Russian cyberspies Gamaredon has been found utilizing two Android spy ware households named ‘BoneSpy’ and ‘PlainGnome’ to spy on and steal knowledge from cell units.
Based on Lookout, which found the 2 malware households, BoneSpy has been energetic since 2021, whereas PlainGnome emerged in 2024. Each goal Russian-speaking people in former Soviet states.
Gamaredon (aka “Shuckworm”) is believed to be a part of Russia’s Federal Safety Company (FSB), and its operations are intently tied to the nation’s nationwide geopolitical pursuits.
Though the menace group has used numerous malware instruments, BoneSpy and PlainGnome are the primary documented instances of Gamaredon malware concentrating on cell units, particularly Android.
From open-source to customized malware
BoneSpy, usually delivered through trojanized Telegram apps or by impersonating Samsung Knox, was primarily based on the open-source ‘DroidWatcher‘ surveillance app, which dates again to 2013.
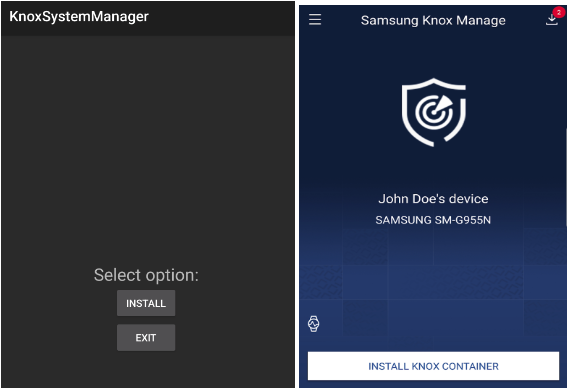
Supply: BleepingComputer
Lookout says growth work on BoneSpy peaked between January and October 2022, stabilizing to the next capabilities:
- Collects SMS messages, together with sender, content material, and timestamps
- Data ambient audio and telephone name conversations
- Captures GPS and cell-based location knowledge
- Takes photos utilizing the digicam and captures system screenshots
- Accesses consumer’s internet searching historical past
- Extracts names, numbers, emails, and name particulars from the contact checklist and name logs
- Accesses clipboard content material
- Reads system notifications
PlainGnome is a more recent, customized Android surveillance malware that doesn’t use the codebase of a beforehand identified undertaking. Lookout noticed important evolution in its code from January to October this 12 months, indicating energetic growth.
The brand new malware makes use of a two-stage set up course of separating the dropper and payload, which makes it stealthier and extra versatile.
PlainGnome options all the info assortment capabilities of BoneSpy but in addition integrates superior options like Jetpack WorkManager to exfiltrate knowledge solely when the system is idle, decreasing detection dangers.
The malware helps a recording mode that prompts solely when the system is idle and the display screen is off to keep away from tipping off victims by way of microphone activation indicators that they’re being spied on.
Regardless of the elevated sophistication in surveillance operations, Lookout notes that the spy ware doesn’t at present function any type of code obfuscation, so evaluation rapidly revealed its true nature.
Upon launch, it requests the approval of harmful permissions like entry to SMS, contacts, name logs, and cameras. Nevertheless, given its masking as a communication app, victims could also be tricked into approving the request.
Lookout notes that neither BoneSpy nor PlainGnome have been ever discovered on Google Play, in order that they’re most certainly downloaded from web sites victims are directed to following social engineering. This method matches Gamaredon’s slender concentrating on scope.
The researcher’s report highlights Gamaredon’s growing give attention to Android units, showcasing the group’s evolving techniques to broaden its surveillance capabilities to cell units, that are more and more utilized in all elements of our lives and making them useful targets.
Google has confirmed to BleepingComputer that Google Play Defend routinely protects in opposition to identified variations of this malware.
