The Russian hacking group tracked as APT29 (aka “Midnight Blizzard”) is utilizing a community of 193 distant desktop protocol proxy servers to carry out man-in-the-middle (MiTM) assaults to steal information and credentials and to put in malicious payloads.
The MiTM assaults utilized the PyRDP purple workforce proxy instrument to scan the victims’ filesystems, steal information within the background, and remotely execute rogue purposes on the breached setting.
Pattern Micro, which tracks the menace actors as ‘Earth Koshchei,’ studies that this marketing campaign targets authorities and navy organizations, diplomatic entities, IT and cloud service suppliers, and telecommunication and cybersecurity corporations.
The domains registered for the marketing campaign recommend that APT29 focused entities primarily within the U.S., France, Australia, Ukraine, Portugal, Germany, Israel, France, Greece, Turkey, and the Netherlands.
Utilizing PyRDP for MitM assaults
Distant Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that permits customers to remotely entry and management one other pc over a community. It’s generally used for distant administration, technical help, and connecting to programs in enterprise environments.
In October 2024, Amazon and CERT-UA printed studies confirming that APT29 is tricking victims into connecting to rogue RDP servers after working a file connected to phishing emails.
As soon as the connection is about up, native sources, together with disks, networks, printers, the clipboard, audio units, and COM ports, are shared with the attacker-controlled RDP server, enabling them unconditional entry to delicate info.
Pattern Micro’s newest report reveals extra particulars about this exercise after figuring out 193 RDP proxy servers that redirected connections to 34 attacker-controlled backend servers, permitting the attackers to observe and intercept RDP classes.
The hackers use a Python “man-in-the-middle” MitM purple workforce instrument referred to as PyRDP to intercept all communication between the sufferer and the distant session, permitting the connection to seem legit.
The instrument permits the attackers to log plaintext credentials or NTLM hashes, steal clipboard information, steal transferred information, steal information from shared drives within the background, and run console or PowerShell instructions on new connections.
The researchers clarify that this method was first described by Mike Felch in 2022, who could have impressed APT29’s ways.
“Upon establishing the connection, the rogue server mimics the behavior of a legitimate RDP server and exploits the session to carry out various malicious activities,” explains Pattern Micro
“A primary attack vector involves the attacker deploying malicious scripts or altering system settings on the victim’s machine.”
“Moreover, the PyRDP proxy facilitates entry to the sufferer’s file system, enabling the attacker to browse directories, learn or modify information, and inject malicious payloads.
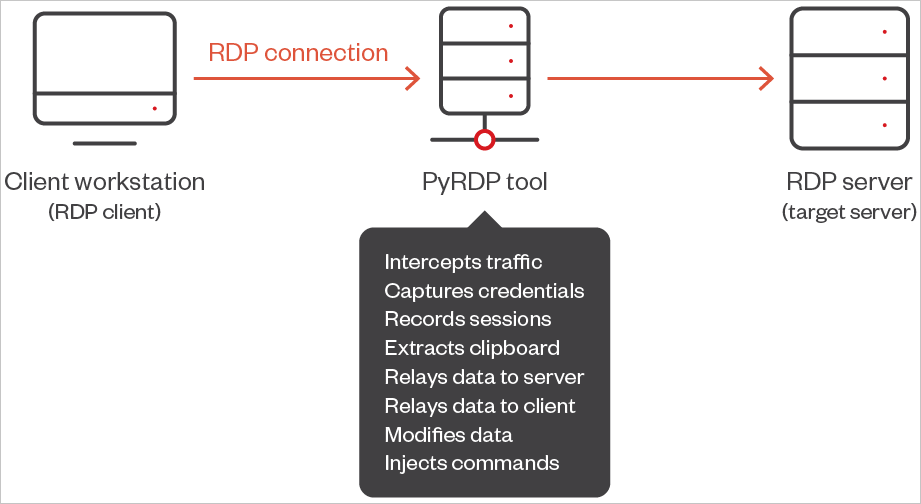
Supply: Pattern Micro
Among the many malicious configurations Pattern Micro analyzed, there’s additionally one which serves the person with a deceptive AWS Safe Storage Connection Stability Check connection request.
