2023 CL0P Development
Rising in early 2019, CL0P was first launched as a extra superior model of its predecessor the ‘CryptoMix’ ransomware, led to by its proprietor CL0P ransomware, a cybercrime organisation. Through the years the group remained lively with vital campaigns all through 2020 to 2022. However in 2023 the CL0P ransomware gang took itself to new heights and have become probably the most lively and profitable ransomware organizations on the planet.
Capitalizing on numerous vulnerabilities and exploits for a number of the world’s largest organizations. The presumed Russian gang took its title from the Russian phrase “klop,” which interprets to “bed bug” and is commonly written as “CLOP” or “cl0p”. As soon as their victims’ information are encrypted, “.clop” extensions are added to their information.
CL0P’s Strategies & Ways
The CL0P ransomware gang (intently related to the TA505. FIN11, and UNC2546 cybercrime teams) was famend for his or her extraordinarily harmful and aggressive campaigns, which focused massive organizations all over the world all through 2023. The “big game hunter” ransomware gang utilized the “steal, encrypt and leak” technique on quite a few massive firms with a particular curiosity for these within the Finance, Manufacturing and Healthcare industries.
CL0P operates a Ransomware-as-a-Service mannequin (RaaS), which regularly employs the ‘steal, encrypt, and leak’ techniques frequent worldwide amongst many ransomware associates. If its victims fail to satisfy the calls for, their knowledge is revealed through the gang’s Tor-hosted leak web site referred to as ‘CL0P^_-LEAKS’. Similar to many different Russian-speaking cyber gangs, their ransomware was unable to function on gadgets positioned within the CIS (Commonwealth of Unbiased States).
LockBit additionally operates as a Ransomware-as-a-service (RaaS) mannequin.
‘In brief, which means that associates make a deposit to make use of the device, then break up the ransom cost with the LockBit group. It has been reported that some associates are receiving a share as excessive as 75%. LockBit’s operators have posted ads for his or her associates program on Russian-language felony boards stating they won’t function in Russia or any CIS international locations, nor will they work with English-speaking builders until a Russian-speaking “guarantor” vouches for them.’ – ‘The Prolificacy of LockBit Ransomware’
SecurityHQ’s World Menace Landscape2024 Forecast talked about CL0P’s resurgence within the ransomware panorama and one to be looking out for in 2024.
third Most Prolific Group 2023
After analyzing the info from ‘CL0P^_-LEAKS’, the menace intelligence group at SecurityHQ was capable of gather knowledge on numerous cybercrime gangs all over the world and assist visualize the extent of CL0P’s rise in exercise all through 2023. The gangs’ transition from remaining outdoors the topmost lively ransomware teams in 2022 to securing the third most prolific in 2023 is one thing that shouldn’t be taken frivolously.
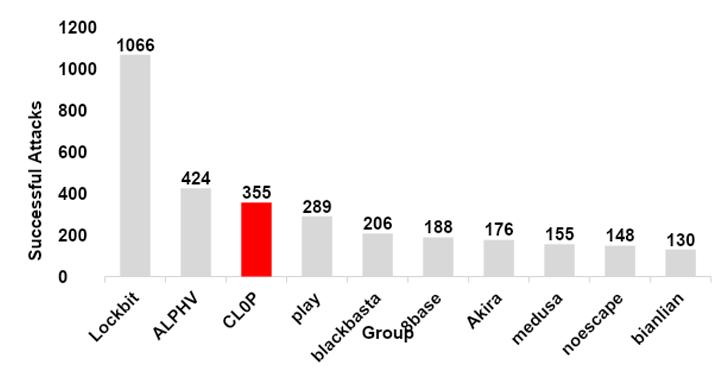 |
| ©2024 SecurityHQ, SecurityHQ Information on Menace Teams Throughout 2023 |
Newest Actions
Over a month-long interval all through March of 2023, the CL0P ransomware gang tried to take advantage of ‘Fortra GoAnywhere MFT’ zero-day vulnerability. Tracked as CVE-2023-0669, attackers have been capable of capitalize on unpatched variations of the software program with web entry to acquire RCE. The vulnerability was patched the next day, however the group had already efficiently focused over 100 organisations.
