Hundreds of thousands of iOS and Android customers are in danger after Symantec found that well-liked apps include hardcoded, unencrypted cloud keys. This safety flaw might result in unauthorized entry, knowledge breaches, and repair disruptions.
Analysis performed by cybersecurity consultants at Symantec has revealed that well-liked apps on each Android and iOS platforms include hardcoded, unencrypted cloud service credentials, placing tens of millions of customers’ delicate knowledge and backend companies prone to unauthorized entry and potential knowledge breaches.
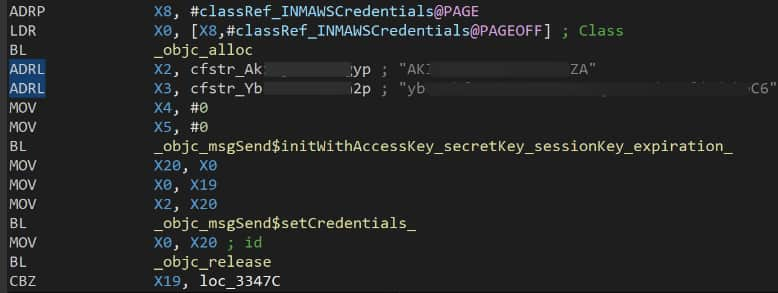
The difficulty comes from builders embedding entry and secret keys straight within the app’s code as a substitute of utilizing safe storage strategies. This makes it simple for attackers to entry delicate knowledge, steal person info, or disrupt companies.
Among the many affected Android apps, Pic Sew: Collage Maker, with over 5 million downloads, and Meru Cabs, Sulekha Enterprise, and ReSound Tinnitus Reduction, every with lots of of hundreds of downloads, had been discovered to include hardcoded AWS and Azure credentials, respectively. These credentials grant entry to important cloud storage and different backend companies.
On the iOS aspect, well-liked apps like Crumbl (over 3.9 million rankings), Eureka: Earn Cash for Surveys (402.1K rankings), and Videoshop – Video Editor (357.9K rankings) had been additionally discovered to have hardcoded AWS credentials, together with entry keys and even WebSocket Safe (WSS) endpoints, additional simplifying potential assaults.
Full listing of impacted apps on iOS and Android
- Crumbl (over 3.9 million rankings)
- Meru Cabs (over 5 million downloads)
- Sulekha Enterprise (over 500,000 downloads)
- Videoshop – Video Editor (over 357,000 rankings)
- ReSound Tinnitus Reduction (over 500,000 downloads)
- Pic Sew: Collage Maker (over 5 million downloads)
- Eureka: Earn Cash for Surveys (over 402,000 rankings)
This problem, discovered on each Android and iOS, is a critical concern. It might result in something from particular person knowledge breaches to main service disruptions. Symantec’s findings present the pressing want for builders to observe safety greatest practices.
To mitigate these dangers, builders are suggested to observe greatest practices for managing delicate info inside their functions. These embrace utilizing surroundings variables, implementing secrets and techniques administration, encrypting delicate knowledge, conducting common code opinions and audits, and automating safety scanning.
“This repeated pattern of insecure credential management across multiple apps underscores the critical need for developers to prioritize security in the mobile app development lifecycle,” mentioned a Symantec spokesperson.
For customers, Symantec advises putting in respected safety software program, downloading apps solely from trusted sources, holding software program up to date, fastidiously reviewing app permissions, and frequently backing up essential knowledge. These precautions can assist mitigate the dangers related to insecure apps whereas builders work to deal with these important vulnerabilities.
RELATED TOPICS
- Google reveals spy ware assault on Android, iOS, and Chrome
- Research: Android sends extra knowledge to Google than iOS to Apple
- Bluetooth Falw Permits Keystroke Injection on Android and iOS
- WiFi Flaws Permit Community Visitors Interception on iOS and Android
- Instagram iOS, Android app flaw allowed account entry to hackers