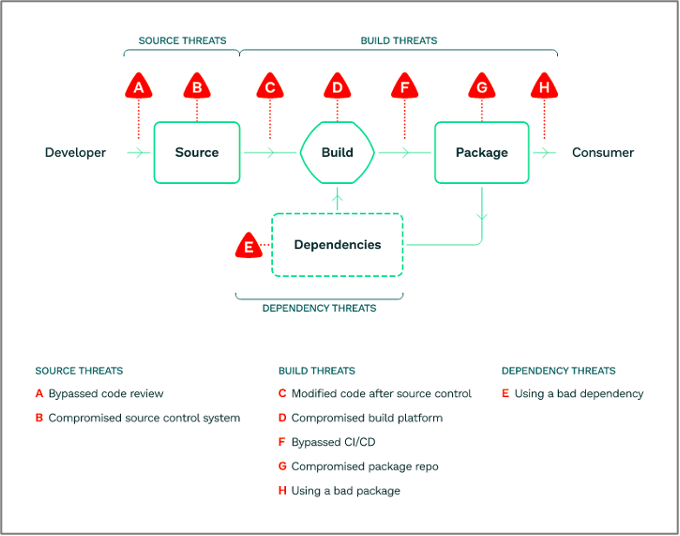
The usage of open-source software program has rapidly uncovered all components of the software program improvement course of as a part of the general assault floor, and has even result in the creation of new assault varieties.
Organizations should take steps at each stage of the software program provide chain to make sure builders’ environments. Enterprises should additionally make sure that processes and secured, so that you aren’t leaving your small business susceptible to next-generation SCS assaults, like AI package deal hallucinations, dependency confusion, typosquatting, and repojacking.
Let’s dive into a short historical past of how “supply chain security” has developed to the purpose we’re right this moment, what organizations should take into account when securing their software program provide chain, and the way Checkmarx is proactively constructing new options to handle this advanced and ongoing concern.
Our mission to safe your complete software program provide chain
For the previous 10 years, safety professionals have been skilled that earlier than you launch code, all excessive vulnerabilities must be recognized and stuck. However over the previous few years particularly, the world has modified. In accordance with GitHub, open supply is now the inspiration of greater than 90% of the world’s software program. Organizations at the moment are going through a shifting assault panorama, together with an awesome variety of vulnerabilities. The assault panorama is shifting from the applying itself, to the place there are new vulnerabilities and weaknesses – within the course of surrounding your improvement, and the parts you employ to construct your utility.
What software program provide chain safety actually means
Historically, provide chain safety was to a solution to acquire visibility and mitigate Third-party code vulnerabilities by SCA. However as time went on and as new assault varieties emerged. In a 2021 govt order, software program invoice of supplies, or SBOMs, are required for all software program offered to the US federal authorities. The mandate underscores the significance of an correct record of all open-source software program elements present in a software-based product. The market rapidly realized that the scope of software program provide chain assaults, and the way we forestall these assaults, go means past SBOMs and malicious packages.
Provide chain safety is outlined as a particular side of utility safety that focuses on defending the software program improvement course of and the parts utilized in that course of. Software program provide chain safety just isn’t a single resolution; it’s a self-discipline.
Supporting the SLSA Framework
The Provide-chain Ranges for Software program Artifacts (SLSA) framework, developed in collaboration with the OpenSSF and Google, addresses the rising concern of software program provide chain safety, providing a structured strategy to assessing and enhancing the integrity of software program parts utilized in improvement.
SLSA introduces key ideas like artifacts, provenance, digests, immutable references, and construct integrity, that present a scientific means for the software program trade to safe the event lifecycle and promote constant safety requirements.
Understanding that the total scope of SCS is past a single device, Checkmarx has applied a broader technique to cowl issues exterior of your typical utility safety posture administration, in full alignment with the SLSA framework.
How Checkmarx helps you safe your software program provide chain
At the moment, Checkmarx is offering knowledgeable steerage and confirmed options to handle open-source threat, together with new and thrilling options to begin defending your complete provide chain right this moment.
In the previous few years, one of many largest rising threats have been malicious packages – notably completely different from susceptible packages. Within the SLSA framework, malicious packages are a type of dependency assault the place attackers inject or contribute malicious code into open-source tasks that your builders obtain and construct into your purposes. As soon as downloaded, the attacker’s malicious code is working inside your purposes, with no matter unknown intent the package deal carries.
