A phishing marketing campaign dubbed ‘Phish n’ Ships’ has been underway since no less than 2019, infecting over a thousand respectable on-line shops to advertise faux product listings for hard-to-find gadgets.
Unsuspecting customers clicking on these merchandise are redirected to a community of tons of of faux net shops that steal their private particulars and cash with out transport something.
Based on HUMAN’s Satori Risk Intelligence workforce that found Phish n’ Ships, the marketing campaign has impacted tons of of hundreds of shoppers, inflicting estimated losses of tens of hundreds of thousands of {dollars}.
The Phish n’ Ships operation
The assault begins by infecting respectable websites with malicious scripts by exploiting identified vulnerabilities (n-days), misconfigurations, or compromised administrator credentials.
As soon as a website is compromised, the menace actors add inconspicuously named scripts resembling “zenb.php” and “khyo.php,” with which they add faux product listings.
These things are full with Search engine optimisation-optimized metadata to extend their visibility on Google search outcomes, from the place victims may be drawn.
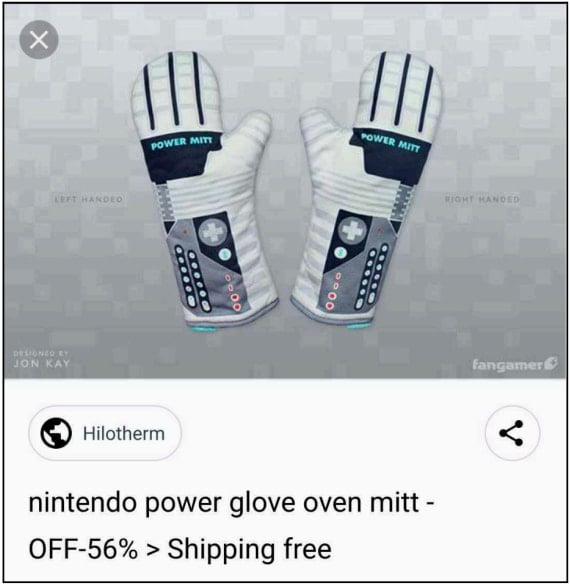
Supply: HUMAN
When victims click on on these hyperlinks, they’re redirected by means of a sequence of steps that finally result in fraudulent web sites, usually mimicking the interface of the compromised e-store or utilizing the same design.
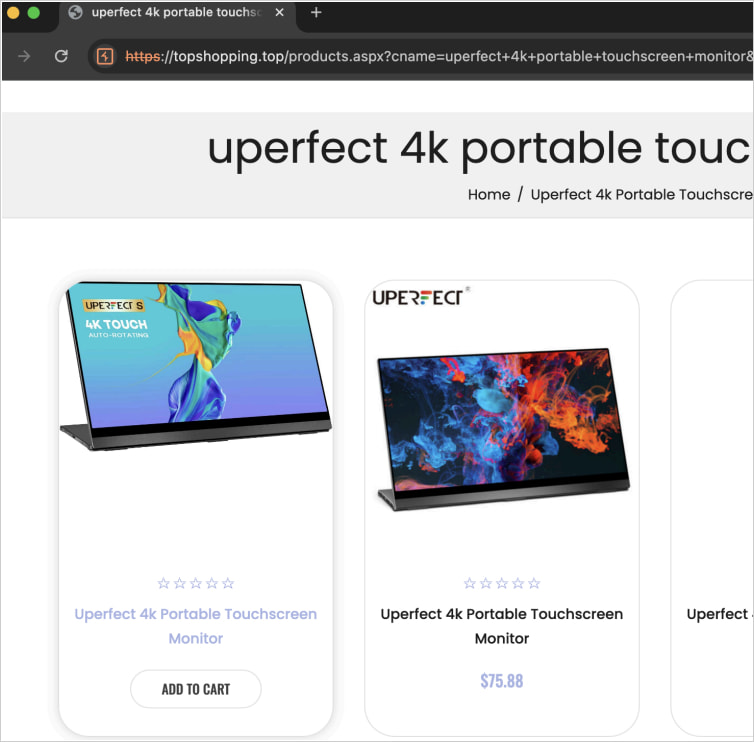
Supply: HUMAN
All of those faux outlets are related to a community of fourteen IP addresses, based on Satori researchers, they usually all include a selected string within the URL that makes them identifiable.
Trying to buy the merchandise on the faux store takes victims by means of a faux checkout course of designed to seem respectable however doesn’t embrace any knowledge verification, an indication of potential fraud.
