Cloud safety operates on a unique paradigm in comparison with conventional IT safety. For instance, it entails a number of contextual layers comparable to cloud providers, containers and Kubernetes that require specialised insights. The problem is even tougher when the group is affected by compliance necessities, and is compounded by the sheer quantity of knowledge that turns into a serious concern for any group. Failing to successfully handle it results in expensive inefficiencies and dangers.
Sysdig’s Cloud native software safety platform (CNAPP) was created with the target of streamlining how corporations safe their cloud infrastructure and purposes, enabling them to realize management over quickly altering environments.
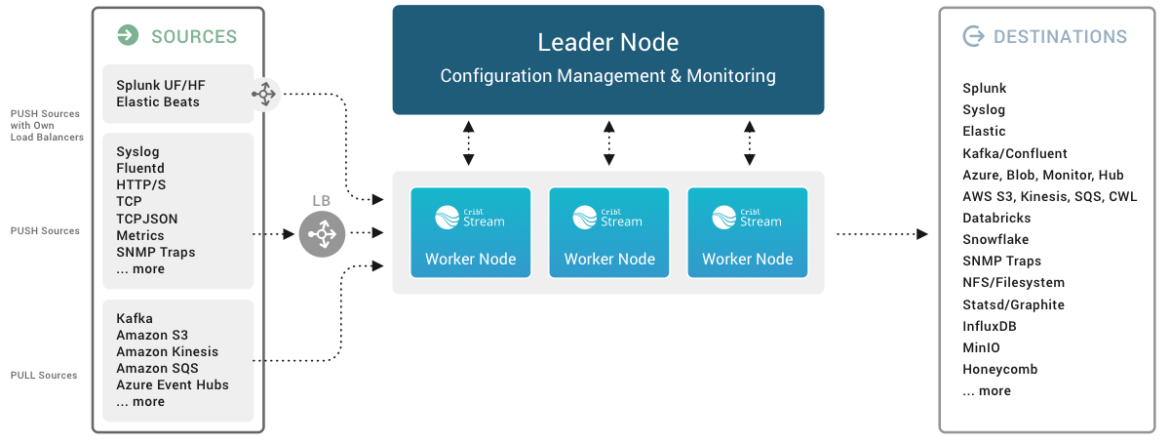
Nevertheless, it’s common for Safety Operations Middle (SOC) groups to usually juggle a number of safety platforms and sources, producing complicated information streams that must be managed, correlated, and saved. Cribl and Sysdig are the proper mixture to convey full cloud visibility whereas optimally managing storage prices and the agility to embrace any modifications that the companies could require.
Worth of cloud safety alerts for SIEM, SOAR and Information Lakes
CNAPPs emerged because the “eyes of the security system” inside cloud environments that when have been stuffed with blind spots. Moreover, cloud safety options feed wealthy, contextual alerts into different platforms, safety options like SIEMs, SOARs, or storage options like Information Lakes.
With Sysdig’s cloud safety engine, related occasions may be filtered and highlighted, contributing to SOC effectivity. Now you’ll be able to shift focus away from widespread logs to detect precise related incidents, consider the severity or examine its cloud context to make choices.
Directing CNAPP information into SIEM, Information Lakes, or a they each, opens up limitless prospects for safety analytics, risk searching, and machine learning-driven anomaly detection. With CNAPP, safety analysts can cut back alert fatigue and give attention to what issues most – defending cloud purposes.
What’s Cribl?
Cribl is a strong SaaS platform that modified how the information is managed. It permits organizations to filter, tweak, and route information dynamically with precision. The structure is versatile and helps a number of information sources and locations. For instance, it could sift by means of the information and cut back it earlier than forwarding to a SIEM or information lake, producing essential value discount in comparison with conventional SIEM connections.
In essence, Cribl empowers organizations to not solely handle their information extra successfully but in addition to unlock its full potential, driving smarter choices and quicker responses in quickly altering environments.
A few of the prime Cribl use instances are:
- Optimization of storage prices by making use of discount, sampling or aggregation strategies.
- Selectively route information to cheaper storage methods or a number of locations.
- Feed information lake, exterior or the Cribl Datalake itself.
- Search and Analyze Information at Supply.
- Enrich with context, or change the form, dimension or high quality of knowledge.
- Replay information from low value storage.
Why mix Sysdig and Cribl?
Safety groups and ITOps are groups which might be inherently synergistic in nature. Our prospects usually leverage this synergy to realize key outcomes.
