A comparatively new ransomware operation named Interlock assaults organizations worldwide, taking the bizarre method of making an encryptor to focus on FreeBSD servers.
Launched on the finish of September 2024, Interlock has since claimed assaults on six organizations, publishing stolen knowledge on their knowledge leak website after a ransom was not paid. One of many victims is Wayne County, Michigan, which suffered a cyberattack initially of October.
Not a lot is understood concerning the ransomware operation, with a number of the first data coming from incident responder Simo in early October, who discovered a brand new backdoor [VirusTotal] deployed in an Interlock ransomware incident.
Quickly after, cybersecurity researcher MalwareHuntTeam discovered what was believed to be a Linux ELF encryptor [VirusTotal] for the Interlock operation. Sharing the pattern with BleepingComputer, we tried to check it on a digital machine, the place it instantly crashed.
Analyzing the strings inside the executable indicated that it was compiled particularly for FreeBSD, with the Linux “File” command additional confirming it was compiled on FreeBSD 10.4.
interlock.elf: ELF 64-bit LSB executable, x86-64, model 1 (SYSV), statically linked, BuildID[sha1]=c7f876806bf4d3ccafbf2252e77c2a7546c301e6, for FreeBSD 10.4, FreeBSD-style, not stripped
Nevertheless, even when testing the pattern on a FreeBSD digital machine, BleepingComputer was unable to get the pattern to correctly execute.
Whereas it is not uncommon to see Linux encryptors created to focus on VMware ESXi servers and digital machines, it’s uncommon to see ones created for FreeBSD. The one different ransomware operation identified to have created FreeBSD encryptors is the now-defunct Hive ransomware operation, which was disrupted by the FBI in 2023.
This week, researchers from cybersecurity agency Development Micro shared on X that they discovered a further pattern of the FreeBSD ELF encryptor [VirusTotal] and a pattern of the operation’s Home windows encryptor [VirusTotal].
Development Micro additional stated that the menace actors doubtless created a FreeBSD encryptor because the working system is usually utilized in essential infrastructure, the place assaults may cause widespread disruption.
“Interlock targets FreeBSD as it’s widely utilized in servers and critical infrastructure. Attackers can disrupt vital services, demand hefty ransoms, and coerce victims into paying,” explains Development Micro.
The Interlock ransomware
Whereas BleepingComputer couldn’t get the FreeBSD encryptor working, the Home windows model ran with out a downside on our digital machine.
In response to Development Micro, the Home windows encryptor will clear Home windows occasion logs, and if self-deletion is enabled, will use a DLL to delete the primary binary utilizing rundll32.exe.
When encrypting information, the ransomware will append the .interlock extension to all encrypted file names, and create a ransom be aware in every folder.
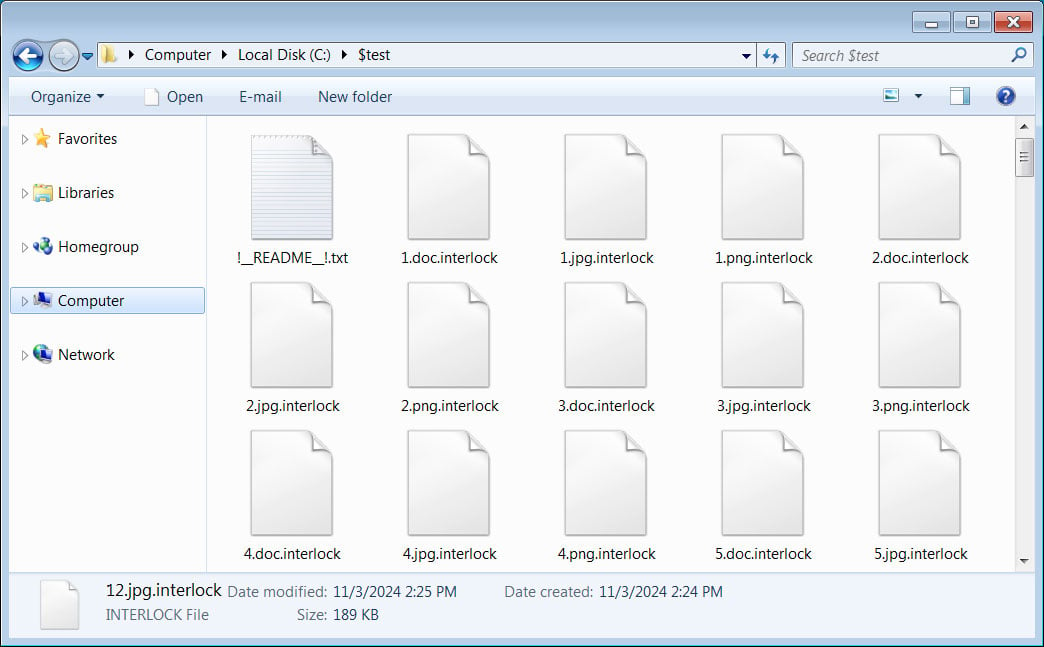
Supply: BleepingComputer
This ransom be aware is known as !__README__!.txt and briefly describes what occurred to the sufferer’s information, makes threats, and hyperlinks to the Tor negotiation and knowledge leak websites.
