Abstract:
- Malware exploits a reliable Avast Anti-Rootkit driver to achieve kernel-level entry.
- Driver is used to terminate essential safety processes and seize management of the system.
- BYOVD (Carry Your Personal Susceptible Driver) safety mechanisms can forestall driver-based assaults.
- Professional guidelines may be deployed to establish and block susceptible drivers.
Cybersecurity researchers at Trellix have recognized a malicious marketing campaign that exploits a reliable Avast Anti-Rootkit driver, aswArPot.sys, to disable safety software program and take management of contaminated techniques.
How the Assault Works:
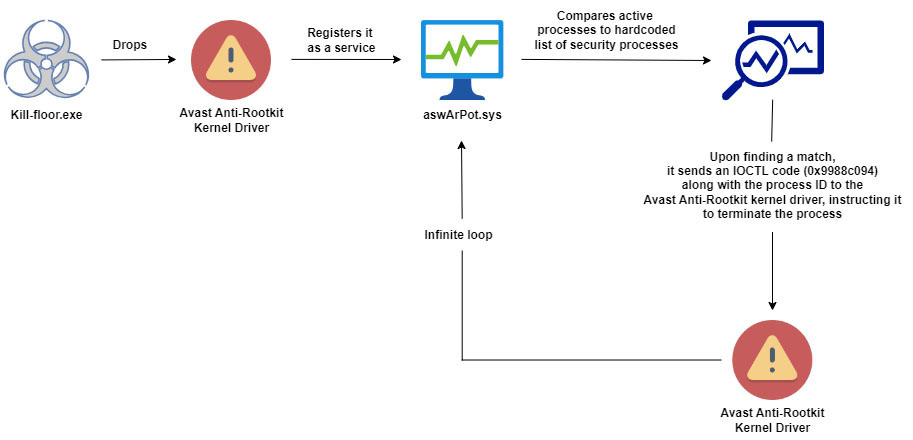
The malware, dubbed “kill-floor.exe,” begins by dropping the aswArPot.sys driver into an apparently innocent Home windows listing, disguising it as “ntfs.bin.” It then registers the driving force as a service, granting the malware kernel-level entry – the very best degree of system privilege permitting it to terminate essential safety processes and take management of the system.
The malware accommodates a hardcoded record of 142 safety purposes it targets for termination. The malware repeatedly displays lively processes and compares them towards this record. When a match is discovered, the malware makes use of the Avast Anti-Rootkit driver to terminate the safety course of.
Merely put: The Avast driver, meant to take away malicious rootkits, unintentionally disables reliable safety software program. Malware takes benefit of this trusted driver to keep away from detection and work quietly inside the system.
Technical Look
Trellix’s technical evaluation of the Avast driver revealed the precise perform, “FUN_14001dc80,” answerable for terminating the safety processes. This perform makes use of commonplace Home windows kernel capabilities (KeAttachProcess and ZwTerminateProcess) to hold out the termination, additional masking the malicious exercise as regular system operations.
Defending Your self
To stop such driver-based assaults, Trellix recommends the usage of BYOVD (Carry Your Personal Susceptible Driver) safety mechanisms. These mechanisms can establish and block particular susceptible drivers primarily based on their distinctive signatures or hashes.
As soon as these guidelines are built-in into your antivirus answer, organizations can forestall malware from exploiting reliable drivers, elevate privileges, or disable safety measures. Trellix has additionally offered a selected BYOVD skilled rule to detect and block the malicious use of the aswArPot.sys driver.
RELATED TOPICS
- After Avast, the NordVPN server will get hacked
- Faux Antivirus Websites Unfold Malware Disguised as Avast
- SpyNote Android Spy ware Poses as Legit Crypto Wallets
- Avast hacked after attackers gained area admin privileges
- Chinese language APT Flax Hurricane makes use of legit instruments for cyber espionage