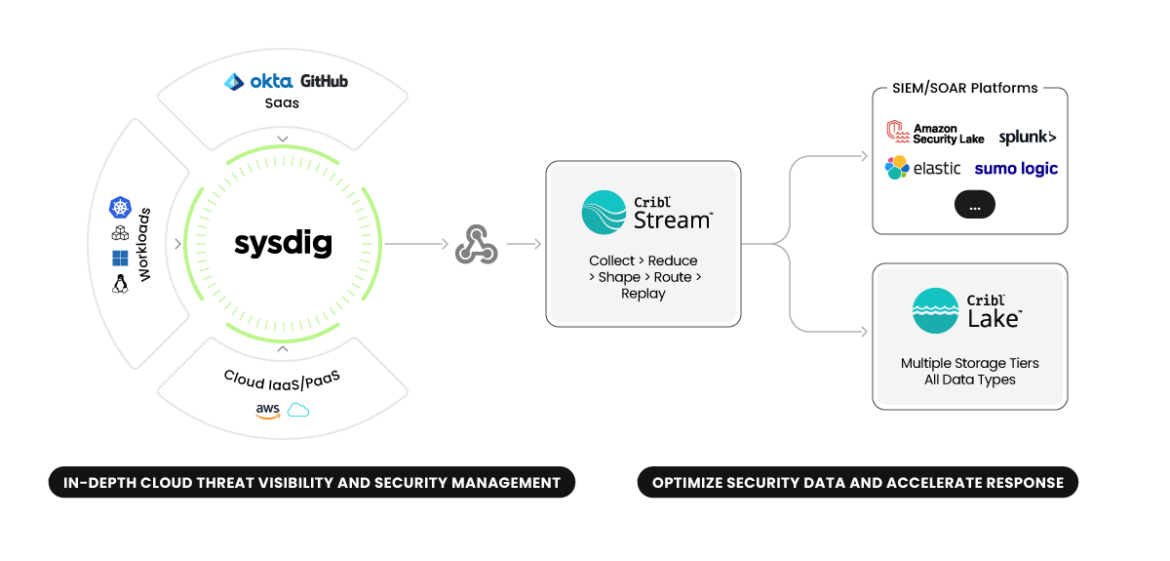
Clever information discount: Sysdig’s routinely up to date risk intelligence guidelines discern what occasions are related beneath the context and the granularity that cloud safety requires. This reduces significantly the quantity of knowledge that must be saved vs uncooked logs. Cribl provides on prime of this course of an extra safety information optimization gate, permitting prospects to form this information to their explicit wants.
Dynamic storage optimization: The brand new paradigm is to separate information dynamically within the occasion it requires totally different entry profiles as a substitute of storing a ton of knowledge collectively.
Versatile Configurations: If yesterday our SOC crew aimed to arrange an enterprise SIEM linked to a number of sources like a WAF and SASE, in the present day they is perhaps contemplating a distributed SIEM mixed with a Information Lake. Or maybe they’re exploring the potential of onboarding a brand new cloud supplier or transferring particular workloads again on-prem for compliance causes. The important thing right here is flexibility—and Cribl excels at offering that.
Fingers on testing of the Sysdig-Cribl integration
With the intention to emulate an actual world multi-cloud setting, we arrange a sandbox with a number of cloud accounts from totally different suppliers, some computing cases, Kubernetes clusters, and deployed a couple of automations to generate different occasions periodically. We plugged Sysdig to ingest cloud audit logs, and instrumented cases and Kubernetes clusters to get CWPP alerts.
Entry Sysdig’s official documentation for step-by-step steerage on integrating with Cribl
Conditions
- A Sysdig account populated with some information. We enabled all of the insurance policies to intentionally generate as many occasions as potential. That is the other of what our prospects ought to do, however is nice for testing functions.
- A Cribl Stream account.
Use case A: Improve effectivity of Sysdig information for Splunk/SIEM
We selected Splunk for this weblog put up demonstration however you’ll be able to join it to any vacation spot comparable to Chronicle, Sentinel, or Sumo, simply to say some.
Organising this integration is fairly easy simply by following the intuitive Cribl Person Interface and its embedded ideas. We’re going to use Sysdig Occasion Forwarder to ship Falco findings to Cribl.
Whereas we define a fast guide method on this put up, Cribl prospects also can leverage Cribl packs for Sysdig to configure it quicker.
- Configure the employee, a supply, and a vacation spot in Cribl Stream
- From the Cribl UI: Browse to Employee Teams and select Default. Go to the Routing tab and choose QuickConnect
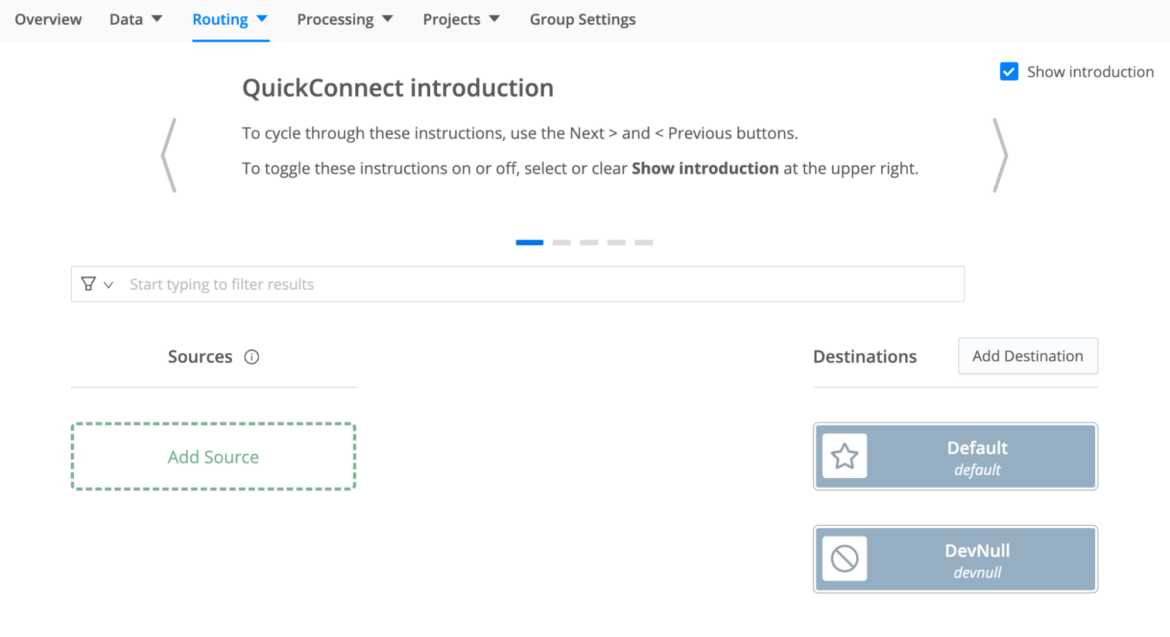
- Click on the Add Supply button, and select http, set the specified port and reserve it.
