A brand new Fortinet FortiManager flaw dubbed “FortiJump” and tracked as CVE-2024-47575 has been exploited since June 2024 in zero-day assaults on over 50 servers, in keeping with a brand new report by Mandiant.
For the previous ten days, rumors of an actively exploited FortiManager zero-day have been circulating on-line after Fortinet privately notified clients in a sophisticated notification safety advisory.
Immediately, Fortinet lastly disclosed FortiManager vulnerability, stating it was a lacking authentication flaw within the Fortinet created the “FortiGate to FortiManager Protocol” (FGFM) API that allowed unauthenticated attackers to execute instructions on the server and managed FortiGate gadgets.
Risk actors may exploit the flaw by using attacker-controlled FortiManager and FortiGate gadgets with legitimate certificates to register themselves to any uncovered FortiManager server.
As soon as their system was related, even when it was in an unauthorized state, they may exploit the flaw to execute API instructions on the FortiManager and steal configuration knowledge about managed gadgets.
Fortinet has launched patches for the CVE-2024-47575 and provided mitigations, equivalent to solely permitting particular IP addresses to attach or stopping unknown FortiGate gadgets from registering utilizing the set fgfm-deny-unknown allow command.
Exploited as a zero-day since June
Tonight, Mandiant experiences {that a} risk actor tracked as UNC5820 has been exploiting FortiManager gadgets since as early as June 27, 2024.
“UNC5820 staged and exfiltrated the configuration data of the FortiGate devices managed by the exploited FortiManager,” reads the new report from Mandiant.
“This data contains detailed configuration information of the managed appliances as well as the users and their FortiOS256-hashed passwords.”
“This data could be used by UNC5820 to further compromise the FortiManager, move laterally to the managed Fortinet devices, and ultimately target the enterprise environment.”
The primary noticed assault was seen coming from 45.32.41[.]202, when the risk actors registered an unauthorized FortiManager-VM to an uncovered FortiManager server.
This system was listed with the title “localhost” and utilized a serial variety of “FMG-VMTM23017412,” as proven beneath.
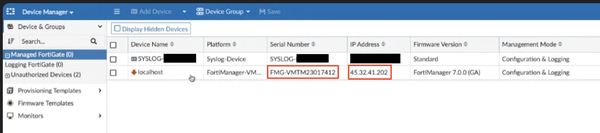
Supply: Mandiant
As a part of the assault, Mandiant says 4 recordsdata had been created:
- /tmp/.tm – A gzip archive containing exfiltrated details about managed FortiGate gadgets, details about the FortiManager server, and its international database.
- /fds/knowledge/unreg_devices.txt – Incorporates the unregistered system’s serial quantity and IP tackle.
- /fds/knowledge/subs.dat.tmp – Unknown
- /fds/knowledge/subs.dat – This file contained the attacker-controlled system’s serial quantity, consumer ID, firm title, and an e-mail tackle.
Within the first noticed assault, the e-mail tackle was “0qsc137p@justdefinition.com,” and the corporate title was “Purity Supreme.”
Mandiant says they analyzed the reminiscence for a compromised system however discovered no indicators of malicious payloads or tampering with system recordsdata.
Whereas the attackers did exfiltrate knowledge from gadgets, Mandiant says there have been no indicators that UNC5820 utilized this delicate info to unfold laterally to the managed FortiGate gadgets or breach networks.
At this level, the stolen knowledge is probably not as worthwhile to the attackers, as Mandiant and Fortinet notified clients of the assaults. Hopefully, the purchasers modified their credentials and took different precautions.
As there was no follow-up exercise after the preliminary assaults, Mandiant has not been capable of decide the risk actor’s aim and the place they might be positioned.
“As a result, at the time of publishing, we lack sufficient data to assess actor motivation or location. As additional information becomes available through our investigations, Mandiant will update this blog’s attribution assessment,” defined Mandiant.
Fortinet shared extra info inn its CVE-2024-47575 (FG-IR-24-423) advisory, together with mitigation and restoration strategies. The advisory additionally contains extra IOCs, together with different IP addresses utilized by the attackers and log entries for detecting a compromised FortiManager server.
