Within the context of cloud safety posture administration (CSPM), customized controls are insurance policies or guidelines that give safety groups the flexibleness to create and implement insurance policies. These are wanted to handle posture, tailor compliance measures, and detect misconfigurations throughout infrastructures like Kubernetes, containers, and the cloud.
Introducing Sysdig Customized Management
Sysdig posture controls are constructed on the Open Coverage Agent (OPA) engine, utilizing the OPA coverage language Rego. The platform exposes the code used to create these controls and the inputs they consider.
These controls can be found in Sysdig’s Posture Controls library. They’ve primary attributes corresponding to severity and insurance policies predefined. Beforehand, you could possibly solely duplicate present controls and customise particular labels.
Sysdig’s new customized management characteristic is out there throughout main cloud service suppliers, together with AWS, Azure, GCP, and IBM. Enterprises can use this characteristic to:
- Outline and implement inner guideline controls which might be intently aligned with their structure and enterprise necessities
- Meet regulatory compliance requirements, corresponding to PCI and HIPAA
- Stop safety misconfigurations throughout Kubernetes, containers, and cloud environments
Preserve studying to discover ways to:
Create a customized management with Rego
Sysdig Safe’s Terraform supplier lets you outline, handle, and deploy customized controls as a part of your infrastructure automation. This ensures that your safety insurance policies are version-controlled, simply maintainable, and constant throughout environments.
Earlier than you get began
Guarantee you’ve got each Terraform and Go put in in your setting:
- Terraform model larger than 0.12.x
- Go model larger than the one laid out in go.mod (Arrange $GOPATH as per the directions right here)
- Terraform Supplier for Sysdig (use directions right here to put in and configure the supplier)
- Your Sysdig API tokens and Agent keys (change these values within the code snippet under)
terraform {
required_providers {
sysdig = {
supply = "local/sysdiglabs/sysdig"
model = "~> 1.0.0"
}
}
}
supplier "sysdig" {
sysdig_secure_url="https://secure.sysdig.com"
sysdig_secure_api_token = "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXXX"
extra_headers = {
"Proxy-Authorization": "Basic XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"
}
}Code language: Perl (perl)Terraform Useful resource for Customized Controls
Sysdig Safe’s Terraform Supplier makes use of the sysdig_secure_posture_control useful resource to outline customized controls. Useful resource attributes embody:
- title: The title of the customized management
- description: An in depth rationalization of what the management does
- resource_kind: The kind of useful resource the management applies to (e.g., AWS S3 buckets, Kubernetes pods)
- severity: The severity stage (e.g., Excessive, Medium, Low) that defines the management’s significance
- rego: The Rego coverage code that defines the management logic
- remediation_details: Directions for remediating any points recognized by the management
Subsequent, we’ll create a customized Sysdig Safe customized management utilizing Rego and Terraform.
S3 Bucket with out versioning
S3 bucket versioning is necessary for a number of causes, particularly knowledge safety, restoration, and administration. On this situation, we’ll create a customized management to make sure object versioning is enabled to your Amazon S3 buckets to protect and get better overwritten and deleted objects.
- Obtain and unzip the git file from the repository right here
- Contained in the
terraform-provider-sysdig-masterfolder, create a brand new Terraform file utilizing your favourite editor. Bonus factors in case you’re utilizing Visible Studio and have the VSCode extension put in - Copy the under code and paste it in your file. The Rego code is embedded inside the Terraform script
useful resource "sysdig_secure_posture_control" "s3_bucket_without_versioning" {
title = "S3 Bucket without versioning"
description = "Ensure that S3 object versioning is enabled for your Amazon S3 buckets to protect and recover overwritten and deleted S3 objects."
resource_kind = "AWS_S3_BUCKET"
severity = "High"
rego = <<-EOF
bundle sysdig
import future.key phrases.if
import future.key phrases.in
default dangerous := false
dangerous if {
rely(enter.Versioning) == 0
}
dangerous if {
some model in enter.Versioning
decrease(model.Standing) != "enabled"
}
EOF
remediation_details = <<-EOF
Code language: Perl (perl)Enabling versioning for S3 buckets helps protect and get better earlier variations of objects. It permits restoration of deleted or overwritten knowledge, and helps guarantee knowledge safety. Archiving earlier variations to Amazon S3 Glacier can also be doable for long-term, low-cost storage.
