Exploring Sensible Steps for Cleansing up Id Sprawl
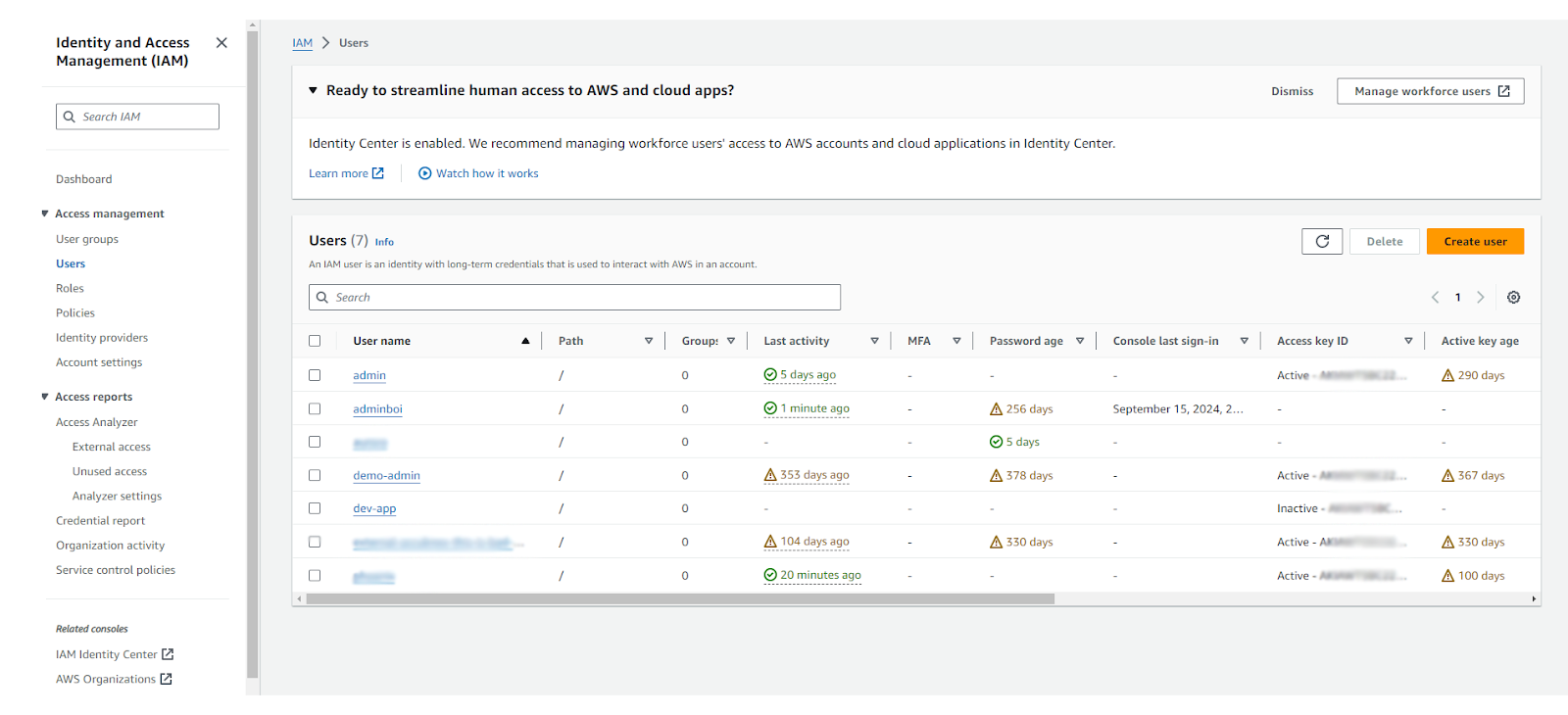
Plenty of safety instruments act like discovering the record of unused identities is the arduous half. The truth, nevertheless, is that operating a scan takes 30 seconds to uncover a 12 months’s price of labor. Anybody who’s managed a cloud setting is aware of that identities sprawl earlier than anything. Even Latio’s tiny AWS account already has 7 customers and 34 roles that I’ve used for various companies and totally different testing at totally different occasions. In actuality, solely 2 of these customers and three of the roles are often used. Extra to the purpose, none of these customers ought to even exist – they need to be roles for short-term entry. However like most firms, that’s one thing for my future DevOps group to deal with later.
