyer data, together with driver’s license data, passport numbers, pictures, and transaction histories.
“The incident impacted information contained on government-issued identification cards, including drivers’ licenses and medical cannabis cards, as well as information related to transactions with our dispensaries,” warns the corporate.
“The categories of information compromised include name, address, date of birth, age, drivers’ license number, passport number, photograph, the signatures appearing on a government ID card, medical cannabis cards, transaction histories, and other personal information. Not all of this information was affected for each impacted individual.”
STIIIZY says their investigation signifies that the breach solely affected clients who made purchases on the following shops:
- STIIIZY Union Sq.: 180 O’Farrell Avenue, San Francisco, CA
- STIIIZY Mission: 3326 Mission Avenue, San Francisco, CA
- STIIIZY Alameda: 1528 Webster St., Alameda, CA
- STIIIZY Modesto: 426 McHenry Ave., Modesto, CA
The corporate says they’ve carried out extra safety measures to guard buyer information and can provide free credit score monitoring providers to these impacted.
As a result of delicate nature of the stolen information, impacted clients are additionally suggested to watch their credit score historical past for fraudulent accounts opened below their identify and to be looking out for focused phishing assaults.
Whereas STIIIZY has not shared any particulars on the seller and the way the information was stolen, a ransomware gang generally known as “Everest” claimed in November to have breached the corporate and stolen the private information and IDs of 422,075 clients.
BleepingComputer contacted STIIIZY with additional questions concerning the breach and can replace this story if we hear again.
Everest ransomware claimed assault
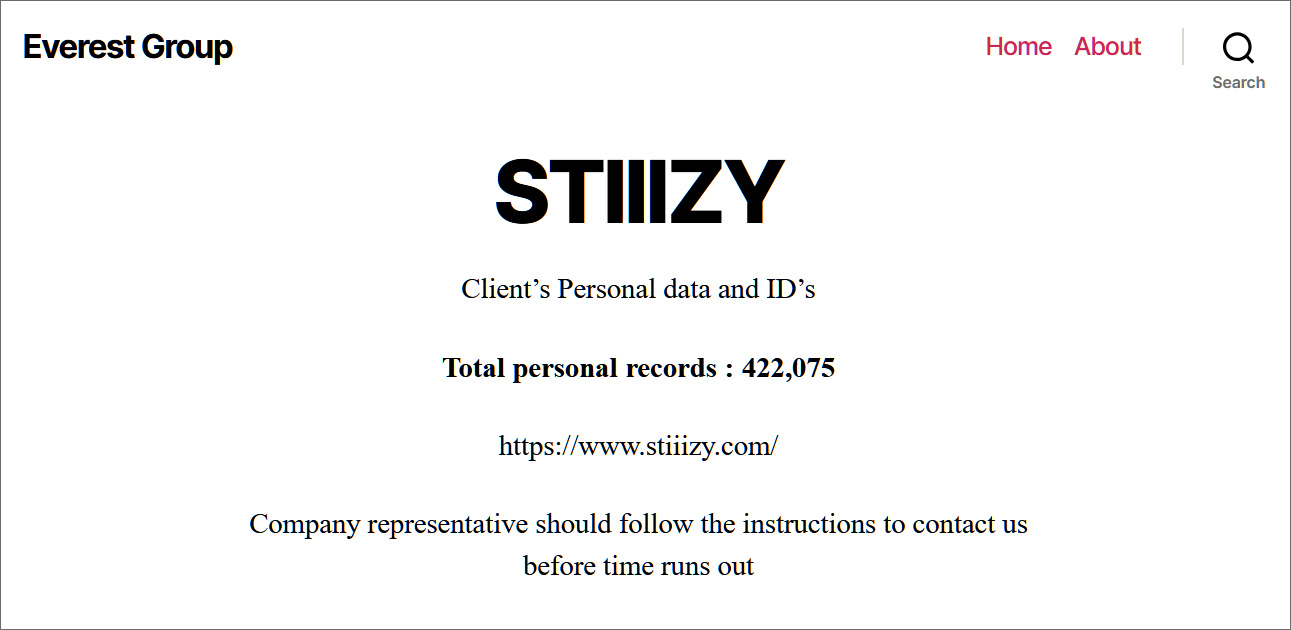
Supply: BleepingComputer
The Everest gang additionally shared screenshots of the allegedly stolen information, which included scans of driver’s licenses, buyer profiles, medical marijuana playing cards, buyer profiles, and firm paperwork.
The Everest ransomware operation launched in 2020 and has had an fascinating development of malicious exercise.
When first launched, the group primarily breached company networks to steal information and extort victims on its information leak web site.
Over time, the risk actors launched ransomware into their assaults to not solely steal information but additionally encrypt the corporate’s information in double-extortion assaults.
The risk actors are additionally identified for appearing as preliminary entry brokers, promoting entry to company networks to different risk actors to carry out their very own assaults.
In August, the U.S. Division of Well being and Human Providers warned that the Everest ransomware gang was more and more focusing on the healthcare business.
