A latest report from Palo Alto Networks’s Unit 42 exposes the persistent and evolving risk of DNS hijacking, a stealthy tactic cybercriminals use to reroute web site visitors. By leveraging passive DNS evaluation, the cybersecurity firm additionally supplied real-world examples of latest DNS hijacking assaults — highlighting the urgency of countering this hidden hazard.
What’s DNS hijacking?
DNS hijacking entails modifying the responses from focused DNS servers, redirecting customers to attacker-controlled servers as an alternative of the reliable ones they intend to achieve.
DNS hijacking might be achieved in a number of methods:
- Gaining management of the area proprietor’s account, offering entry to DNS server settings: On this state of affairs, the attacker possesses legitimate consumer credentials with the authority to immediately change the DNS server configuration. The attacker might even have legitimate credentials for the area registrar or DNS service supplier and alter the configuration.
- DNS cache poisoning: The attacker impersonates a DNS nameserver and forges a reply, resulting in attacker-controlled content material as an alternative of the reliable one.
- Man-in-the-Center assault: The attacker intercepts the consumer’s DNS queries and offers outcomes that redirect the sufferer to the attacker-controlled content material. This solely works if the attacker is accountable for a system implicated within the DNS question/reply course of.
- Modifying DNS-related system recordsdata, such because the host file in Microsoft Home windows programs. If the attacker has entry to that native file, it’s doable to redirect the consumer to attacker-controlled content material.
Attackers typically use DNS hijacking to redirect customers to phishing web sites that look much like the supposed web sites or to contaminate the customers with malware.
Detecting DNS hijacking with passive DNS
The Unit 42 report described a way to detect DNS hijacking through passive DNS evaluation.
What’s passive DNS?
Passive DNS describes terabytes of historic DNS queries. Along with the area title and the DNS document kind, passive DNS data typically include a “first seen” and a “last seen” timestamp. These data enable customers to hint the IP addresses a site has directed customers to over time.
For an entry to seem in passive DNS, it should be queried by a system whose DNS queries are recorded by passive DNS programs. Because of this probably the most complete passive DNS data typically comes from suppliers with excessive question volumes, equivalent to ISPs or corporations with intensive buyer bases. Subscribing to a passive DNS supplier is usually advisable, as they acquire extra DNS queries than the typical firm, providing a extra full view than native DNS queries alone.
SEE: Every little thing You Have to Know in regards to the Malvertising Cybersecurity Risk (TechRepublic Premium)
Detecting DNS hijacking
Palo Alto Community’s methodology for detecting DNS hijacking begins by figuring out never-seen-before DNS data, as attackers usually create new data to redirect customers. By no means-seen-before domains are excluded from detection as a result of they lack ample historic data. Invalid data are additionally eliminated at this step.
The DNS data are then analyzed utilizing passive DNS and geolocation information primarily based on 74 options. In response to the report, “some features compare the historical usage of the new IP address to the old IP address of the domain name in the new record.” The aim is to detect anomalies that would point out a DNS hijack operation. A machine-learning mannequin then offers a chance rating primarily based on the evaluation.
WHOIS data are additionally checked to forestall a site from being re-registered, which typically leads to a whole IP deal with change that may very well be detected as DNS hijack.
Lastly, lively navigations are carried out on the domains’ IP addresses and HTTPS certificates. Equivalent outcomes point out false positives and may due to this fact be excluded from DNS hijacking operations.