## Remediate Utilizing Command Line
Run the next command to allow versioning for the chosen bucket:
```
aws s3api put-bucket-versioning --bucket <bucket-name> --versioning-configuration Standing=Enabled
```
Repeat this command for different buckets in your AWS setting.
EOF
}Code language: Perl (perl)Subsequent, out of your terminal, initialize the Terraform setting. If the conditions are correctly configured, you’ll see a message just like the under snapshot
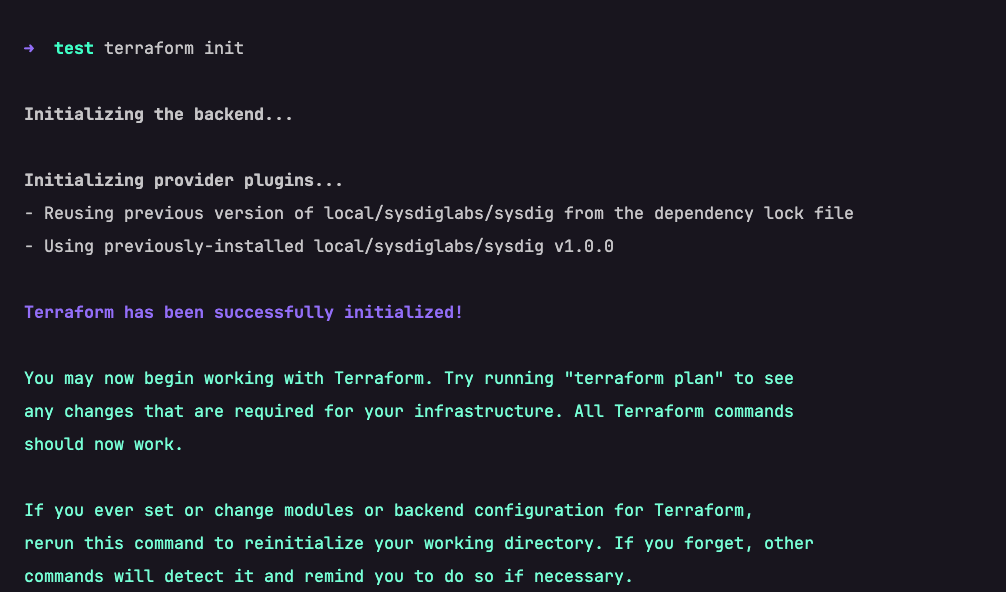
After the setting is initialized, the following activity is to deploy this Terraform script as a customized management in Sysdig Safe.
- Run
terraform applyout of your terminal
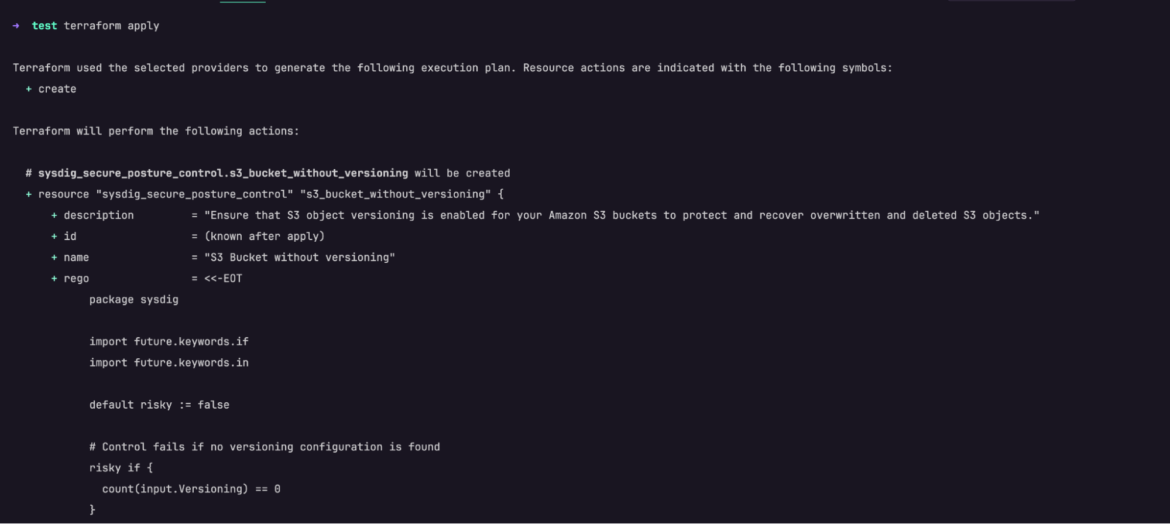
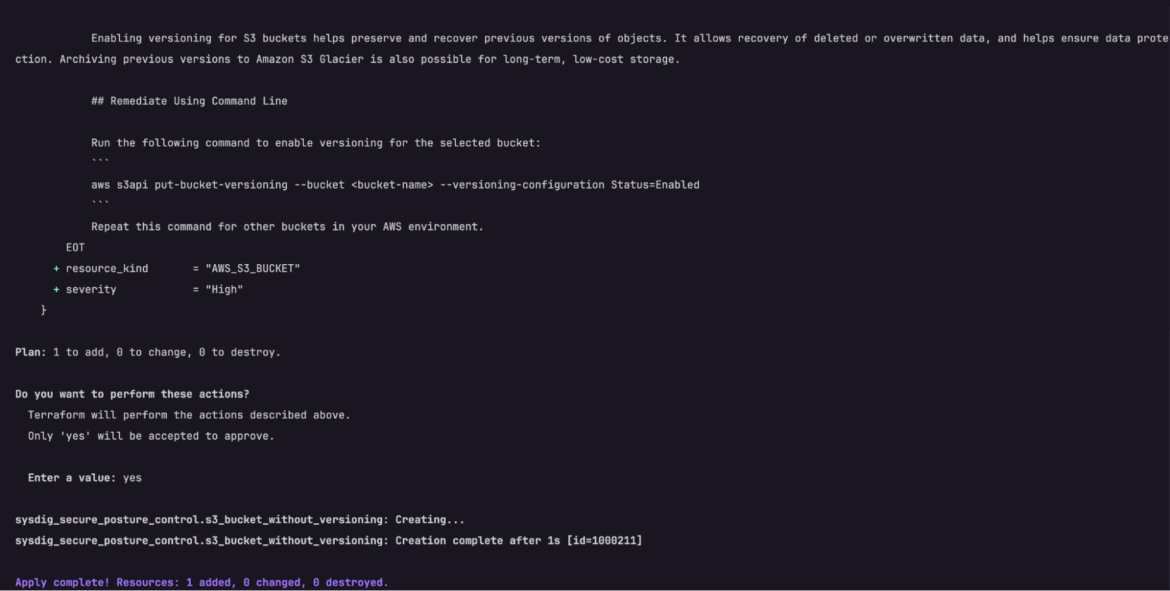
Terraform generates an execution plan describing what it should do to deploy the code, after which executes it to construct the described infrastructure or configuration.
