Chinese language risk actors use a customized post-exploitation toolkit named ‘DeepData’ to take advantage of a zero-day vulnerability in Fortinet’s FortiClient Home windows VPN consumer that steal credentials.
The zero-day permits the risk actors to dump the credentials from reminiscence after the person authenticated with the VPN machine
Volexity researchers report that they found this flaw earlier this summer time and reported it to Fortinet, however the difficulty stays unfixed, and no CVE has been assigned to it.
“Volexity reported this vulnerability to Fortinet on July 18, 2024, and Fortinet acknowledged the issue on July 24, 2024,” explains the report.
“At the time of writing, this issue remains unresolved and Volexity is not aware of an assigned CVE number.”
Concentrating on VPN credentials
The assaults are performed by Chinese language hackers named “BrazenBamboo,” identified for creating and deploying superior malware households concentrating on Home windows, macOS, iOS, and Android techniques in surveillance operations.
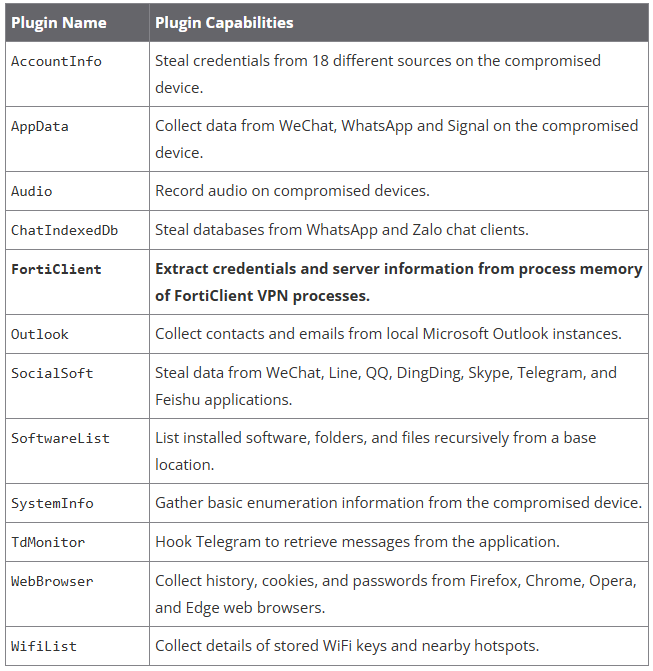
Volexity explains that the risk actors make the most of quite a few malware as a part of their assaults, together with the LightSpy and DeepPost malware.
LightSpy is a multi-platform spyware and adware for information assortment, keylogging, browser credential theft, and the monitoring of communications. The DeepPost malware is used to steal information from compromised gadgets.
Volexity’s report focuses on DeepData, a modular post-exploitation software for Home windows, which employs a number of plugins for focused information theft.
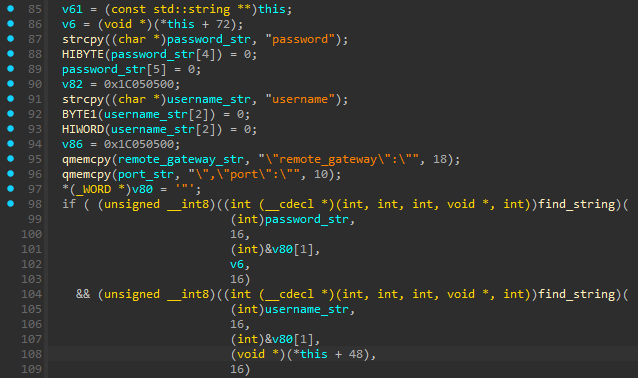
Its newest model, noticed final summer time, DeepData features a FortiClient plugin that exploits a zero-day vulnerability within the product to extract credentials (usernames, passwords) and VPN server info.
DeepData locates and decrypts JSON objects in FortiClient’s course of reminiscence the place the credentials persist, and exfiltrates them to the attacker’s server utilizing DeepPost.
Supply: Volexity
By compromising VPN accounts, BrazenBamboo can achieve preliminary entry to company networks, the place they’ll then unfold laterally, achieve entry to delicate techniques, and usually broaden espionage campaigns.
Supply: Volexity
FortiClient zero-day
Volexity found that DeepData leverages the FortiClient zero in mid-July 2024 and located that it is just like a 2016 flaw (additionally with out a CVE), the place hardcoded reminiscence offsets uncovered credentials.
Nonetheless, the 2024 vulnerability is new and distinct and works solely on latest releases, together with the newest, v7.4.0, indicating that it is seemingly tied to latest modifications within the software program.
Volexity explains that the issue is FortiClient’s failure to clear delicate info from its reminiscence, together with username, password, VPN gateway, and port, which stay in JSON objects in reminiscence.
Till Fortinet confirms the flaw and releases a fixing patch, it is suggested to limit VPN entry and monitor for uncommon login exercise.
Indicators of compromise related to the newest BrazenBamboo marketing campaign are out there right here.
BleepingComputer contacted Fortinet to ask concerning the reported zero-day vulnerability and whether or not they plan to difficulty a safety replace quickly, however we’re nonetheless ready for his or her response.
