abstract
- Phishing Assault: Cybercriminals use pretend model collaboration emails to focus on YouTube creators.
- Malware Disguise: Malicious recordsdata are hidden in password-protected attachments like contracts or promotional supplies.
- Cloud Internet hosting: Attackers leverage platforms like OneDrive to host malware, including a layer of credibility.
- Delicate Information Theft: Malware steals login credentials, monetary info, and grants distant entry.
- Vast Attain: Over 200,000 creators focused globally, with 1000’s of phishing emails despatched through automated instruments.
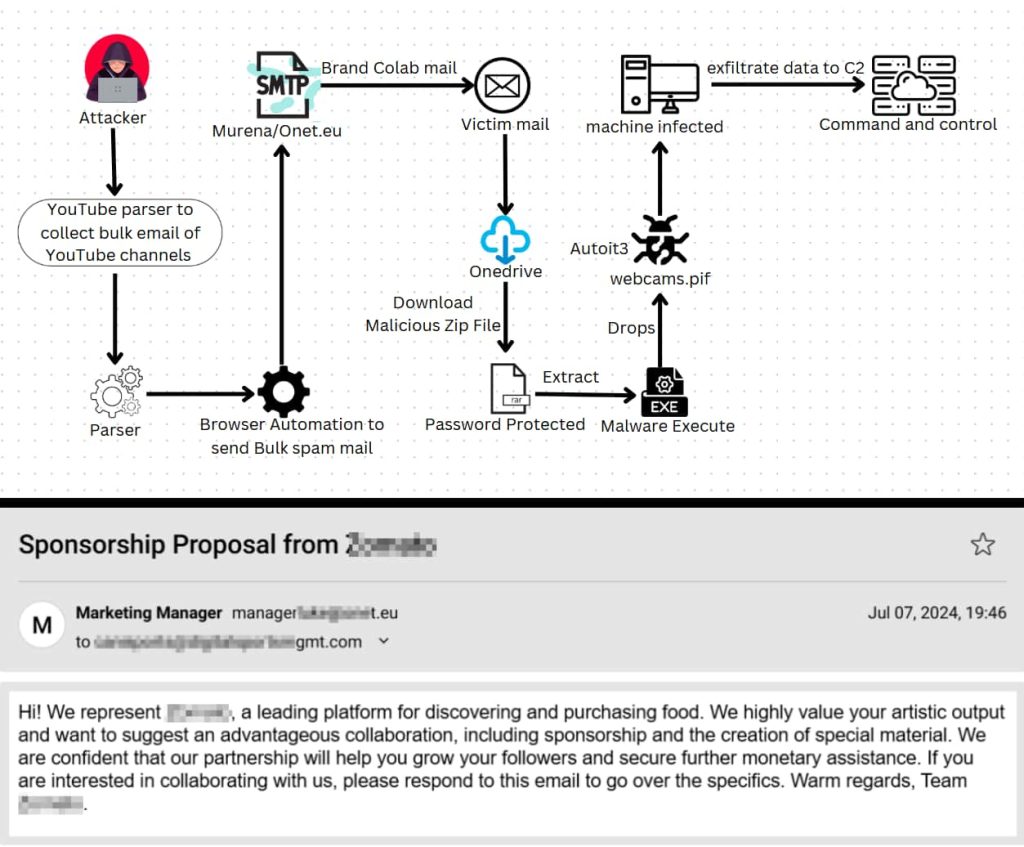
CloudSEK’s menace analysis group has disclosed particulars of a complicated new phishing marketing campaign focusing on YouTube creators. In accordance with CloudSEK’s investigation, shared completely with Hackread.com, scammers are utilizing pretend model collaboration emails to steal accounts and unfold scams to hundreds of thousands of followers.
Marketing campaign Evaluation
Report creator Mayank Sahariya notes that this refined phishing marketing campaign entails impersonating trusted manufacturers to distribute malware via pretend collaboration affords.
Attackers start by scraping e-mail addresses from YouTube channels, doubtless utilizing a specialised parser instrument. This permits them to focus on creators and organizations immediately. With e-mail addresses in hand, attackers use browser automation instruments to ship bulk phishing emails.
Subsequent, the attackers ship cleverly crafted emails that look like respectable enterprise proposals from well-known manufacturers. These emails entice recipients with profitable collaboration offers and embody engaging compensation buildings primarily based on subscriber depend. The malware is cleverly disguised inside attachments reminiscent of Phrase paperwork, PDFs, or Excel recordsdata, typically masquerading as promotional supplies, contracts, or enterprise proposals.
“At the end of the email, the threat actor includes instructions and a OneDrive link to access a zip file containing the agreement and promotional materials, secured with the password,” the report learn.
The extracted recordsdata reveal 4 recordsdata, together with Digital Settlement Phrases and Funds Complete Analysis.exe, which is a malicious payload. As soon as downloaded and extracted, the zip file unleashes a malicious script disguised as a innocent file format, reminiscent of “webcams.pif.” This script leverages AutoIt3 automation software program to execute additional malware hidden throughout the archive.
To additional bypass detection, the attackers host these malicious attachments on cloud storage platforms like OneDrive (kind this ID- [email protected] created on August 15, 2024), protected by passwords. This tactic provides a layer of legitimacy, as recipients may count on collaboration agreements and promotional supplies to be password-protected.
As soon as a curious YouTuber downloads the attachment, the malware installs itself on the sufferer’s system. This malware is designed to steal delicate info, together with login credentials, monetary knowledge, and mental property. In some circumstances, it may even grant distant entry to the attacker, compromising your complete system.
Who’re the Targets?
In accordance with CloudSec’s weblog submit, this world marketing campaign primarily targets companies and people concerned in advertising, gross sales, and government positions. These people usually tend to have interaction with model collaborations and promotions, making them prime targets for this phishing scheme.
To date, this marketing campaign has focused over 2 lakh YouTube creators, involving 500-1,000 phishing emails despatched from a single e-mail account and round 340+ SMTP servers have been weaponized for assaults.
To remain protected, YouTube creators needs to be cautious of unsolicited collaboration affords, particularly password-protected attachments. At all times double-check e-mail addresses, and speak to manufacturers immediately to verify the legitimacy of collaboration affords. Additionally, keep away from downloading attachments from unknown senders, even when password-protected to guard worthwhile knowledge.