Faux Bitwarden password supervisor ads on Fb are pushing a malicious Google Chrome extension that collects and steals delicate consumer information from the browser.
Bitwarden is a well-liked password supervisor app with a “free” tier that includes end-to-end encryption, cross-platform assist, MFA integration, and a user-friendly interface.
Its consumer base has been rising steadily prior to now couple of years, particularly following safety breaches of rivals that led many to search for alternate options.
A brand new malvertising marketing campaign impersonating Bitwarden was noticed by Bitdefender Labs, whose researchers report that the operation launched on November 3, 2024.
Supply: Bitdefender
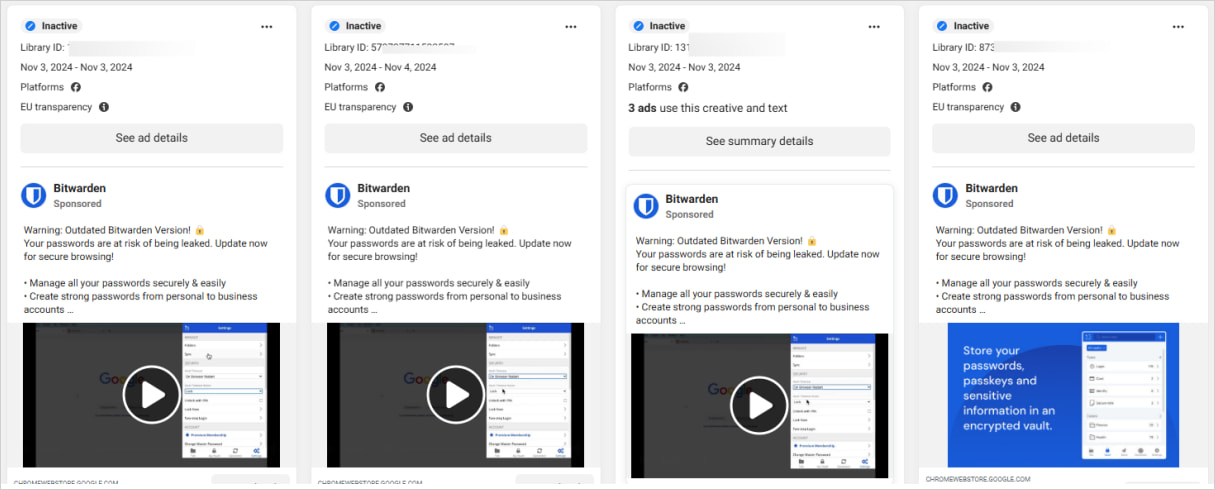
Malicious Fb ads
The Fb promoting marketing campaign warns customers that they are “using an outdated version of Bitwarden,” and must replace this system instantly to safe their passwords.
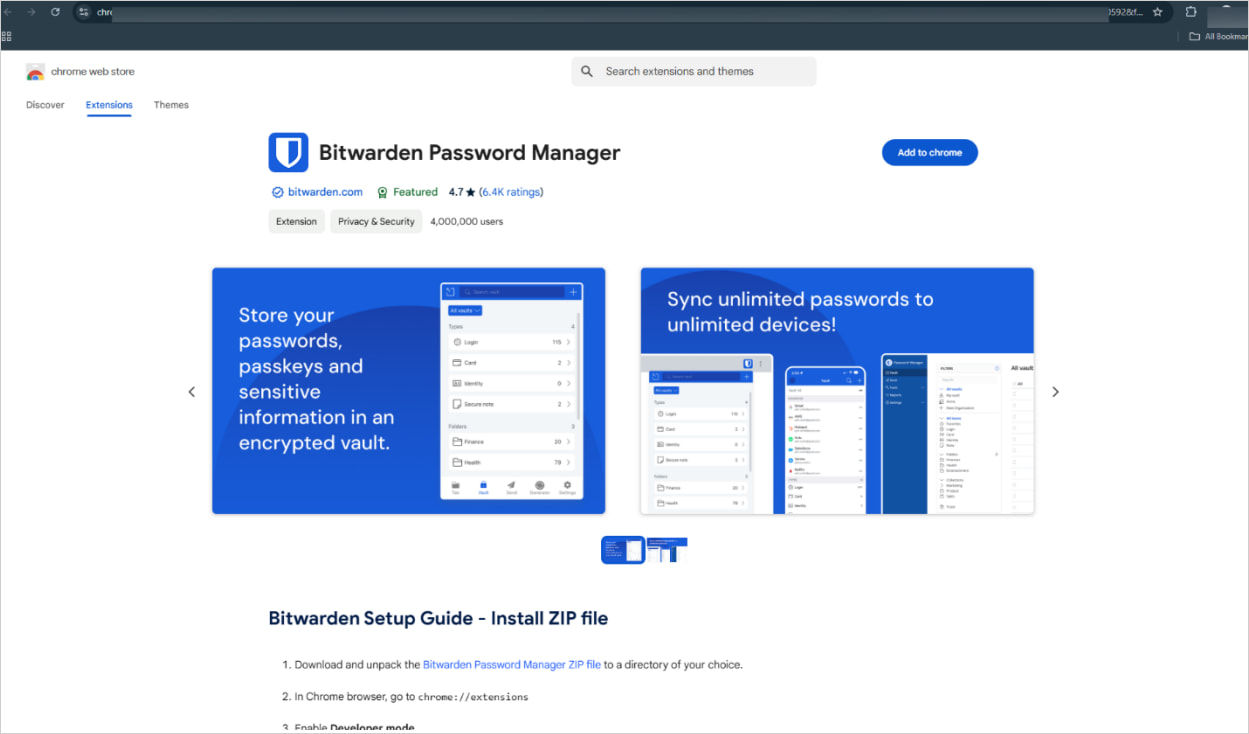
The hyperlink included within the advert is ‘chromewebstoredownload[.]com,’ which pretends to be Google’s official Chrome Net Retailer at ‘chromewebstore.google.com.’
The touchdown web page additionally includes a design carefully resembling the Chrome Net Retailer, together with an ‘Add to Chrome’ button.
Supply: Bitdefender
Nonetheless, as an alternative of the extension routinely putting in whenever you click on the hyperlink, guests are prompted to obtain a ZIP file from a Google Drive folder.
Although this must be a transparent signal of hazard, customers unfamiliar with the Chrome Net Retailer could proceed with the guide set up, following the directions on the webpage.
The set up requires enabling ‘Developer Mode’ on Chrome and manually sideloading the extension on this system, so primarily, safety checks are bypassed.
As soon as put in, the extension registers as ‘Bitwarden Password Supervisor’ model 0.0.1 and secures permissions that allow it to intercept and manipulate consumer actions.
Its most important features are the next:
- Gather Fb cookies, significantly the ‘c_user’ cookie containing the consumer ID.
- Collect IP and geolocation information utilizing public APIs
- Gather Fb consumer particulars, account data, and billing information via Fb’s Graph API
- Manipulates browser DOM to show faux loading messages for legitimacy or deception.
- Encodes delicate information and transmits it to a Google Script URL beneath the attackers’ management.
To mitigate this threat, Bitwarden customers are suggested to disregard advertisements prompting extension updates, as Chrome extensions are routinely up to date when the seller releases a brand new model.
Extensions ought to solely be put in through Google’s official internet retailer or by following hyperlinks from the venture’s official web site, on this case, bitwarden.com.
When putting in a brand new extension, at all times examine the requested permissions and deal with overly aggressive requests involving entry to cookies, community requests, and web site information with excessive suspicion.
