Assault surfaces within the cloud are increasing at a breakneck tempo. Cloud safety has reached an unprecedented stage of complexity — starting from misconfigurations and vulnerabilities to superior threats and compliance challenges, all whereas malicious actors are more and more utilizing generative AI to focus on your cloud infrastructure.
At Sysdig, we perceive these challenges higher than anybody. As cloud adoption accelerates and organizations embrace more and more advanced architectures, safety groups are grappling with a various set of points, from runtime threats to ever-shifting infrastructure and cloud-native functions. With our November 2024 launch targeted on cloud safety posture administration (CSPM), we’re supplying you with the instruments to remain forward of those challenges.
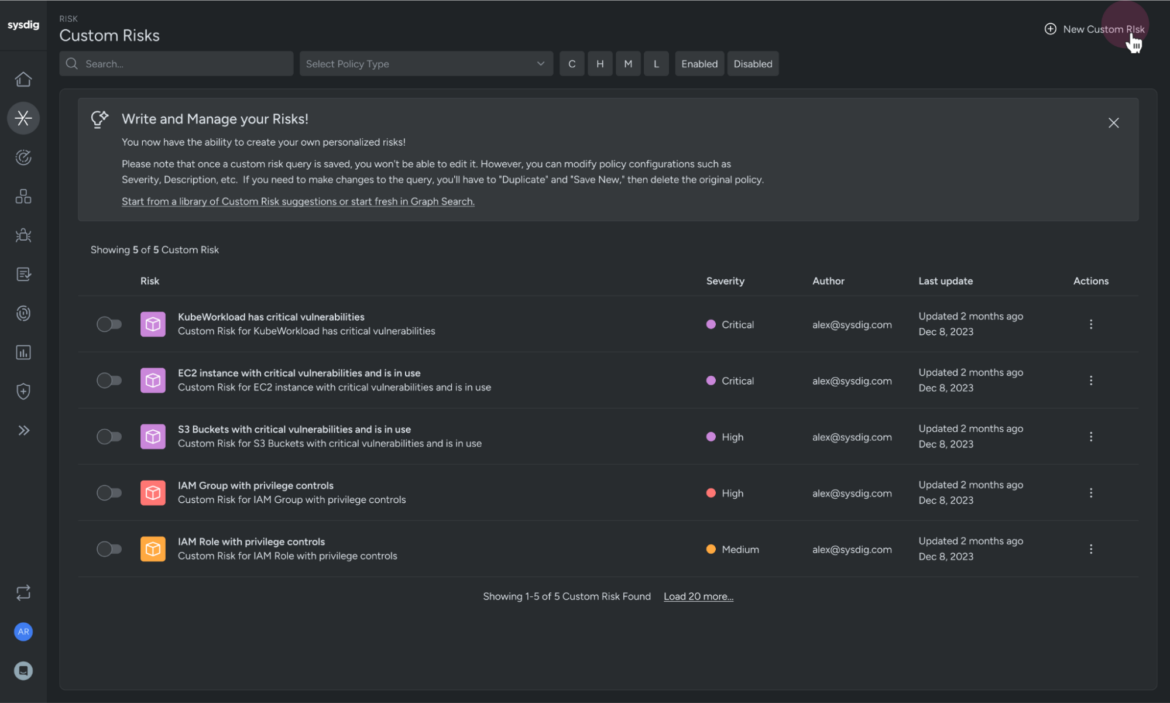
1. Customized Dangers: Take again management of threat administration
One-size-fits-all safety doesn’t work, particularly within the cloud. Whether or not you’re working with containers, Kubernetes, or multi-cloud environments, every group has a singular safety posture — and a set of threats that requires a tailor-made strategy.
Sysdig’s Customized Dangers characteristic was constructed with this in thoughts. It permits safety groups to outline, write, and execute on their very own customized threat patterns — a stage of flexibility and management that offers you the power to create adaptive queries tailor-made to your surroundings and your particular threat urge for food. For instance, in case your group is working with high-risk workloads on AWS cloud in a regulated business like finance, you may tag them with related labels and create a customized question for such threat markers. We offer you again the ability to customise your threat administration technique.