- As soon as created you’ll be able to configure throughput settings. We left it OOTB for this instance. Please copy the agent HTTP url.
- Create a brand new Vacation spot (For instance Splunk Single Occasion), configure it accordingly, take a look at it and save.
- Click on the (+) icon and drag to attach this supply to the beforehand created Splunk vacation spot. Select the pipeline choice when the pipeline kind is introduced. From that immediate Add Pipeline > Create New Pipeline. Kind in “Sysdig” because the pipeline identify and reserve it.
At this level it is best to have a supply linked to a vacation spot, with a pipeline within the
center.
- Create a brand new Sysdig Occasion Forwarder
- From the Sysdig Console: Go to the Integrations choice out of your Sysdig console menu and from there to Occasion Forwarding.
- Click on the Add Integration button, select Webhook from the dropdown menu.
- Configure the Occasion Forwarding Webhook kind. Including an authentication technique is strongly beneficial. Fill the Endpoint subject by pasting the employee url supplied by Cribl Stream once we configured the http supply.
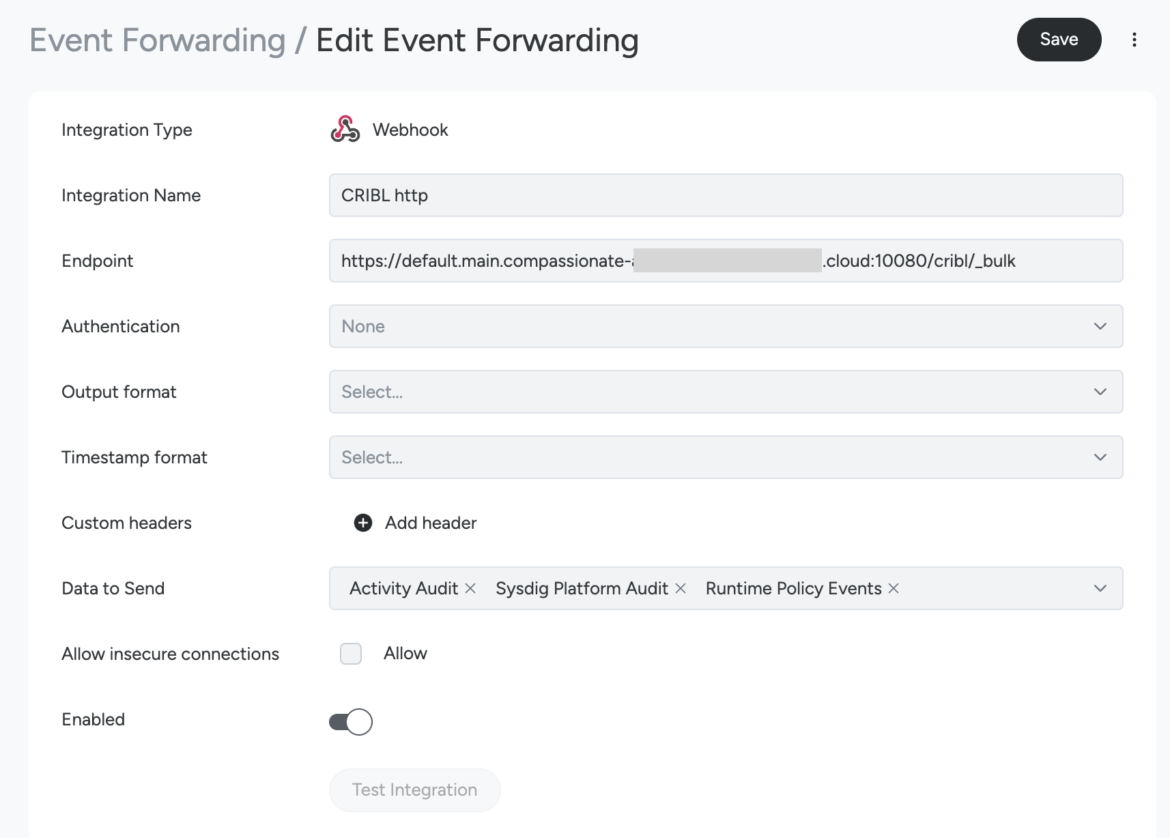
- Choose the Information to Ship (Runtime Coverage Occasions if you wish to share Sysdig Falco findings and threats from any supply like AWS, GCP, Azure, or Kubernetes, Linux and Home windows Situations, and so forth.).
