A number of end-to-end encrypted (E2EE) cloud storage platforms are weak to a set of safety points that would expose consumer information to malicious actors.
Cryptographic evaluation from ETH Zurich researchers Jonas Hofmann and Kien Tuong Turong revealed concern with Sync, pCloud, Icedrive, Seafile, and Tresorit companies, collectively utilized by greater than 22 million folks.
The evaluation was based mostly on the menace mannequin of an attacker controlling a malicious server that may learn, modify, and inject information at will, which is practical for nation-state actors and complex hackers.
The group feedback that lots of the found flaws immediately oppose the advertising and marketing guarantees of the platforms, which create a misleading and false premise for purchasers.
Findings
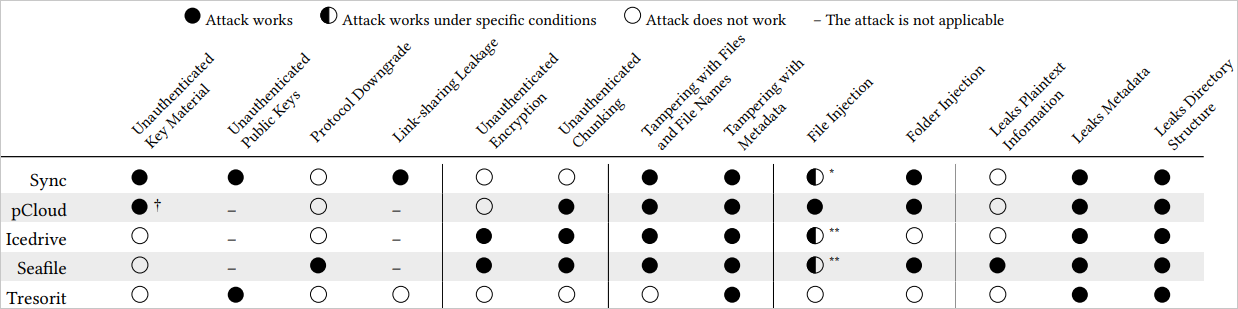
The ETH Zurich researchers discovered severe vulnerabilities in all 5 merchandise, together with implementations that permit a malicious actor to inject information, tamper with information, or acquire entry to consumer information. This is an outline of the found points:
- Sync‘s vulnerabilities embrace unauthenticated key materials, permitting attackers to inject their very own encryption keys and compromise information. The shortage of public key authentication in file sharing additional permits attackers to decrypt shared information. Shared hyperlinks expose passwords to the server, breaking confidentiality. Moreover, attackers can rename or transfer information undetected and even inject folders into consumer storage, making them seem as if the consumer uploaded them.
- pCloud‘s foremost points stem from unauthenticated key materials, permitting attackers to overwrite personal keys and drive encryption with attacker-controlled keys. Public keys are additionally unauthenticated, giving attackers entry to encrypted information. Moreover, attackers can inject information, manipulate metadata like file measurement, and reorder or take away chunks as a result of lack of authentication within the chunking course of.
- Icedrive‘s use of unauthenticated CBC encryption makes it weak to file tampering, permitting attackers to switch file contents. File names may also be truncated or altered. The chunking course of lacks authentication, that means attackers can reorder or take away file chunks, compromising file integrity.
- Seafile is weak to protocol downgrades, making password brute-forcing simpler. Its use of unauthenticated CBC encryption permits file tampering, and unauthenticated chunking lets attackers manipulate file chunks. File names and areas are additionally unsecured, and the server can inject information or folders into consumer storage.
- Tresorit‘s public key authentication depends on server-controlled certificates, which attackers can change to entry shared information. Metadata can also be weak to tampering, permitting attackers to change file creation particulars and mislead customers.
Out of the examined group of 5, Tresorit fared comparatively higher, as the problems found don’t immediately expose file contents or permit for straightforward information manipulation.
Supply: ETH Zurich
Disclosure and vendor responses
The researchers notified Sync, pCloud, Seafile, and Icedrive of their findings on April 23, 2024, and contacted Tresorit on September 27, 2024, to debate potential enhancements of their explicit cryptographic designs.
Icedrive determined to not handle the problems, Seafile promised to patch the protocol downgrade downside on a future improve, whereas Sync and pCloud had not responded as of October 10, 2024.
BleepingComputer contacted all 5 cloud service suppliers for a touch upon Hofmann’s and Truong’s analysis, and we acquired the beneath statements.
Sync: Our safety group grew to become conscious of those points final week, and we have since taken swift motion to deal with them. We have additionally reached out to the analysis group to share findings and collaborate on subsequent steps.
The potential information leak concern on hyperlinks (as reported) has already been fastened, and we’re fast-tracking fixes for the remaining potential points proper now. Because the analysis paper outlines, these vulnerabilities exist underneath the pretext of a compromised server. There is no such thing as a proof that these vulnerabilities have been exploited or that file information has been accessed.
We perceive that through the use of Sync, belief is positioned in us. However the promise of end-to-end encryption is that you just needn’t belief anybody, not even us. This idea is on the core of our encryption mannequin and central to what we do.
We’re dedicated to getting these points resolved.
Tresorit: The examine of ETH Zürich’s world-class analysis group examined the potential for ten courses of assaults on end-to-end-encrypted cloud storage programs, together with confidentiality breaches and file injection vulnerabilities. The findings confirmed that Tresorit’s considerate design and cryptographic decisions made our system largely unaffected by these assaults. Whereas we’re happy with these outcomes, we additionally acknowledge the untapped potential the analysis highlighted.
Presenting public key fingerprints to customers when sharing folders is on our 2025 roadmap. This can fully stop key alternative assaults by permitting out-of-band verification. We already do that for enterprise invites so the consumer can get cryptographic proof about their future information administrator earlier than becoming a member of. Our Widespread Standards EAL4 + AVA_VAN.5 evaluated shopper software program — a primary amongst cloud storage companies — requires out-of-band key authentication for folder sharing, too.
Although some metadata, such because the file measurement, the time of final modification, and folder memberships are shared with the servers, these are additionally saved as cryptographically authenticated information to stop tampering. This metadata can also be wanted to be recognized on the server aspect: for the correct bookkeeping of our clients’ storage quota, and to implement server-side entry guidelines as a further layer of safety.
At Tresorit, safety is our high precedence, and we’re dedicated to steady enchancment, utilizing these insights to strengthen our platform additional. This analysis not solely helps us evolve but additionally guides the broader business towards safer options. Safety is the muse of every little thing we construct, and we’re proud to collaborate with educational establishments just like the Technical College in Budapest to make sure that we keep on the forefront of innovation in safe cloud storage.
Seafile: We do not have something to remark in the intervening time.
Icedrive and pCloud didn’t reply to BleepingComputer’s request for a press release.
