Tailgating, generally known as piggybacking, is a sort of bodily safety breach by which an unauthorized particular person follows a certified particular person to enter secured premises whereas avoiding detection by an digital or human entry management (or alarm) system.
Usually, when tailgating assaults succeed, it is as a result of a mix of two elements: 1) human carelessness on the a part of the adopted social gathering, and a pair of) ingenuity and confidence on the a part of the next social gathering. Tailgating is a major safety danger for organizations and their property, gear, knowledge and personnel.
Understanding tailgating
Tailgating is likely one of the easiest types of a social engineering assault, by which menace actors reap the benefits of human habits or weaknesses to perpetrate a malicious incident, corresponding to a rip-off, theft or a cyberattack.
By merely following a certified particular person (AP); an unauthorized social gathering (UP) can simply get round safety mechanisms, corresponding to retina scanners, fingerprint scanners, and even human safety guards, and achieve entry to restricted bodily areas.
Typically, unauthorized individuals are in a position to take action by taking reap the benefits of cognitive biases that have an effect on human decision-making. One such “human bug” is the tendency to be courteous; one other is the tendency to belief different folks; a 3rd is easy behavior. Because of these human quirks, many APs have a tendency to carry the door for UPs, who then would possibly exploit such well mannered gestures to entry areas they won’t have been capable of entry in any other case.
How tailgating occurs
Tailgating assaults can occur in some ways, together with the next:
- The best methodology is somebody following another person by a door.
- Tailgating also can happen when a certified particular person enters an space with out closing the door behind them. This may depart a small window of time accessible for an unauthorized particular person to enter the premises.
- One other methodology is when an AP retains a door propped open for some purpose. As an illustration, a painter would possibly depart it open to do away with paint fumes, or an IT vendor is likely to be troubleshooting a server or router within the server room whereas leaving the room’s door open.
- A extra refined sort of assault happens when menace actors disguise themselves, both as approved personnel with entry to a selected space (e.g., a supervisor) or seemingly innocent individuals (e.g., a supply particular person) to trick folks into granting them entry to that space.
The place does tailgating occur?
Tailgating is a typical drawback in multitenant buildings with excessive visitors (many individuals accessing the constructing and its premises). Excessive visitors makes it tough to determine and observe unauthorized personnel, and to maintain them out.
Tailgating additionally occurs extra typically in corporations the place workers lack good cybersecurity hygiene or do not observe cybersecurity greatest practices. This is likely to be because of the following:
- Carelessness.
- Lack of information about cyber dangers.
- Insufficient cybersecurity coaching, notably coaching about how people are sometimes the “weak link” in cybersecurity.
Tailgating also can occur in corporations missing biometric entry management programs. With out such digital programs in place, virtually anyone can enter safe areas by merely strolling in. It is also tough to determine blind spots in a facility or plan methods to deal with them.
Risks of tailgating
Tailgating is taken into account a “low-tech” assault tactic as a result of it hardly ever includes refined gear. Nonetheless, it’s a severe bodily and cybersecurity concern for enterprises as a result of it will increase the chance of a malicious particular person compromising or harming the agency in a roundabout way. For instance, an intruder would possibly do the next:
- Exfiltrate delicate data to trigger a knowledge breach.
- Steal beneficial gear corresponding to unattended laptops.
- Insert adware into enterprise units.
- Set up malware or ransomware on computer systems.
- Flip off important programs corresponding to servers.
- Entry the server room and create a backdoor to your complete enterprise community.
- Set up cameras to remotely keep watch over firm operations and have interaction in company or cyberespionage.
- Steal cash or enterprise secrets and techniques like blueprints, mental property (IP), shopper lists or monetary data.
- Destroy or injury the agency’s bodily property (vandalism).
Tailgaters can embody disgruntled former workers, thieves, vandals or mischief makers. Mainly, anybody who has a difficulty with the corporate or hopes to revenue off it may be a tailgater. Whether or not tailgating individuals are harmless or malicious, they will probably disrupt the enterprise, trigger injury or create sudden prices. They could additionally create additional questions of safety for firm personnel as a result of fires or stampedes. Tailgating can also result in bodily violence.
Methods to keep away from tailgating
Organizations can defend their premises from unauthorized personnel and stop tailgating by implementing sure efficient safety measures. These embody the next:
Digital entry doorways
Putting in entry controls for entrances and restricted areas with swiftly closing doorways is important to stop tailgating. Moreover, revolving doorways present tailgating detection and be sure that a person is alone, stopping others from coming into behind them with out going by a correct entry mechanism.
Laser sensors or mantraps
Photosensors, laser sensors and mantraps can restrict entry to a single particular person at a time, stopping somebody from following a certified particular person and coming into an space they aren’t approved to enter.
