Russian hackers launched a focused malware marketing campaign through Telegram, aimed toward Ukrainian navy recruits. Disguised as recruitment instruments, the malware steals information and spreads disinformation, weakening Ukraine’s defence efforts.
A brand new report by Google’s Menace Intelligence Group (TAG) exposes a cyber marketing campaign concentrating on Ukrainian males eligible for navy service. The marketing campaign, linked to Russian state-sponsored hackers, orchestrated by the UNC5812 group, makes use of a mixture of malware and disinformation.
It’s price noting that originally of October 2024, stories indicated that Russian cyber operations in opposition to Ukraine through the first half of the 12 months shifted from broad-spectrum assaults to a extra focused strategy, particularly specializing in Ukraine’s navy and defence sectors.
For the newest marketing campaign, the rapid goal is to compromise the gadgets of potential Ukrainian navy recruits. Hackers are distributing malicious software program to assist Ukrainian navy recruits find recruitment facilities. These packages are laced with malware that may steal delicate data like browser information, keystrokes, and cryptocurrency pockets particulars.
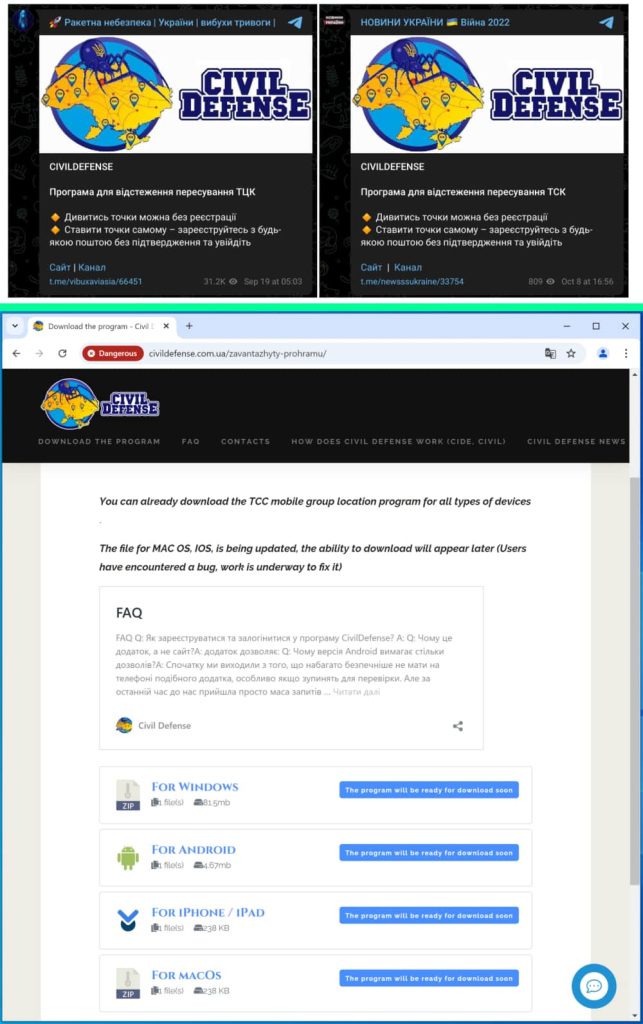
To attain this, the attackers have established a misleading on-line presence via a Telegram channel and web site referred to as “Civil Defense.” Reportedly, the web site was registered in April 2024, however the Telegram channel was created in September
These platforms entice customers with guarantees of useful data and instruments associated to navy conscription. Nevertheless, as soon as victims obtain and set up the provided software program, they unwittingly expose their gadgets to varied malware strains.
For Home windows customers, this sometimes includes the Pronsis Loader, which subsequently delivers the information-stealing PURESTEALER. Android customers, then again, are focused with the CRAXSRAT backdoor, a flexible instrument able to information theft, surveillance, and distant management.
To bypass safety measures, the attackers have employed social engineering strategies, instructing victims to disable Google Play Defend and manually grant permissions to the malicious apps. The marketing campaign additionally includes a concerted effort to unfold disinformation and undermine public morale in Ukraine.
The “Civil Defense” platform disseminates anti-mobilization narratives, promotes false details about the battle, and encourages customers to share movies of alleged unfair practices at recruitment facilities. The web site has a devoted information part rife with fabricated tales depicting purported injustices surrounding mobilization. The content material is posted on pro-Russian social media channels.
The UNC5812 marketing campaign is a part of a broader sample of Russian cyberattacks aimed toward destabilizing Ukraine. By concentrating on potential recruits, the attackers search to erode public help for the navy and hinder Ukraine’s capability to defend itself.
Researchers suspect that UNC5812 is buying promoted posts in Ukrainian-language channels to focus on potential victims. A channel with over 80,000 subscribers selling the “Civil Defense” Telegram channel-website was noticed on September 18th. An extra Ukrainian-language information channel selling the posts as just lately as October eighth suggests the marketing campaign is actively in search of new Ukrainian-language communities for focused engagement.
Google has recognized and blocked malicious web sites and domains by including them to Secure Looking, actively scanning gadgets for dangerous apps, and collaborating with Ukrainian authorities to dam the marketing campaign’s web site throughout the nation. Google Play Defend additionally actively scans gadgets for dangerous apps, together with these put in exterior the Play Retailer.
However, Google’s report sheds mild on Russia’s multifaceted strategy to weakening Ukraine’s battle effort via cyber means. By staying knowledgeable and using safety measures offered by platforms like Google, customers may help mitigate the influence of such campaigns.
RELATED REPORTS
- Russia Liable for Widespread Energy Outage in Ukraine?
- Ukraine Blocks Russian Industroyer 2 Assault on Vitality Supplier
- Hackers Declare Information Breach at Russian Cybersecurity Agency Dr.Internet
- Russian APT29 Utilizing NSO Group-Fashion Exploits in Assaults, Google
- Russian Midnight Blizzard Breached UK Residence Workplace through Microsoft