2. Customizable controls: Tailor-made to your wants
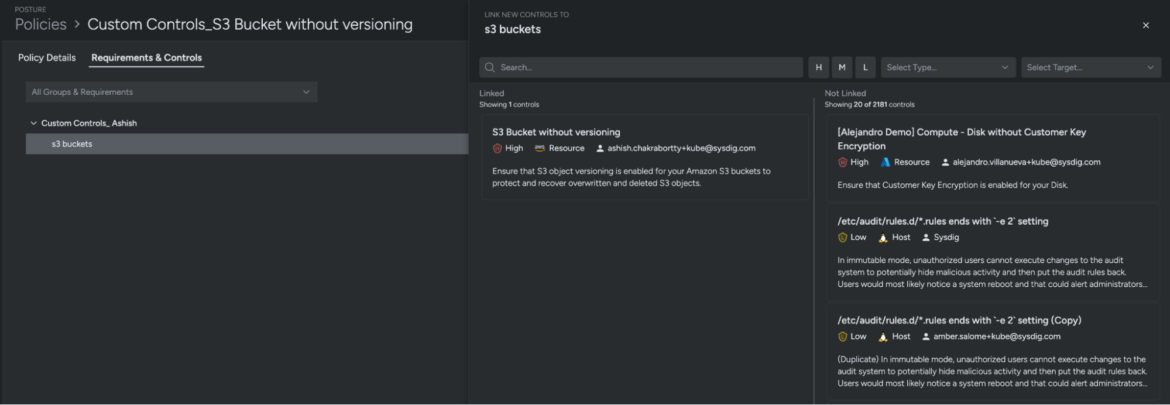
Cloud safety isn’t static, and your controls shouldn’t be both. With Sysdig’s Customized Controls, safety groups can tailor safety insurance policies and compliance checks to their group’s distinctive wants:
- Outline your individual safety insurance policies and controls leveraging OPA, Rego and Terraform that align with the precise dangers of your cloud surroundings.
- Keep compliant with regulatory frameworks whereas concurrently guaranteeing the safety of your cloud sources.
3. Graph Search: Proactive and adaptive, not reactive
As a result of dynamic nature of cloud infrastructure, safety groups are sometimes within the place of reacting to threats after they’ve already taken root. A much-loved characteristic inside our Sysdig platform is our capability to establish evolving threats in actual time.
We’ve got constructed on prime of this functionality with Sysdig’s Graph Search, in an effort to proactively seek for dangerous patterns earlier than they turn into full-fledged threats. Think about this: A brand new improvement group launches an software, and within the course of, they by accident expose delicate cloud belongings to the web. With Sysdig’s Graph Search, you may spot these dangerous configurations earlier than a possible breach or misconfiguration escalates.