Safety engineers like me are inclined to get actually fixated on that idealized situation – we all know that all the things must be ephemeral, least privileged roles which are all granting short-term entry to assets solely when wanted. This was the unique imaginative and prescient of CIEM – or cloud id and entitlement administration – to assist groups establish these over-permissioned roles and replace them.
Figuring out Zombie Identities
Fortunately, AWS has added just a few options to make figuring out zombie identities simpler. Within the outdated days, there was simply the person’s web page, sorted by console final sign-in.
Sadly, there are a variety of gotchas with simply doing this:
- It’s not accounting for roles
- It’s not accounting for SSO customers
- It’s not simple to automate
- It’s tough to separate the a number of entry keys from console use, and why an id exists within the first place. Normally, names don’t mirror actual use!
The subsequent best factor to do is use the Credential Report:
This creates a CSV report of principally the identical factor that was displayed on the person display screen. That is helpful for auditor hand offs, however usually not a lot better than the place we began.
Again in 2019, AWS launched the AWS Entry Analyzer. This device began very primary – taking a look at 90 days of CloudTrail logs to find out what permissions a person account was utilizing, and you could possibly use these outcomes to tighten permissions for customers.
Since then, the performance has been tremendously improved:
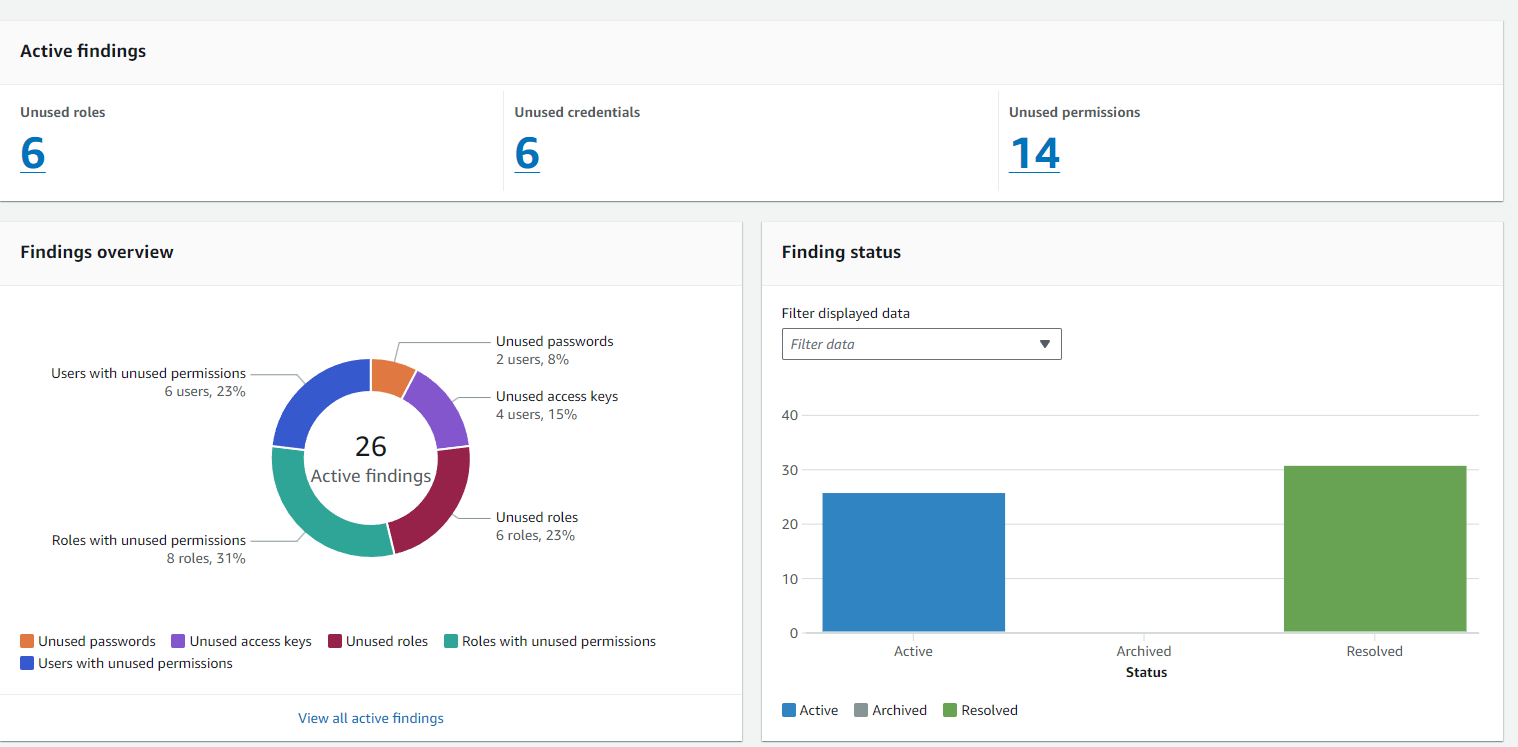
Whereas nobody has ever accused the AWS UI of being good to take a look at, they’ve added a variety of extra usable information right here for the reason that preliminary launch. Sadly, as I’ll argue later, it nonetheless doesn’t remedy the core situation with zombie identities. Creating an unused entry and exterior IAM Entry Analyzer is easy from this web page, however watch out about what you set the “unused days detector” to since you may’t change it with out creating a brand new analyzer.
A fast observe: sooner or later, AWS Entry Analyzer acquired weirdly costly. As a safety engineer, I’ve been self educated to click on the allow button earlier than studying something, for this reason I’m simply realizing this now. The pricing web page exhibits that even a small account with 100 customers in 5 accounts will run up about $3,000/12 months.
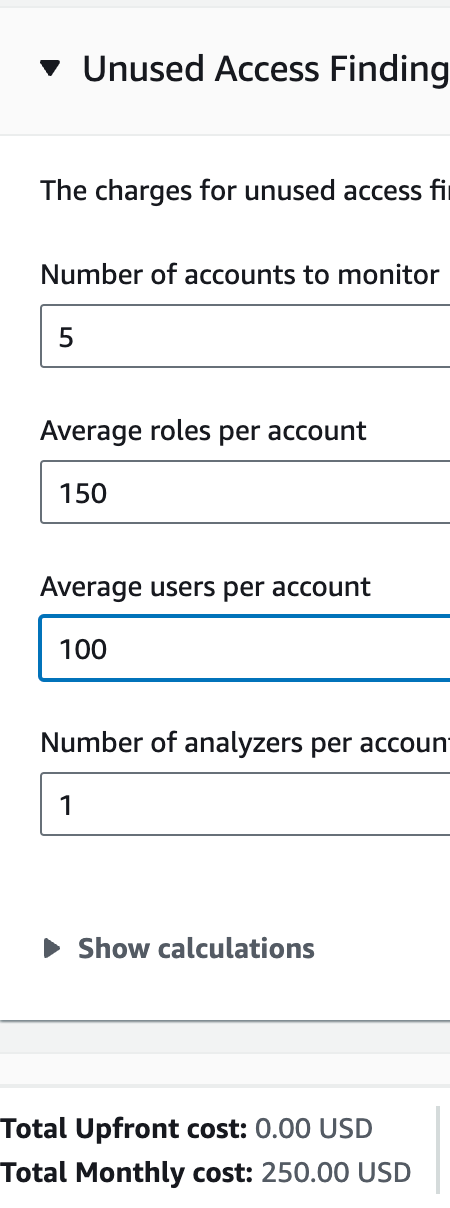
For our functions, let’s have a look at utilizing AWS Entry Analyzer to seek out unused roles and credentials, is it price the fee?
Determine Out What Permissions to Change
Going again to our customers web page, my AWS account has 7 customers, of which 1 account is used through the CLI, 1 is only for console entry, and a couple of are vendor keys from testing (sure, they need to be utilizing roles, however we’ll give them a go for now).
