Secrets and techniques are supposed to be hidden or, on the very least, solely identified to a particular and restricted set of people (or methods). In any other case, they aren’t actually secrets and techniques. In private life, a secret revealed can injury relationships, result in social stigma, or, on the very least, be embarrassing. In a developer’s or software safety engineer’s skilled life, the results of exposing secrets and techniques can result in breaches of safety, information leaks, and, nicely, even be embarrassing. And whereas there are instruments out there for detecting supply code and code repositories, there are few choices for figuring out secrets and techniques in plain textual content, paperwork, emails, chat logs, content material administration methods, and extra.
What Are Secrets and techniques?
Within the context of functions, secrets and techniques are delicate data reminiscent of passwords, API keys, cryptographic keys, and different confidential information that an software must operate however shouldn’t be uncovered to unauthorized customers. Secrets and techniques are usually saved securely and accessed programmatically by the applying when wanted.
Using secrets and techniques is a vital side of securing functions. Unauthorized entry to those delicate items of data can result in safety breaches and different malicious actions. To guard secrets and techniques, builders, system directors, and safety engineers use quite a lot of safety methods reminiscent of encryption, safe storage, and entry management mechanisms to make sure that solely licensed customers can entry them. Moreover, they implement greatest practices reminiscent of often rotating passwords and keys and limiting the scope of entry to secrets and techniques to solely what is important for the applying to operate.
Secrets and techniques within the Software program Provide Chain
Secrets and techniques are a essential element of software program provide chain safety, which encompasses collaboration to deployment, and every thing in between.
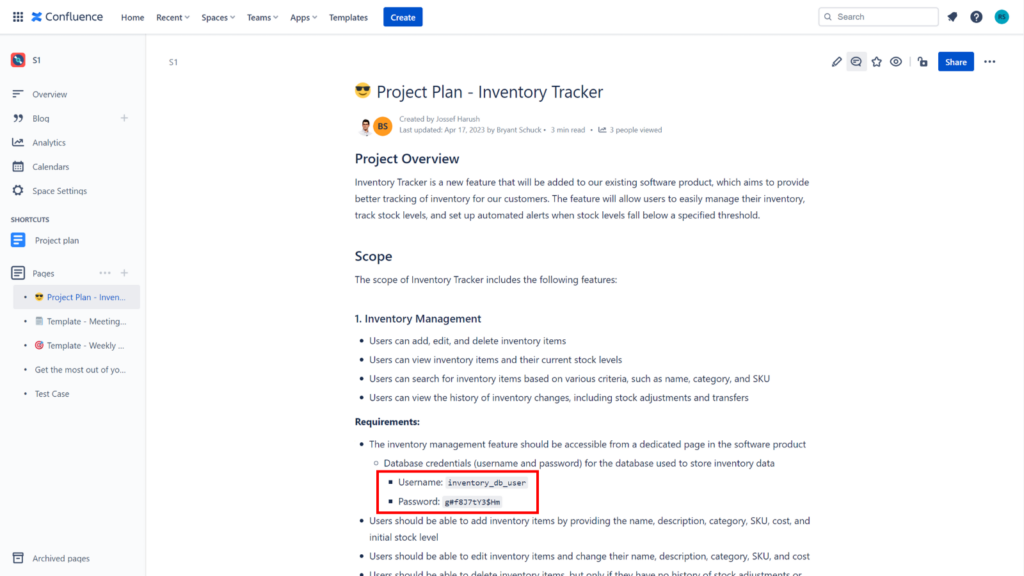
For instance, Confluence is a well-liked collaboration device utilized by many organizations to retailer and share data and is usually a widespread supply of secret leaks. It’s because Confluence permits anybody with entry to a web page to view its contents, together with delicate data like API keys and passwords (see picture under). Moreover, customers could by chance expose secrets and techniques by copy-pasting them into Confluence pages or by together with them in code snippets or in saved configuration information.
A secret, reminiscent of an entry key or password, is commonly the one factor standing between an attacker and delicate information or methods. Due to this fact, it is important to maintain these secrets and techniques confidential and safe. When secrets and techniques are compromised, it could result in a devastating information breach, which may trigger vital monetary and reputational injury to a company.
Secrets and techniques are a frequent goal of software program provide chain assaults. Attackers usually goal secrets and techniques to realize entry to enterprise methods, information, or servers. They’ll simply acquire these secrets and techniques if they’ve mistakenly leaked to a public supply. Safeguarding secrets and techniques in software program provide chain safety is important to make sure that attackers can not exploit them to compromise enterprise methods and information. Correct secret administration will help forestall unauthorized entry to essential methods and information, defending organizations from provide chain assaults.
How Do You Maintain Secrets and techniques Secret?
To guard in opposition to secrets and techniques being leaked, you’ll be able to make use of the next practices:
- Use setting variables to retailer secrets and techniques: as a substitute of hardcoding secrets and techniques in your code, retailer them in setting variables. This makes it simpler to handle secrets and techniques and ensures that they don’t seem to be by chance dedicated to a code repository.
- Use a .gitignore file: Create a .gitignore file to exclude information that comprise secrets and techniques from being tracked by Git. This can forestall delicate data from being by chance dedicated to a code repository. If following #1 above, be sure if secrets and techniques are saved in an setting variable file, that file is laid out in .gitignore.
- Use a secrets and techniques administration device: a secrets and techniques administration device will help securely retailer and handle software or system secrets and techniques. This ensures that secrets and techniques are encrypted and solely accessible by licensed customers.
- Use encryption: encrypt secrets and techniques earlier than storing them in code repositories. This offers an additional layer of safety and makes it tougher for attackers to entry delicate data.
- Use two-factor authentication (2FA): Allow 2FA for code repositories to forestall unauthorized entry. This provides an additional layer of safety and makes it tougher for attackers to realize unauthorized entry to a code repository.
By following these greatest practices, you’ll be able to defend yourselves from by chance exposing delicate data in our code repositories and supply management managers. However what about different methods, reminiscent of content material administration methods, plain textual content paperwork, emails, chat logs, and different digital property not saved in a repository?
Introducing Too Many Secrets and techniques by Checkmarx
Too Many Secrets and techniques (2MS) is an open supply undertaking devoted to serving to individuals defend their delicate data like passwords, credentials, and API keys from showing in public web sites and communication providers. 2MS helps Confluence in the present day and we are going to quickly be including assist for Discord. As well as, it’s simply extensible to different communication or collaboration platforms as nicely.
Putting in and working 2MS is extraordinarily fast and easy. Inbuilt Go, all you want is to clone the repository, construct the undertaking, and run the binary in opposition to your platform. Under is the record of instructions I used to stand up and working on OSX (utilizing Bash 5.1.16):
# brew set up go
# git clone https://github.com/Checkmarx/2ms.git
# cd 2ms
# go construct
# ./2ms –confluence https://<MyConfluence>.atlassian.internet/wiki –confluence-spaces <MySpace> –confluence-username <MyUsername> –confluence-token <MyToken>
2MS is constructed on a secrets and techniques detection engine (at present gitleaks) and consists of varied plugins to work together with standard platforms. This implies anybody within the open supply group can contribute, enhance, and lengthen 2MS fairly simply.
Study Extra
We imagine that by working collectively, we are able to create a safer digital world. To be taught extra or obtain the undertaking your self, head over to the https://github.com/Checkmarx/2ms, out there on GitHub.