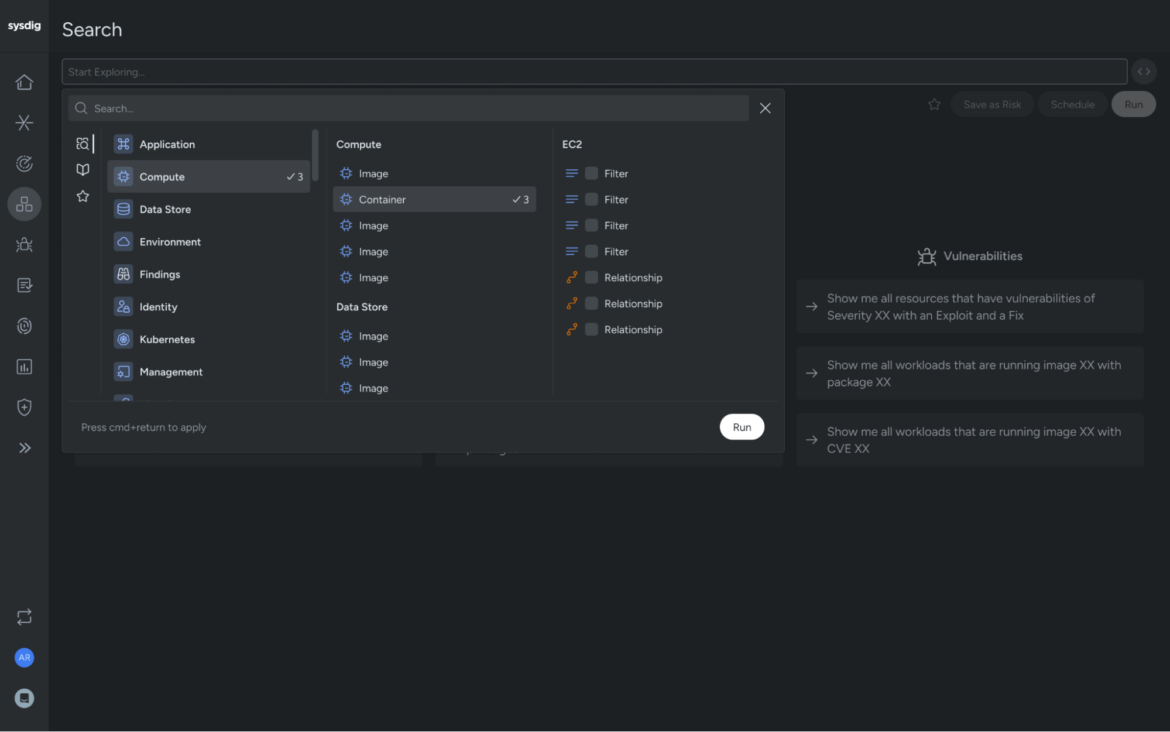
By leveraging a graph database enhanced with runtime context, Sysdig’s Graph Search doesn’t simply allow you to observe vulnerabilities; it empowers you to discover and prioritize evolving patterns of threat in actual time. That is the type of proactive safety that each CISO desires to construct into their group’s DNA — catching points early, staying forward of threats, and minimizing threat publicity.
4. Clear reporting for management: Demonstrating safety impression
One of many biggest challenges product leaders encounter is speaking the worth of advanced safety applications to executives. Safety groups perceive the intricacies of dangers, however executives and key stakeholders want clear, actionable insights they will evaluate with enterprise worth to make knowledgeable selections.

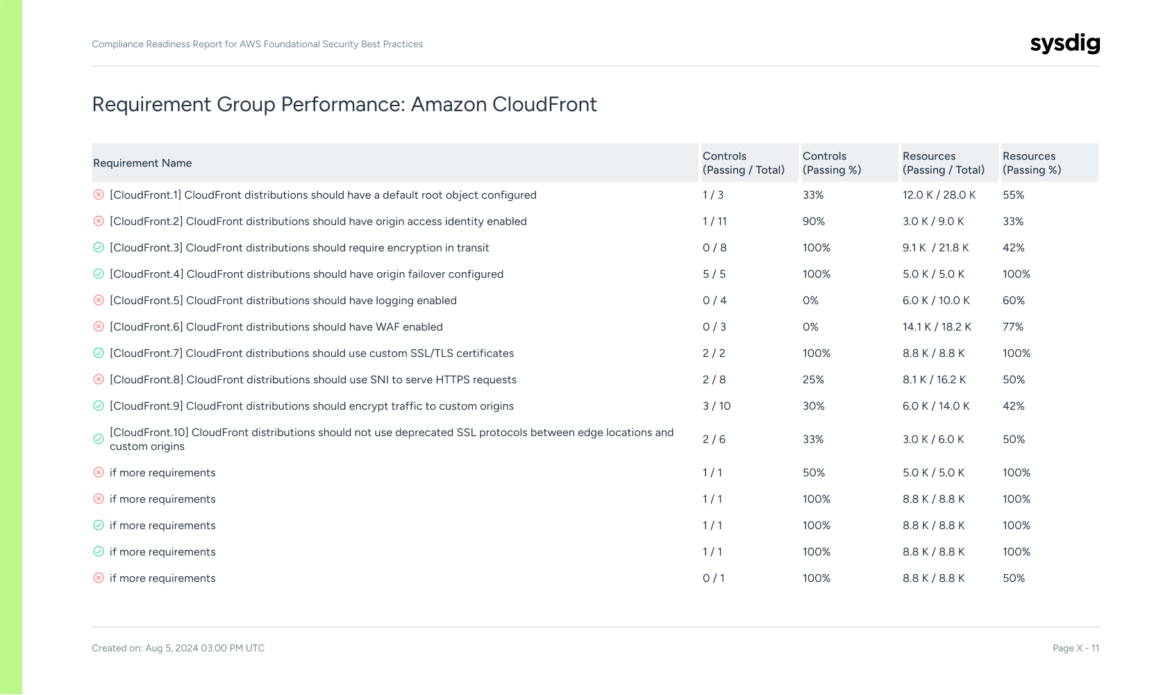
Sysdig’s CSPM Reporting characteristic solves this drawback by offering clear, concise reviews that talk the impression of your CSPM initiatives in phrases everybody can perceive. With real-time insights into your safety posture, key dangers, and ongoing mitigation efforts, you may exhibit the effectiveness of your safety program to management and different stakeholders — guaranteeing that safety is at all times aligned with enterprise objectives.