On roles, it’s vital to notice that that is in all probability the only most ignored side of AWS safety. I’ve 34 roles in my account, though I personally use 0 of them straight, and solely 3 of them had been created by me to run https://record.latio.tech. Of those roles, 5 are associated to distributors, 3 are associated to my net app, and an unknown variety of them are associated to companies.
Figuring out these service roles is the arduous half, take these eksctl roles for instance:
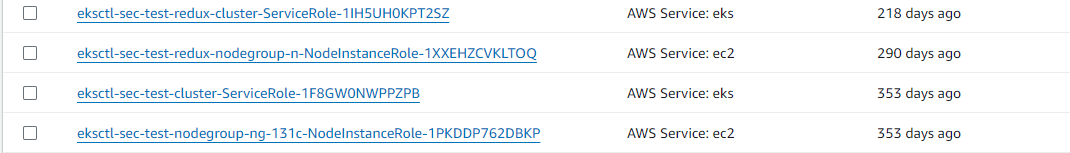
I bear in mind these roles getting created after I made my first cluster with eksctl on this account, however I don’t know the main points of why they had been created as a result of it was finished behind the scenes. Think about I’m in an enterprise with hundreds of comparable roles; it’s unattainable to inform who, what, the place, how, and why these roles had been created. Extra importantly, I received’t know in the event that they’re wanted once more – perhaps they’re important for deploying the EKS cluster in an emergency? These sorts of questions are what create inaction for safety groups on these findings.
In sum, I’ve 3 unused customers and an unknown variety of unused roles. AWS Entry Analyzer helped in two foremost methods: first, it helpfully cut up out particular person entry keys in case they’re used for various issues. Second, it helpfully confirmed unused permissions and gave a brand new coverage suggestion to replace these permissions.
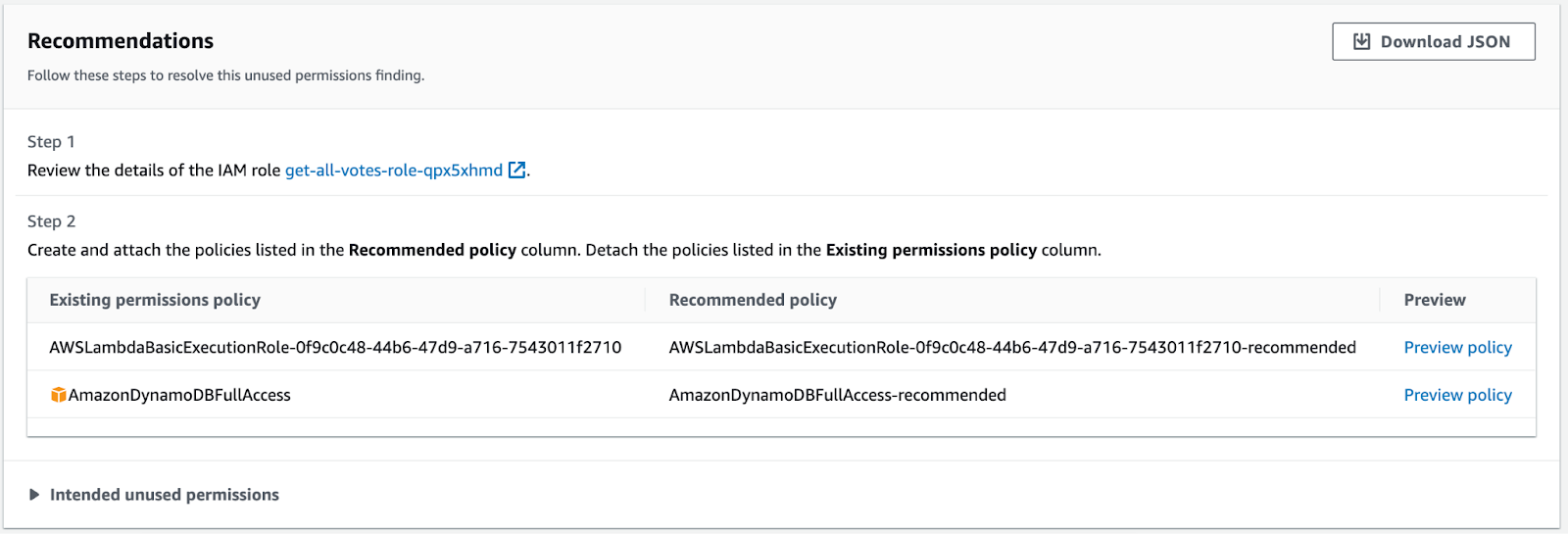
At this level, AWS Entry Analyzer would appear to recommend that I click-ops my manner by each coverage, creating customized per-user insurance policies. In different phrases, starting the time-consuming nightmare of making an attempt to create per-user least privileged insurance policies. That is what many firms keep in mind, nevertheless it’s a challenge that simply doesn’t warrant the time funding wanted.