Checkmarx SCA, launched in 2021, was a significant step in serving to organizations determine and begin reporting on their open-source vulnerabilities. We had been the primary vendor to incorporate malicious package deal detection inside our SCA resolution. Since then, our analysis workforce has inspected over 7.6 million open-source packages for every kind of threats, discovering 200,000+ malicious packages. We make that menace intelligence out there to you, both in our SCA product, the place findings are within the portal or immediately in builders’ IDE, or by an API-based menace intelligence feed.
Checkmarx SCA allows automated SBOM era, and Checkmarx Container Safety, which works with Checkmarx SCA, identifies vulnerabilities in open-source packages included in container pictures. Along with our companions at Sysdig, we just lately introduced runtime insights, so organizations can get the total image of pre-production and deployment, gaining visibility into which container pictures are in-use and prioritize those that pose probably the most threat.
We realized prospects want assist in prioritization, particularly with all these newly found vulnerabilities, so we launched Exploitable Path. It’s a singular characteristic that permits our prospects to prioritize vulnerabilities in open-source libraries.
Once you have a look at the SLSA framework, we even have at all times led the best way by way of figuring out Infrastructure-as-Code (IaC) misconfigurations. We’re the driving drive behind probably the most downloaded open-source device on this space – Preserve Infrastructure as Code Safe, or KICS for brief.
All of those are essential instruments in managing open-source threat, however we’re not stopping there.
Since GenAI is turning into a preferred useful resource for builders to generate code, a number of new SCS assaults have just lately emerged, resembling:
- AI hallucinations: These are false knowledge factors or patterns that AI fashions would possibly “perceive” on account of adversarial inputs or misinterpretations, which will be exploited by malicious actors.
- Immediate injections: Risk actors can manipulate AI fashions by introducing or “injecting” specifically crafted prompts, tricking the system into undesired behaviors or outputs.
- AI secret leakage: There is a potential threat of AI fashions inadvertently revealing confidential info they had been skilled on, providing a goldmine for cybercriminals.
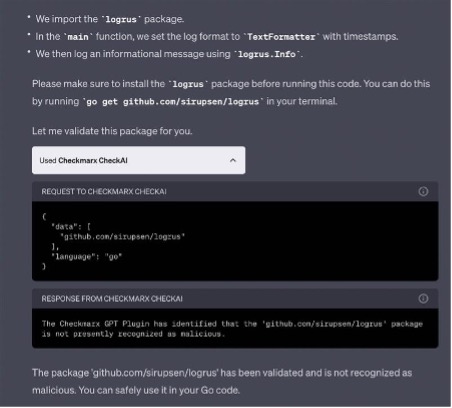
In August, Checkmarx launched the trade’s first plugin to detect and forestall assaults towards ChatGPT-generated code. The plugin allows builders to simply scan their ChatGPT-generated code for vulnerabilities throughout the ChatGPT interface, obtain on the spot suggestions on potential vulnerabilities or validation of open-source packages, and make use of safety towards malicious open-source packages.
Now, we’re main the best way once more, and broaden the definition of software program provide chain safety, past simply malicious packages, to each part in, and each device used to construct your purposes. As a part of the Checkmarx One 3.0 launch, we’re taking it one step additional, introducing two new capabilities –Secrets and techniques Detection and Venture Scorecard.
Stop secrets and techniques from leaking on exterior instruments with Secrets and techniques Detection
Secrets and techniques, resembling passwords, API keys, cryptographic keys, and different confidential knowledge, are a frequent goal of a distributed supply-chain assault.
Secrets and techniques can simply be mistakenly shared on exterior instruments like slack, confluence, twitch, and documentation pages.
Secret detection isn’t new – we’ve got some of the fashionable open-source instruments for secret detection. 2MS from Checkmarx has over 2 million downloads, and anybody can get began right this moment by detecting secrets and techniques resembling login credentials, API keys, SSH keys and extra hidden in code, content material techniques, chat purposes and extra.