- The immediate will pause for a consumer enter. At this stage, kind
sureand proceed
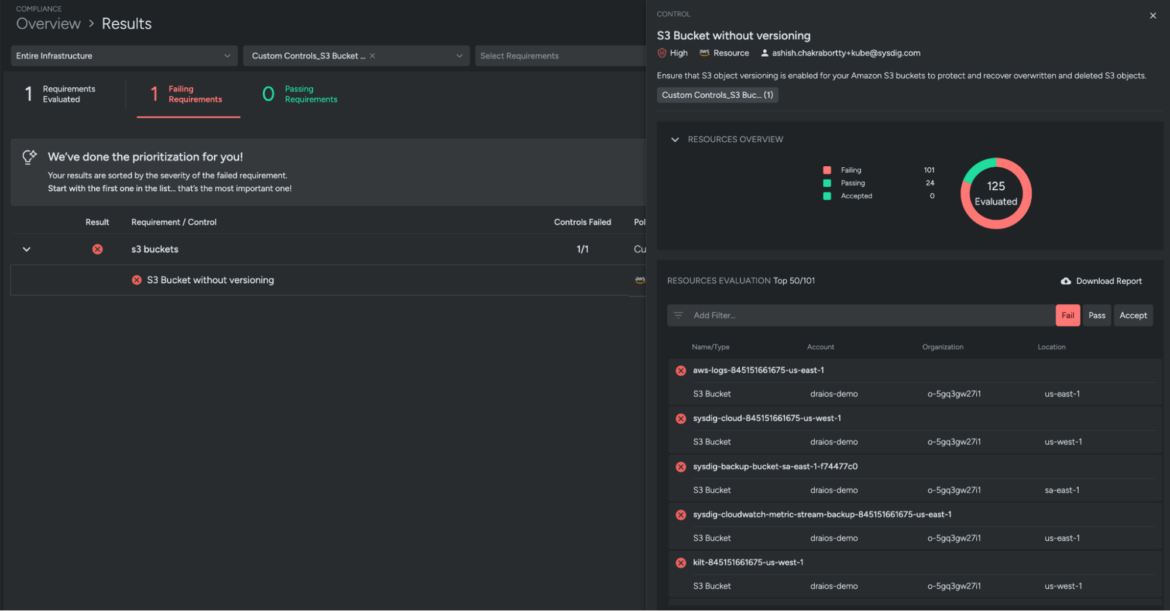
Our new customized management S3 Bucket with out versioning will seem within the Posture Controls library and is prepared for use in customized insurance policies. Confirm it by navigating to your Sysdig Safe consumer interface.
- Navigate to Posture → Controls
- Seek for S3 Bucket with out versioning
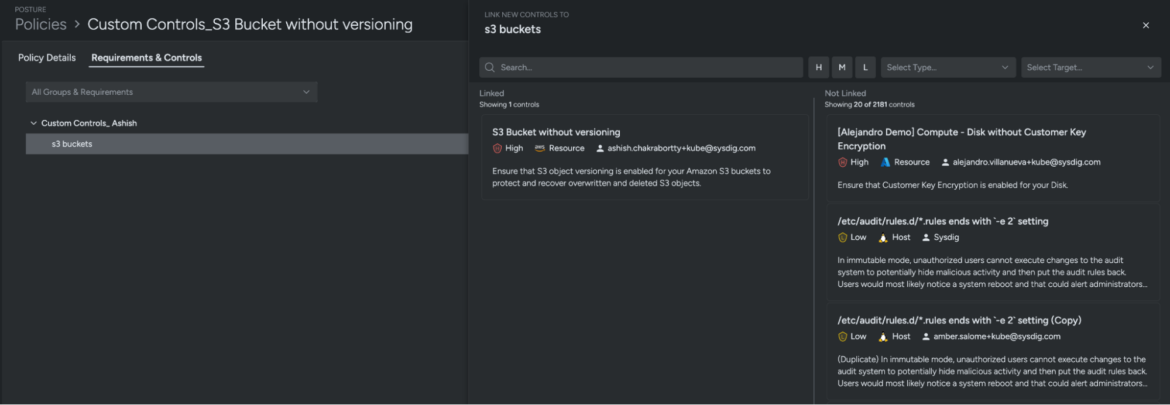
Apply your Customized Management
From right here, you possibly can assign the brand new customized management to a brand new or present Sysdig Safe Posture Coverage primarily based in your enterprise wants. The instance under was created by following these steps:
- Navigate to Posture → Insurance policies and create a brand new coverage Customized Controls_S3 Bucket with out versioning
- Select the infrastructure scope throughout which the brand new management should apply. This instance makes use of Complete Infrastructure
- Hyperlink your customized management as proven within the picture under to judge the posture compliance of your outlined infrastructure

To rollback, merely delete the useful resource definitions out of your Terraform file and reapply. It will replace the Posture Controls library and detach the outlined controls from the insurance policies.