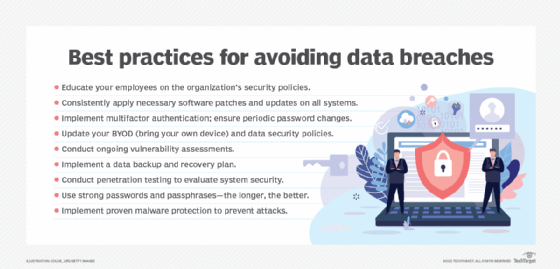
Biometric scanners
Biometric scanners and turnstiles enable just one particular person to enter an space at a time, stopping tailgaters from strolling with or behind a certified particular person. Additionally, biometric programs retailer particular people’ knowledge (e.g., fingerprints, palm prints, retinal scans, and so forth.) to facilitate entry to particular areas, so people whose data is not saved within the safety system are routinely stored out of these areas.
Good playing cards
Good playing cards are normally personalized to be used by a single particular person, which helps to manage entry to a room, workplace or constructing. When carried out with digital entry management mechanisms, good playing cards can forestall tailgating in entrances and restricted areas.
Photograph ID
Staff have to be required to put on picture IDs and guests have to be supplied momentary badges and required to put on them so long as they’re throughout the group’s premises. All IDs have to be clearly seen. With these ID strategies in place, anybody not sporting one turns into conspicuous, making it simpler to acknowledge and detain them, and stop them from coming into safe premises.
Video surveillance
Surveillance units corresponding to CCTVs present a way to keep watch over the premises 24/7. If the units are clearly seen, they act as a deterrent to these trying to tailgate their approach into an workplace or server room. Now, AI-enabled video surveillance programs can be found to supply uninterrupted views of safe areas plus real-time insights that allow safety workers to determine unauthorized or malicious events and take quick remedial motion.
Multifactor authentication (MFA)
MFA on entry doorways requires customers to supply multiple credential to entry an space. On this approach, even when an unauthorized particular person manages to compromise one credential, they are going to nonetheless not be capable to achieve entry. One instance of MFA is requiring people to supply each an entry card and a thumb print. One other is requiring entrants to enter numbers on a keypad and supply a retina print. MFA is especially helpful to maintain unauthorized individuals from accessing safe areas like server rooms or file rooms.
Examine use instances for MFA.
Human safety guards
Safety guards present a bodily means to safeguard premises. These guards must be skilled to ask unfamiliar personnel or personnel not sporting ID playing cards who they’re and why they’re on the premises. Additionally they must be approved to detain these individuals in a holding room till administration can decide what additional motion (e.g., a police report) is required towards them.
The significance of worker schooling in stopping tailgating
The above safety measures are all essential to curtail tailgating. Nonetheless, their presence can create a false sense of safety amongst workers, resulting in carelessness or ignorance of workers’ position in stopping tailgating. That is why it is important to coach them on the next:
- The risks of tailgating.
- Methods to acknowledge tailgating makes an attempt.
- What they will do to withstand tailgating and to maintain tailgaters out.
It is also vital to create a sturdy cyber consciousness tradition all through the group and to make workers conscious of their tasks to guard the corporate’s property from unauthorized events. Staff also needs to be taught to observe these safety greatest practices:
- By no means maintain the door for anybody.
- At all times maintain doorways closed, particularly these to safe or restricted areas like server rooms.
- Cease folks from following them into particular entry zones or restricted areas, particularly if they aren’t sporting worker or customer badges.
- Be certain that any outsiders, corresponding to repairmen or supply individuals, are reliable and sporting applicable customer badges.
- Direct unfamiliar folks, folks with out badges or individuals who seem “lost” to the reception desk.
- By no means enable former workers to entry the corporate premises if they do not have the permission of approved personnel (e.g., IT workforce) or are usually not sporting correct ID badges.
- Report suspicious exercise to safety guards.
- Inform safety guards or the IT workforce if an digital door shouldn’t be functioning correctly.
Tailgating vs. piggybacking
Tailgating shouldn’t be the identical as piggybacking, a sort of breach by which the unauthorized particular person methods or convinces the approved particular person into letting them right into a safe space. Thus, piggybacking normally includes an AP’s data, consent or permission. Additionally, the AP offering entry to the UP normally assumes that the UP has a reliable purpose for requesting entry.
That stated, each tailgating and piggybacking are types of in-person social engineering assaults by which menace actors attempt to achieve entry to an space that might be off-limits to them, normally for nefarious or malicious functions. Each will be very damaging for a company in a large number of how.
Organizations ought to know the important thing indicators of widespread safety incidents and the way to reply to maintain programs and knowledge secure. Learn in regards to the forms of safety incidents and how you can forestall them.
