Over 28,000 folks from Russia, Turkey, Ukraine, and different nations within the Eurasian area have been impacted by a large-scale cryptocurrency-stealing malware marketing campaign.
The malware marketing campaign disguises itself as respectable software program promoted through YouTube movies and fraudulent GitHub repositories the place victims obtain password-protected archives that provoke the an infection.
Based on cybersecurity agency Dr. Net, the marketing campaign makes use of pirated office-related software program, recreation cheats and hacks, and even automated buying and selling bots to deceive customers into downloading malicious information.
“In total, this malware campaign has affected more than 28,000 people, the vast majority of whom are residents of Russia,” stated Dr. Net.
“Significant numbers of infections have also been observed in Belarus, Uzbekistan, Kazakhstan, Ukraine, Kyrgyzstan and Turkey.”
Supply: Dr. Net
An infection chain
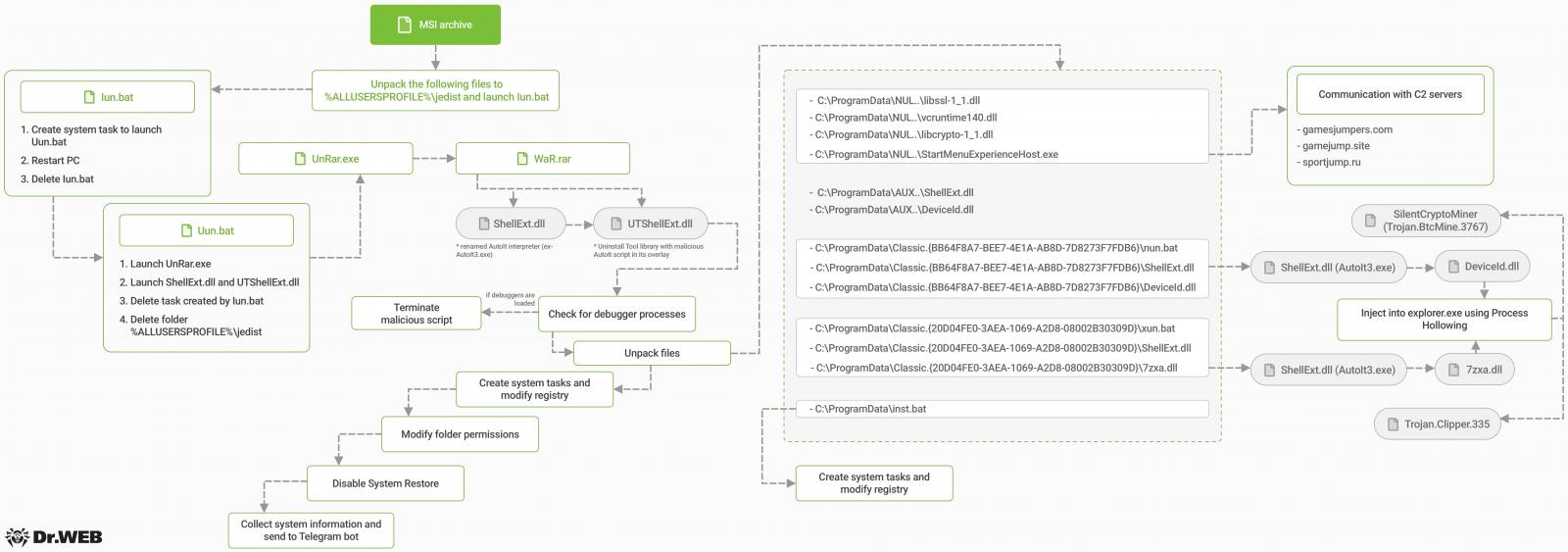
The an infection begins with opening a self-extracting archive that evades antivirus scans when downloaded because it’s password-protected.
After the sufferer enters the supplied password, the archive drops numerous obfuscated scripts, DLL information, and an AutoIT interpreter used to launch the digitally signed loader of the principle payload.
The malware checks for the presence of debugging instruments to see if it is working on an analyst’s atmosphere and terminates if any are discovered.
Subsequent, it extracts the information required for the following levels of the assault after which makes use of the Picture File Execution Choices (IFEO) method to change the Home windows Registry for persistence.
Briefly, it hijacks respectable Home windows system companies in addition to Chrome’s and Edge’s replace processes with malicious ones, so the malware information are executed upon the launch of those processes.
The Home windows Restoration Service is disabled, and the “delete” and “modify” permissions on the malware’s information and folders are revoked to stop tried cleanups.
From there on, the Ncat community utility is employed to ascertain communication with the command and management (C2) server.
The malware may also accumulate system data, together with working safety processes, which it exfiltrates through a Telegram bot.
Supply: Dr. Net
Monetary affect
The marketing campaign delivers two key payloads onto the victims’ machines. The primary one is “Deviceld.dll,” a modified .NET library used to execute the SilentCryptoMiner, which mines cryptocurrency utilizing the sufferer’s computational sources.
The second payload is “7zxa.dll,” a modified 7-Zip library that acts as a clipper, monitoring the Home windows clipboard for copied pockets addresses and changing them with addresses beneath the attacker’s management.
Dr. Net didn’t specify within the report the potential mining income from the 28,000 contaminated machines however discovered that the clipper alone had hijacked $6,000 value of transactions, diverting the quantity onto the attacker’s addresses.
To keep away from surprising monetary losses, solely obtain software program from the venture’s official web site and block or skip promoted outcomes on Google Search.
Moreover, watch out of shared hyperlinks on YouTube or GitHub, because the legitimacy of those platforms doesn’t assure the obtain vacation spot’s security.