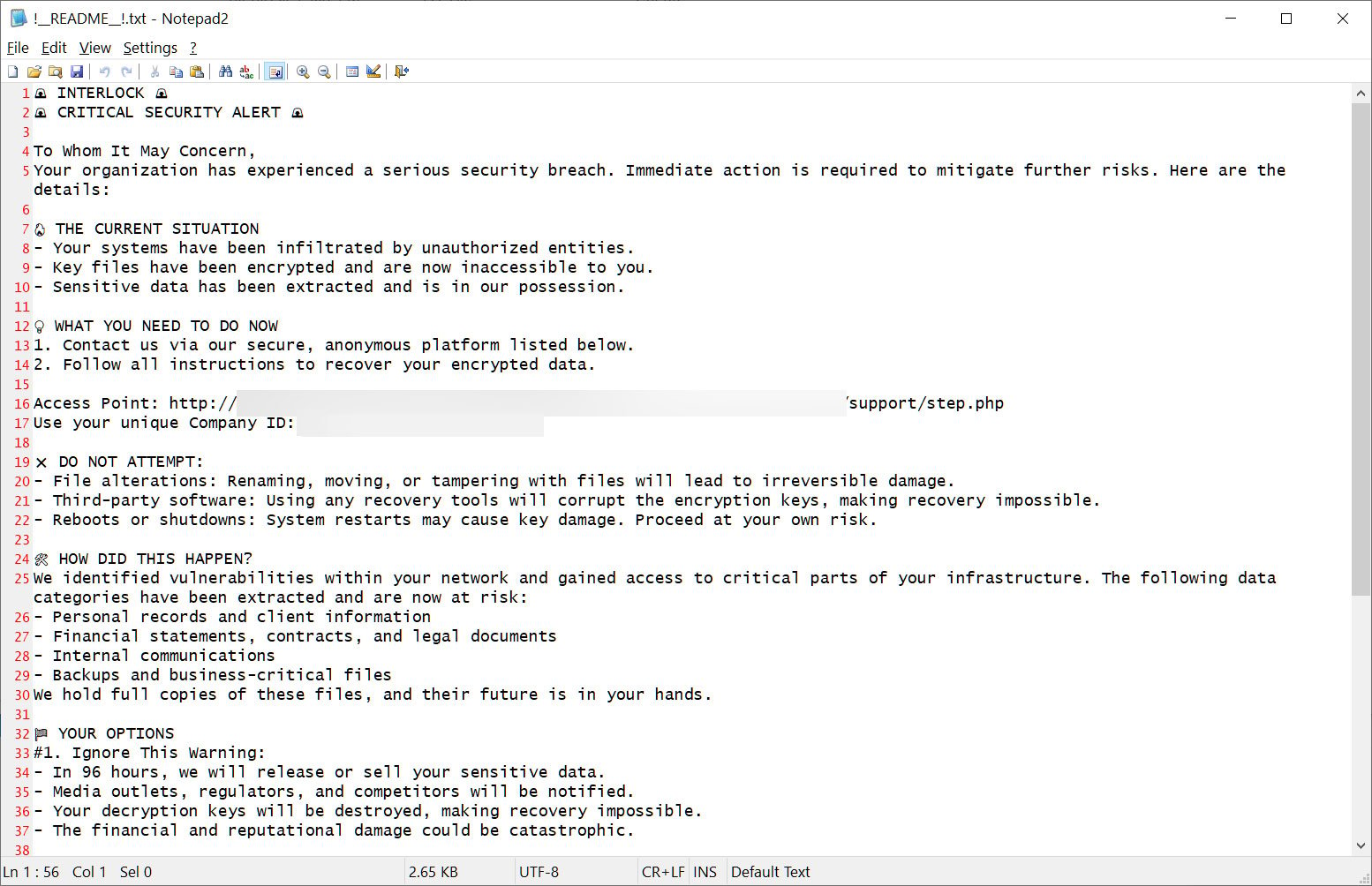
Supply: BleepingComputer
Every sufferer has a novel “Company ID” that’s used together with an e mail handle to register on the menace actor’s Tor negotiation website. Like many different latest ransomware operations, the victim-facing negotiation website simply features a chat system that can be utilized to speak with the menace actors.