- Click on the Take a look at Integration button to examine that Sysdig can ahead information to your Cribl employee with success.
- Save the brand new Occasion Forwarder. From now onwards, Sysdig will ahead all the chosen occasions to Cribl.3. Monitor the information touring from Sysdig to Cribl
At this level, Sysdig is forwarding all of the runtime findings to our Cribl default employee. Let’s see it in motion.
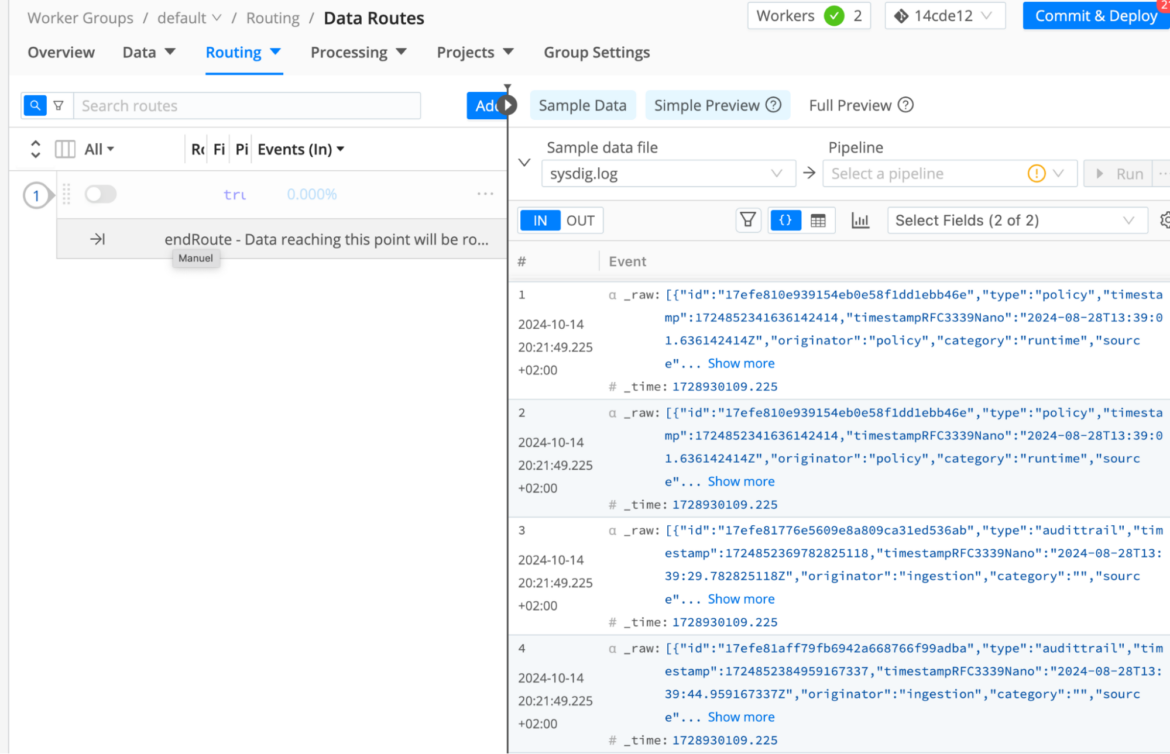
- Browse to Employee Teams > Routing > Information Routes and go to the fitting tab known as Pattern