Then, in April, Microsoft was capable of determine the involvement of two ransomware gangs (CL0P and LockBit) who have been exploiting the tracked CVE-2023-27350 and CVE-2023-27351. Contained contained in the print administration software program referred to as PaperCut, which is a typical device used amongst all the big printing corporations worldwide. The teams have been capable of exploit this vulnerability, efficiently deploying the notorious TrueBot malware that had been used many months prior. An ideal goal for the likes of CL0P, whose techniques have shifted from not simply encrypting the information anymore however extra in the direction of stealing the info to additional extort the organisations. This labored completely as Papercut encompasses a “Print Archiving” device that saves any job/doc that’s despatched by their server.
The group’s main occasion got here in Might; the extensively used MOVEit Switch (CVE-2023-24362) and MOVEit Cloud Software program (CVE-2023-35036) have been actively exploited through an unknown SQL injection vulnerability. CL0P was capable of capitalize on susceptible networks and methods extraordinarily rapidly, extracting delicate knowledge from a number of the world’s largest organizations (BBC, Ernst Younger, PwC, Gen Digital, British Airways, TFL, Siemens, and lots of extra). The group acknowledged they’d deleted all knowledge referring to governments, navy, and hospitals, however with a number of US authorities companies being affected by the MOVEit breach, a bounty of $10 million was set in place that might assist hyperlink them to a international agent.
Lasting Impression of Quadruple Extortion
The group has not solely performed a serious function on the inflow in ransomware exercise all through 2023 however was virtually single handedly liable for the drastic enhance within the common ransomware funds.
CL0P’s operators are famend for going to excessive lengths to get their message throughout. After publicly displaying the proof of the organisations breach, publishing knowledge on their leak web site and their messages being ignored, they are going to go straight to stakeholders and executives to make sure their calls for are met. This is called quadruple extortion.
From single to double, double to triple and now the development to quadruple extortion, it is truthful to say ransomware teams aren’t stopping till they get what they got here for. Similar to the double or triple extortion, quadruple extortion provides a brand new layer which comes within the type of two primary avenues.
- The primary is DDoS assaults, which purpose to close down a corporation’s on-line presence till the ransom is paid.
- The harassment of assorted stakeholders (clients, media, staff, and so forth.) will increase strain on the decision-makers.
Finest Protection In opposition to CL0P Group Defending In opposition to CL0P
To defend in opposition to CLOP all through 2024, it’s endorsed by SecurityHQ to
- Take note of your panorama and your surroundings. Know what’s regular to your surroundings and what’s not so you’ll be able to act rapidly.
- Develop and evaluate your Incident Response Plan, with clear steps proven in order that actions are set within the occasion of a worst-case state of affairs.
- Make sure that Menace Monitoring is in place to determine threats quickly.
- Assessment present cyber safety practices to be sure that the very best practices are getting used.
- These at higher threat, as an illustration, these in industries particularly focused by CLOP (Finance, Manufacturing, Healthcare), or those who maintain delicate knowledge, ought to work with an MSSP to make sure that the very best safety practices are in place.
Menace Intelligence for the Future
SecurityHQ’s Menace Intelligence group is a cohesive world unit devoted to Cyber Menace Intelligence. Their group is concentrated on researching rising threats and monitoring actions of menace actors, ransomware teams, and campaigns to make sure that they keep forward of potential dangers. Past their investigative work, the Intelligence group offers actionable menace intelligence and analysis, enriching the understanding of SecurityHQ’s clients worldwide. United by a typical dedication, the SecurityHQ Menace Intelligence group delivers the insights wanted to navigate the intricacies of the cyber safety menace panorama confidently.
For extra data on these threats, communicate to an skilled right here. Or in case you suspect a safety incident, you’ll be able to report an incident right here.
Observe: This expertly contributed article is written by Patrick McAteer, Cyber Menace Intelligence Analyst at SecurityHQ Dubai, excels in analyzing evolving cyber threats, figuring out dangers, and crafting actionable intelligence stories to empower proactive protection.