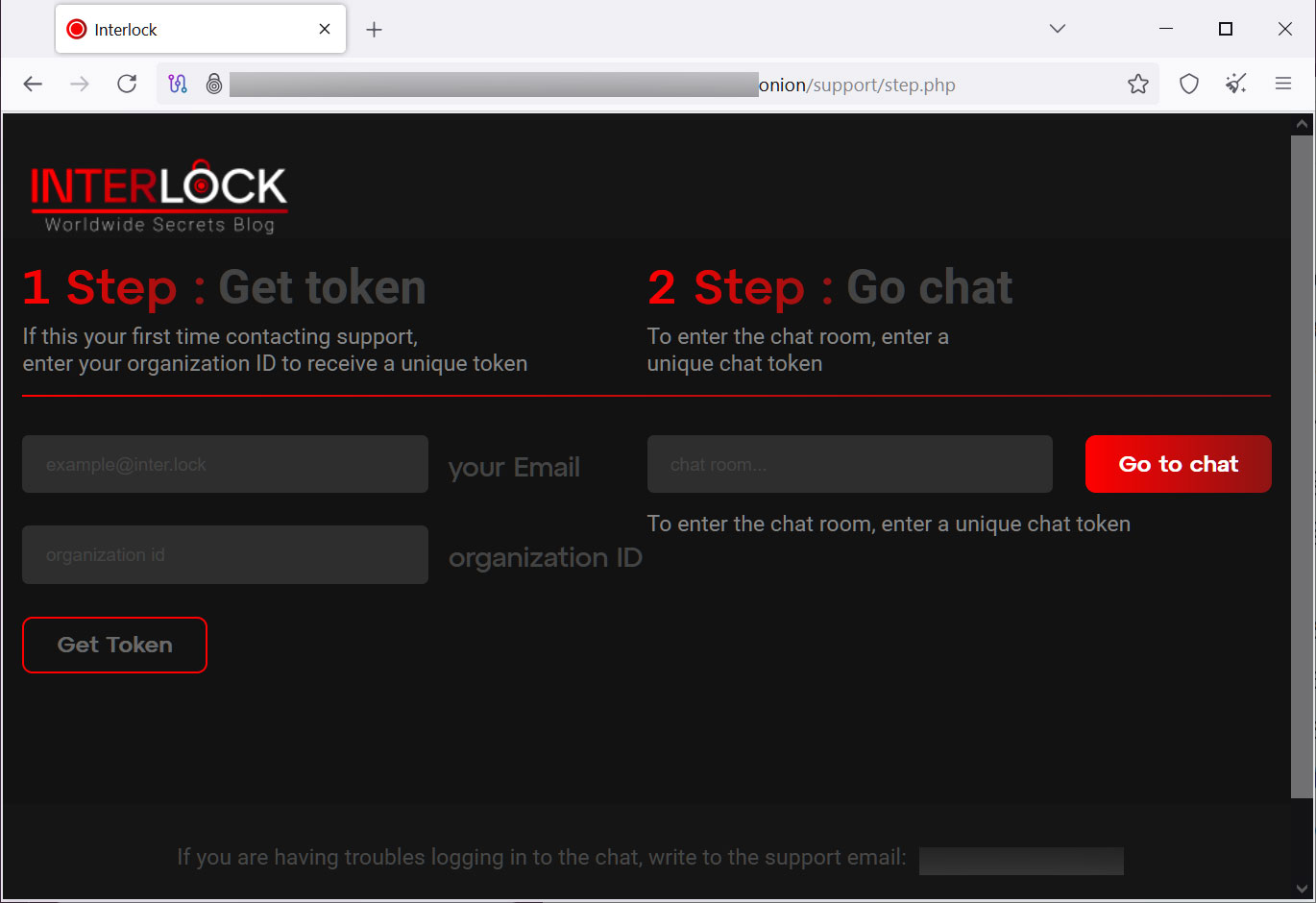
Supply: BleepingComputer
When conducting assaults, Interlock will breach a company community and steal knowledge from servers whereas spreading laterally to different gadgets. When performed, the menace actors deploy the ransomware to encrypt all the information on the community.