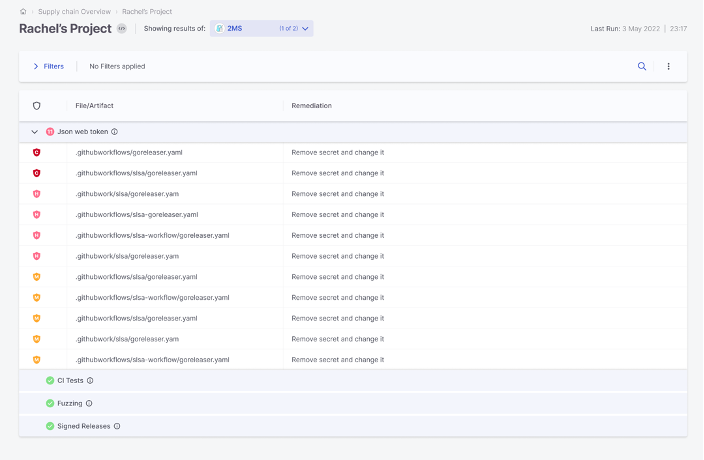
In case you are a Checkmarx One consumer, Secret Detection is now out there immediately within the Checkmarx One platform.
Deal with probably the most susceptible tasks first with Venture Scorecard
One of many newest additions to the Checkmarx Provide Chain Safety portfolio is Venture Scorecard, which allows organizations to test their very own tasks rapidly and see probably the most susceptible or at-risk tasks, permitting enterprises to prioritize which to deal with first.
Venture Scorecard leverages the format from a preferred device, the OSSF Scorecard, which assesses open-source tasks for safety dangers by a sequence of automated checks.
These checks cowl completely different components of the software program provide chain together with supply code, construct, and dependencies, and assigns every test a rating of 1-10. An auto-generated “security score” helps customers as they determine the belief, threat, and safety posture for his or her particular utility.
Whereas an essential device in combating the uptick of open-source software program assaults, open-source tasks are solely a portion of the tasks in your utility. Checking the method and parts of owned tasks is a crucial aspect in securing the full software program provide chain.
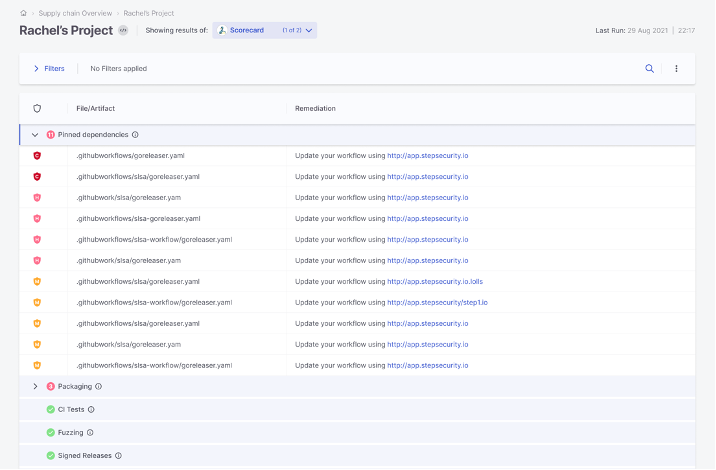
With Venture Scorecard, customers can auto-generate a safety rating for their very own tasks primarily based on a sequence of checks, together with:
- Binary Artifacts – Is the venture freed from checked-in binaries?
- Department Safety – Does the venture use department safety?
- CI Assessments – Does the venture run assessments in CI, e.g., GitHub Actions, Prow?
- Code evaluate – Does the venture observe code evaluate earlier than code is merged?
- Harmful workflow – Does the venture keep away from harmful coding patterns?
- Vulnerabilities – Does the venture have unfixed vulnerabilities?
By using the Venture Scorecard, as a part of the Checkmarx Provide Chain module, we enable enterprises to rapidly see probably the most susceptible or at-risk tasks, and in the end assist prioritize which to deal with first.
Taking the following step to safe your software program provide chain
It’s essential to take steps to safe your software program provide chain right this moment; detecting provide chain assaults in code packages, securing your developer’s evolving workstations helps speedy improvement whereas decreasing threat.
Present Checkmarx One or Checkmarx SCA prospects could have entry to all these instruments throughout the platform.
For those who’re not already a Checkmarx One buyer, you can begin securing your software program provide chain right this moment with too many secrets and techniques (2MS), out there as an open-source venture on GitHub.
We’re extremely excited to announce these new options that will help you safe your software program provide chain, however we’re solely getting began. The work of securing the software program provide chain is rarely completed, as dangerous actors determine progressive new methods to capitalize on gaps in course of and parts, so keep tuned for extra thrilling bulletins.
For those who’d prefer to study extra register now to hitch us for our technical deep dive webinar on Nov sixth, “Secure your software supply chain”.