Iranian menace actors are using a brand new malware named IOCONTROL to compromise Web of Issues (IoT) units and OT/SCADA methods utilized by vital infrastructure in Israel and america.
Focused units embody routers, programmable logic controllers (PLCs), human-machine interfaces (HMIs), IP cameras, firewalls, and gas administration methods.
The malware’s modular nature makes it able to compromising a broad spectrum of units from numerous producers, together with D-Hyperlink, Hikvision, Baicells, Crimson Lion, Orpak, Phoenix Contact, Teltonika, and Unitronics.
Claroty’s Team82 researchers, who’ve found and sampled IOCONTROL for evaluation, report that it is a nation-state cyberweapon that may trigger vital disruptions in vital infrastructure.
Given the continued geopolitical battle, IOCONTROL is at the moment used to focus on Israel and U.S. methods, like Orpak and Gasboy gas administration methods.
The software is reportedly linked to an Iranian hacking group generally known as CyberAv3ngers, who have proven curiosity in attacking industrial methods prior to now. OpenAI additionally not too long ago reported that the menace group makes use of ChatGPT to crack PLCs, develop customized bash and Python exploit scripts, and plan its post-compromise exercise.
IOCONTROL assaults
Claroty extracted malware samples from a Gasboy gas management system, particularly the machine’s fee terminal (OrPT), however the researchers have no idea exactly how the hackers contaminated it with IOCONTROL.
Inside these units, IOCONTROL may management pumps, fee terminals, and different peripheral methods, probably inflicting disruption or knowledge theft.
The menace actors have claimed to compromise 200 fuel stations in Israel and the U.S. on Telegram, which aligns with Claroty’s findings.
These assaults occurred in late 2023, across the similar time because the defacement of Unitronics Imaginative and prescient PLC/HMI units in water therapy amenities, however the researchers report that new campaigns emerged in mid-2024.
As of December 10, 2024, the UPX-packed malware binary is detected by not one of the 66 VirusTotal antivirus engines.

Supply: Claroty
Malware capabilities
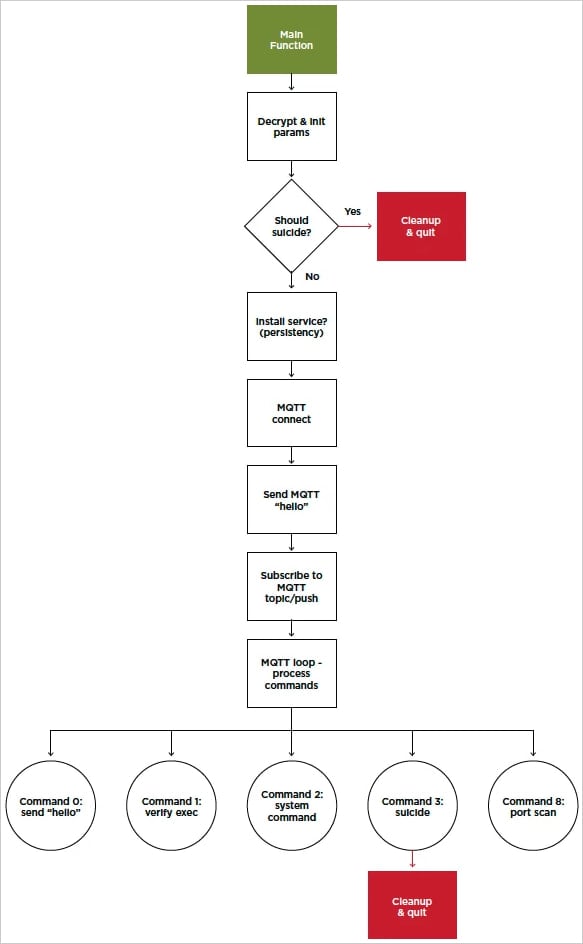
The malware, which is saved within the ‘/usr/bin/’ listing below the title ‘iocontrol.’ makes use of a modular configuration to adapt to completely different distributors and machine varieties, concentrating on a broad spectrum of system architectures.
It makes use of a persistence script (‘S93InitSystemd.sh’) to execute the malware course of (‘iocontrol’) upon system boot, so restarting the machine doesn’t deactivate it.
It makes use of the MQTT protocol by means of port 8883 to speak with its command and management (C2) server, which is a normal channel and protocol for IoT units. Distinctive machine IDs are embedded into the MQTT credentials for higher management.
DNS over HTTPS (DoH) is used to resolve the C2 domains whereas evading community site visitors monitoring instruments, and the malware’s configuration is encrypted utilizing AES-256-CBC.
The instructions IOCONTROL helps are the next:
- Ship “hello”: Studies detailed system info (e.g., hostname, present consumer, machine mannequin) to the C2.
- Test exec: Confirms the malware binary is correctly put in and executable.
- Execute command: Runs arbitrary OS instructions through system calls and reviews output.
- Self-delete: Removes its personal binaries, scripts, and logs to evade detection.
- Port scan: Scans specified IP ranges and ports to establish different potential targets.
The above instructions are executed utilizing system calls retrieved dynamically from the ‘libc’ library, and the outputs are written to non permanent recordsdata for reporting.
Supply: Claroty
Given IOCONTROL targets’ function in vital infrastructure and the group’s steady exercise, Claroty’s report constitutes a beneficial useful resource for defenders to assist establish and block the menace.
The whole indicators of compromise (IoC) are listed on the backside of the report.