The stolen knowledge is used as a part of a double-extortion assault, the place the menace actors threaten to publicly leak it if a ransom is just not paid.
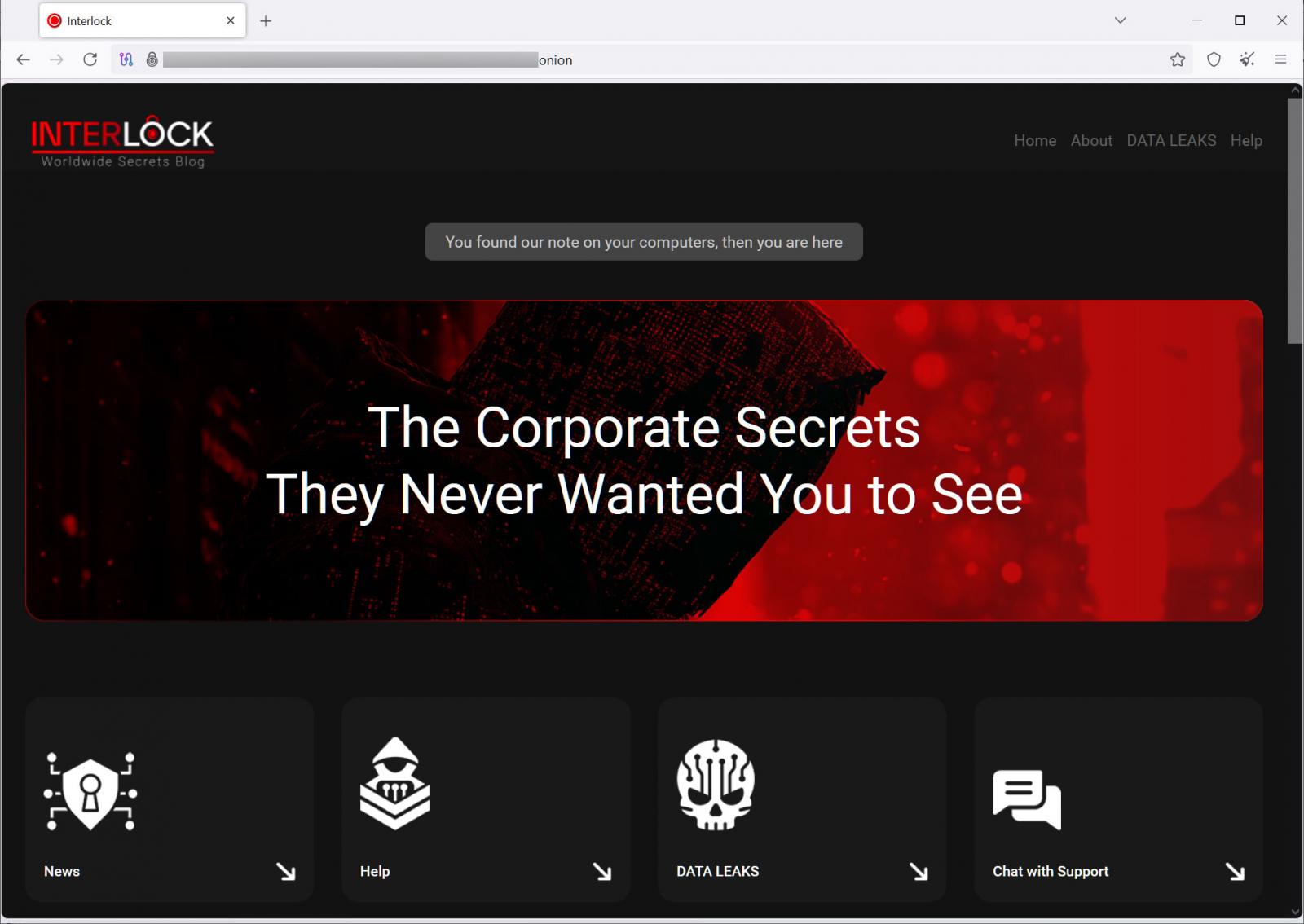
Supply: BleepingComputer
BleepingComputer has realized that the ransomware operation calls for ransoms starting from a whole lot of hundreds of {dollars} to tens of millions, relying on the scale of the group.
