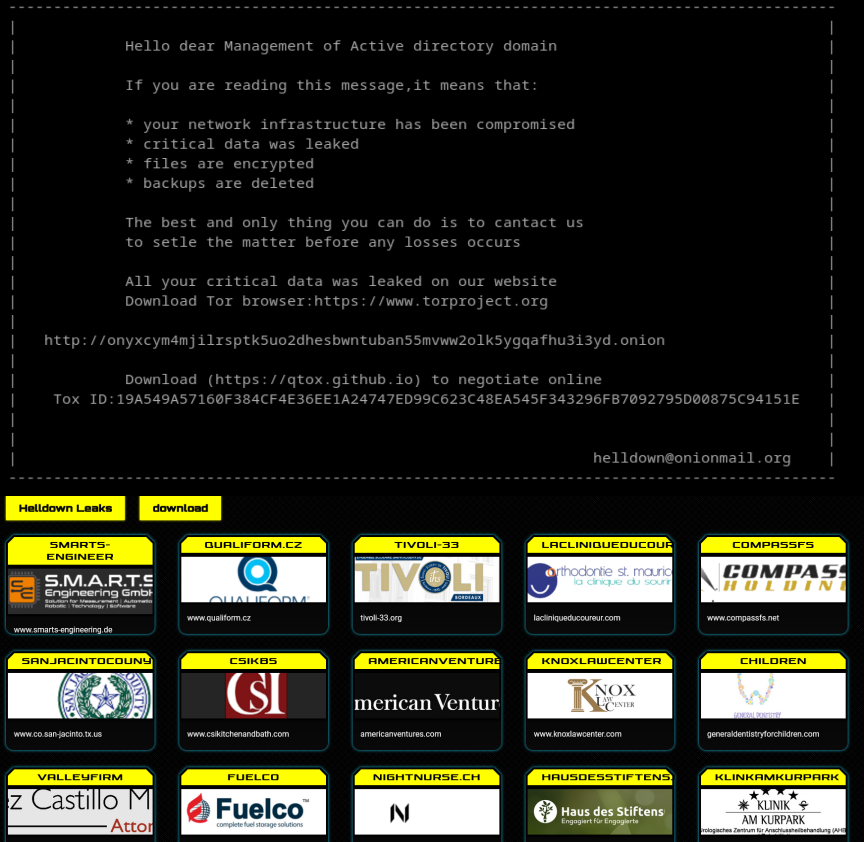
Cybersecurity agency Sekoia has found a brand new variant of Helldown ransomware. The article particulars their ways and the way they exploit vulnerabilities in community units, steal delicate information, and encrypt essential programs.
Sekoia’s cybersecurity researchers have found a Linux variant of the brand new ransomware pressure, Helldown, first discovered by Halcyon and deploys Home windows ransomware derived from the LockBit 3.0 code.
Helldown is a comparatively new ransomware group that has been actively concentrating on organizations since August 2024, affecting over 30 corporations in three months. This menace actor primarily exploits vulnerabilities in community units, significantly Zyxel firewalls.
As soon as they acquire entry, they make use of a double extortion technique, encrypting essential information and threatening to leak delicate data if a ransom isn’t paid. Researchers suspect that the group is increasing its assaults to focus on virtualized infrastructures by way of VMware, “given the recent development of ransomware targeting ESX.”
Helldown’s Linux variant particularly targets VMware ESX servers. This variant was first noticed by cybersecurity researcher Alex Turing (@TuringAlex) on 31 October 2024.
In line with Sekoia’s weblog publish shared with Hackread.com, the ransomware’s code focuses on a pattern of VMware ESX servers and is simple, missing obfuscation and anti-debugging mechanisms. The primary perform executes a easy workflow, together with configuration loading, file search, encryption, and ransom observe creation.
The code additionally features a perform known as kill_vms, which lists and kills VMs sequentially. Terminating VMs earlier than encryption grants ransomware write entry to picture recordsdata, however static and dynamic evaluation reveals this performance isn’t invoked, indicating that the ransomware continues to be underneath growth or not that superior.
On its darkish net information leak website, the group has disclosed a considerable amount of information, starting from 22GB to 431GB, and averaging 70GB excluding outliers. The stolen recordsdata are largely PDFs or scanned paperwork, possible obtained from servers like NAS programs or digital doc administration portals. The massive quantity suggests the attacker targets information sources storing administrative recordsdata, which generally comprise delicate data.
Researchers suspect a connection between Helldown vs. Hellcat and Darkrace/Donex teams, because of the timing of an organization (Schneider Electrical) compromise and social media exercise by alleged Hellcat operators. Nonetheless, no technical similarities have been discovered between these teams to date.
“Two accounts on the X social media, @grepcn and @ReyBreached, claiming to be Hellcat operators, posted to distinguish themselves from Helldown, each displaying Hellcat’s DLS link in their profiles.”
Sekoia’s Menace Detection & Analysis (TDR) staff
On your data, @grepcn has been fairly energetic on Breach Boards. They’re additionally the hacker behind current information breaches involving Dell (1, 2, 3) and Twilio.
Additionally it is price noting, although, that Helldown shares behavioural similarities with Darkrace, as each possible originated from leaked LockBit 3 code, and is suspected to be a rebrand of Darkrace.
However, to guard towards the Helldown assault, organizations ought to patch their community units, significantly Zyxel firewalls, with the newest safety updates. Adopting essential safety measures like community segmentation, entry controls, and common backups, and educating workers on cybersecurity greatest practices, together with phishing consciousness and safe password utilization is crucial to deal with evolving ransomware threats proactively.
Jason Soroko, Senior Fellow at Sectigo, a Scottsdale, Arizona-based supplier of complete certificates lifecycle administration (CLM) weighed on within the newest growth stating that Helldown ransomware represents a classy evolution of recent malware.
“Helldown is a chief instance of how cybercriminals are piecing collectively the entire components of recent malware to create a formidable menace. All the components of this malware variant have been seen earlier than, however we’re more and more seeing malware that’s strengthening on all fronts,“ Jason defined.
He added that safety groups should design safety assuming adversaries will use superior, well-crafted methods, reasonably than counting on flaws or oversights by attackers to mitigate threats.
“From fileless execution to robust customized encryption, this malware variant teaches us that we will’t depend on our adversaries to make errors that give us a straightforward solution to mitigate their assaults. Safety architects who’re constructing defensive programs towards assaults resembling this could assume that adversaries are bringing a classy set of instruments with few weak spots.“
RELATED TOPICS
- Telegram-Managed TgRat Trojan Targets Linux Servers
- Hackers Deploy Linux FASTCash Malware for ATM Cashouts
- Play Ransomware Variant Focusing on Linux ESXi Environments
- AcidRain Linux Malware Variant “AcidPour” Focusing on Ukraine
- Linux Malware ‘Perfctl’ Hits Thousands and thousands by Mimicking System Recordsdata