Suspected Russian hackers have been caught exploiting a just lately patched Home windows vulnerability as a zero-day in ongoing assaults focusing on Ukrainian entities.
The safety flaw (CVE-2024-43451) is an NTLM Hash Disclosure spoofing vulnerability reported by ClearSky safety researchers, which might be exploited to steal the logged-in person’s NTLMv2 hash by forcing connections to a distant attacker-controlled server.
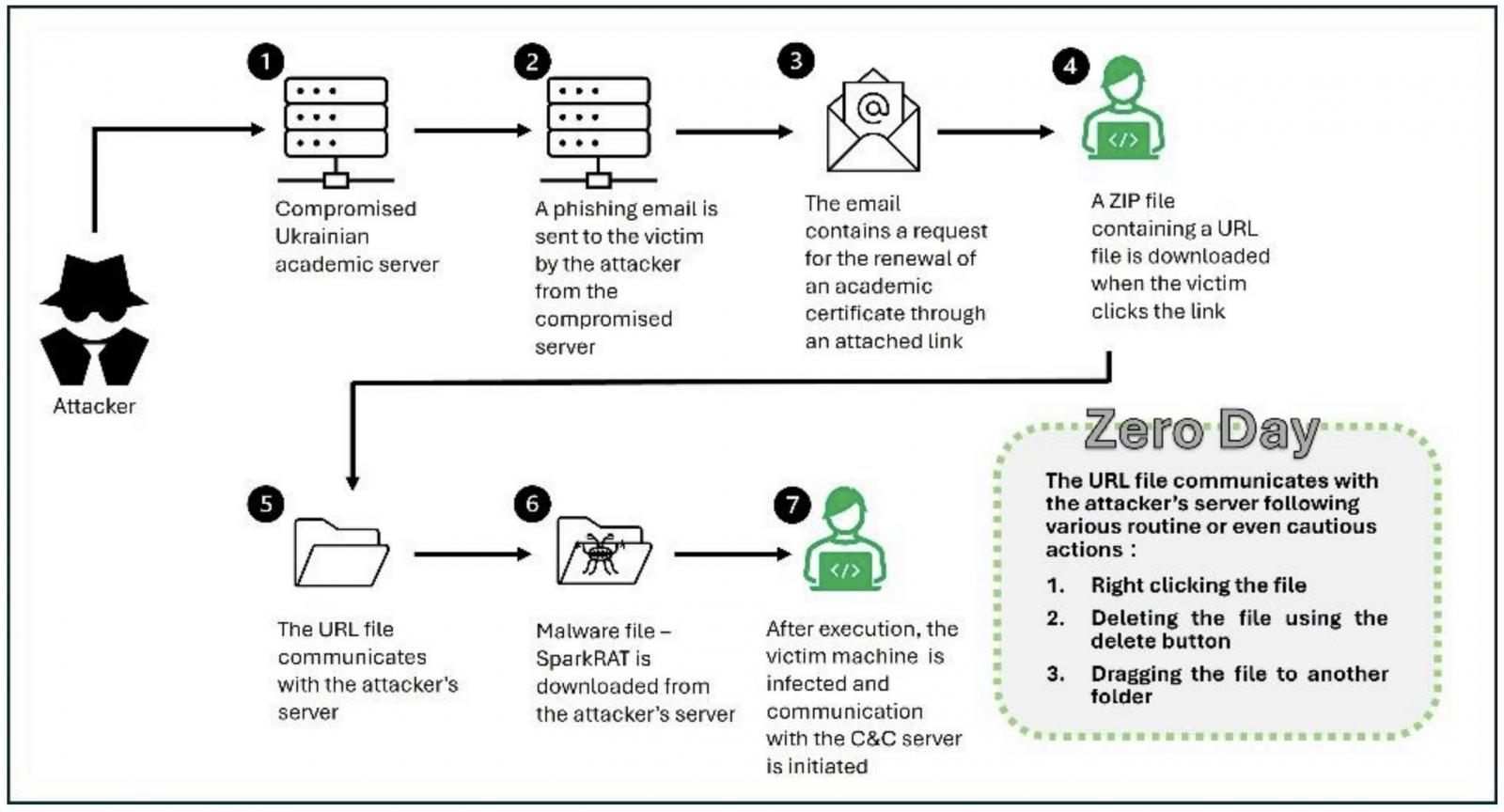
ClearSky noticed this marketing campaign in June after observing phishing emails designed to take advantage of it. These emails contained hyperlinks that will obtain an Web shortcut file hosted on a beforehand compromised server (osvita-kp.gov[.]ua) belonging to the Kamianets-Podilskyi Metropolis Council’s Division of Schooling and Science.
“When the user interacts with the URL file by right-clicking, deleting, or moving it, the vulnerability is triggered,” ClearSky stated.
When this occurs, a connection to a distant server is created to obtain malware payloads, together with the SparkRAT open-source and multi-platform distant entry instrument that permits attackers to manage compromised methods remotely.
Whereas investigating the incident, the researchers have been additionally alerted of an try to steal an NTLM hash by way of the Server Message Block (SMB) protocol. These password hashes can be utilized in “pass-the-hash” assaults or cracked to get a person’s plaintext password.
ClearSky shared this info with Ukraine’s Pc Emergency Response Workforce (CERT-UA), which linked the assaults to hackers a part of a menace group believed to be Russian and tracked as UAC-0194.
Yesterday, Microsoft patched the vulnerability as a part of the November 2024 Patch Tuesday and confirmed ClearSky’s findings, saying that person interplay is required for profitable exploitation.
“This vulnerability discloses a user’s NTLMv2 hash to the attacker who could use this to authenticate as the user,” Redmond’s advisory defined.
“Minimal interaction with a malicious file by a user such as selecting (single-click), inspecting (right-click), or performing an action other than opening or executing could trigger this vulnerability.”
The corporate says CVE-2024-43451 impacts all supported Home windows variations, together with Home windows 10 or later and Home windows Server 2008 and up.
CISA additionally added the vulnerability to its Identified Exploited Vulnerabilities Catalog on Tuesday, ordering them to safe weak methods on their networks by December 3, as mandated by the Binding Operational Directive (BOD) 22-01.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” the cybersecurity company warned.
