A novel phishing assault abuses Microsoft’s Phrase file restoration function by sending corrupted Phrase paperwork as e mail attachments, permitting them to bypass safety software program resulting from their broken state however nonetheless be recoverable by the applying.
Risk actors continuously search for new methods to bypass e mail safety software program and land their phishing emails in targets’ inboxes.
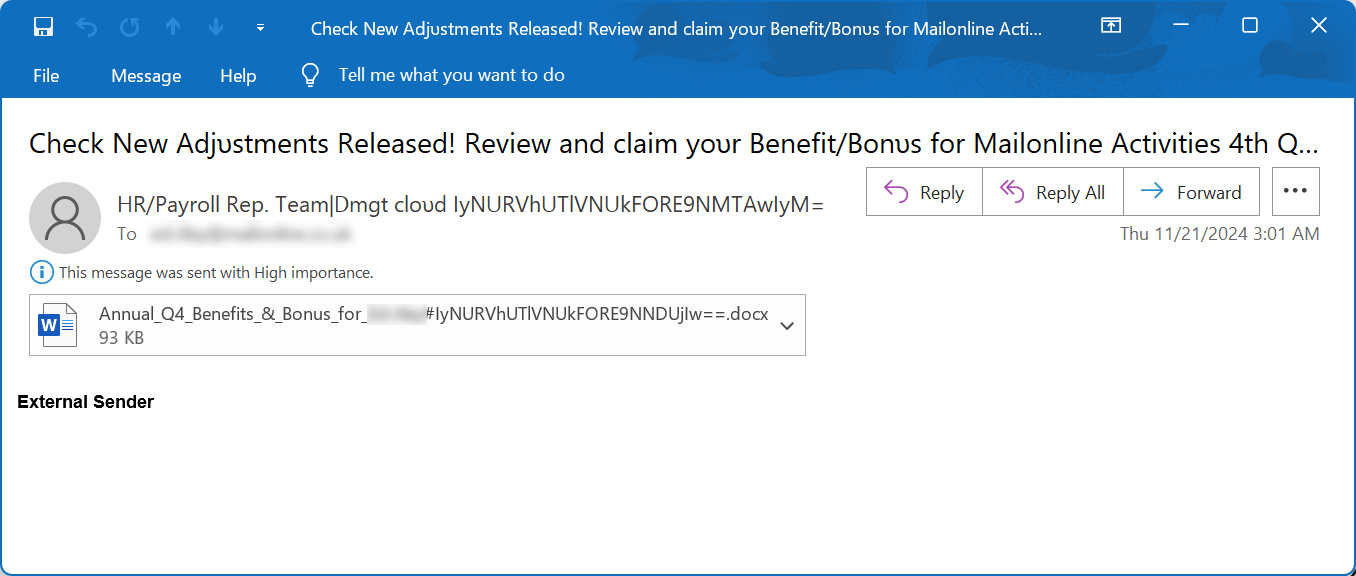
A brand new phishing marketing campaign found by malware searching agency Any.Run makes use of deliberately corrupted Phrase paperwork as attachments in emails that faux to be from payroll and human assets departments.
Source: BleepingComputer
These attachments use a variety of themes, all revolving round worker advantages and bonuses, together with:
Annual_Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx
Annual_Q4_Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
Due_&_Payment_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
Q4_Benefits_&_Bonus_for_[name]_IyNURVhUTlVNUkFORE9NNDUjIw__.docx.bin
The paperwork on this marketing campaign all embody the base64 encoded string “IyNURVhUTlVNUkFORE9NNDUjIw,” which decodes to “##TEXTNUMRANDOM45##”.