Doing the Needful
The primary annoying factor about utilizing the analyzer is that you may’t take any motion straight from it. An “update policy” button would go a good distance right here. As an alternative, you need to click on the discovering, go to it, then go to the person, then delete the entry keys.
Let’s see if the AWS Entry Analyzer makes us really feel snug deleting something… lengthy story brief, it didn’t assist as a lot as I needed. Right here had been the issues:
- The analyzer doesn’t give broader context in regards to the position or person, like what property it’s deployed on or what IP addresses its final calls got here from. In different phrases, you may’t work out why the present permissions exist.
- That is nonetheless scary to automate – it flagged identities I don’t need to delete, which implies I can by no means “just do this” in the case of deleting identities.
- The workflow could be very time-consuming as a result of most orgs will disable an id, wait per week, after which delete it later. Multiply that throughout hundreds of findings, and it’s a endless course of.
- The unused permissions are nonetheless scary to vary since you nonetheless have to know what a service is doing earlier than you’re feeling snug blocking actions it would want for a uncommon motion.
Some extra points with AWS Entry Analyzer are:
- Understanding these leads to an SSO context, the place the disabling course of can transcend disabling the position on the AWS facet or the place a number of customers seemingly share a single position. On this context, the AWS IAM Entry Analyzer wouldn’t present you a lot.
- The analyzer suggests insurance policies, assuming you’ll be okay creating what are successfully per position permissions. Whereas that is good from a right away safety perspective, the draw back is making a ton of added complexity should you’re not already utilizing IaC to outline per-role permissions.
A quick observe: the exterior entry analyzer is a neat manner to assemble information in your third-party connections. Nonetheless, it has the identical issues with not offering context because the unused analyzer, so I view it extra as helpful for auditing.
Conclusion
In my expertise prior to now, and from this newest take a look at drive, AWS IAM Entry Analyzer is only a small step in the direction of figuring out and eradicating zombie identities. In my view, the core drawback with zombie identities was by no means recognizing them – sorting by final use time was all the time effective for that. As an alternative, the important thing issues are:
- Realizing why these identities had been created
- Realizing why they’re now not used
- Realizing if they are going to be wanted sooner or later
- With the ability to automate a course of for removals. Normally, one thing involving a day by day lambda operate hitting cloud APIs, sending to SQS, and sending slacks with opt-in/opt-out
For many orgs, attending to quantity 4 will not be one thing their in-house engineering groups can prioritize. Even when it was, it’s not the form of work that tends to get prioritized at mid-market companies!
Probably the most helpful a part of AWS Entry Analyzer is seeing what permissions are going unused by present assets; nevertheless, I’ve not often seen safety groups in a spot the place they really feel good leveraging these findings. These are all the time positioned within the “deal with it later” bucket, the place they’ll keep for fairly a while.
Distributors like Sonrai assist make this workflow much more actionable by sustaining the automation for you and quarantining zombie identities, which implies all permissions are restricted till a workflow to grant them again is accomplished.
Their answer, the Cloud Permissions Firewall, does this for unused sensitive permissions, too, by setting customized block insurance policies, creating approval workflows, and doing it throughout your entire accounts in a single place. This workflow is much more scalable than clicking between particular person findings.
As a plus, they’re not paying me to say this, however the pricing even appears akin to AWS Entry Analyzer while you’re getting considerably extra worth out of Sonrai.