A important safety flaw impacting the LayerSlider plugin for WordPress may very well be abused to extract delicate info from databases, comparable to password hashes.
The flaw, designated as CVE-2024-2879, carries a CVSS rating of 9.8 out of a most of 10.0. It has been described as a case of SQL injection impacting variations from 7.9.11 by means of 7.10.0.
The difficulty has been addressed in model 7.10.1 launched on March 27, 2024, following accountable disclosure on March 25. “This update includes important security fixes,” the maintainers of LayerSlider mentioned of their launch notes.
LayerSlider is a visible net content material editor, a graphic design software program, and a digital visible results that permits customers to create animations and wealthy content material for his or her web sites. In response to its personal web site, the plugin is used by “millions of users worldwide.”
The flaw found within the instrument stems from a case of inadequate escaping of person equipped parameters and the absence of wpdb::put together(), enabling unauthenticated attackers to append extra SQL queries and glean delicate info, Wordfence mentioned.
That having mentioned, the best way the question is structured limits the assault floor to a time-based method the place an adversary would wish to look at the response time of every request to steal info from the database.
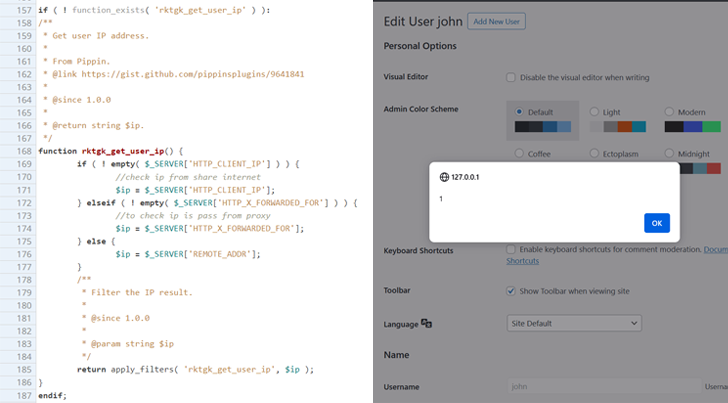
The event follows the invention of an unauthenticated saved cross-site scripting (XSS) flaw within the WP-Members Membership Plugin (CVE-2024-1852, CVSS rating: 7.2) that would facilitate the execution of arbitrary JavaScript code. It has been resolved in model 3.4.9.3.
The vulnerability, as a result of inadequate enter sanitization and output escaping, “makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page which is the edit users page,” the WordPress safety firm mentioned.
Ought to the code be executed within the context of an administrator’s browser session, it may be used to create rogue person accounts, redirect web site guests to different malicious websites, and perform different assaults, it added.
Over the previous few weeks, safety vulnerabilities have additionally been disclosed in different WordPress plugins comparable to Tutor LMS (CVE-2024-1751, CVSS rating: 8.8) and Contact Kind Entries (CVE-2024-2030, CVSS rating: 6.4) that may very well be exploited for info disclosure and injecting arbitrary net scripts, respectively.