Information. There we are able to click on to retrieve a “Simple” Preview and examine Sysdig entries.
- Another strategy to examine the combination in motion goes to Monitoring > Overview to evaluate the streaming charts in actual time
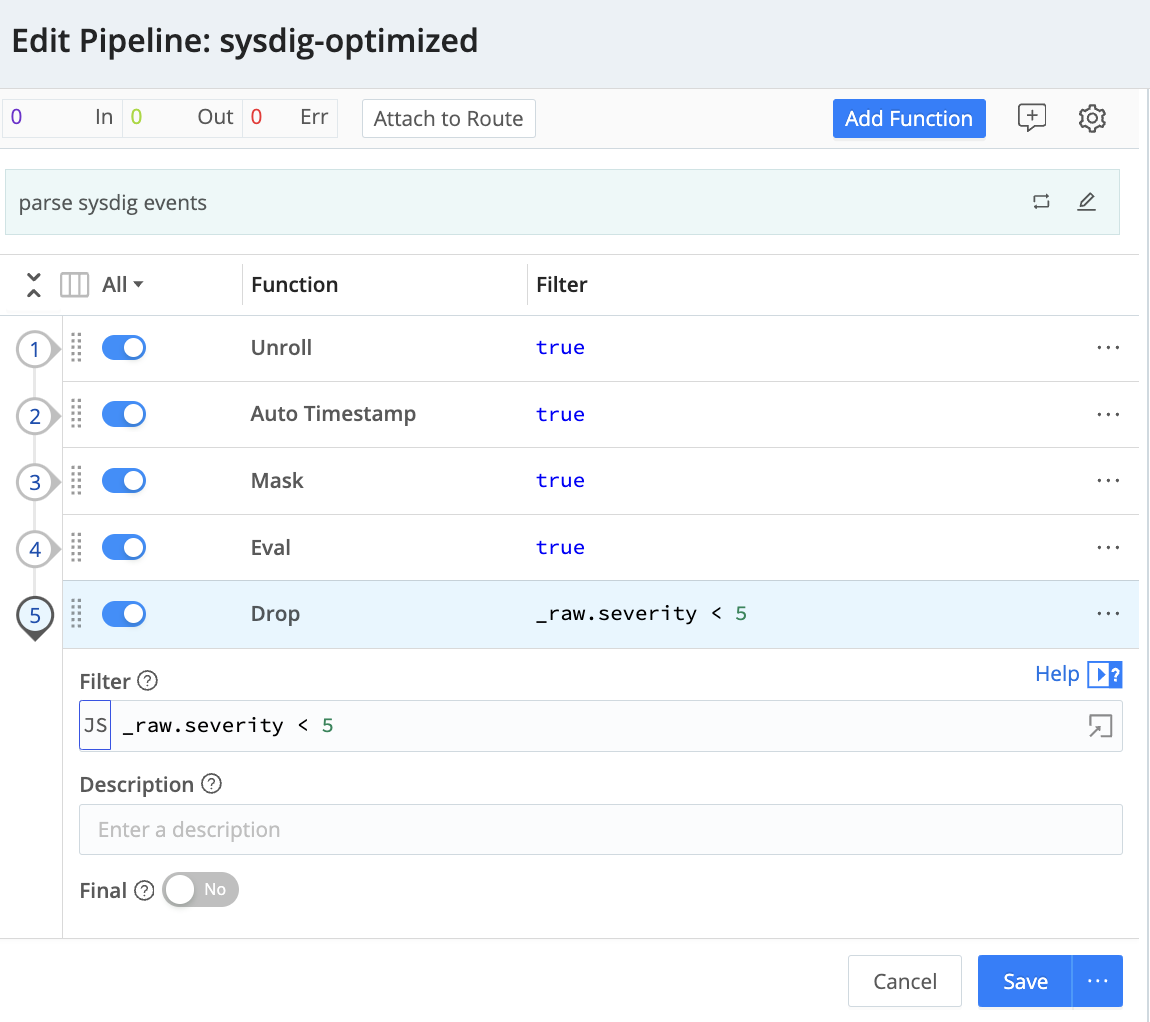
4. Configure a Cribl Pipeline for optimization or dynamic routing
We would need to use Cribl to route Sysdig information “as is”. Nevertheless, as talked about earlier than, Cribl permits information transformation with strategies like suppression, sampling, changing or parsing, amongst others.