5. Roadmap merchandise – Useful resource 360: You can’t defend what you don’t see
We even have additional essential options deliberate for the close to future, like Resource360. One of the urgent challenges safety groups face is visibility. You’ll be able to’t defend what you may’t see, and in cloud environments, sources are continually being spun up, torn down, and altered in ways in which make conventional safety fashions ineffective.
Useful resource 360 is Sysdig’s reply to this problem. It offers you a full, real-time view of your cloud sources, permitting you to know at a look the place dangers are occurring, on a useful resource in a single place.
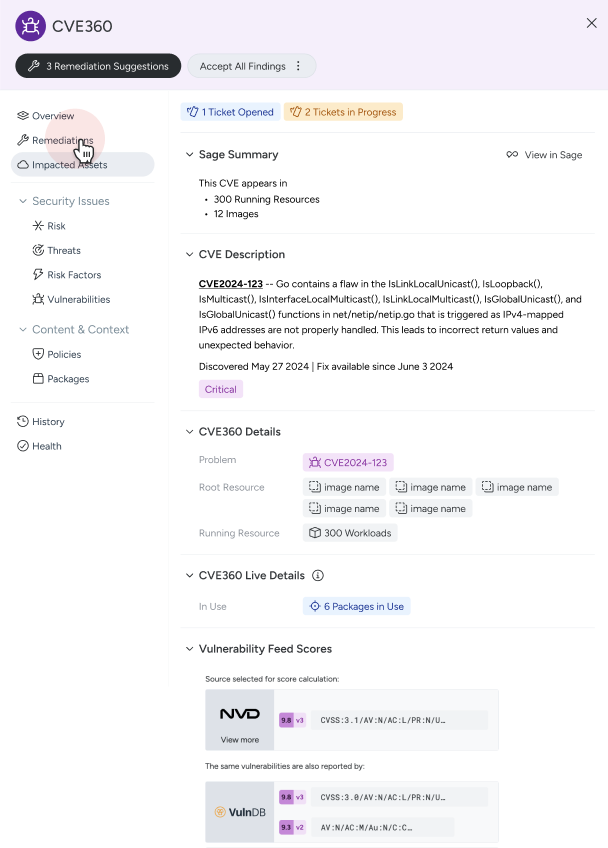
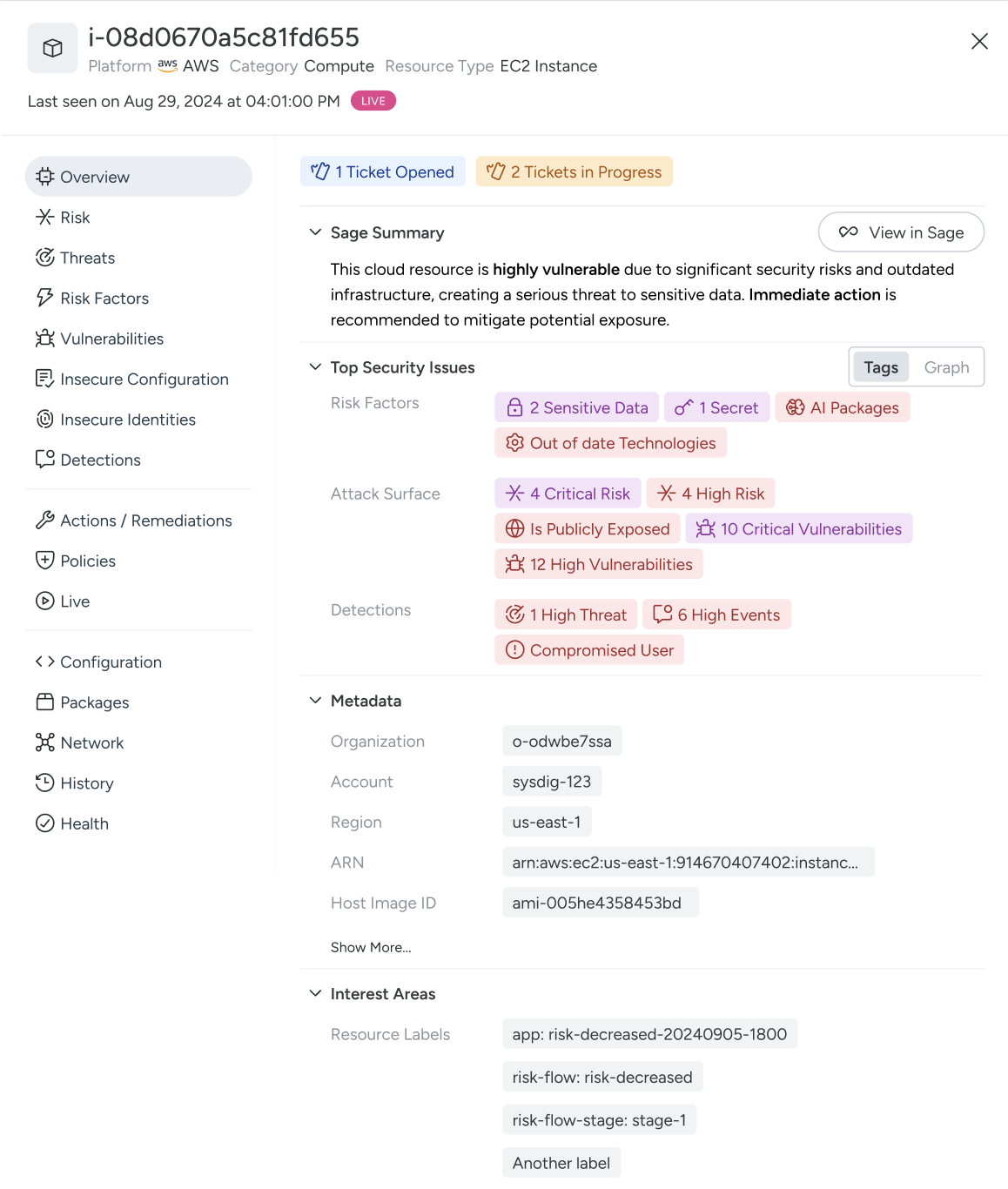
The true magic of Useful resource 360 is that it doesn’t simply provide visibility; it ties that visibility to real-time safety occasions and context. It helps in understanding the safety posture of every useful resource at any given second and having the context you want to make knowledgeable selections.
For safety groups who want to reply rapidly to incidents or handle giant, dynamic cloud environments, this stage of visibility is indispensable.
A extra proactive, versatile, and insightful strategy to CSPM
We’ve designed our resolution with one objective in thoughts: to assist organizations take management of their cloud safety posture in a approach that’s each adaptive and actionable.
TLDR:
- Customized Dangers: Totally customizable threat patterns to match your distinctive cloud surroundings.
- Graph Search: Actual-time, graph-powered searches that allow you to proactively establish and prioritize evolving dangers.
- Useful resource 360: Complete visibility into your cloud sources, tied to real-time safety occasions.
- Customizable Controls: Tailor-made safety insurance policies and compliance checks throughout Kubernetes, containers, and cloud infrastructure.
- CSPM Reporting: Actionable insights and clear reporting for management and key stakeholders.
At Sysdig, we’re dedicated to offering safety groups with the instruments they should handle dangers, implement insurance policies, and safe cloud environments — whether or not they’re on a journey to the cloud or already totally cloud-native. That is the way forward for cloud safety, and we’re excited that will help you take management.
Do you wish to see these options in motion? Click on right here to get a demo.