Now that we’ve warmed up a bit, let’s have a look at a number of instruments you could possibly use to streamline your growth workflows.
Sysdig API Endpoint
The Sysdig API Endpoint permits your builders to question and fetch values for Terraform attributes like resource_kind. The REST APIs allow them to programmatically entry and handle Sysdig Monitor, Sysdig Safe, and Sysdig Platform.
On the Sysdig API endpoint, you’ll discover a number of class headers like Compliance, Cloud Organizations, CSPM, and extra, together with particulars just like the question parameters. For instance, to fetch Cloud Sources, you’ll want to question with the GET request and outline parameters like providerType, resourceKind, and filter. The API endpoint additionally builds your customized queries in a number of codecs, like Go, Curl, Node, Java, and Python.
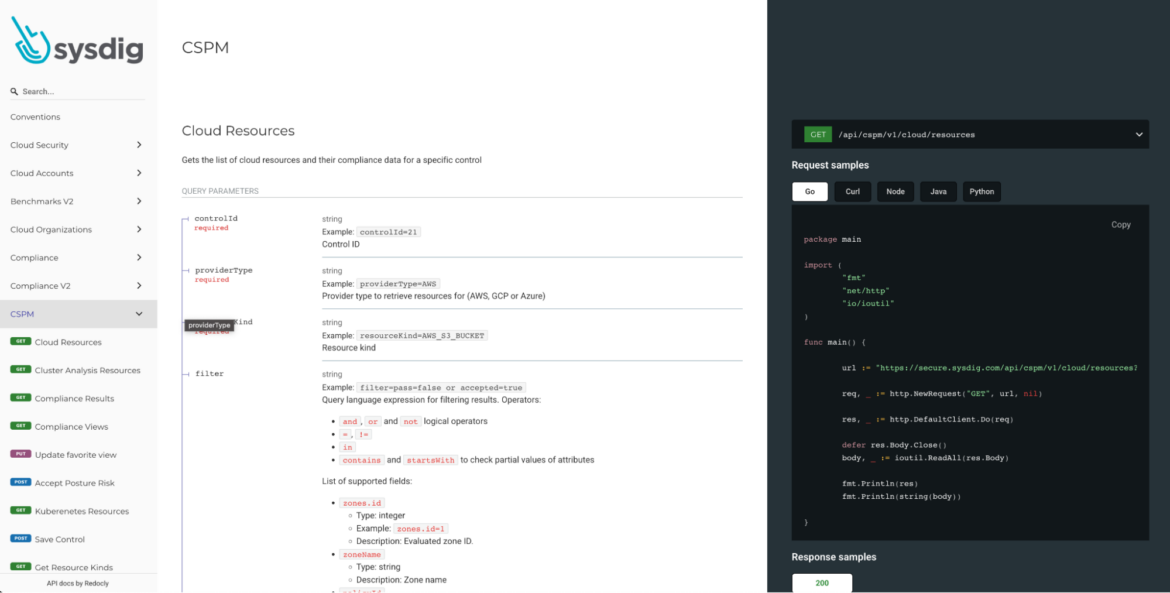
On this train, you’ll use Curl to question the API endpoint by utilizing a GET request, after which fetch values for the Terraform attribute resource_kind.