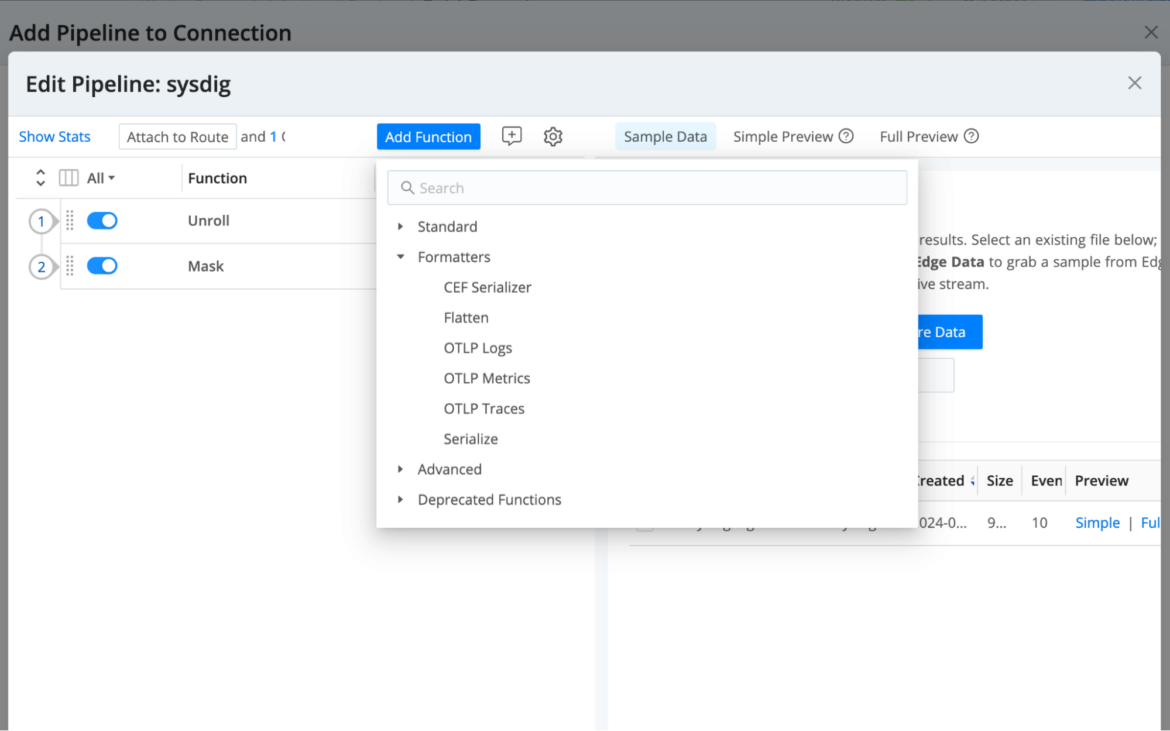
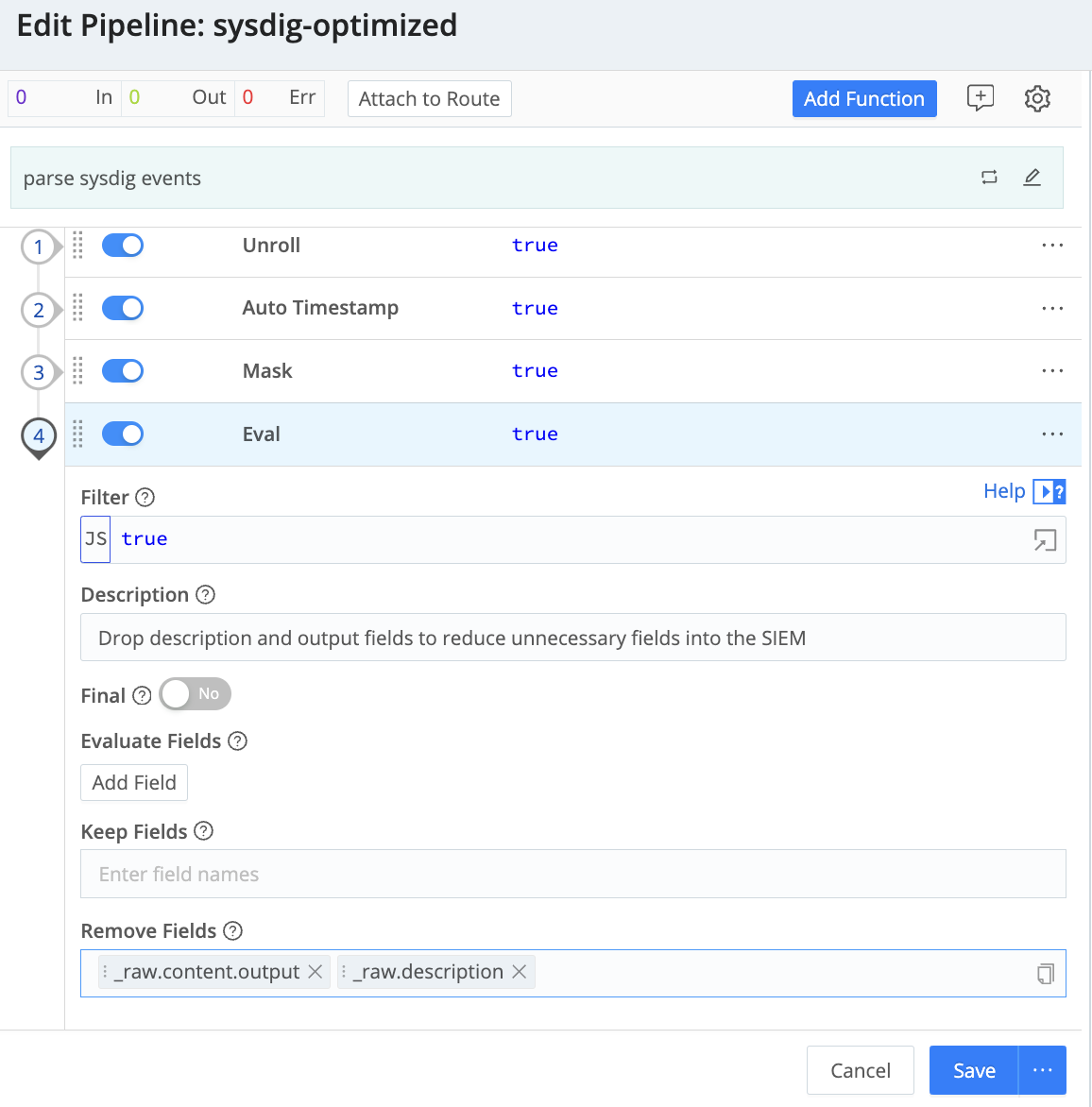
Optimization: To exhibit how straightforward it’s so as to add features to the transformation course of, let’s take away a few fields that we would like to not retailer (on this instance we’re utilizing an eval operate to do away with content material.output and content material.description)
Dynamic routing: Suppose you need to persist solely probably the most essential findings in your SIEM, storing the remainder of the occasions in a less expensive storage like a Information Lake.
