CRON#TRAP is a brand new phishing assault utilizing emulated Linux environments to bypass safety and set up persistent backdoors. Leveraging QEMU and Chisel, hackers acquire covert entry to steal knowledge and management techniques.
Securonix Risk Analysis has found a complicated phishing marketing campaign, “CRON#TRAP,” that leverages a novel method to infiltrate techniques and set up persistent backdoors. This artistic assault methodology includes deploying emulated Linux environments inside compromised endpoints, particularly Tiny Core Linux.
Multi-Stage Assault Strategy of CRON#TRAP
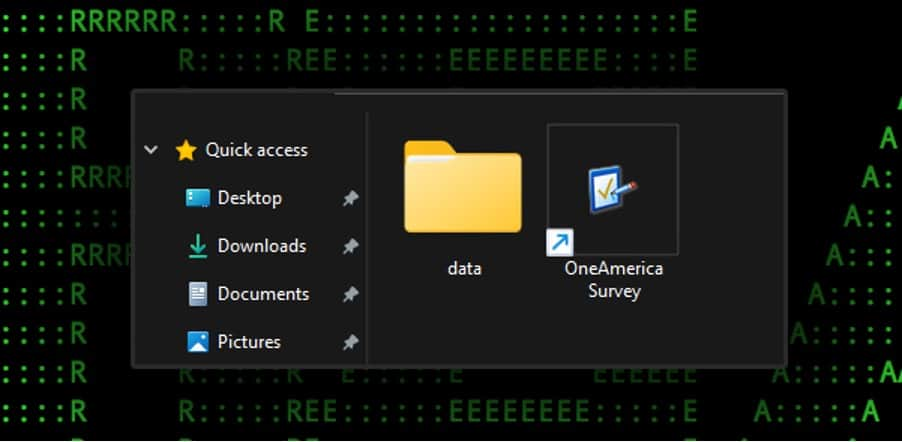
The CRON#TRAP marketing campaign employs a multi-stage assault methodology to compromise goal techniques and set up persistent backdoors. The preliminary an infection vector sometimes includes a phishing e-mail containing a malicious ZIP and a shortcut file (named OneAmerica Survey.zip and OneAmerica Survey.lnk).
The malicious attachment is commonly disguised as a reputable doc, reminiscent of a survey or software program replace, to trick customers into executing it. When executed, this shortcut file downloads the big ZIP archive, which incorporates the mandatory parts for the emulated Linux setting.
Emulated Linux Setting Deployment
The downloaded archive features a customized Linux distribution, reminiscent of Tiny Core Linux, and the QEMU virtualization instrument. The batch file ‘start.bat’ shows a server error message, indicating a server-side survey hyperlink problem. The script executes the QEMU course of and command line to begin an emulated Linux setting, making a hid setting for the attacker’s actions.
The explorer.exe course of executes an HTTPS-hosted picture, which the consumer’s default browser shows. This enables the attacker to additional masks the exercise as reputable system behaviour, avoiding detection.
Set up of the Chisel Tunneling Instrument
Inside the emulated Linux setting, the attacker installs a pre-configured Chisel consumer, a tunneling instrument that establishes a covert communication channel with a distant command-and-control (C&C) server. Via the Chisel tunneling instrument, attackers set up safe tunnels over HTTP and SSH protocols.
The instrument is configured with particular settings, such because the goal C&C server tackle, port quantity, and encryption parameters, permitting it to robotically hook up with the attacker’s infrastructure.
The Chisel consumer is executed inside the emulated Linux setting, activating the backdoor each time the system boots or is began. This safe, encrypted connection permits attackers to transmit knowledge and instructions between the compromised system and the attacker’s infrastructure.
This safe connection permits attackers to execute arbitrary instructions, obtain malware, steal delicate knowledge, manipulate system settings, exfiltrate delicate knowledge, deploy persistence mechanisms, modify registry settings, create scheduled duties, set up rootkits, and unfold to different community techniques.
Evasion Strategies Utilizing Official Instruments
By disguising malicious exercise inside a reputable virtualization instrument, QEMU, attackers can bypass conventional safety measures and set up a stealthy foothold. Moreover, utilizing the Chisel tunneling instrument permits attackers to take care of persistent entry and execute additional malicious actions.
“The attacker’s reliance on legitimate software like QEMU and Chisel adds an additional layer of evasion, as these tools are unlikely to trigger alerts in many environments,” the report learn.
The CRON#TRAP marketing campaign highlights cybercriminals’ evolving ways, together with emulating environments and reputable software program abuse. This methodology permits attackers to realize persistent entry to compromised techniques, underscoring the significance of consideration towards suspicious emails.
RELATED TOPICS
- Telegram-Managed TgRat Trojan Targets Linux Servers
- Hackers Deploy Linux FASTCash Malware for ATM Cashouts
- Play Ransomware Variant Concentrating on Linux ESXi Environments
- AcidRain Linux Malware Variant “AcidPour” Concentrating on Ukraine
- Linux Malware ‘Perfctl’ Hits Thousands and thousands by Mimicking System Information