SUMMARY
- EC2 Grouper Recognized: Researchers discovered EC2 Grouper exploiting AWS credentials and instruments utilizing distinct patterns like “ec2group12345.”
- Credential Compromise: They primarily get hold of credentials from code repositories tied to legitimate accounts.
- API Reliance: The group avoids handbook exercise, utilizing APIs for reconnaissance and useful resource creation.
- Detection Challenges: Indicators like naming conventions and consumer brokers are unreliable for constant detection.
- Safety Suggestions: Use CSPM instruments, monitor for credential misuse, and detect uncommon API exercise to mitigate dangers.
Cloud environments are continually underneath assault, with subtle menace actors using varied methods to achieve unauthorized entry. One such actor, dubbed EC2 Grouper, has change into a notable adversary for safety groups.
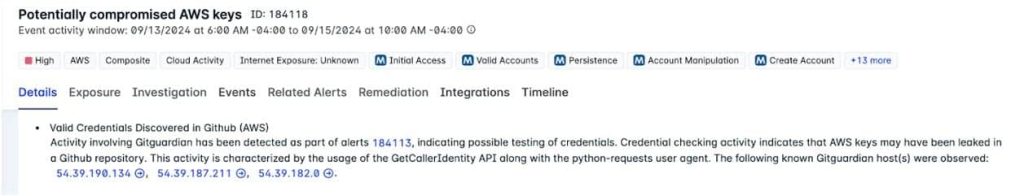
Based on the newest analysis from Fortinet’s FortiGuard Labs Menace Analysis group, this group is characterised by its constant use of AWS instruments and a singular safety group naming conference in its assaults. Researchers tracked this actor in a number of dozen buyer environments on account of comparable consumer brokers and safety group naming conventions.
The newest revelation comes amid rising exploitation of AWS infrastructure by high hacker teams. In December 2024, studies revealed that ShinyHunters and the Nemesis Group collaborated to focus on misconfigured servers, notably AWS S3 Buckets.
EC2 Grouper sometimes initiates assaults by leveraging AWS instruments like PowerShell, usually using a particular consumer agent string. Moreover, the group constantly creates safety teams with naming patterns like “ec2group,” “ec2group1,” “ec2group12,” and so forth. Additionally, they ceaselessly use code repositories to amass credentials of their cloud assaults, usually originating from legitimate accounts. This technique is believed to be the first technique of credential acquisition.
Additional probing revealed that Grouper makes use of APIs for reconnaissance, safety group creation, and useful resource provisioning, avoiding direct actions like inbound entry configuration.
Whereas these indicators can present preliminary clues, they’re usually inadequate for dependable menace detection, researcher Chris Corridor famous within the weblog put up, shared with hackread.com. That’s as a result of relying solely on these indicators might be deceptive. Attackers can simply modify their consumer brokers and should deviate from their regular naming conventions.
Researchers didn’t observe calls to AuthorizeSecurityGroupIngress, which is important to configure inbound entry to EC2 launched with the safety group, however they noticed CreateInternetGateway and CreateVpc for distant entry.
Furthermore, no actions have been primarily based on goals or handbook exercise in a compromised cloud setting. EC2 Grouper could also be selective of their escalation or compromised accounts have been detected and quarantined earlier than they escalated.
Nonetheless, researchers word that by analysing alerts like credential compromise and API utilization, safety groups can develop a dependable detection technique and assist organizations defend in opposition to subtle adversaries like EC2 Grouper. They counsel {that a} more practical strategy could be monitoring for suspicious exercise associated to authentic secret scanning providers to determine potential credential compromises, that are the first supply of entry for EC2 Grouper.
To remain protected, organizations should additionally make the most of Cloud Security Posture Administration (CSPM) instruments to observe and assess your cloud setting’s safety posture constantly. Implementing anomaly detection methods to determine uncommon behaviour throughout the cloud setting, equivalent to surprising API calls, useful resource creation, or knowledge exfiltration may assist.
RELATED TOPICS
- Hackers Use Faux PoCs on GitHub to Steal AWS Keys
- New APT Group “Unfading Sea Haze” Hits Navy Targets
- TA866 Linked to WarmCookie Malware in Espionage Marketing campaign
- Builder.ai Database Misconfiguration Exposes 1.29TB of Information
- Russian Cozy Bear Phish Essential Sectors with Microsoft, AWS Lures