Simply create two pipelines and add a Drop operate to suppress any occasions whose severity is lower than 5 (Excessive and Essential)
- Confirm that the information is starting to look in Splunk
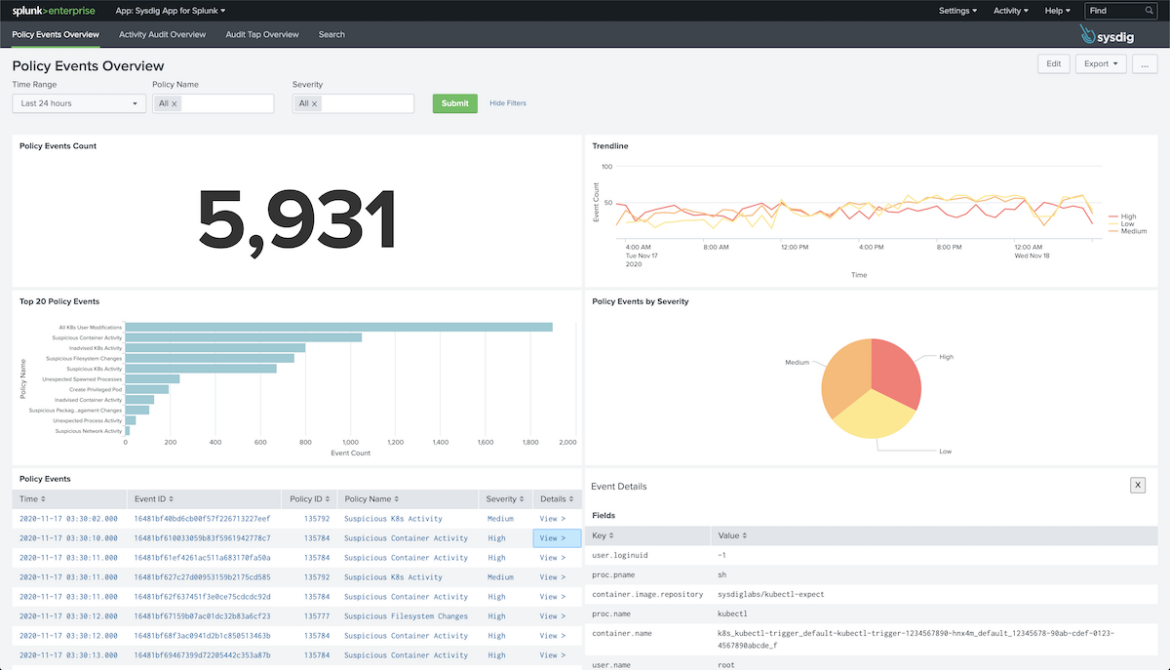
Use case B: Squeeze Sysdig information with Cribl Information Lake
- Add a brand new vacation spot
- Entry to Cribl Streams, browse to Route and Fast Join once more.
- Add Vacation spot and select Cribl Lake, reuse the earlier pipeline or create a brand new one.
- Join the Sysdig supply to the Cribl Lake vacation spot.
- Go to Cribl Lake, Datasets and examine that the combination is related to the default occasions (right here you may as well change the retention interval if you wish to).
- Question the Information Lake
- From the Cribl Lake, Datasets display, click on the corresponding Search button from default occasions.
- Set the time window to the specified time (i.e. 24 hours) and take a look at some queries within the search field.
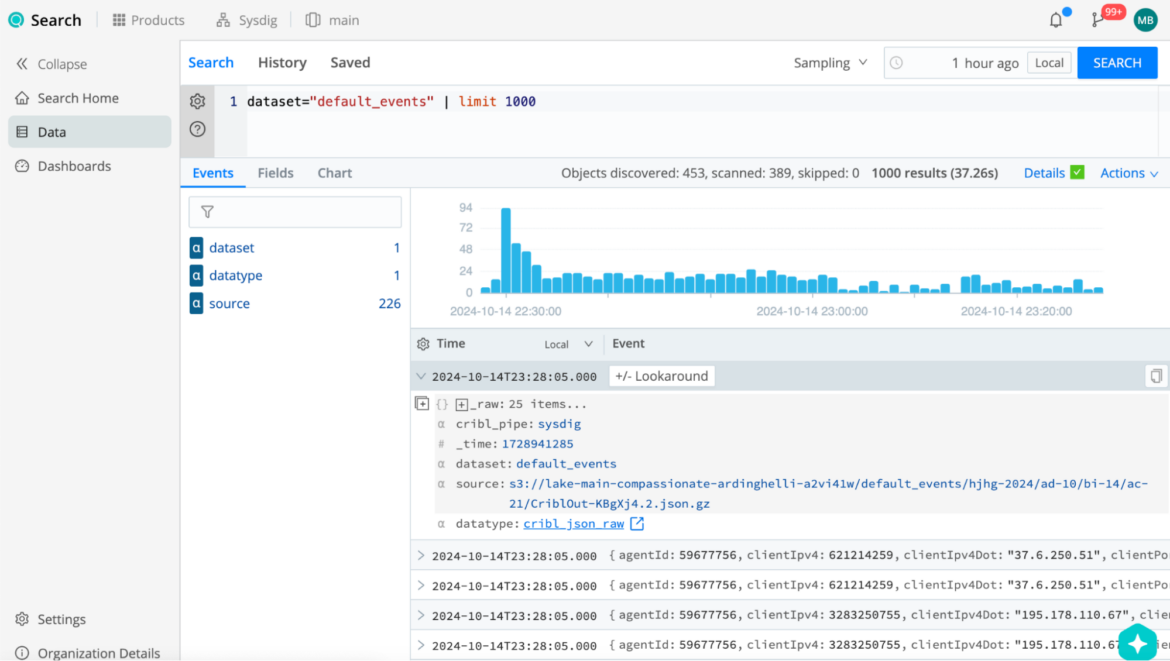
Let’s strive some helpful queries:
dataset="default_events" | extract kind=json | the place kind == 'coverage' and supply == 'syscall' and labels["cloudProvider.name"] == 'gcp'Code language: JavaScript (javascript)Request all of the CWPP occasions working in a GCP venture.
dataset="default_events" | extract kind=json | the place kind == 'coverage' and supply == 'awscloudtrail' | summarize rely()Code language: JavaScript (javascript)Request all of the CDR occasions from AWS Cloudtrail.
dataset="default_events" | extract kind=json | the place kind == 'coverage' and supply == 'syscall' | dedup by labels["host.hostName"]Code language: JavaScript (javascript)Request CWPP occasions, deduplicating by hostname.