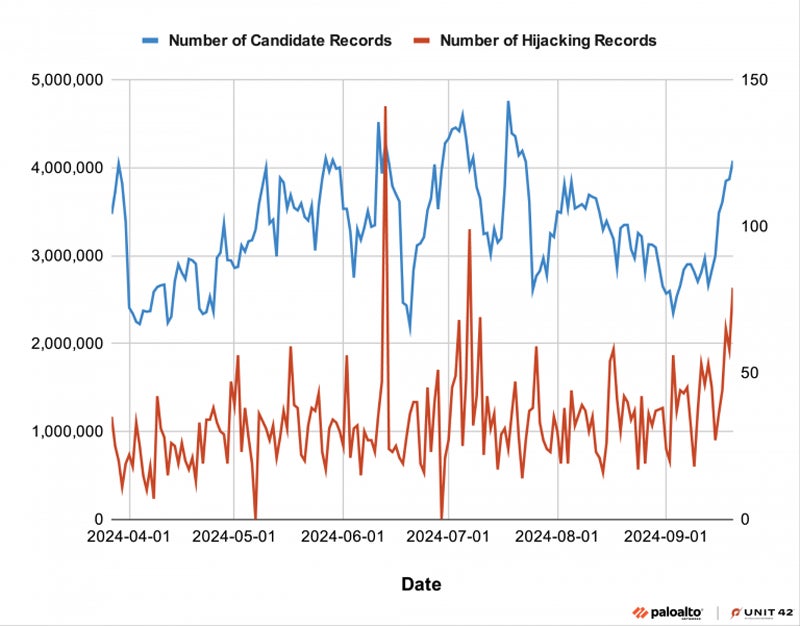
DNS hijack statistics
From March 27 to Sept. 21 2024, researchers processed 29 billion new data, 6,729 of which had been flagged as DNS hijacking. This resulted in a mean of 38 DNS hijack data per day.
Unit 42 signifies that cybercriminals have hijacked domains to host phishing content material, deface web sites, or unfold illicit content material.
DNS hijacking: Actual-world examples
Unit 42 has seen a number of DNS hijack instances within the wild, principally for cybercrime functions. But it is usually doable to make use of DNS hijacking for cyberespionage.
Hungarian political celebration results in phishing
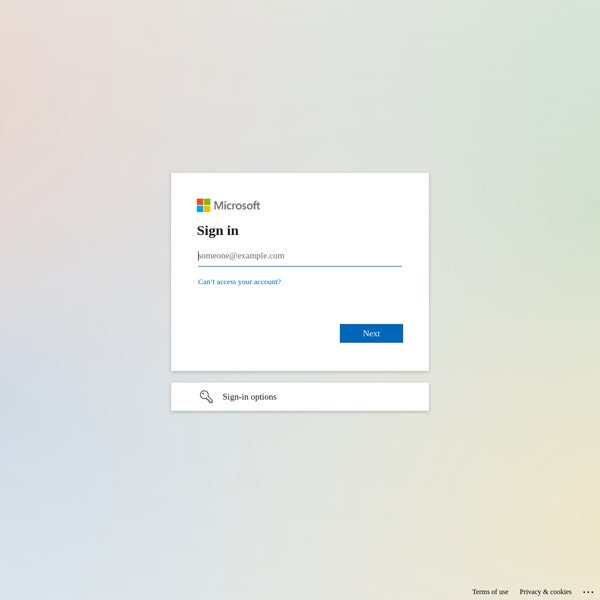
One of many largest political opposition teams to the Hungarian authorities, the Democratic Coalition (DK), has been hosted on the identical subnet of IP addresses in Slovakia since 2017. In January 2024, researchers detected a change within the DK’s web site, which out of the blue resolved to a brand new German IP deal with, resulting in a Microsoft login web page as an alternative of the political celebration’s traditional information web page.
US firm defaced
In Might 2024, two domains of a number one U.S. utility administration firm had been hijacked. The FTP service, which has led to the identical IP deal with since 2014, out of the blue modified. The DNS nameserver was hijacked utilizing the attacker-controlled ns1.csit-host.com.
In response to the analysis, the attackers additionally used the identical nameservers to hijack different web sites in 2017 and 2023. The aim of the operation was to indicate a defaced web page from an activist group.
How corporations can defend themselves from this risk
To guard from these threats, the report urged that organizations:
- Deploy multi-factor authentication to entry their DNS registrar accounts. Establishing a whitelist of IP addresses allowed to entry DNS settings can be a good suggestion.
- Leverage a DNS registrar that helps DNSSEC. This protocol provides a layer of safety by digitally signing DNS communications, making it tougher to intercept and spoof information for risk actors.
- Use networking instruments that examine DNS queries outcomes from third-party DNS servers — equivalent to these from ISPs — to the DNS queries outcomes obtained when utilizing the corporate’s traditional DNS server. A mismatch might point out a change in DNS settings, which is perhaps a DNS hijacking assault.
As well as, all {hardware}, equivalent to routers, should have up-to-date firmware, and all software program should be up-to-date and patched to keep away from being compromised by widespread vulnerabilities.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.