- Export the Sysdig API token in your setting (mine is MacOS). To export it in Home windows, learn these directions
- From the left panel, choose CSPM, scroll down, and click on Get Useful resource Varieties (you need to use this hyperlink right here)
- Subsequent, swap to the Curl tab and duplicate the GET request
- After that, open up a terminal window and paste the GET request. Present extra particulars like your Sysdig API token
curl --request GET
--url https://safe.sysdig.com/api/cspm/v1/coverage/controls/resource-template/varieties -H "Authorization: Bearer $SYSDIG_SECURE_API_TOKEN" | jq .resourceKindsCode language: Perl (perl)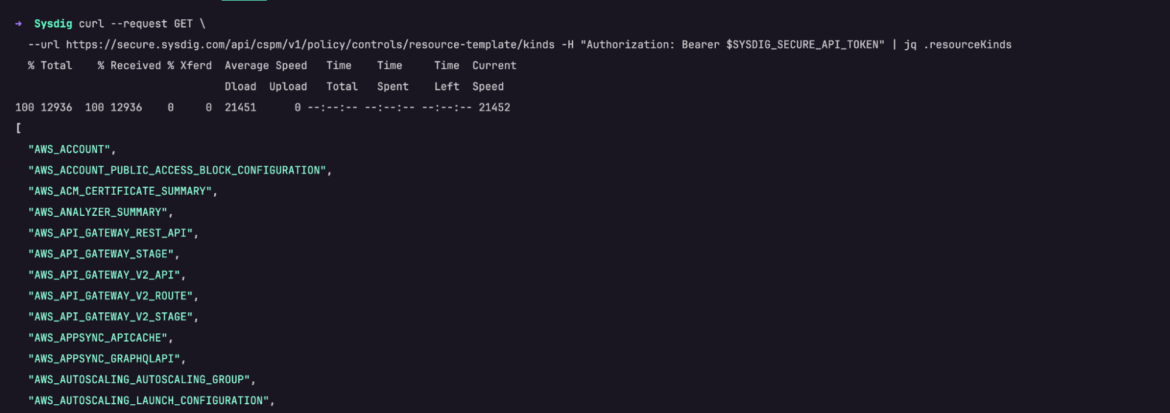
The JSON output offers an inventory of all official useful resource varieties obtainable to question inside the Sysdig Safe platform.
If we glance again at our Terraform script, we had outlined resource_kind as AWS_S3_Bucket.
- On the Sysdig API endpoint, click on Get Useful resource Instance
- Like final time, select Curl, copy the GET request, and paste it in your terminal
The brand new request ought to appear to be the one under. It fetches all of the values related to AWS_S3_Bucket.
curl --request GET
--url https://safe.sysdig.com/api/cspm/v1/coverage/controls/resource-template/view/AWS_S3_BUCKET -H "Authorization: Bearer $SYSDIG_SECURE_API_TOKEN" | jq -r .knowledge | jqCode language: Perl (perl)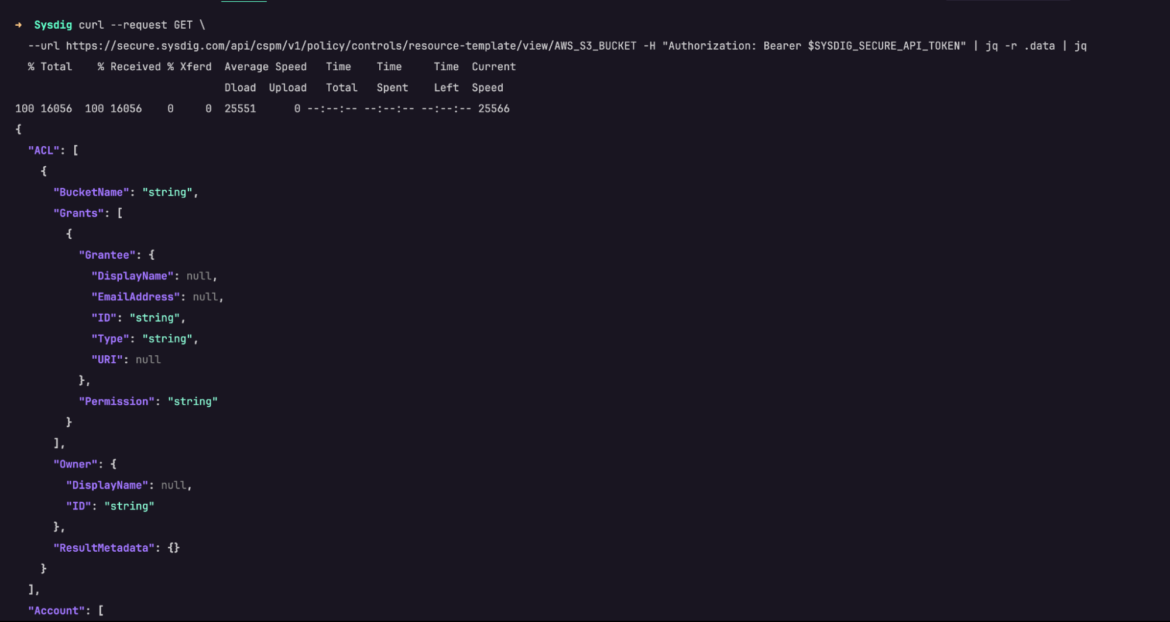
After this, copy and save the outcomes. We’ll want it for the final leg of our train the place we confirm our Rego code.