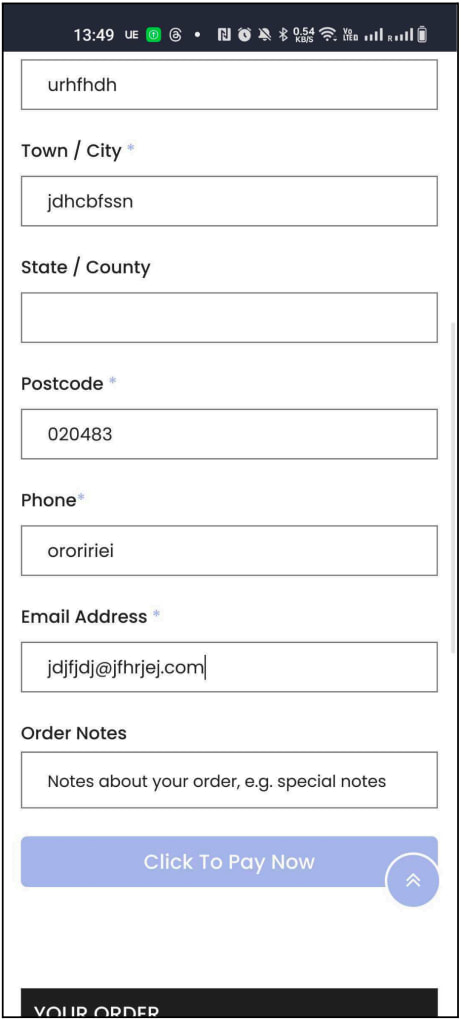
Supply: HUMAN
The malicious websites steal the data victims enter within the order fields, together with their bank card particulars, and full the fee utilizing a semi-legitimate fee processor account managed by the attacker.
The bought merchandise isn’t shipped to the customer, so the victims lose each their cash and knowledge.
Satori has discovered that over the 5 years throughout which Phish n’ Ships has been lively, the menace actors abused a number of fee suppliers to money out the proceeds of the rip-off.
Extra lately, they tailored to implementing a fee mechanism on among the faux e-shop websites to allow them to snatch the sufferer’s bank card particulars instantly.
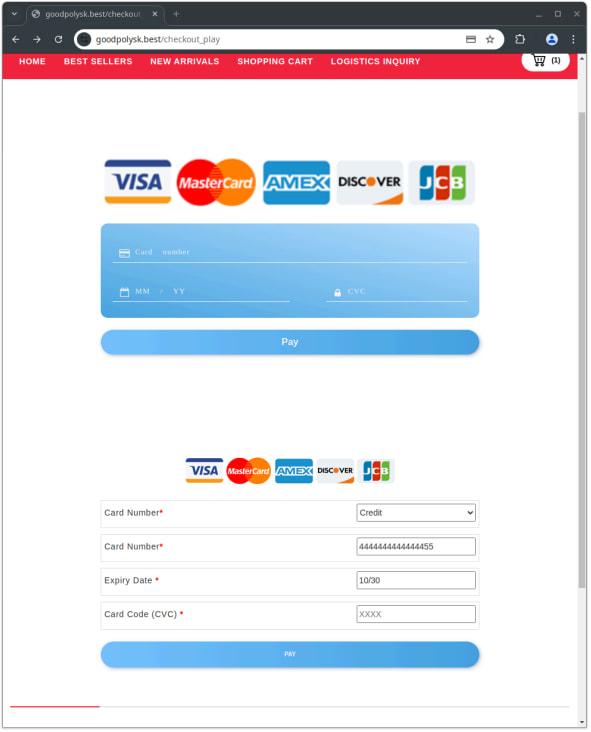
Supply: HUMAN
Marketing campaign disrupted
HUMAN and its companions coordinated a response to Phish n’ Ships, informing most of the impacted organizations and reporting the faux listings to Google so that they could possibly be eliminated.
As of writing, most malicious search outcomes have been cleaned, and practically all recognized outlets have been taken offline.
Additionally, fee processors who facilitated cashouts for the fraudsters had been knowledgeable accordingly and eliminated the offending accounts from their platforms, considerably disrupting the menace actor’s skill to generate revenue.
Regardless of all that, the menace actors can adapt to this disruption. Though Satori continues monitoring the exercise for resurgence, it is unlikely that they may quit and never attempt to set up a brand new shopper-defrauding community.
Customers are really useful to look out for uncommon redirects when looking e-commerce platforms, validate they’re on the proper store URL when making an attempt to purchase an merchandise, and report fraudulent fees to their financial institution and authorities as quickly as doable.
