Cyber attackers are utilizing encoded JavaScript recordsdata to cover malware, abusing Microsoft’s Script Encoder to disguise dangerous scripts in .jse recordsdata. ANY.RUN’s sandbox helps detect and decrypt these threats, enhancing safety evaluation effectivity.
Cyber attackers consistently innovate new methods to cover their malicious intentions. Just lately, cybersecurity researchers at ANY.RUN got here throughout a tactic utilized by attackers which includes the abuse of encoded JavaScript recordsdata. Attackers have been utilizing the Microsoft Script Encoder to disguise dangerous scripts inside .jse recordsdata.
This tactic permits malware to stay hidden inside seemingly official scripts, posing a serious menace to unsuspecting customers and conventional safety measures.
Microsoft Script Encoder Exploited
Microsoft initially developed the Script Encoder to assist builders obfuscate JavaScript and VBscript whereas holding them executable with wscript and related interpreters. This software was initially designed to guard supply code, however it has additionally turn into a helpful useful resource for malware builders.
By encoding JavaScript right into a non-human-readable format, attackers can conceal their malicious scripts. The latter may be delivered via phishing campaigns or drive-by-download assaults, the place customers unknowingly run the malicious script.
This obfuscation method makes it troublesome for conventional safety instruments to detect hidden threats. Nevertheless, they are often detected quicker with the assistance of instruments, like ANY.RUN’s Script Tracer.
How one can Decrypt Encoded Malicious Scripts
To view the log of the script execution, run the pattern inside ANY.RUN’s sandbox.
View evaluation session
After working the pattern, you possibly can uncover the behaviour of the script in an remoted atmosphere utilizing ANY.RUN’s Script Tracer:
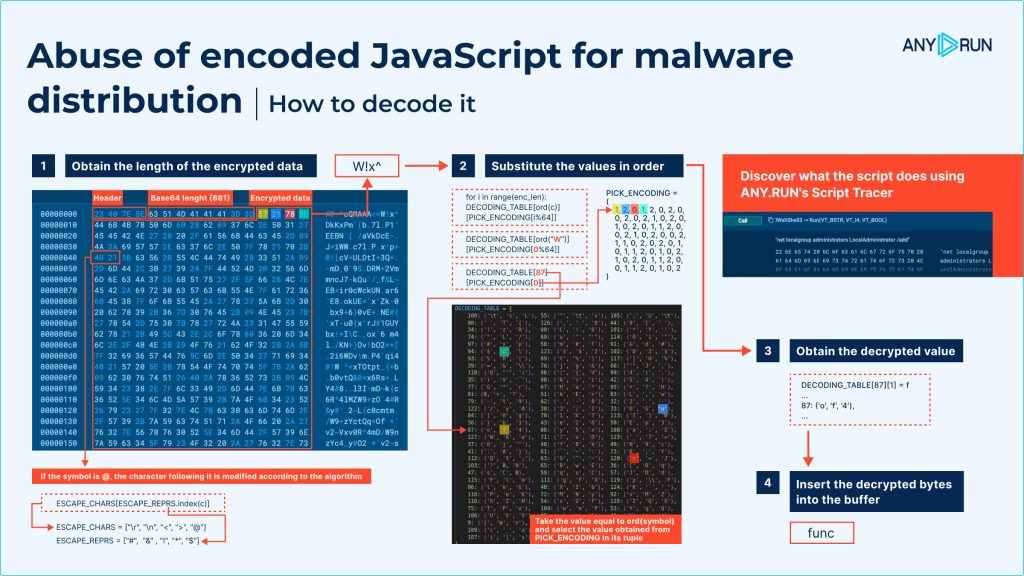
- Receive the size of the encrypted information
Start by figuring out the size of the encoded portion of the script. Whereas doing this, hold an eye fixed out for the @ image, which serves as a key marker within the script.
If you see @, it signifies that the subsequent character has been modified utilizing a particular algorithm.
- Substitute values so as
With the encoded characters recognized, start the substitution course of. This step includes changing every encoded image with its corresponding decoded worth. To decode every character within the script, observe the directions within the picture under:
- Receive the decrypted worth
As you decode every character, you’ll begin to uncover the readable type of the script. This step-by-step decoding reveals the underlying instructions hidden inside the encoded information.
- Insert the decrypted bytes into the buffer
After decoding every character, retailer the decoded end in a buffer (a brief house to carry the information). Proceed including decrypted characters till your complete script has been processed.
- Use the ord() operate for character values
Take the numeric worth of every image utilizing the ord() operate, then retrieve the corresponding decoded character from the predefined encoding tuple utilizing PICK_ENCODING.
Analyzing Malicious Scripts in a Protected Atmosphere
Manually decrypting encoded scripts may be advanced and time-consuming. To make the decryption course of simpler and quicker, you should utilize instruments like ANY.RUN’s sandbox.
It permits you to analyze malware behaviour in a safe atmosphere, supplying you with the insights you want for detailed evaluation.
Join a 14-day free trial for limitless malware evaluation and see the way it simplifies the method.
RELATED TOPICS
- Evaluation of High Infostealers: Redline, Vidar and Formbook
- PythonAnywhere Cloud Platform Abused for Internet hosting Ransomware
- OpenSSF Warns of Faux Maintainers Focusing on JavaScript Initiatives
- ANY.RUN Upgrades Menace Intelligence to Determine Rising Threats
- Visa warns of Baka JavaScript skimmer able to evading detection