Cleo has launched safety updates for a zero-day flaw in its LexiCom, VLTransfer, and Concord software program, at the moment exploited in knowledge theft assaults.
In October, the corporate patched a pre-auth distant code execution vulnerability (CVE-2024-50623) in its managed file switch software program and really useful that “all customers upgrade immediately.”
Huntress safety researchers first noticed proof of assaults focusing on absolutely patched Cleo software program on December 3. This was adopted by a notable enhance in exercise on Sunday, December 8, after attackers rapidly found a CVE-2024-50623 bypass (with no CVE-ID) that lets them import and execute arbitrary bash or PowerShell instructions by exploiting the default Autorun folder settings.
This zero-day bug is now being exploited in ongoing assaults linked by cybersecurity knowledgeable Kevin Beaumont to the Termite ransomware gang, which lately claimed the breach of software program as a service (SaaS) supplier Blue Yonder.
“This vulnerability is being actively exploited in the wild and fully patched systems running 5.8.0.21 are still exploitable,” Huntress warned on Monday.
“We strongly recommend you move any internet-exposed Cleo systems behind a firewall until a new patch is released.”
Shodan at the moment tracks 421 Cleo servers worldwide, 327 of that are in the USA. Macnica risk researcher Yutaka Sejiyama additionally discovered 743 Cleo servers accessible on-line (379 working Concord software program, 124 VLTrader, and 240) LexiCom).

Patches out there to dam Malichus malware assaults
Right now, Cleo launched patches to dam ongoing assaults and urged clients to improve to model 5.8.0.24 as quickly as potential to safe Web-exposed servers susceptible to breach makes an attempt.
“Cleo strongly advises all customers to immediately upgrade instances of Harmony, VLTrader, and LexiCom to the latest released patch (version 5.8.0.24) to address additional discovered potential attack vectors of the vulnerability,” the firm stated. “After applying the patch, errors are logged for any files found at startup related to this exploit, and those files are removed,” it added.
Cleo advises those that can not instantly improve to disable the Autorun function by going into the System Choices and clearing out the Autorun listing (this won’t block incoming assaults however will cut back the assault floor).
Risk actors exploited the now-patched to deploy an encoded Java Archive (JAR) payload [VirusTotal] that’s half of a bigger Java-based post-exploitation framework, as Rapid7 discovered whereas investigating the assaults.
Huntress additionally analyzed the malware (now named Malichus) and stated it was solely deployed on Home windows gadgets though it additionally comes with Linux help. In line with Binary Protection ARC Labs, malware operators can use Malichus for file transfers, command execution, and community communication.
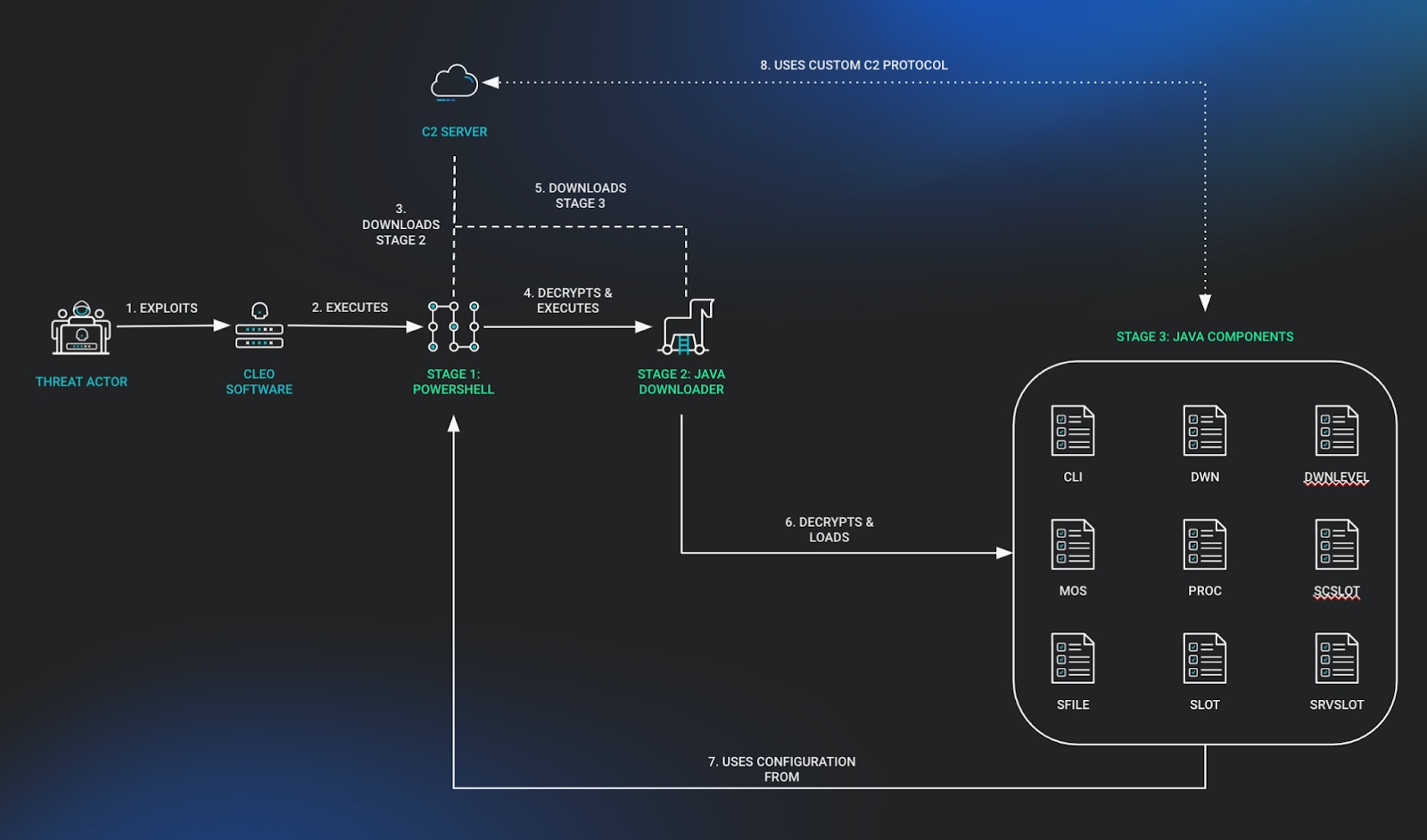
Thus far, Huntress found at the very least ten firms whose Cleo servers have been hacked in these ongoing assaults and stated there are different potential victims. Sophos has additionally discovered indicators of compromise on over 50 Cleo hosts.
“All observed impacted customers have a branch or operate within the North Americas, primarily the US. We note the majority of observed affected customers are retail organizations,” Sophos stated.
These assaults are similar to Clop knowledge theft assaults focusing on zero-days in MOVEit Switch, GoAnywhere MFT, and Accellion FTA in recent times.