- Construct a Sysdig Dashboard
As soon as once more, though we clarify it step-by-step right here, you’ll be able to reuse the Cribl packs for Sysdig to hurry up the method.
- From the principle menu, browse to Cribl Search > Dashboards and click on the button Add Dashboard, set the specified Title, and Save.
- From the highest proper three dots, select Edit. As soon as the dashboard is in edit mode, click on Add > Visualization. Set the Title, Search Question, and time window.
- For our pattern Sysdig Dashboard we created the next 7 visualization components:
- Take a look at the brand new dashboard (just remember to have sufficient historic information to get the charts drawn correctly).
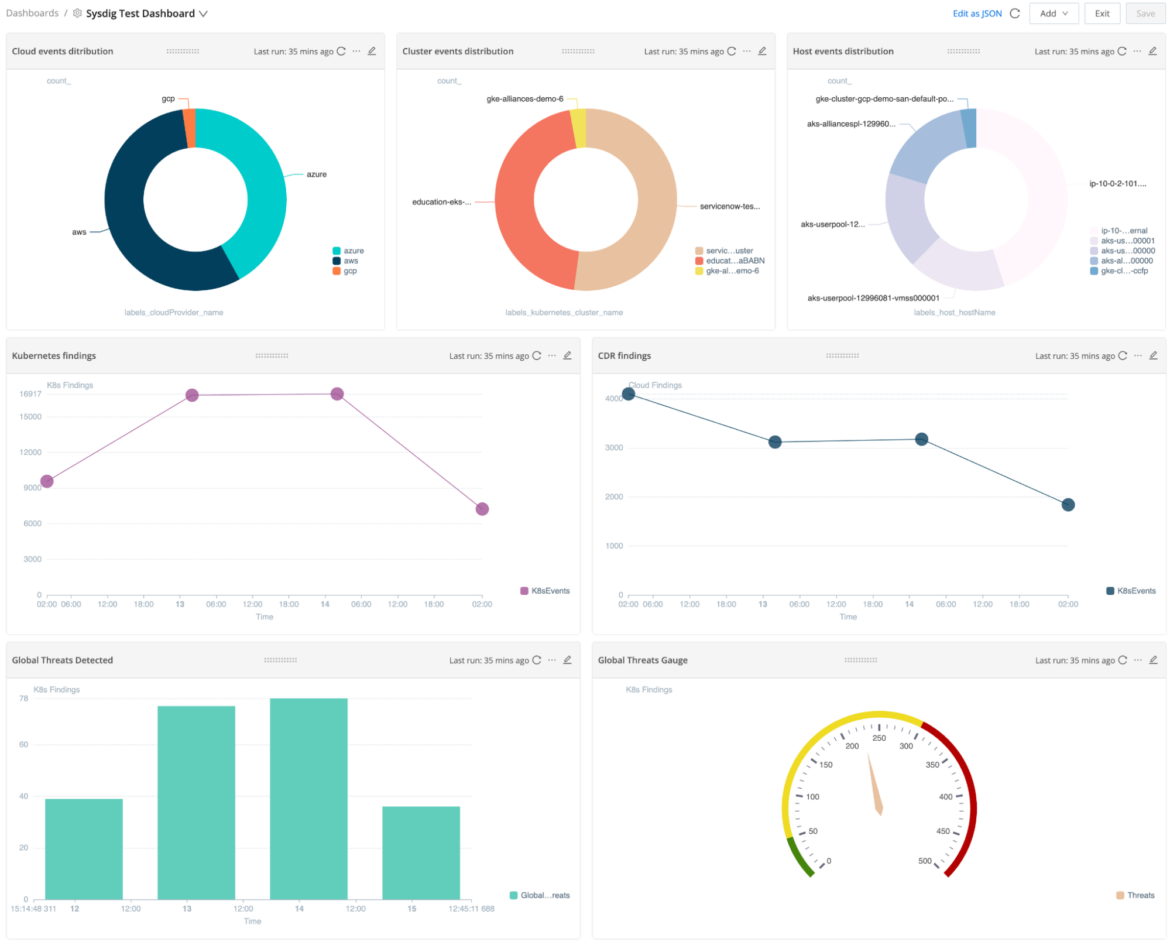
- You may mess around with the dashboard and take a look at choices like Open In Search or Export visualization to PNG.
Conclusion
This integration offers a strong answer for managing the complexities of cloud safety information at scale. By combining Sysdig’s strong safety insights with Cribl’s information routing and optimization capabilities, safety groups can streamline their workflows and cut back storage prices, whereas rising their resilience.