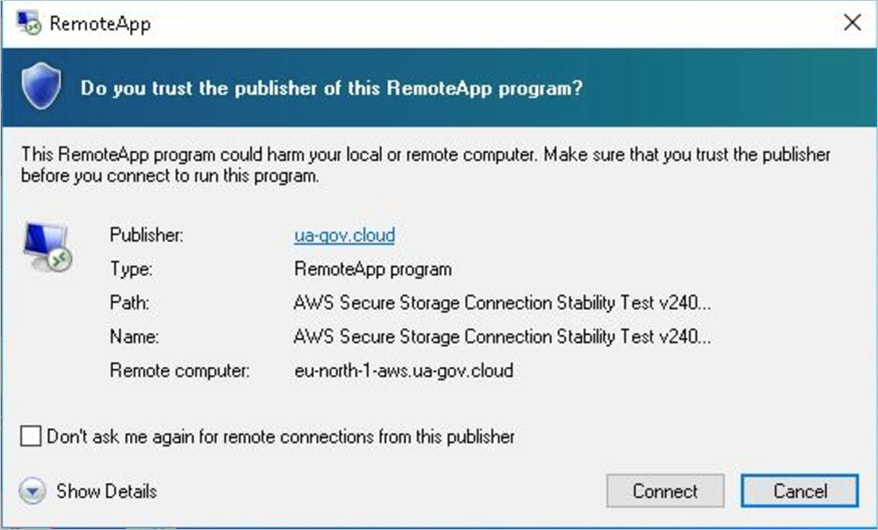
Supply: Pattern Micro
Concerning APT29’s evasion, the researchers report that the Russian hackers use a mix of economic VPN merchandise accepting cryptocurrency funds, TOR exit nodes, and residential proxy providers to obscure the IP addresses of the rogue RDP servers.
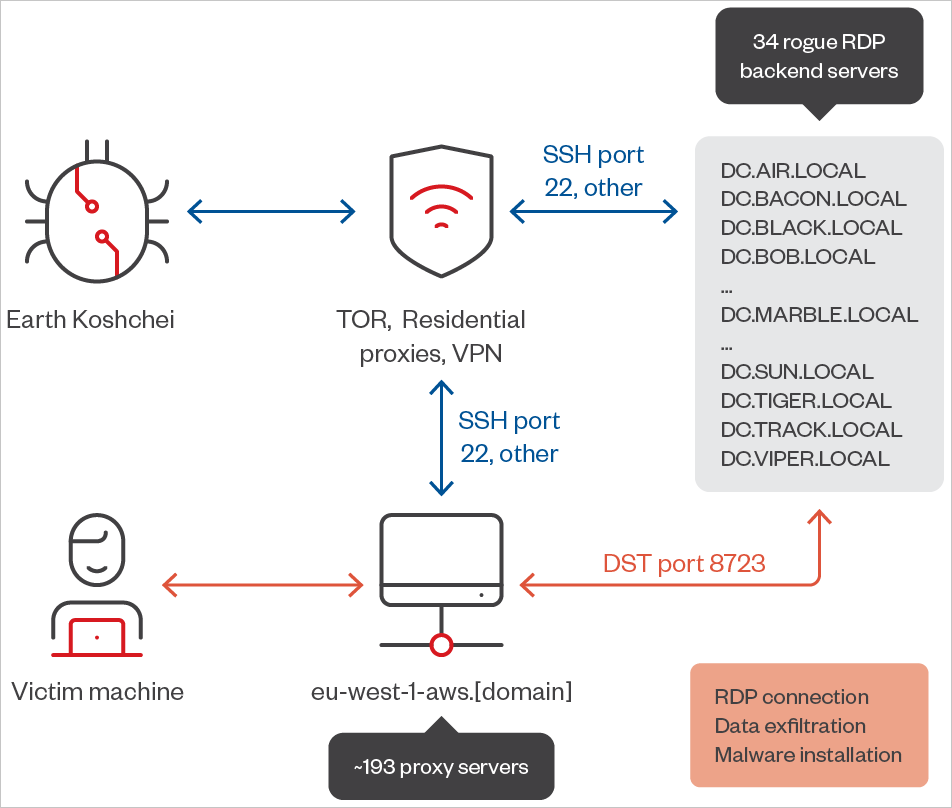
Supply: Pattern Micro
Defending in opposition to rogue RDP configurations requires a great response to malicious emails, which, on this case, had been despatched from legit addresses compromised earlier than the marketing campaign’s launch.
Much more necessary, Home windows customers ought to solely make RDP connections to identified, trusted servers and by no means make the most of RDP connections despatched by way of e-mail attachments.
