This text particulars a brand new marketing campaign by TeamTNT, a infamous hacking group, leveraging uncovered Docker daemons to deploy malware, utilizing compromised servers and Docker Hub to unfold their assaults. Additionally they use cryptomining to earn cash from their victims’ computational energy.
Cybersecurity researchers at Aqua Nautilus have found a brand new hacking marketing campaign by Adept Libra (aka TeamTNT), concentrating on uncovered Docker daemons to deploy Sliver malware, a cyber worm, and cryptominers.
TeamTNT is a infamous hacking group recognized for aggressive and protracted assaults on cloud-native environments. The group is thought for exploiting vulnerabilities in Docker daemons and Kubernetes clusters to deploy malware and hijack sources for cryptocurrency mining.
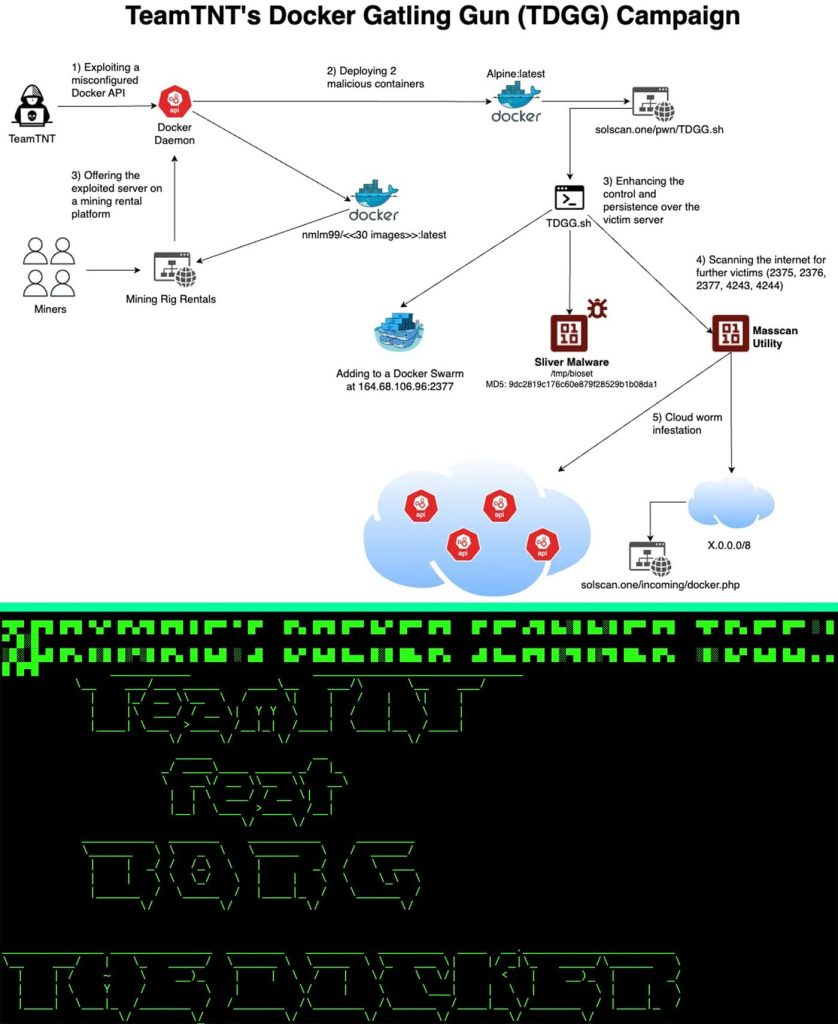
In a latest marketing campaign, TeamTNT compromised a reliable Docker Hub account (nmlm99) to host malicious software program, importing round 30 photographs divided into two classes: infrastructure and impression. The infrastructure photographs are used to unfold malware, whereas the impression photographs give attention to mining cryptocurrency or renting out computing energy.
TeamTNT is utilizing Docker Gatling Gun, which scans an enormous vary of IP addresses (round 16.7 million) for vulnerabilities in Docker daemons operating on particular ports (2375, 2376, 4243, and 4244). If a vulnerability is discovered, a container from a compromised TeamTNT Docker Hub account is deployed, operating a minimal Alpine Linux working system and executing a malicious script known as “TDGGinit.sh”. This script possible units the stage for additional malicious exercise on the compromised system.
“TeamTNT deploys among other a local search of keys and credentials, such as SSH, cloud metadata server calls etc. Once they gain access, they store and disseminate their malware through these accounts,” the report learn.
To evade detection, TeamTNT employs the Sliver malware, a extra superior and stealthier instrument in comparison with their earlier instrument, Tsunami. Additionally they use acquainted names like Chimaera and Bioset to mix in with reliable processes. Moreover, they steal credentials and scan networks for additional targets.
For command and management, TeamTNT depends on internet servers, Docker Hub, and varied communication protocols like DNS, mTLS, and probably proxies. Finally, their objective is to hijack sources for cryptocurrency mining or promote entry to the compromised methods.
To mine cryptocurrency, akin to Monero, TeamTNT makes use of varied mining software program, together with XMRig, T-Rex, CGMiner, BFGMiner, and SGMiner. They usually optimize mining operations by concentrating on particular {hardware} and software program configurations.
This marketing campaign reveals TeamTNT’s skill to adapt and evolve, urging organizations to be alert and improve their cybersecurity. The group is extremely expert and motivated and isn’t afraid to take dangers. To guard in opposition to TeamTNT dangers, organizations should put money into robust safety practices, together with software program updates and community infrastructure safety.
RELATED TOPICS
- Google Kubernetes Engine Flaws May Enable Cluster Takeover
- OracleIV DDoS Botnet Malware Hits Docker Engine API Situations
- Malware Exploits 9Hits, Turns Docker Servers into Crypto Miners
- Linux Malware Alert: Spinning YARN Hits Docker, Different Key Apps
- Cryptomining, Malware Flourish on Uncovered Kubernetes Clusters