The Rego Playground
The Rego Playground is a web based interactive setting that lets you write, check, and debug Rego insurance policies in a sandboxed, browser-based interface. It’s very best for these trying to discover policy-based management throughout varied methods.
The browser-based interface offers options like real-time analysis of Rego expressions, enter/output simulation, and coverage testing, making it a superb device for studying, creating, and even sharing insurance policies with out the necessity to arrange a full Open Coverage Agent (OPA) setting domestically.
On this train, we’ll use the platform to judge the Rego code logic beforehand outlined in our Terraform script. The JSON output from the final train will likely be wanted as enter variables.
Copy the under code snippet and paste it within the editor part. If wanted click on Format to align the code
If you happen to observe fastidiously, the logic right here is to judge the article as dangerous primarily based on a subject worth.
bundle sysdig
import future.key phrases.if
import future.key phrases.in
default dangerous := false
dangerous if {
rely(enter.Versioning) == 0
}
dangerous if {
some model in enter.Versioning
decrease(model.Standing) != "enabled"
}Code language: Perl (perl)Add the beforehand saved JSON output within the INPUT window
The Versioning.Standing subject is outlined on the backside of the JSON output. Discover that it’s at present set to string.
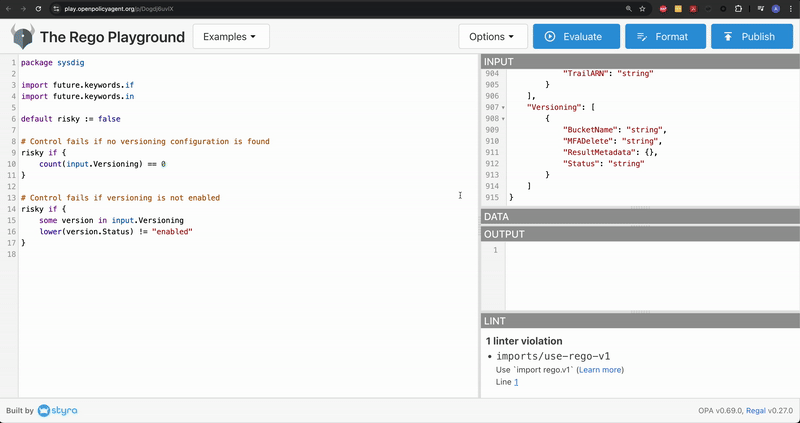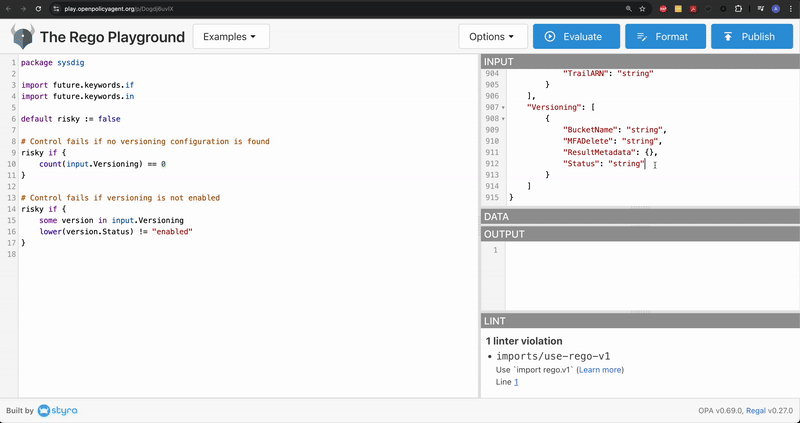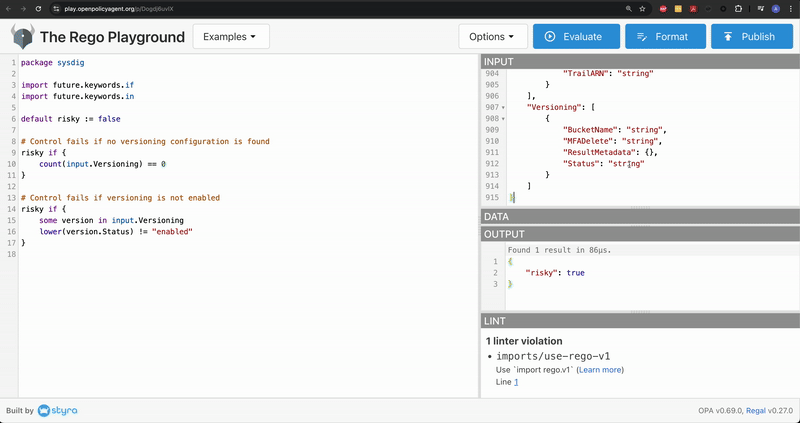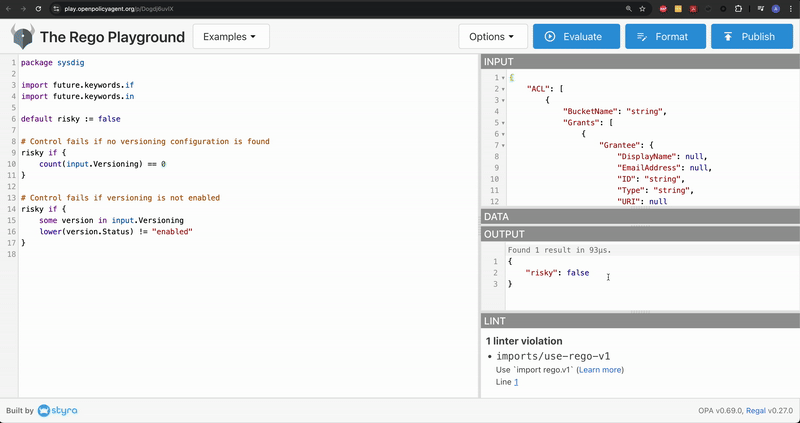
Now, click on Consider and check the Rego script