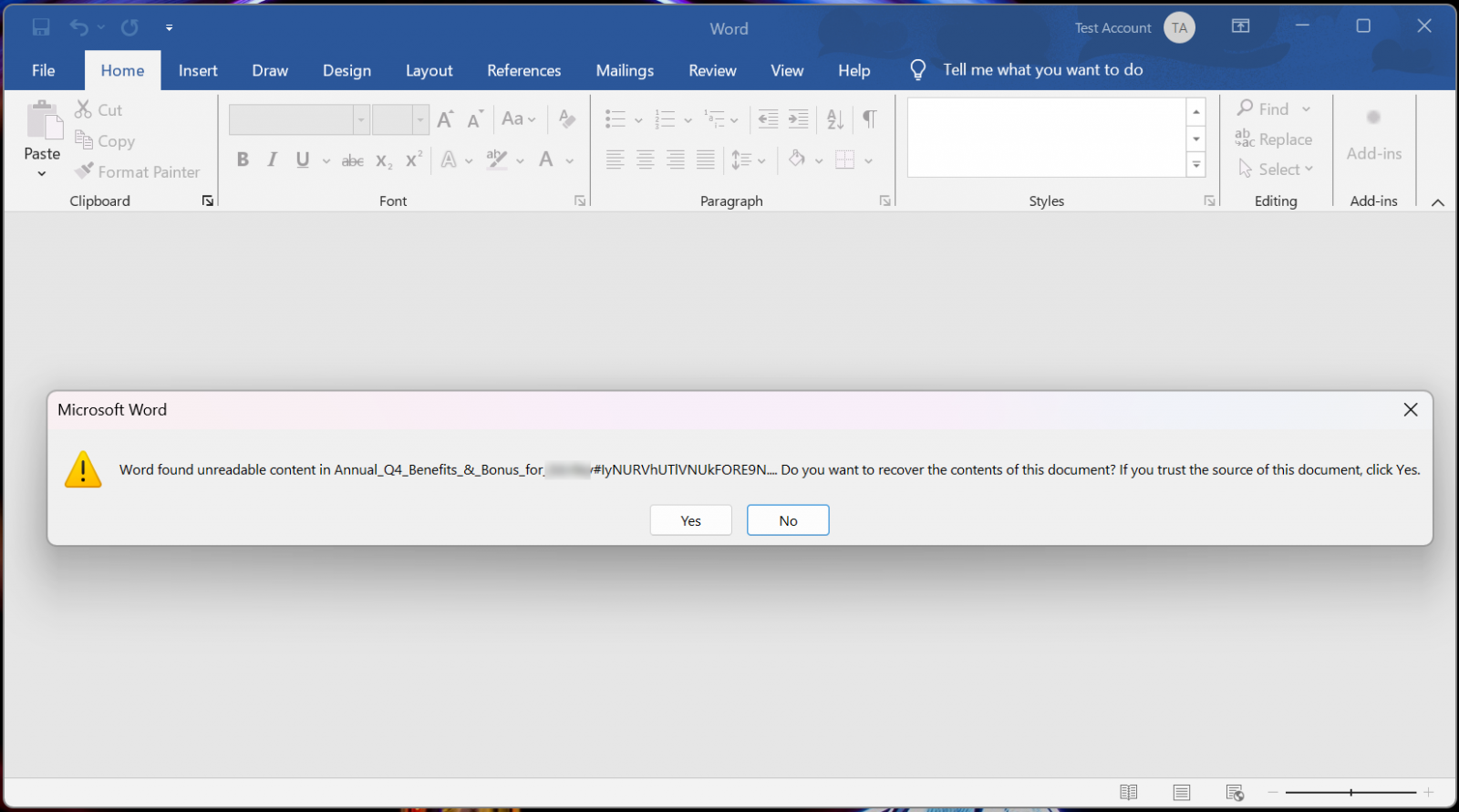
When opening the attachments, Phrase will detect that the file is corrupted and state that it “found unreadable content” within the file, asking when you want to get well it.
Supply: BleepingComputer
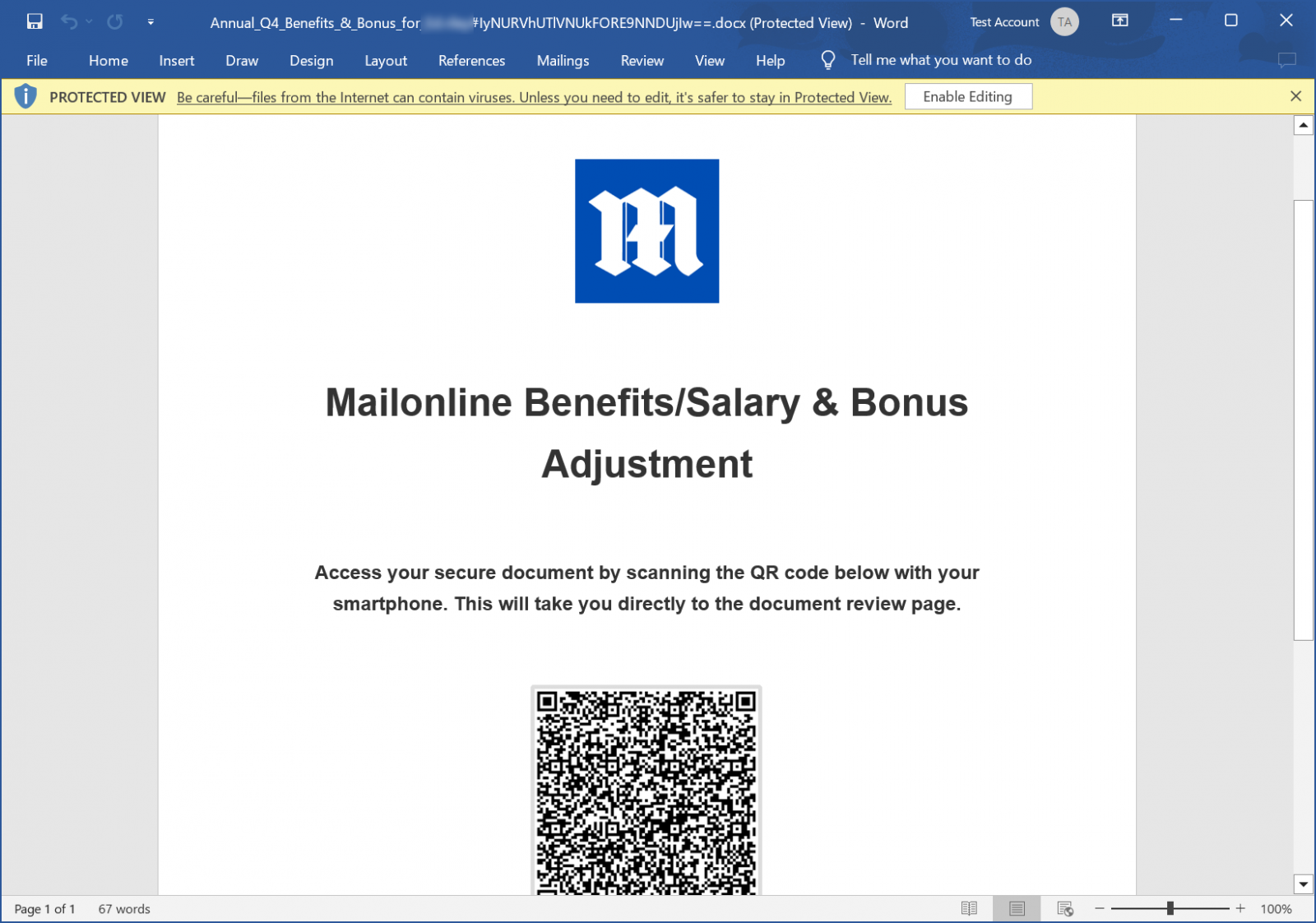
These phishing paperwork are corrupted in such a manner that they’re simply recoverable, displaying a doc that tells the goal to scan a QR code to retrieve a doc. As you may see under, these paperwork are branded with the logos of the focused firm, such because the marketing campaign focusing on Each day Mail proven under.
Supply: BleepingComputer
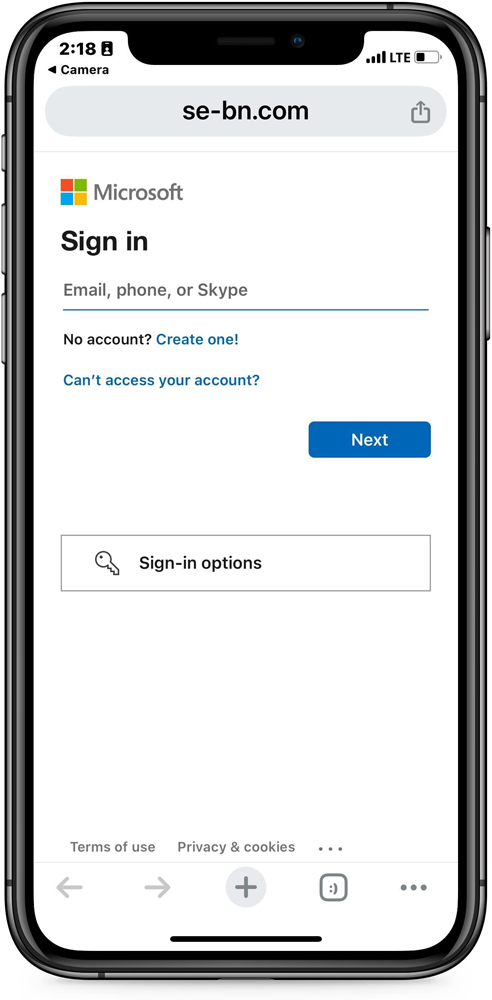
Scanning the QR code will carry the person to a phishing website that pretends to be a Microsoft login, trying to steal the person’s credentials.
Supply: BleepingComputer
Whereas the final word aim of this phishing assault is nothing new, its use of corrupted Phrase paperwork is a novel tactic used to evade detection.
“Although these files operate successfully within the OS, they remain undetected by most security solutions due to the failure to apply proper procedures for their file types,” explains Any.Run.
“They were uploaded to VirusTotal, but all antivirus solutions returned “clear” or “Merchandise Not Discovered” as they couldn’t analyze the file properly.”
These attachments have been pretty profitable in reaching their aim.
From attachments shared with BleepingComputer and used on this marketing campaign, virtually all have zero detections [1, 2, 3, 4] on VirusTotal, with just some [1] detected by 2 distributors.
On the identical time, this is also brought on by the truth that no malicious code has been added to the paperwork, and so they merely show a QR code.
The overall guidelines nonetheless apply to guard your self towards this phishing assault.
If you happen to obtain an e mail from an unknown sender, particularly if it incorporates attachments, it needs to be deleted instantly or confirmed with a community admin earlier than opening it.
