A big-scale malicious operation named “EmeraldWhale” scanned for uncovered Git configuration information to steal over 15,000 cloud account credentials from hundreds of personal repositories.
In line with Sysdig, who found the marketing campaign, the operation entails utilizing automated instruments that scan IP ranges for uncovered Git configuration information, which can embody authentication tokens.
These tokens are then used to obtain repositories saved on GitHub, GitLab, and BitBucket, that are scanned for additional credentials.
The stolen knowledge was exfiltrated to Amazon S3 buckets of different victims and was subsequently utilized in phishing and spam campaigns and offered on to different cybercriminals.
Whereas exposing Git authentication tokens can permit knowledge theft, it may additionally result in full-blown knowledge breaches like we just lately noticed with the Web Archive.
Uncovered Git configuration information
Git configuration information, equivalent to /.git/config or .gitlab-ci.yml, are used to outline varied choices like repository paths, branches, remotes, and typically even authentication info like API keys, entry tokens, and passwords.
Builders would possibly embody these secrets and techniques in personal repositories for comfort, making knowledge transmissions and API interactions simpler with out configuring or performing authentication every time.
This isn’t dangerous so long as the repository is appropriately remoted from public entry. Nonetheless, if the /.git listing containing the configuration file is mistakenly uncovered on a web site, menace actors utilizing scanners may simply find and browse them.
If these stolen configuration information comprise authentication tokens, they can be utilized to obtain related supply code, databases, and different confidential assets not meant for public entry.
The menace actors behind EmeraldWhale use open-source instruments like ‘httpx’ and ‘Masscan’ to scan web sites hosted on an estimated 500 million IP addresses divided into 12,000 IP ranges.
Sysdig says the hackers even created information itemizing each attainable IPv4 handle, spanning over 4.2 billion entries, to streamline future scans.
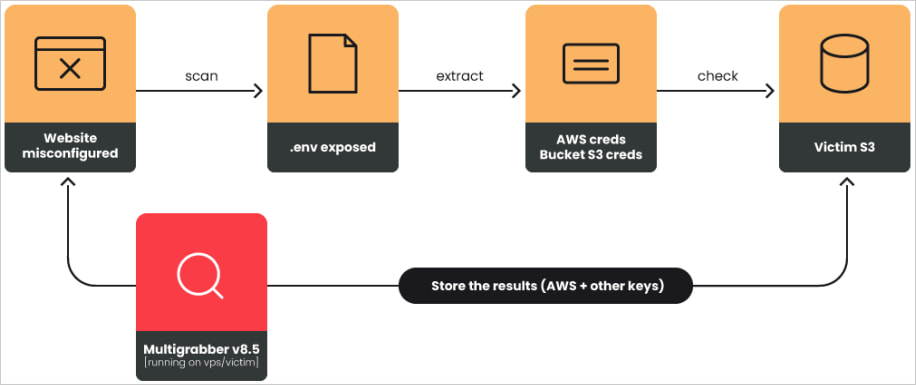
The scans merely test if the /.git/config file and surroundings information (.env) in Laravel functions are uncovered, which can additionally comprise API keys and cloud credentials.
As soon as an publicity is recognized, the tokens are verified utilizing ‘curl’ instructions to numerous APIs and, if legitimate, are used to obtain personal repositories.
These downloaded repositories are scanned once more for authentication secrets and techniques for AWS, cloud platforms, and electronic mail service suppliers. The menace actors used the uncovered authentication tokens for electronic mail platforms to conduct spam and phishing campaigns.