Within the OUTPUT window, we discover the worth of dangerous is about to true. We will infer that the AWS S3 Bucket will likely be tagged as a threat if the model standing isn’t enabled in your cloud accounts.

Subsequent, modify the Standing subject to enabled
Consider the script once more and spot that dangerous adjustments to false within the OUTPUT window. This proves that our Rego logic works correctly.

Use this hyperlink right here to run the above train.
Finest Practices for Implementing Customized Controls
- Begin with high-impact controls: Prioritize customized controls that handle important safety dangers, corresponding to blocking privileged containers or making certain S3 versioning.
- Use Terraform for automation: Terraform makes it simple to handle customized controls as code, making certain consistency throughout environments and permitting you to automate the deployment and updates of controls.
- Take a look at controls in a staging setting: At all times check your customized controls in a non-production setting to make sure that they work as anticipated and don’t produce false positives.
- Repeatedly evaluate and replace controls: As your infrastructure evolves, often evaluate and replace your customized controls to mirror new safety challenges and compliance necessities.
Conclusion
Customized controls in Sysdig Safe present the flexibleness to implement safety insurance policies which might be distinctive to your group’s wants. By leveraging Rego for coverage logic and Terraform for automation, you possibly can implement sturdy safety measures throughout cloud and Kubernetes environments. Whether or not it’s making certain S3 versioning or blocking privileged containers, these customized controls provide the energy to implement constant safety and compliance requirements.
For extra info and in-depth examples, check with: