A vulnerability in Microsoft Bookings can expose your group to severe safety dangers. Learn the way attackers can exploit this flaw to create convincing impersonations, launch phishing assaults, and compromise delicate information.
Info security-oriented agency Cyberis has found a brand new vulnerability in Microsoft Bookings which permits attackers to create extremely convincing impersonations of key personnel inside a corporation, buy TLS certificates or switch domains/providers counting on e-mail verification comparable to Cloudflare, and hijack accounts.
To your info, Microsoft Bookings is a device used for scheduling appointments. The difficulty lies in an in any other case innocent characteristic: Shared Reserving Pages. By default, customers with applicable Microsoft 365 licenses can create these pages. When a person creates a Shared Reserving Web page, it routinely generates a corresponding account inside Entra, which is Microsoft’s identification and entry administration platform.
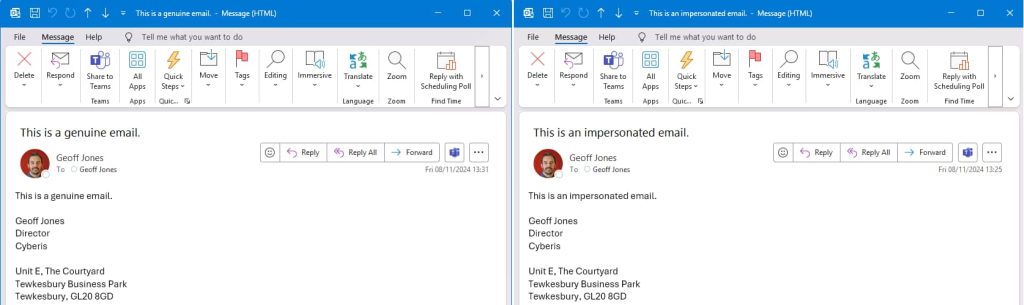
In response to a weblog submit printed by Cyberis’ director Geoff Jones, the difficulty lies in account creation is problematic because of a number of elements. Firstly, the default setting permits any person with an applicable Microsoft 365 license to create Shared Reserving Pages, bypassing normal safety protocols, the place directors sometimes have the only authority to create new accounts.
Secondly, the system routinely generates e-mail addresses primarily based on the Reserving Web page identify, typically following a predictable format (e.g., “FirstnameLastname” turns into “FirstnameLastname@”). Attackers can exploit this predictability to create e-mail addresses resembling official customers, enabling phishing and identification theft.
These accounts even have full e-mail performance, permitting them to ship and obtain emails each internally and externally, resulting in malware distribution, phishing assaults, and compromising of delicate info.
Jones additional explains that these accounts are usually not readily seen in normal administrative instruments just like the Change Admin Heart, which makes it tough for directors to detect and handle them. This hidden characteristic expands the group’s assault floor, making it extra susceptible to account hijacking.
Account hijacking can contain reusing former worker e-mail addresses, creating Reserving Pages with matching e-mail addresses, resetting passwords for exterior providers, or verifying area possession for SSL certificates.
As per Jones, attackers can exploit Bookings in Microsoft 365 to impersonate somebody with larger authority by making a shared reserving web page mimicking a high-profile goal, such because the CEO, and generate a convincing e-mail handle. As an illustration, [email protected] turns into [email protected].
Moreover, they will create legitimate-looking emails, add a profile image or signature equivalent to the goal, and launch extremely plausible phishing assaults towards different staff. They’ll bypass detection mechanisms and goal people with extra entry to delicate info inside the group.
The vulnerability extends past impersonating current staff. Attackers can create Reserving pages with e-mail addresses matching these of former staff, probably reset passwords and achieve entry to exterior providers linked to the e-mail handle, and confirm area possession by acquiring SSL certificates by way of e-mail validation mechanisms.
To mitigate the danger of attackers exploiting Microsoft Reserving’s vulnerabilities, organizations ought to establish hidden mailboxes, prohibit reserving entry, monitor incoming accounts, assessment permissions, and safe high-value e-mail addresses. These steps, mixed with a proactive method to safety configuration, can scale back the danger of attackers exploiting Microsoft Reserving’s vulnerabilities.
RELATED TOPICS
- Hackers Might Exploit Microsoft Groups on macOS to Steal Information
- Hacker Leaks Hundreds of Microsoft and Nokia Worker Particulars
- Russian Midnight Blizzard Breached UK Dwelling Workplace by way of Microsoft
- NAKIVO Backup Answer for MSPs: Information Safety for Microsoft 365
- ZDI Slams Microsoft for Not Crediting It in Final Week’s Patch Tuesday