Palo Alto Networks is warning {that a} vital zero-day vulnerability on Subsequent-Technology Firewalls (NGFW) administration interfaces, at the moment tracked as ‘PAN-SA-2024-0015,’ is actively being exploited in assaults.
The flaw was initially disclosed on November 8, 2024, with Palo Alto Networks warning prospects to limit entry to their next-generation firewalls due to a “potential” distant code execution (RCE) vulnerability impacting them.
No indicators of exploitation had been detected at the moment, however now, one week later, the scenario has modified.
“Palo Alto Networks has observed threat activity exploiting an unauthenticated remote command execution vulnerability against a limited number of firewall management interfaces which are exposed to the Internet,” warns an replace on the advisory web page.
“At this time, we believe devices whose access to the Management Interface is not secured as per our recommended best practice deployment guidelines are at increased risk,” warns the seller in the identical bulletin.
The vulnerability, rated with a CVSS v4.0 rating of 9.3 (“critical”), is remotely exploitable and requires no authentication or person interplay.
As soon as an internet-exposed interface is detected, the attacker can ship a specifically crafted request to realize unauthorized management over the firewall, probably enabling them to change guidelines, redirect or intercept community visitors, and switch off safety protections.
Sadly, the seller doesn’t have adequate info to formulate a helpful listing of indicators of compromise at the moment, however recommended the next mitigation steps:
- Configure entry to the firewall administration interface so it’s only accessible from trusted inside IP addresses.
- Block all web entry to the administration interface to stop exploitation.
- Place the administration interface behind a secured community or VPN to make sure entry is managed and authenticated.
- Assessment and implement the safety tips discovered right here.
Regardless of the harmful RCE bug being found every week in the past, Palo Alto Networks has not but made safety updates accessible to impacted purchasers.
“At this time, securing access to the management interface is the best recommended action,” says Palo Alto Networks.
“As we investigate the threat activity, we are preparing to release fixes and threat prevention signatures as early as possible.”
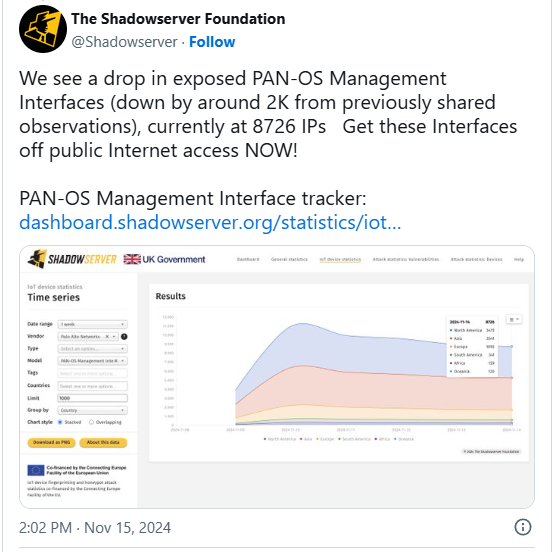
Menace monitoring platform The Shadowserver Basis reported earlier as we speak that it sees roughly 8,700 uncovered interfaces.
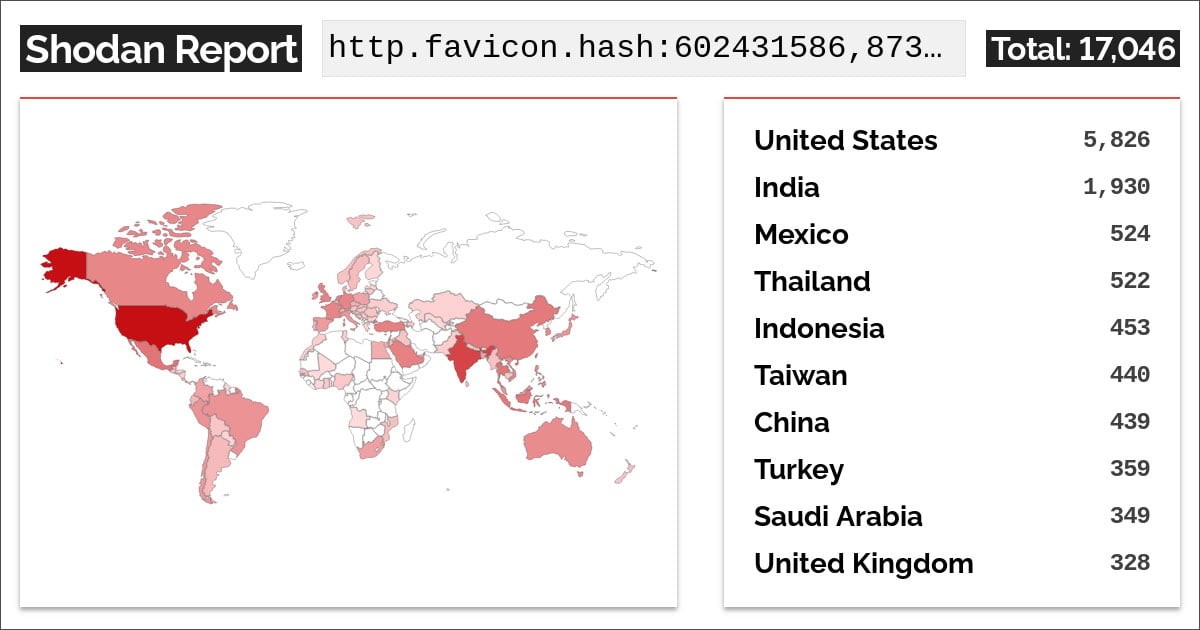
Menace researcher Yutaka Sejiyama carried out his personal scans on Shodan and advised BleepingComputer that he noticed 11,180 IP addresses uncovered on-line related to the Palo Alto administration interface.
“As you know, the results from Shodan are not real-time information. However, during my investigation three days ago, I confirmed that 11,180 of these IPs were actually online,” Sejiyama advised BleepingComputer.
Based on Shodan, a lot of the gadgets are positioned in the USA, adopted by India, Mexica, Thailand, and Indonesia.
Supply: Shodan
To make sure that you might have utilized the mitigations correctly, go to the Property part of the Palo Alto Networks Buyer Help Portal to discover a listing of gadgets with Web-facing administration interfaces, and search for gadgets tagged with ‘PAN-SA-2025-0015.’
If none confirmed up, the scan didn’t detect any internet-exposed administration interfaces. In the event that they do, admins ought to use the steps talked about to safe gadgets.