A global legislation enforcement operation, led by america, Europol, and the Netherlands, has efficiently dismantled the infrastructure behind the infamous RedLine and META infostealer malware. Uncover how these cyberattacks steal delicate data and the influence they’ve on people and companies worldwide.
A global legislation enforcement operation has efficiently dismantled the infrastructure behind two infamous infostealer malware strains: RedLine and Meta. The operation, codenamed “Operation Magnus,” was led by the Dutch Nationwide Police, the U.S. Division of Justice (DOJ) and supported by Europol.
The investigation concerned legislation enforcement businesses from throughout the globe, together with Belgium (Belgian Federal Police, Belgian Federal Prosecutor’s Workplace), Australia (the Australian Federal Police), Portugal (Polícia Judiciária), and the UK (Nationwide Crime Company).
Different US businesses concerned on this operation embody the FBI, Naval Felony Investigative Service, IRS Felony Investigation, Protection Felony Investigative Service, and Military Felony Investigation Division. These businesses collaborated below a Joint Cybercrime Motion Taskforce (“JCAT”) Operation Magnus.
This operation resulted in full entry (PDF) to the servers internet hosting the malware’s infrastructure, together with supply code, license servers, consumer information, and seizing domains and Telegram accounts. Authorities have created a devoted web site to supply assets for victims and the general public
In your data, Infostealers are a sort of malware designed to steal delicate data from victims’ units, corresponding to login credentials, passwords, and bank card particulars. These stolen credentials are sometimes offered on underground markets, enabling additional cyberattacks and fraudulent actions.
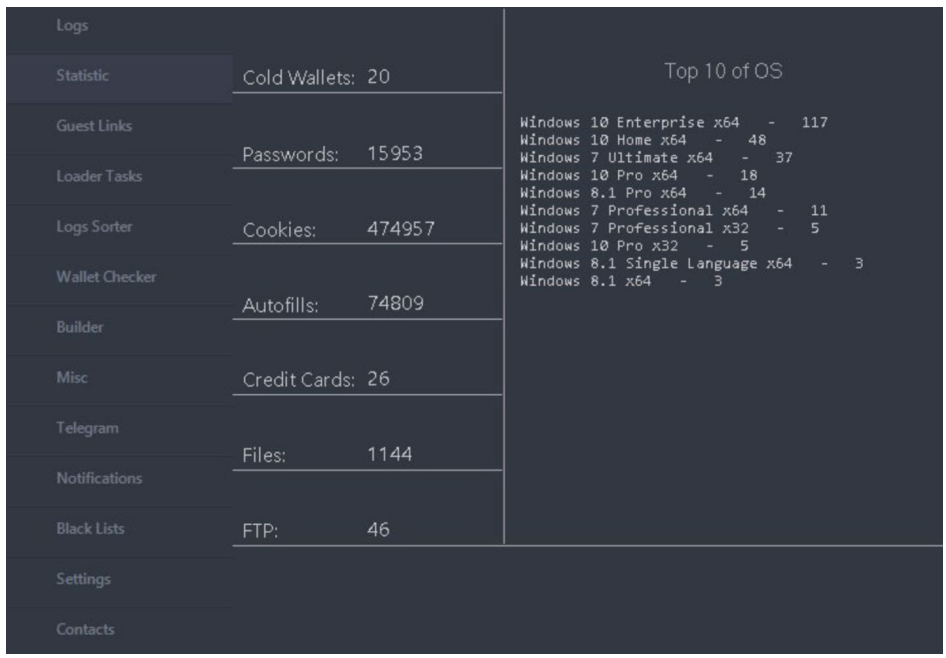
RedLine and META are designed to infiltrate sufferer computer systems and steal delicate data. This stolen information, sometimes called “logs,” can embody usernames, passwords, monetary data, and even cryptocurrency pockets particulars. Criminals use these stolen credentials for a wide range of nefarious functions, together with launching additional assaults, committing fraud, or bypassing multi-factor authentication (MFA).
Investigations revealed RedLine and META could have contaminated tens of millions of computer systems worldwide. Estimates counsel RedLine alone may be one of the vital prevalent malware variants globally. Regulation enforcement has recognized tens of millions of distinctive credentials stolen by the malware, together with usernames, passwords, and monetary information.
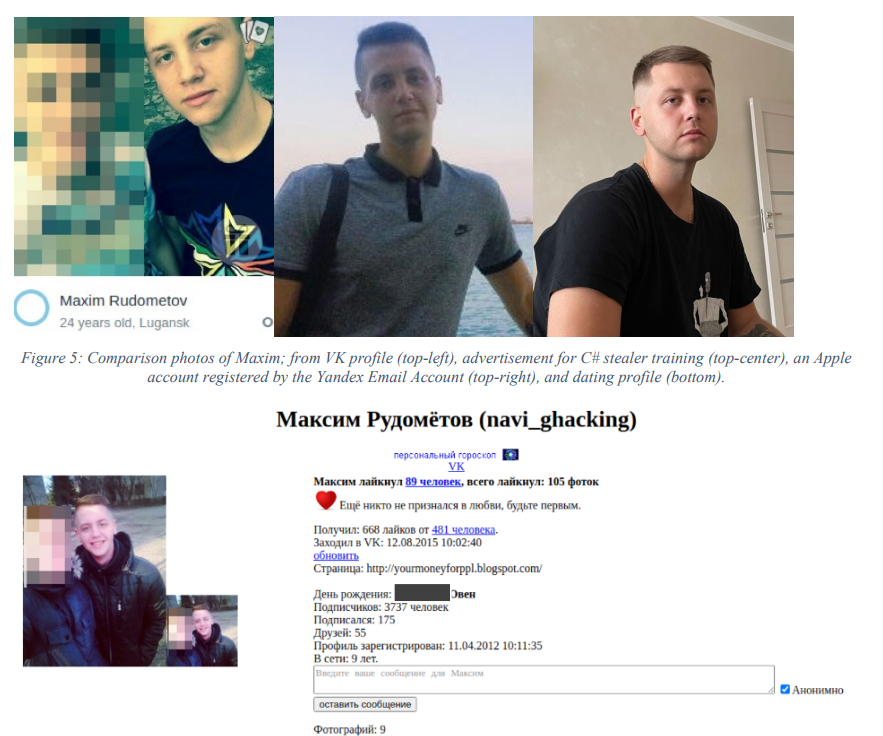
As a part of Operation Magnus, authorities unsealed a legal grievance (PDF) in opposition to Maxim Rudometov, believed to be a developer and administrator of RedLine. The grievance accuses Rudometov of managing RedLine’s infrastructure, receiving funds by way of cryptocurrency accounts, and possessing the malware itself. He faces prices together with entry gadget fraud, conspiracy to commit pc intrusion, and cash laundering, and if convicted, he might face a most sentence of 10 years in jail.
Operation Magnus serves as a robust instance of worldwide cooperation in combating cybercrime. By dismantling the RedLine and META infrastructure, legislation enforcement has considerably disrupted the actions of cybercriminals who depend on stolen information for his or her illicit operations. Nevertheless, the ever-evolving nature of cybercrime necessitates continued vigilance and cooperation between legislation enforcement and cybersecurity specialists.
RELATED TOPICS
- VirusTotal Reveals Apps Most Exploited To Unfold Malware
- Konni RAT Exploiting Phrase Docs to Steal Knowledge from Home windows
- FBI Dismantles Chinese language-Linked Botnet of 260,000 IoT Gadgets
- Police Dismantle Phishing-as-a-Service Platform BulletProftLink
- Arid Viper’s AridSpy Trojan Hits Android Customers in Palestine, Egypt