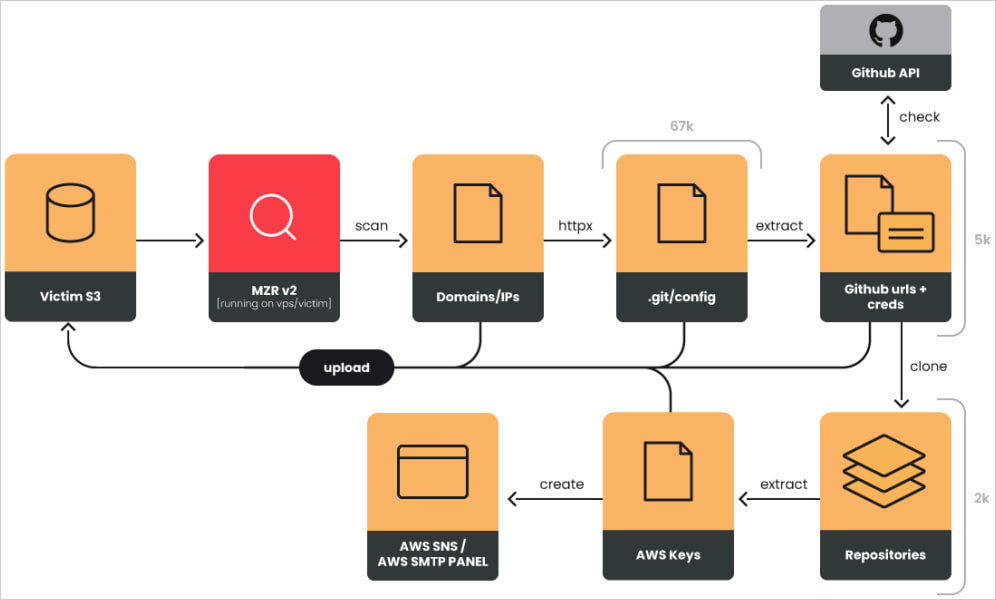
Sysdig noticed using two commodity toolsets to streamline this large-scale course of, particularly MZR V2 (Mizaru) and Seyzo-v2.
Supply: Sysdig
For Laravel, the Multigrabber v8.5 software was used to test domains for .env information, steal them, after which classify the knowledge based mostly on its usability potential.
Supply: Sysdig
Evaluating the stolen knowledge
Sysdig examined the uncovered S3 bucket and located one terabyte price of secrets and techniques in it, together with stolen credentials and logging knowledge.
Primarily based on the collected knowledge, EmeraldWhale stole 15,000 cloud credentials from 67,000 URLs that uncovered configuration information.
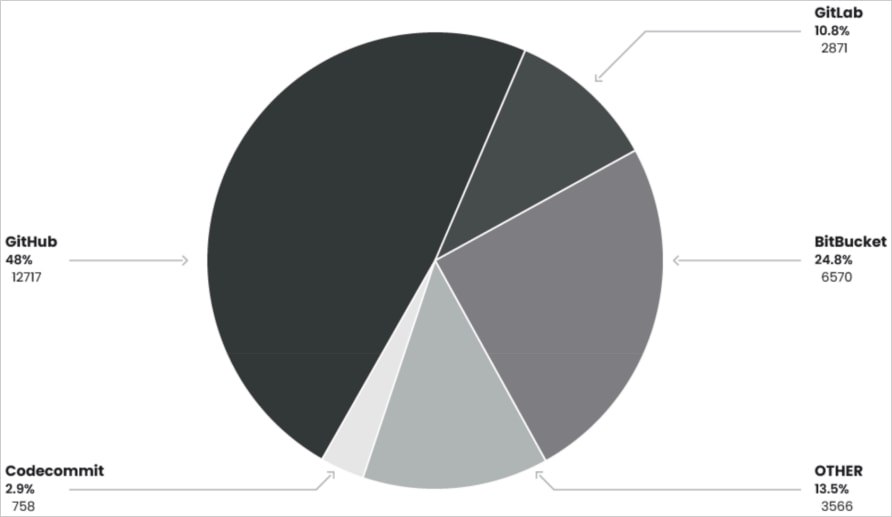
Of the uncovered URLs, 28,000 corresponded to Git repositories, 6,000 have been GitHub tokens, and a notable 2,000 have been validated as energetic credentials.
Apart from main platforms like GitHub, GitLab, and BitBucket, the hackers additionally focused 3,500 smaller repositories belonging to small groups and particular person builders.
Supply: Sysdig
Sysdig says that mere lists of URLs pointing to uncovered Git configuration information are offered on Telegram for about $100, however these exfiltrating the secrets and techniques and validating them have much more vital monetization alternatives.
The researchers word that this marketing campaign is not notably subtle, depends on commodity instruments and automation, but nonetheless managed to steal hundreds of secrets and techniques that may probably result in catastrophic knowledge breaches.
Software program builders can mitigate the chance through the use of devoted secret administration instruments to retailer their secrets and techniques and utilizing surroundings variables to configure delicate settings at runtime as a substitute of hardcoding them in Git configuration information.
